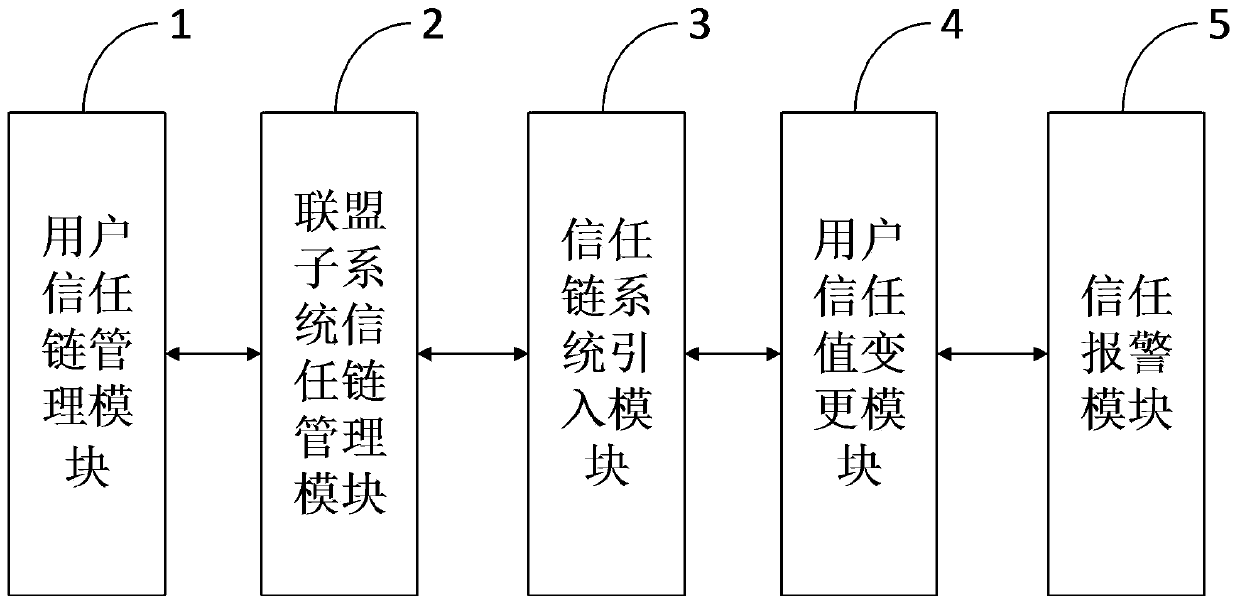
Heterogeneous identity alliance user trust management system based on class block chain technology
A trust management and blockchain technology, applied in the field of heterogeneous identity alliance user trust management system, can solve the problems of no other data, high cost, no trust management system, etc., to reduce the risk of damage and reduce costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
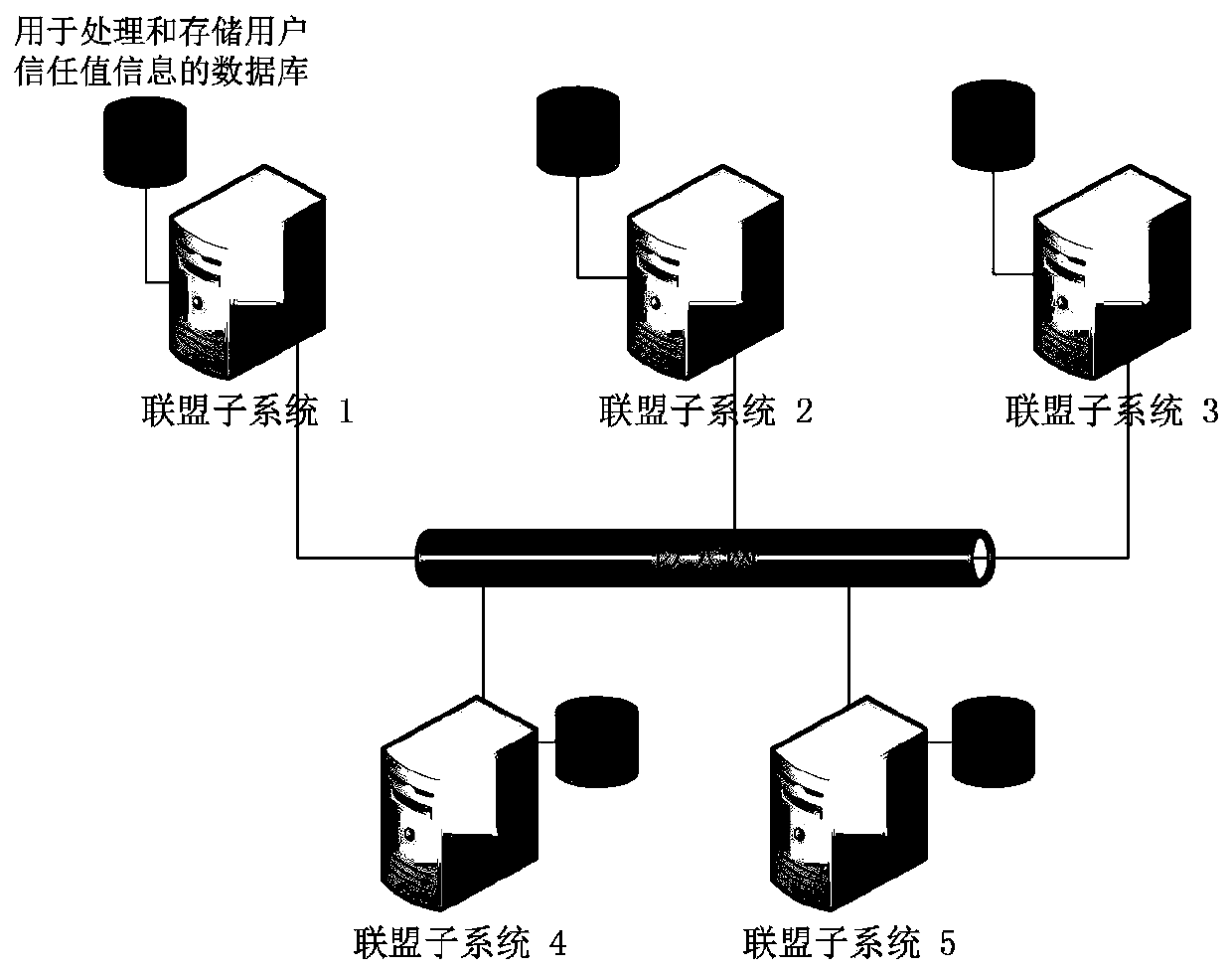
[0096] Addition of user trust chain: such as Figure 5-Figure 6 As shown, when all subsystems of the heterogeneous identity alliance have established a trust chain system, if a subsystem needs to add new users, follow the steps below to add the user trust chain:
[0097] (1) Create a database for users of the alliance subsystem to store user trust chain information.
[0098] (2) Perform user trust value evaluation according to the existing trust value evaluation of the system.
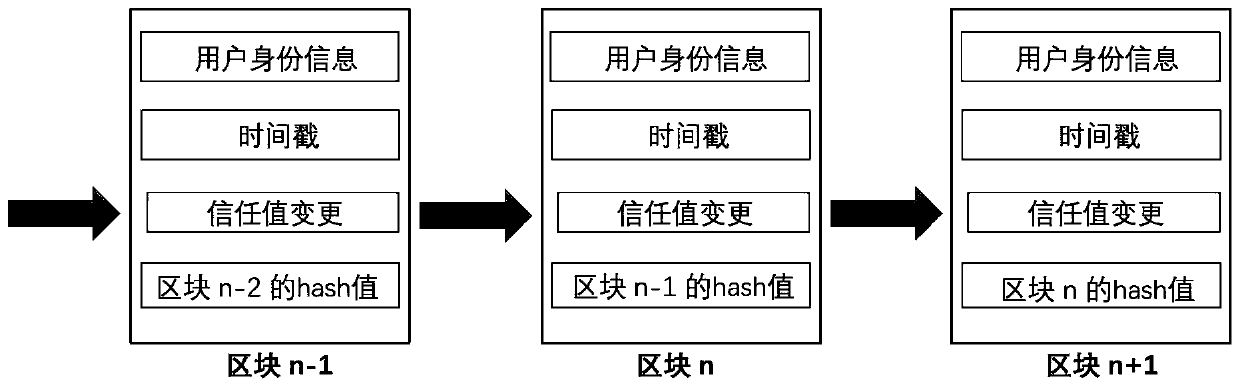
[0099] (3) Use the evaluation value to build the first node of the trust chain and the initial trust block. The initial trust block specifically includes: the user identity information is an ID value for uniform identification of the user in the alliance. The timestamp is the timestamp when the information was written. The initial value of the trust value is a value calculated by evaluating the user trust value according to the existing trust value evaluation of the system. And use random value ins...
Embodiment 2
[0104] Alliance subsystem added: as Figure 7 As shown, when the heterogeneous identity federation adds subsystems, it is necessary to add all users' trust chains for the added subsystems. It is necessary to ensure that no repeated and different trust chains are added for the same user.
[0105] Specific steps are as follows:
[0106] (1) Broadcast user information to other subsystems of the alliance.
[0107] (2) If the trust chain already exists in other subsystems, copy the existing trust chain to the trust chain database of the user.
[0108] (3) If the user does not exist in all subsystems, calculate the trust value for the user and establish a new trust chain for it.
Embodiment 3
[0110] Introduction of trust chain system: When introducing the trust chain system for the first time, first select one of the systems in the heterogeneous identity alliance to add the process of trust chain for all users, and then switch to the next step when all users are added The introduction of a subsystem can avoid the situation that the same user repeatedly establishes different trust chains caused by the simultaneous introduction of multiple systems.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com