Entrance guard control method and device and terminal equipment
An access control and door control technology, applied in the direction of instruments, single input/output port registers, time registers, etc., can solve problems such as inability to guarantee user safety, security loopholes, etc. The effect of safety management efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
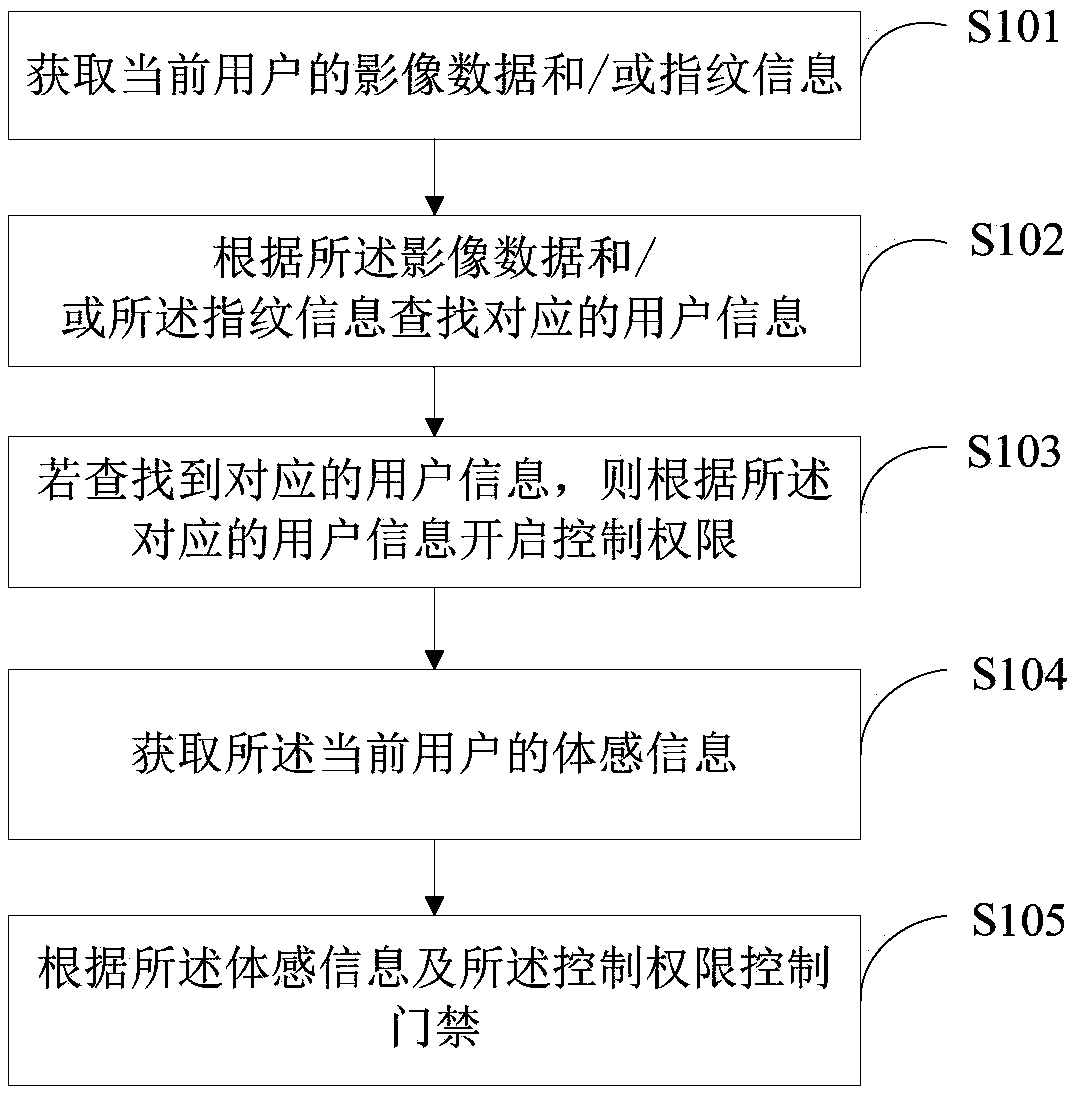
[0047] Such as figure 1 As shown, this embodiment provides an access control method, which can be applied to terminal devices such as hands. The access control method provided in this embodiment includes:
[0048] S101. Obtain image data and / or fingerprint information of a current user.
[0049] In a specific application, the camera is controlled to capture the image data of the current user or obtain the fingerprint information of the current user. The current user includes one or more users who are currently within the shooting range of the camera set on the access control. Among them, the image data can include image data such as photographs and videos of the current user taken, and can also include pupil image data, iris image data, and palmprint image data for pupil, iris, and palmprint recognition verification. feature image data.
[0050] S102. Search for corresponding user information according to the image data and / or the fingerprint information.
[0051] In a spe...
Embodiment 2
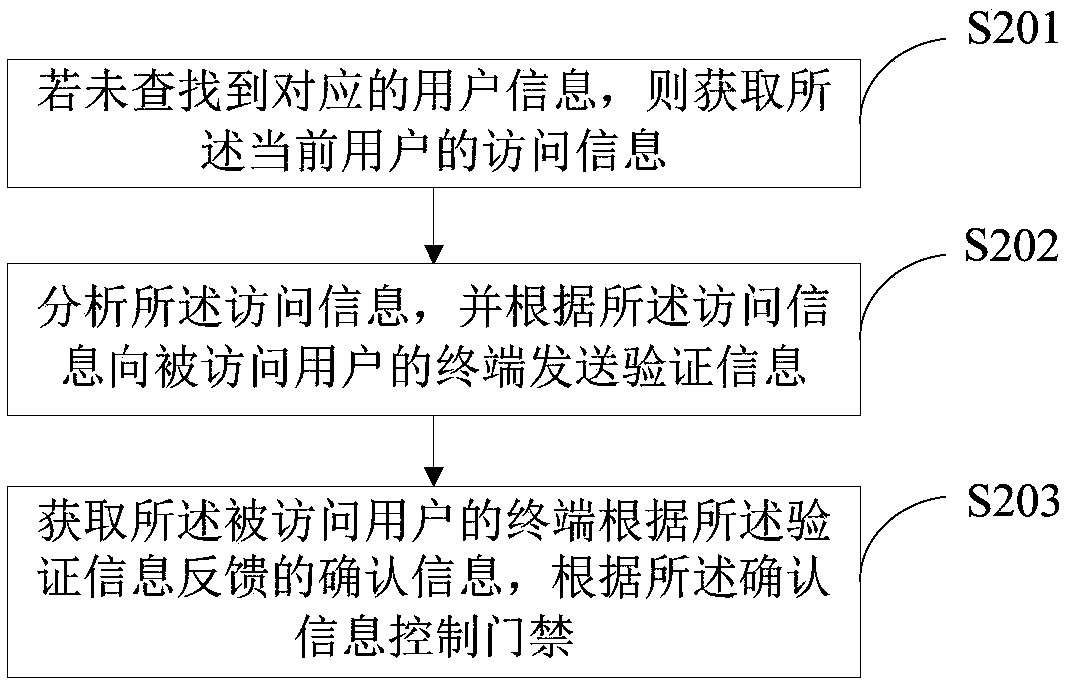
[0064] Such as figure 2 As shown, this embodiment is a further description of the method steps in the first embodiment. In this embodiment, after step S102, include:
[0065] S201. If no corresponding user information is found, acquire the access information of the current user.
[0066] In a specific application, if the corresponding user information is not found in the database according to the recognized face image information or the obtained fingerprint information, then the current user is not a registered user. At this time, the access information input by the current user is obtained.
[0067] S202. Analyze the access information, and send verification information to the terminal of the accessed user according to the access information.
[0068] In a specific application, after obtaining the access information input by the current user, analyze it, and send a verification message to the terminal of the accessed user in the access information according to the analysis...
Embodiment 3
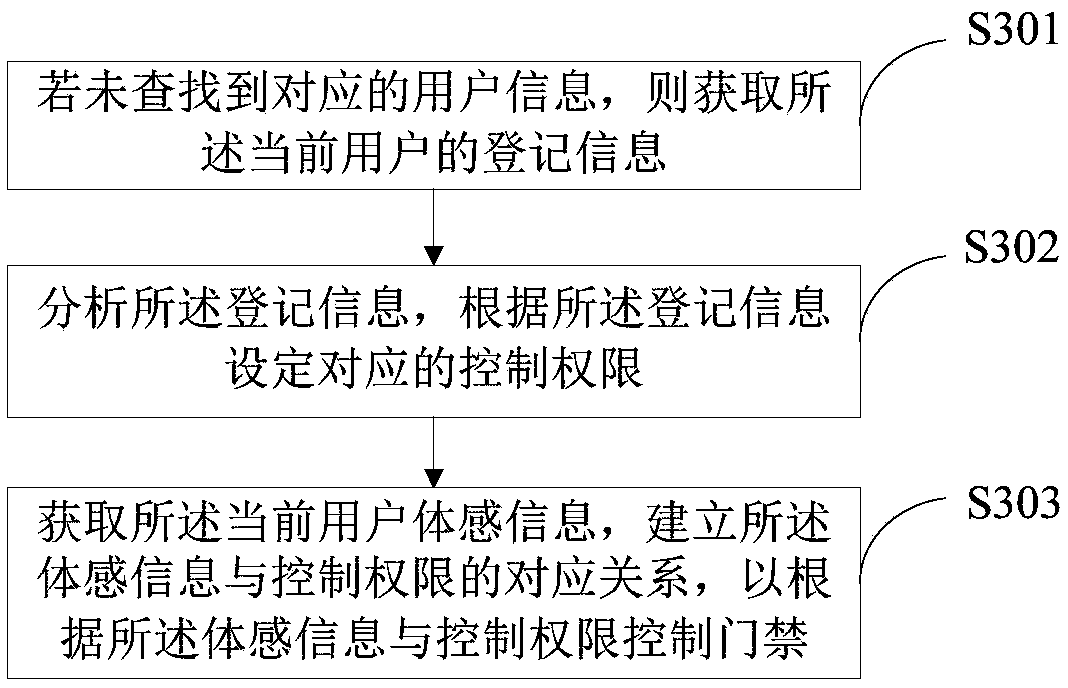
[0073] Such as image 3 As shown, this embodiment is a further description of the method steps in the first embodiment. In this embodiment, after step S102, it also includes:
[0074] S301. If no corresponding user information is found, acquire registration information of the current user.
[0075] In a specific application, if the corresponding user information is not found in the database according to the recognized face image information or the acquired fingerprint information, then the current user is not a registered user, and the registration information input by the current user is obtained.
[0076] In this embodiment, after step S301, it also includes:
[0077] Send the registration information to the manager's terminal to confirm the registration;
[0078] Acquiring confirmation registration information fed back by the manager's terminal according to the registration information, and performing registration.
[0079] Specifically, after obtaining the registration...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com