Security management method and security system of sensor network based on distributed ledger technology
A security management and security system technology, applied in transmission systems, computer security devices, electrical digital data processing, etc., can solve the problem that the sensor network cannot realize the security enhancement data sharing function, and there is no blockchain network smart contract, etc. Achieve the effect of ensuring that it is not tampered with, eliminating data sharing, and ensuring the security of data transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Below, in conjunction with the accompanying drawings, preferred embodiments of the present invention are given and described in detail, so that the functions and features of the present invention can be better understood.
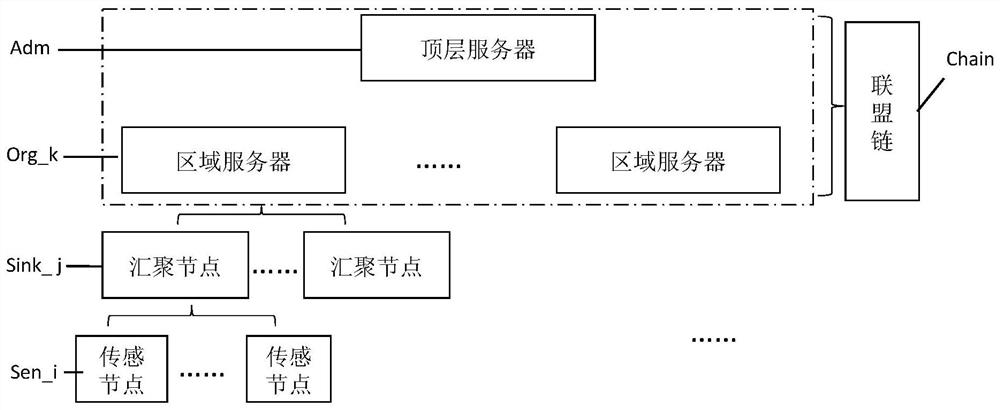
[0042] Before describing the specific content of the invention, the composition of the sensor network system will be explained first. In a large-scale sensor network, it includes but is not limited to the following elements: sensor nodes, sink nodes, regional servers and regional managers, top-level servers and global managers, and alliance chains.
[0043] Such as figure 1 Shown is a typical sensor network, which shows the network topology and components of the sensor network. The sensor network is basically consistent with the existing layered structure of the sensor network, including bottom-up Layer architecture consists of multiple sensor nodes Sen_i, multiple sink nodes Sink_j, multiple regional servers Org_k and a top-level server Adm. Among...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com