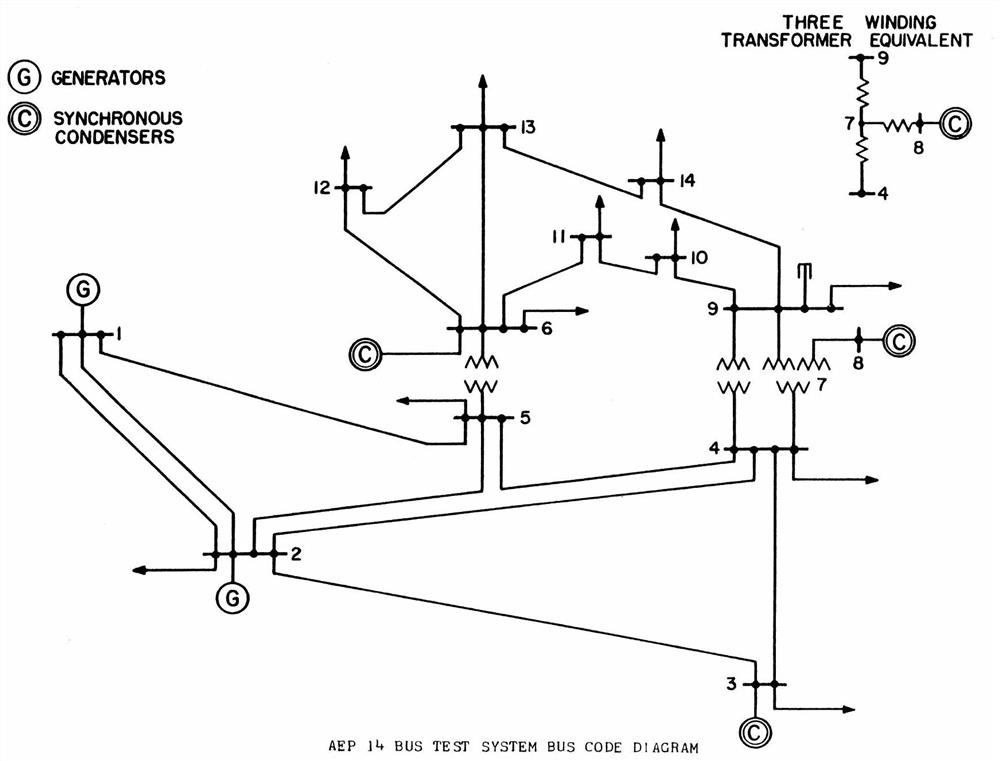
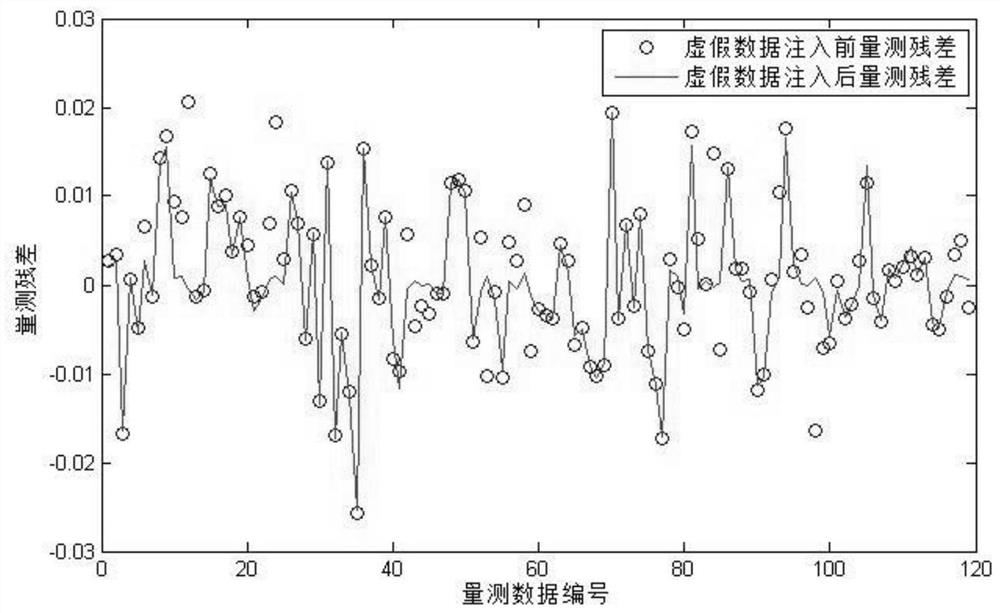
A False Data Attack Identification Method Based on Probability Distribution
A technology of false data attack and identification method, applied in the field of smart grid data information security, can solve problems such as affecting calculation results, large residual error of bad data, loss of false data, etc., to ensure universality, improve reliability, and reduce errors. The effect of judgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The specific embodiments of the present invention will be further described in detail below with reference to the accompanying drawings. The following examples are only descriptive, not restrictive, and cannot limit the protection scope of the present invention.
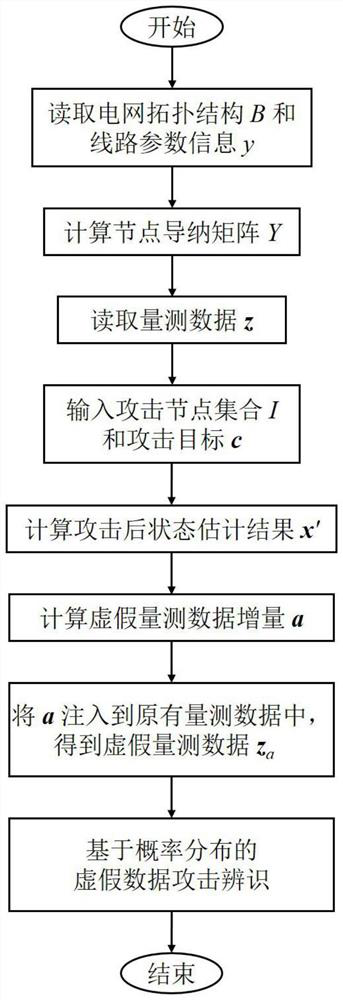
[0048] This embodiment provides a method for identifying false data attacks based on probability distribution, the flowchart of which is as follows image 3 shown, including the following steps:
[0049] 1) Read the grid topology B and line parameter information y:
[0050] The topology of the power grid includes the connection status between each node, the number of connection lines, the opening and closing of switches, and so on. Line parameter information includes conductance g and susceptance b of the line, conductance and susceptance y to ground i0 Wait.
[0051]2) Calculate the node admittance matrix Y;
[0052] The elements in the admittance matrix are divided into mutual admittance and self admitt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com