Quick encryption system based on base-4 binary system underlying modular operation
An encryption system, modulo operation technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as large computing time and computing resources, serious and limited elliptic curve encryption algorithm application scenarios, etc., to save The effect of shortening operation time and operation cycle
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
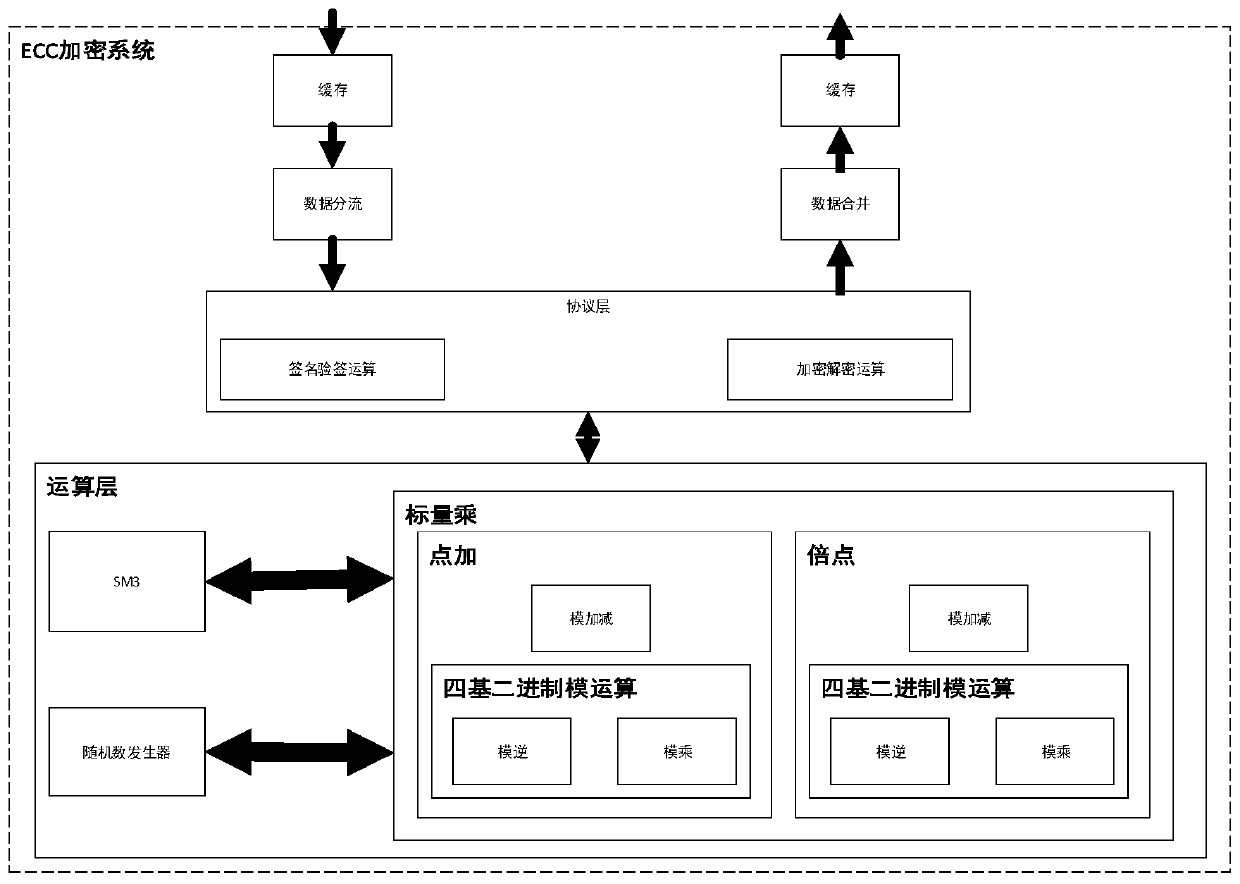
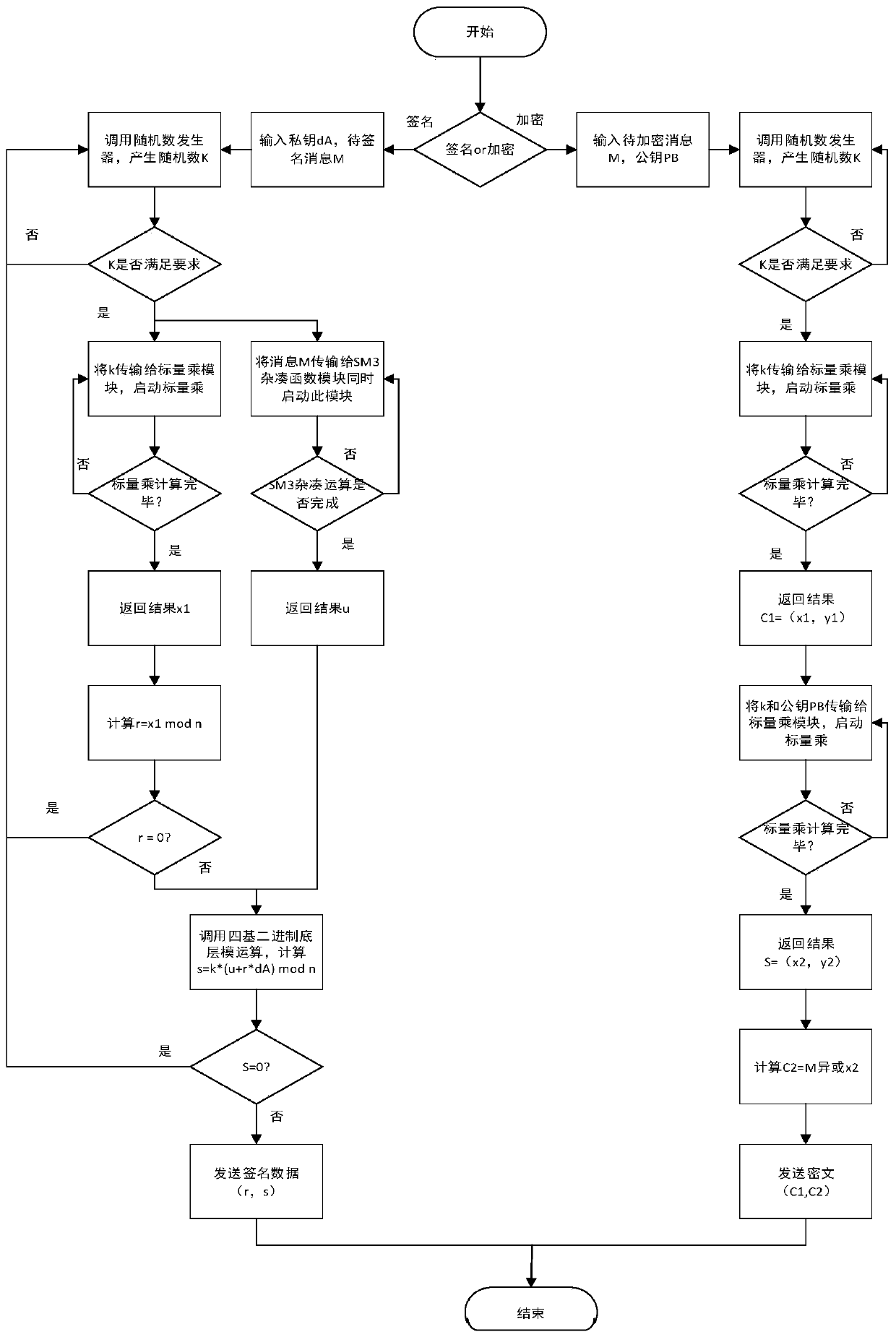
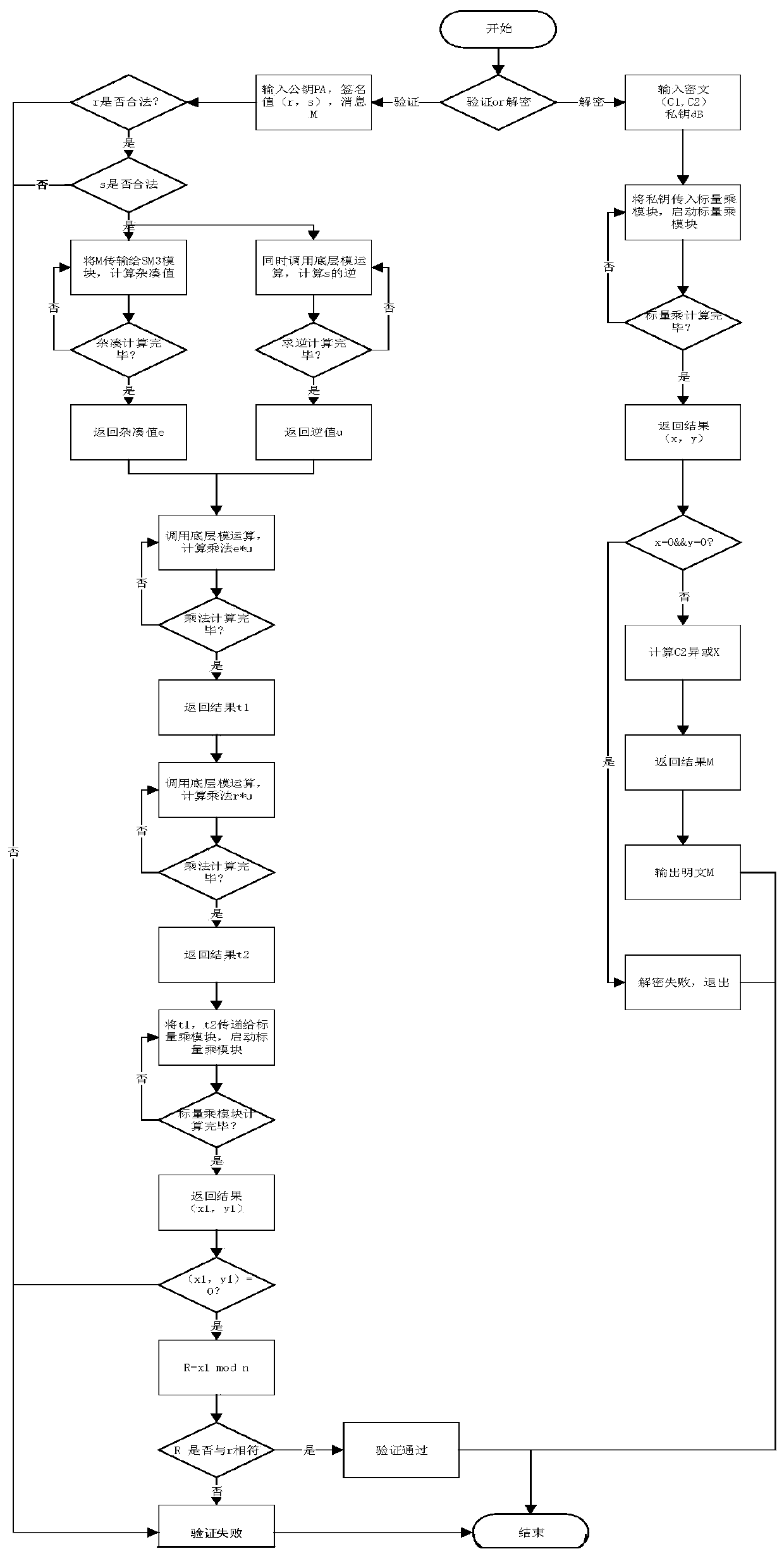
[0049] The system as a whole is composed of a protocol layer and a calculation layer. The protocol layer is a functional module, which is responsible for realizing the signature verification and encryption and decryption functions of the entire system; the calculation layer mainly performs curve domain arithmetic and prime number domain modulo calculation. All operations of the protocol layer are completed by the operation layer, and then the data is sent back to the protocol layer. Among them, modular inverse, modular multiplication and modular addition and subtraction constitute point addition and doubling operations, and point addition and doubling operations constitute scalar multiplication operations.
[0050] The hash operation required by the protocol layer is completed by the SM3 module, and the random number generator is responsible for generating random numbers to form a private key and generating operands required in the operation process. In addition, the buffer mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com