Data desensitization control method, electronic device and computer readable storage medium
A control method and data desensitization technology, applied in the field of information security, can solve the problem of low data table processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
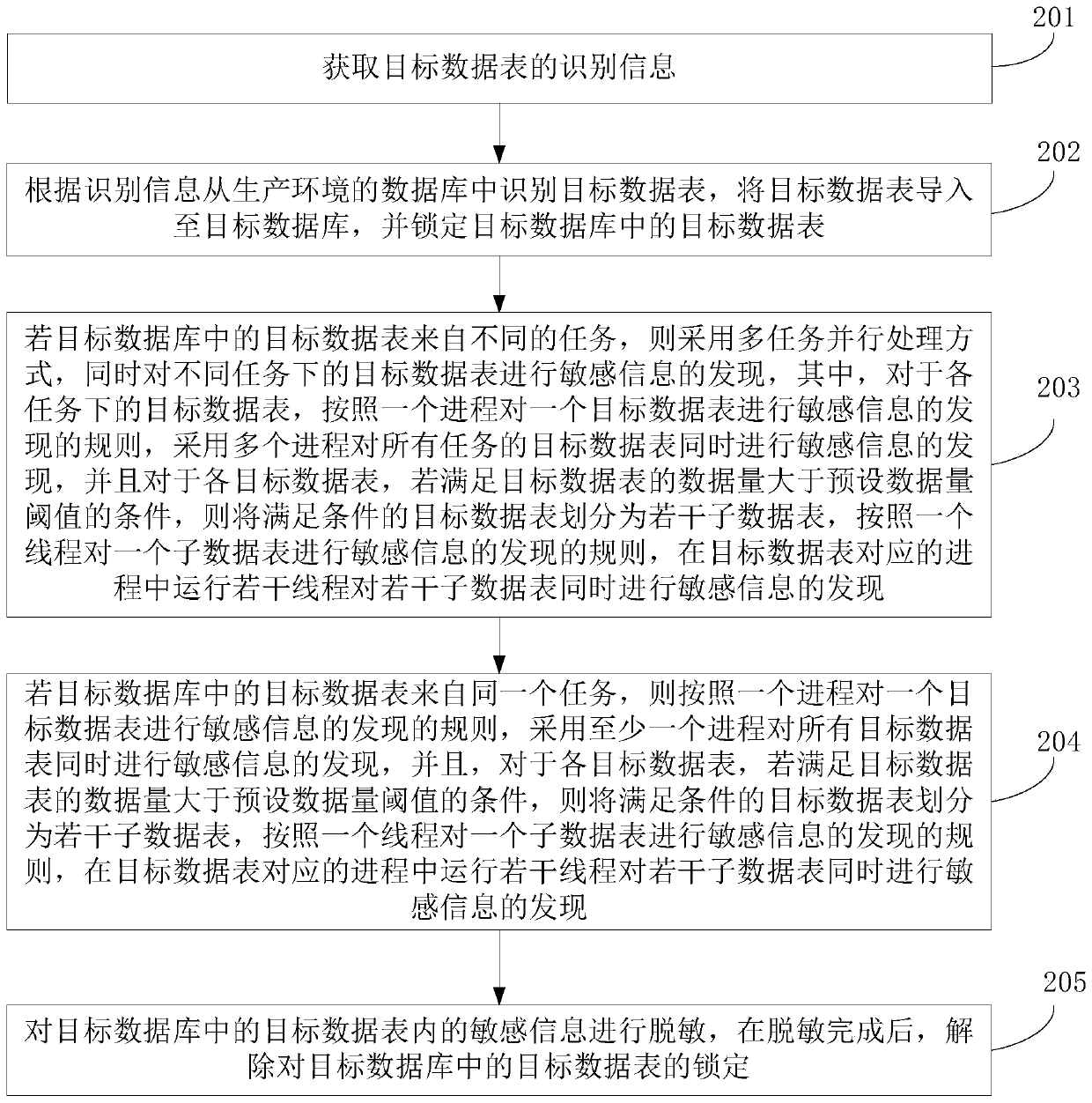
[0035] The embodiment of this application proposes a data desensitization control method, see figure 2 , the method includes:
[0036] Step 201, obtaining the identification information of the target data table;
[0037] In this embodiment, the target data table is a data table required by the data demander. Optionally, the identification information of the target data table may be a table name, or a field name in the table, etc., which is not limited in this embodiment. In this embodiment, the table name and field name for determining the target data may be provided by the data requester.
[0038] Optionally, obtaining the identification information of the target data table includes: obtaining the identification information of the target data table sent by the data demander, or obtaining the identification information of the target data table stored locally.
[0039] Step 202, identifying the target data table from the database of the production environment according to th...
no. 2 example
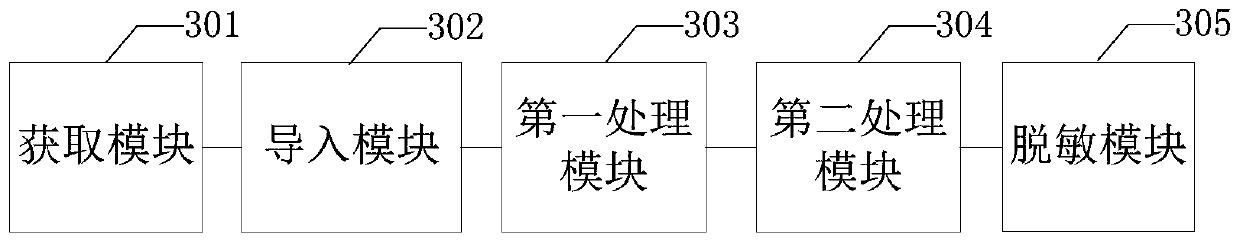
[0077] The second embodiment of the present invention provides an electronic device, see image 3 , the electronic device includes:
[0078] An acquisition module 301, configured to acquire the identification information of the target data table;
[0079] The import module 302 is used to identify the target data table from the database of the production environment according to the identification information, import the target data table into the target database, and lock the target data table in the target database to prohibit the data demander of the target data table from accessing the target database The target data table in;
[0080] The first processing module 303 is used for if the target data tables in the target database come from different tasks, then adopt a multi-task parallel processing method, and simultaneously discover sensitive information on the target data tables under different tasks, wherein, for each task According to the rule of discovering sensitive i...
no. 3 example
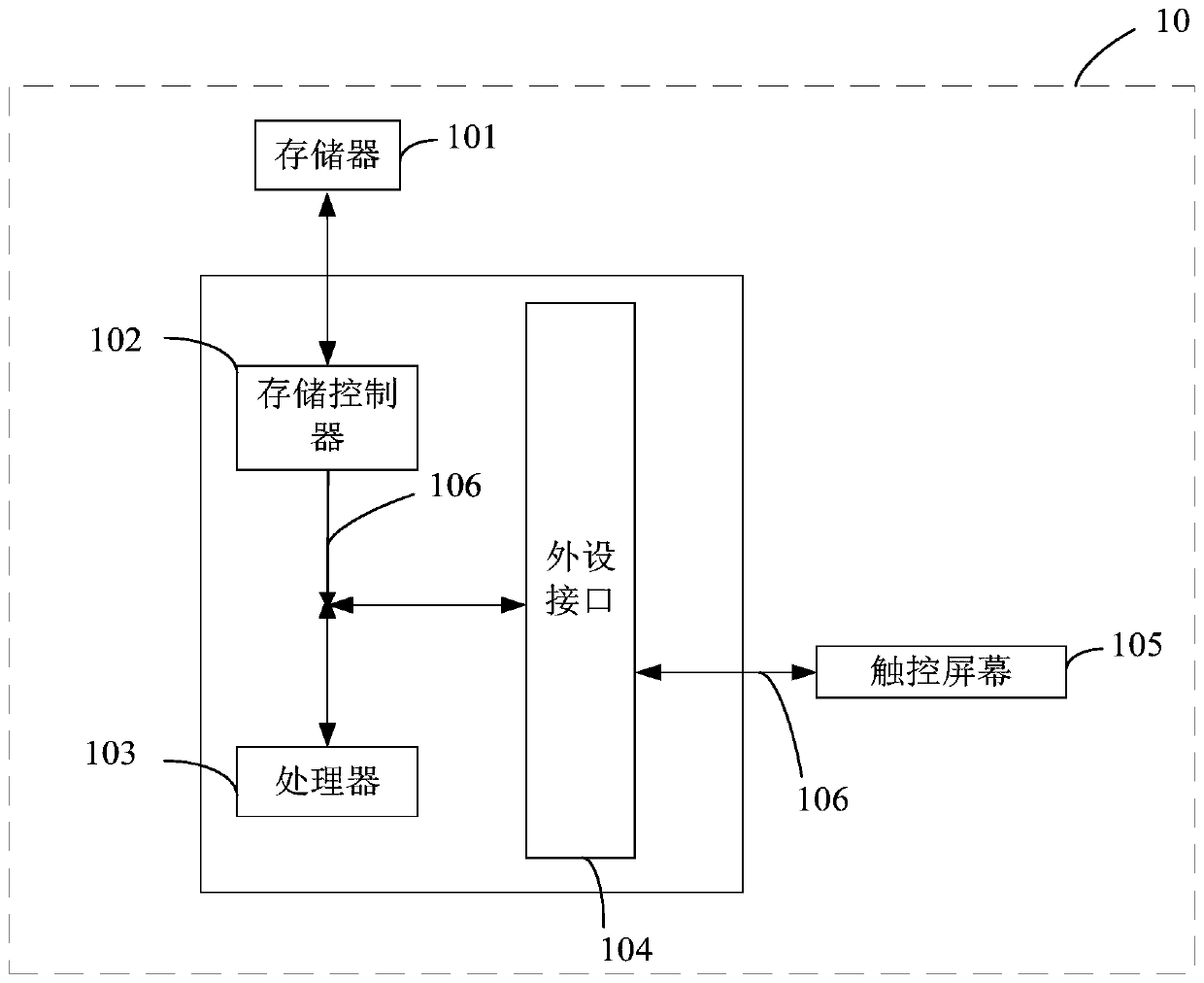
[0094] see Figure 4 , Figure 4 It is an electronic device provided by the third embodiment of the present invention. The electronics can be used to implement figure 2 The data desensitization control method in the illustrated embodiment. like Figure 4 As shown, the electronic device mainly includes:
[0095] A memory 401 , a processor 402 , a bus 403 and computer programs stored in the memory 401 and operable on the processor 402 . The memory 401 and the processor 402 are connected through the bus 403 . When the processor 402 executes the computer program, it realizes figure 2 The data desensitization control method in the illustrated embodiment. Wherein, the number of processors may be one or more, which is not limited in this embodiment.
[0096] The memory 401 may be a high-speed random access memory (RAM, Random Access Memory) memory, or a non-volatile memory (non-volatile memory), such as a disk memory. The memory 401 is used to store executable program eleme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com