Risk identification method and device for transaction data
A transaction data and risk identification technology, applied in the Internet field, can solve the problems of low identification rate, low efficiency, single data analysis model, etc., and achieve the effect of improving risk identification efficiency, accuracy and data diversification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0098] In the following description, numerous specific details are set forth in order to facilitate a thorough understanding of this specification. However, this manual can
[0099] The terminology used in one or more embodiments of this specification is for the purpose of describing the particular embodiment only,
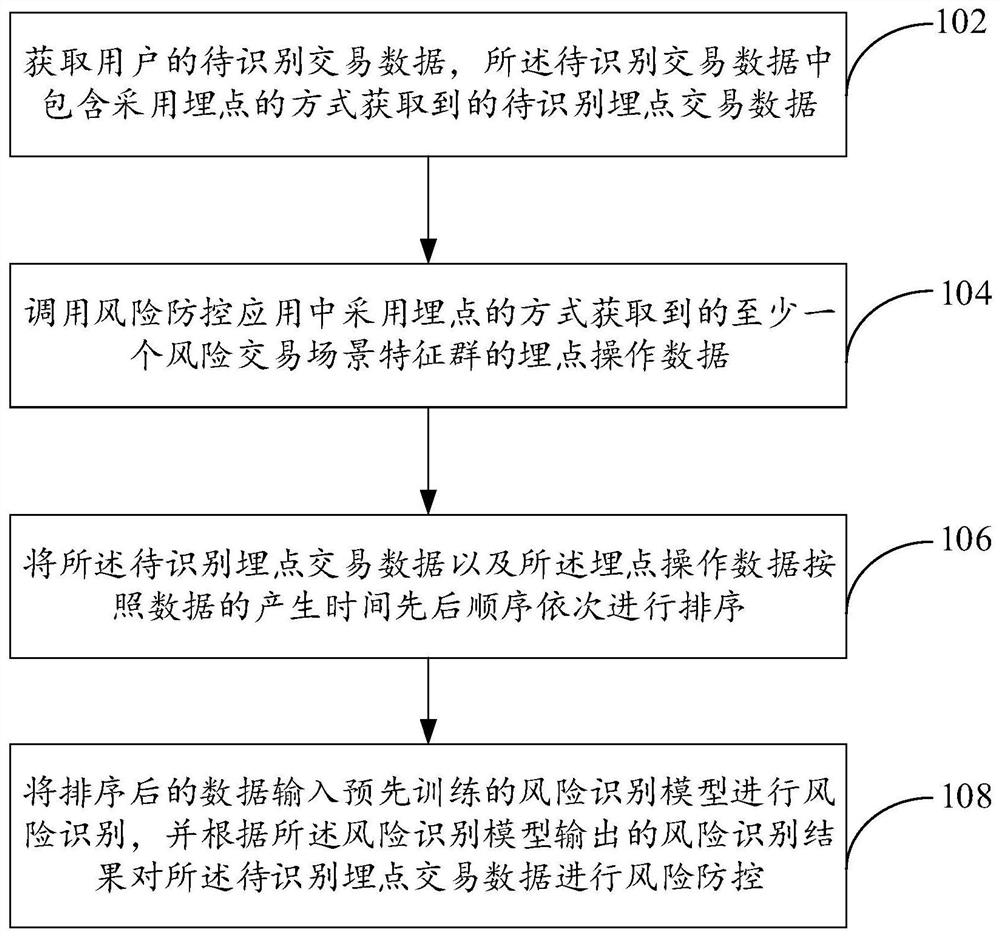
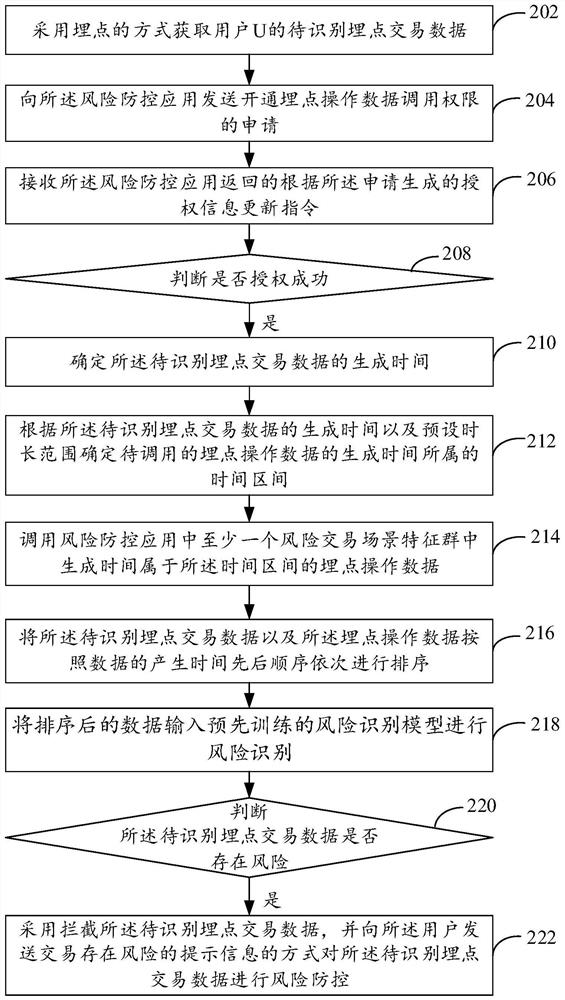
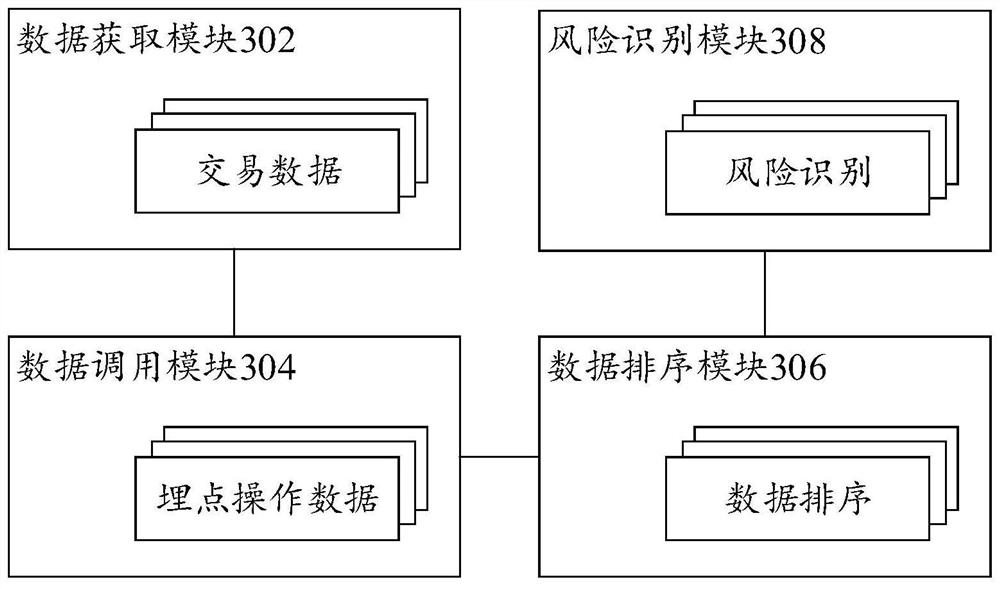
[0102] FIG. 1 shows the flow of a method for risk identification of transaction data provided according to an embodiment of the present specification
[0104] The risk identification method of the transaction data in the embodiment of this specification is applied to a payment application, by applying the payment application
[0113] Determine the risk transaction scenario feature involved in the historical transaction data according to the risk labeling result;
[0115] The risk transaction scenario feature of accounting for greater than the preset ratio threshold is determined as the target risk transaction scenario feature.
[0118] In an embodiment provided in thi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com