A risk identification method, device and system
A risk identification and risk technology, applied in the computer field, can solve the problems of real-time requirements and low efficiency of business completion, and achieve the effect of improving risk identification efficiency and completion efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] In order to solve the problem that using the risk identification method in the prior art will result in low completion efficiency of services with high real-time requirements, an embodiment of the present application provides a risk identification method. The subject of execution of the method may be a server, a risk control system, or any device capable of executing the method. The execution subject does not constitute a limitation of the present application. For the convenience of description, the embodiments of the present application are described by taking the execution subject as a risk control system as an example.
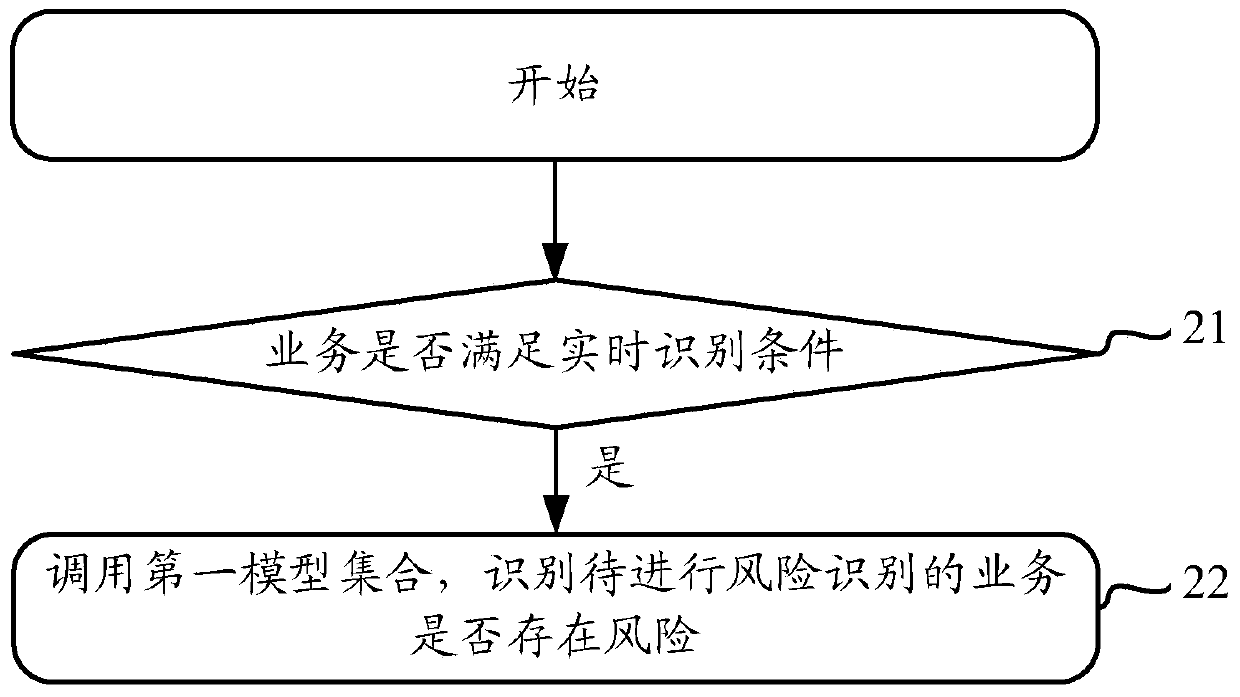
[0035] Specifically, the specific implementation flow chart of the method is as follows figure 2 shown, including the following steps:
[0036] Step 21, the risk control system judges whether the business to be risk identified meets the real-time identification conditions; if the judgment result is yes, execute step 22;
[0037] In the embodiment ...
Embodiment 2
[0079] Based on the same inventive idea as Embodiment 1 of the present application, Embodiment 2 provides a risk identification system to solve the problem of using the risk identification method in the prior art, which will lead to low efficiency in completing businesses with high real-time requirements. The problem.
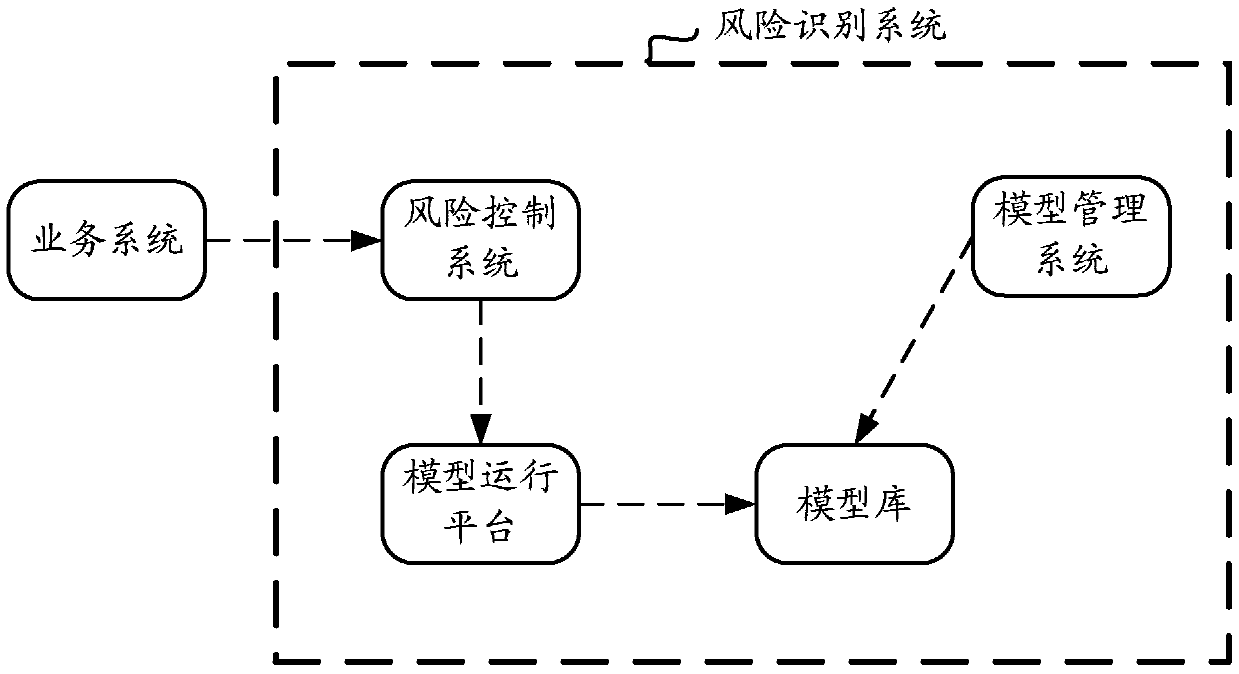
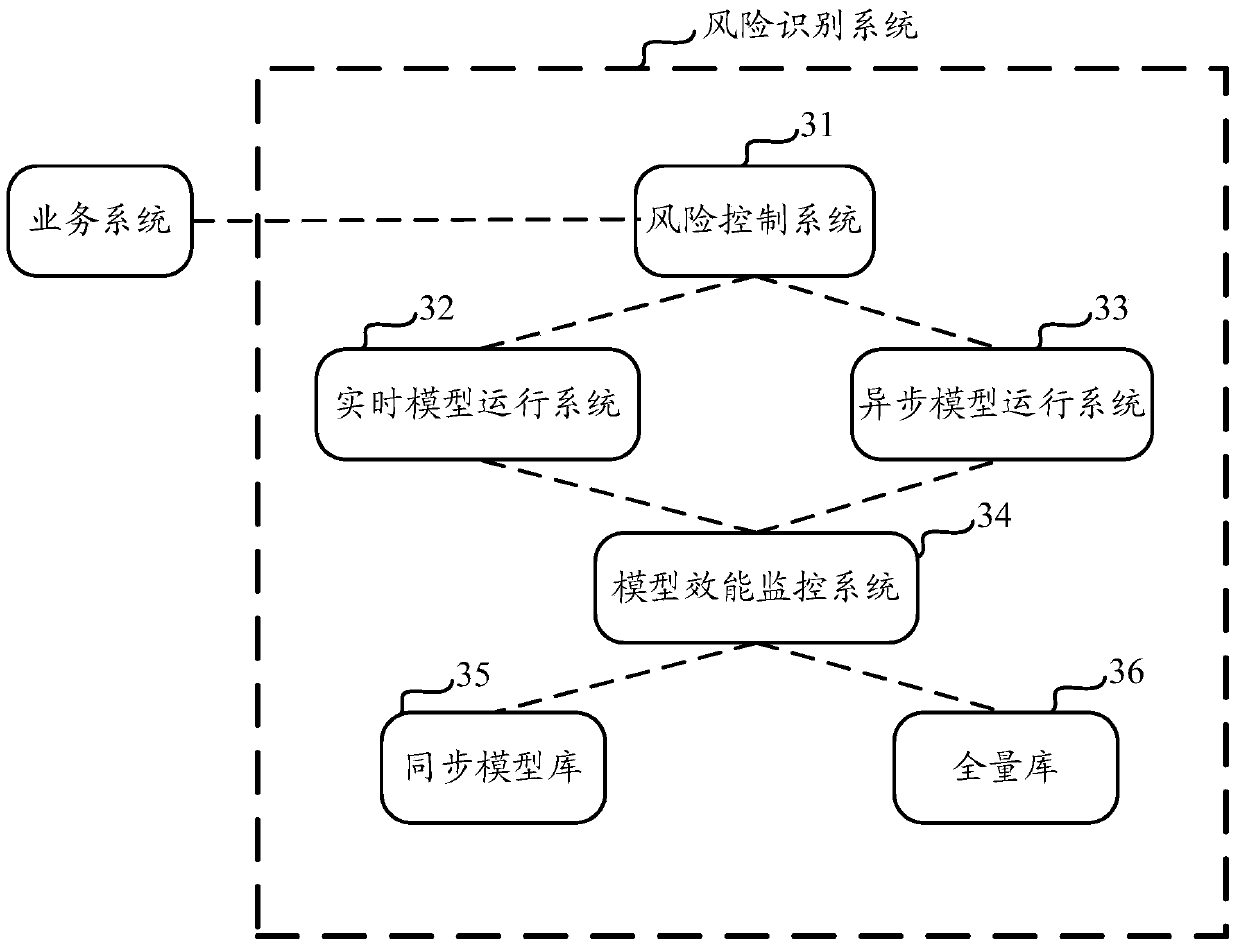
[0080] The schematic structural diagram of the risk identification system provided in Embodiment 2 is as follows image 3 As shown, it includes a risk control system 31 , a real-time model running system 32 , an asynchronous model running system 33 , a model performance monitoring system 34 , a synchronous model library 35 and a full library 36 . The main function of the risk identification system is to respond to image 3 Consultation on the business system in the business system, and feedback the risk consultation results to the business system. Wherein, the function of the service system is similar to that of the service system in the prior art, and will n...
Embodiment 3
[0093] In order to solve the problem that using the risk identification method in the prior art will result in low completion efficiency of services with high real-time requirements, Embodiment 3 of the present application provides a risk identification device. The specific structural diagram of the device is shown in Figure 4 As shown, it mainly includes the following functional units:
[0094] The judging unit 41 is configured to judge whether the business to be risk identified satisfies the real-time identification condition.
[0095] The real-time identification condition is used to distinguish services with higher real-time requirements for completing services from services with lower real-time requirements.
[0096] The model calling unit 42 is configured to call the risk identification model in the first model set when the judgment result obtained by the judging unit 41 is yes, to identify whether the business is at risk.
[0097] Wherein, the risk identification mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com