Implicit channel detection method between Android applications based on semantic graph of intent communication behavior
A detection method and inter-application technology, applied in the field of mobile platform information security, can solve single and other problems, and achieve the effects of increasing training samples, strong practicability, and small feature dimensions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
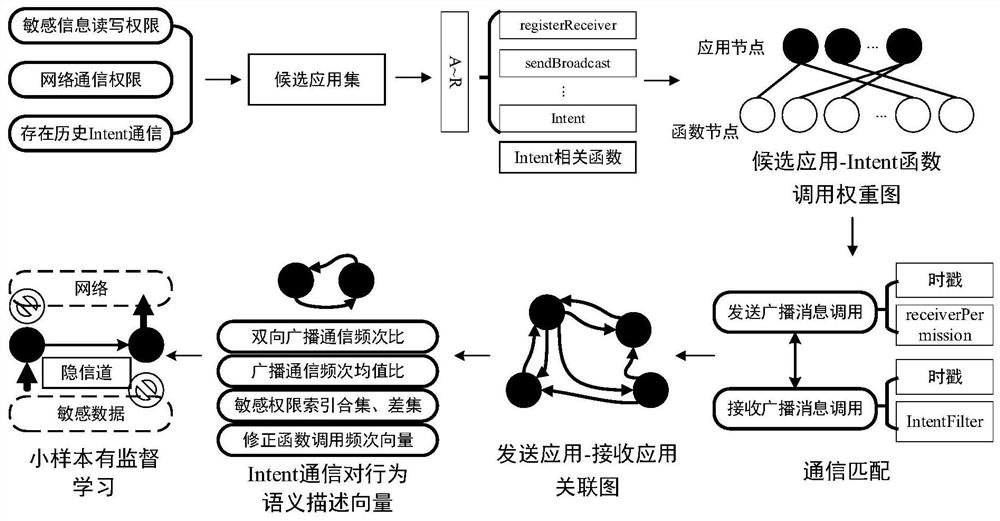
[0014] combine figure 1 , the present invention is based on the Android inter-application hidden channel detection method of Intent communication behavior semantic map, comprising the following steps:
[0015] Step 1. Screening suspicious candidate applications: Screening suspicious candidate application sets from the target Android platform according to the read and write permissions of sensitive information, network communication permissions and whether there is historical Intent communication;
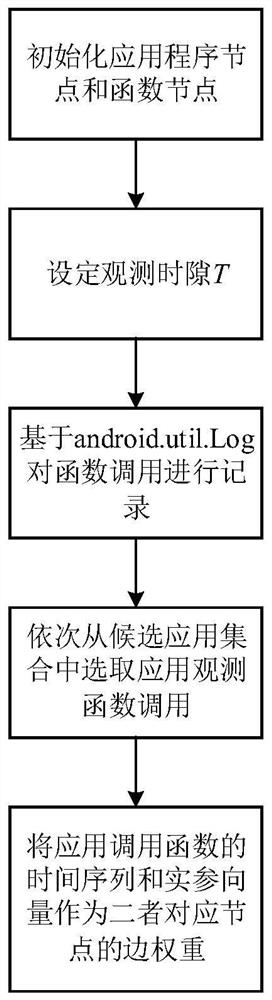
[0016] Step 2. Build a candidate application-Intent function call weight map: obtain Intent communication events by monitoring Intent-related functions to build a candidate application-Intent function call weight map;
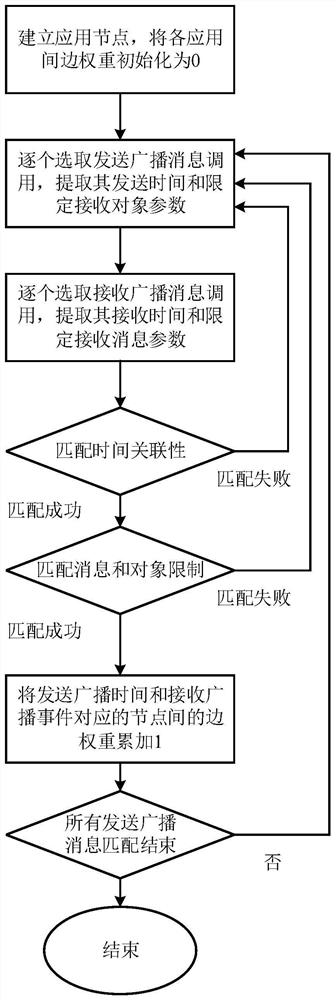
[0017] Step 3, establishing a sending application-receiving application association graph: performing relationship matching between the sending broadcast message calling behavior and the receiving broadcast message calling behavior, and establishing a sending applica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com