An attack detection method and system for sdn network
An attack detection and network technology, applied in the field of network security, which can solve problems such as being vulnerable to man-in-the-middle attacks and not forcing the establishment of TLS secure channels.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings to be more readily understood by those skilled in the art, so as will be more clearly defined by those skilled in the art.
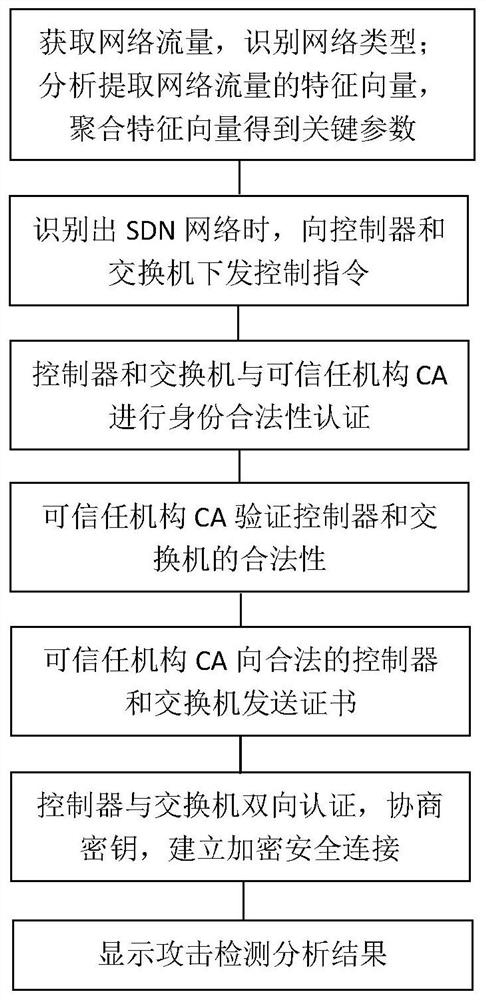
[0045] figure 1 A flowchart of an attack detection method of an SDN network provided herein, the method includes:
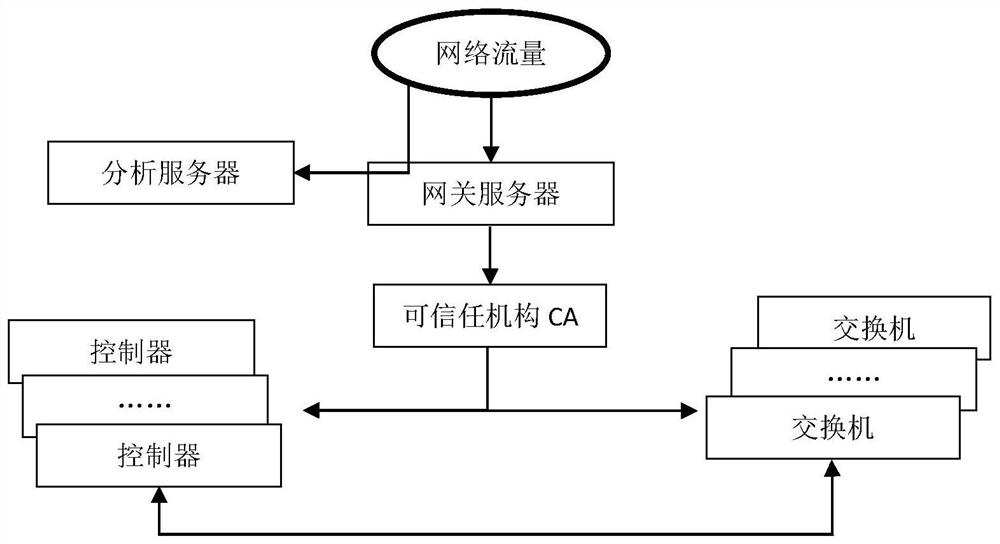
[0046] Get network traffic data, according to network features, identify the type of network;
[0047] Use the OpenFlow protocol to collect traffic statistics, analyze the feature vectors in network traffic data, polymerize the transmission rate, packet transmission rate, data transmission rate, data packet mean, duration standard, data packet by the feature vector One or several types of standard deviation, one-way flow table ratio;
[0048] The transmission rate, data packet transmission rate, data transmission rate, data packet mean, duration standard, poor data packet standard, poor data packet standard, p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com