Attack defense method and system for flow self-adaptive scheduling
An adaptive, traffic-based technology, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as the blockage of the security channel between the controller and the attacked switch, the inability of users to access the attacked host, and serious consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, so as to define the protection scope of the present invention more clearly.
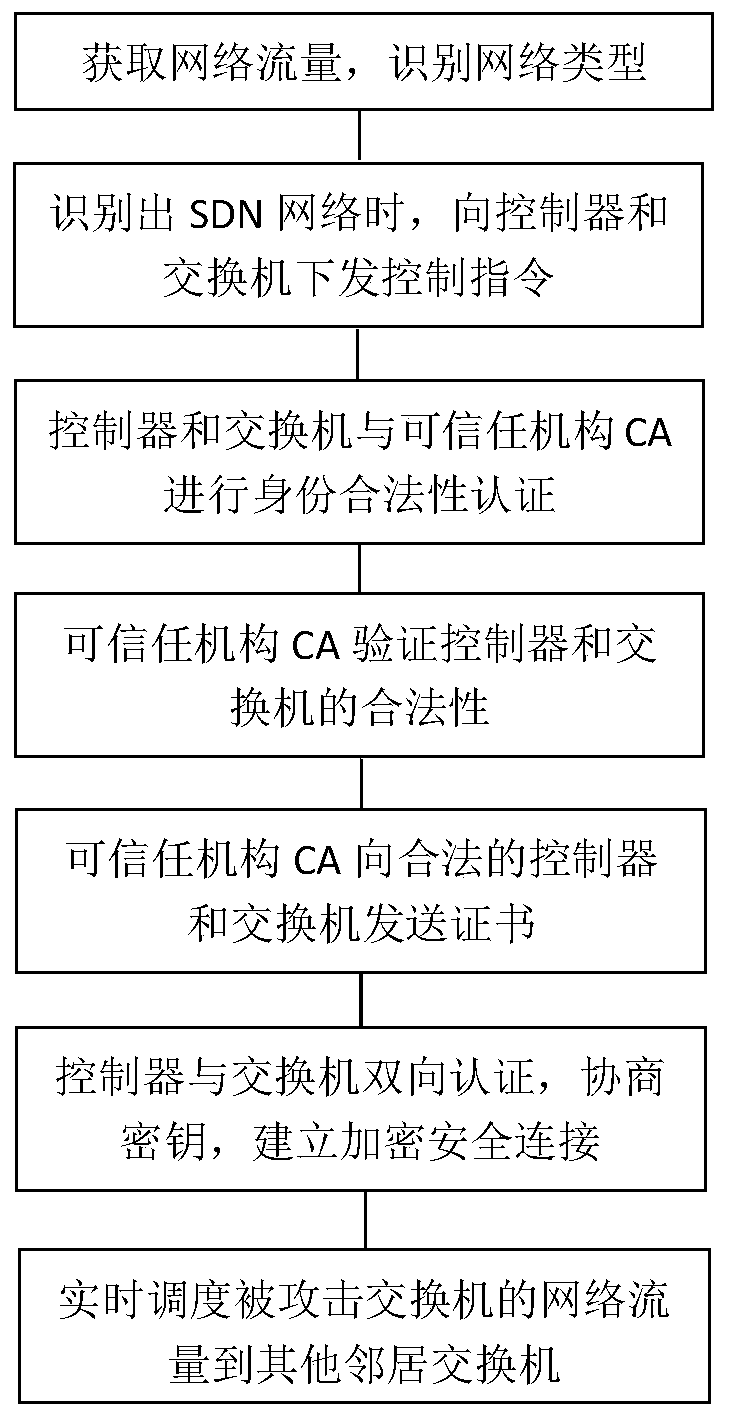
[0047] figure 1 It is a flow chart of the attack defense method for traffic adaptive scheduling provided by this application, and the method includes:
[0048] Obtain network traffic data and identify network types based on network characteristics;
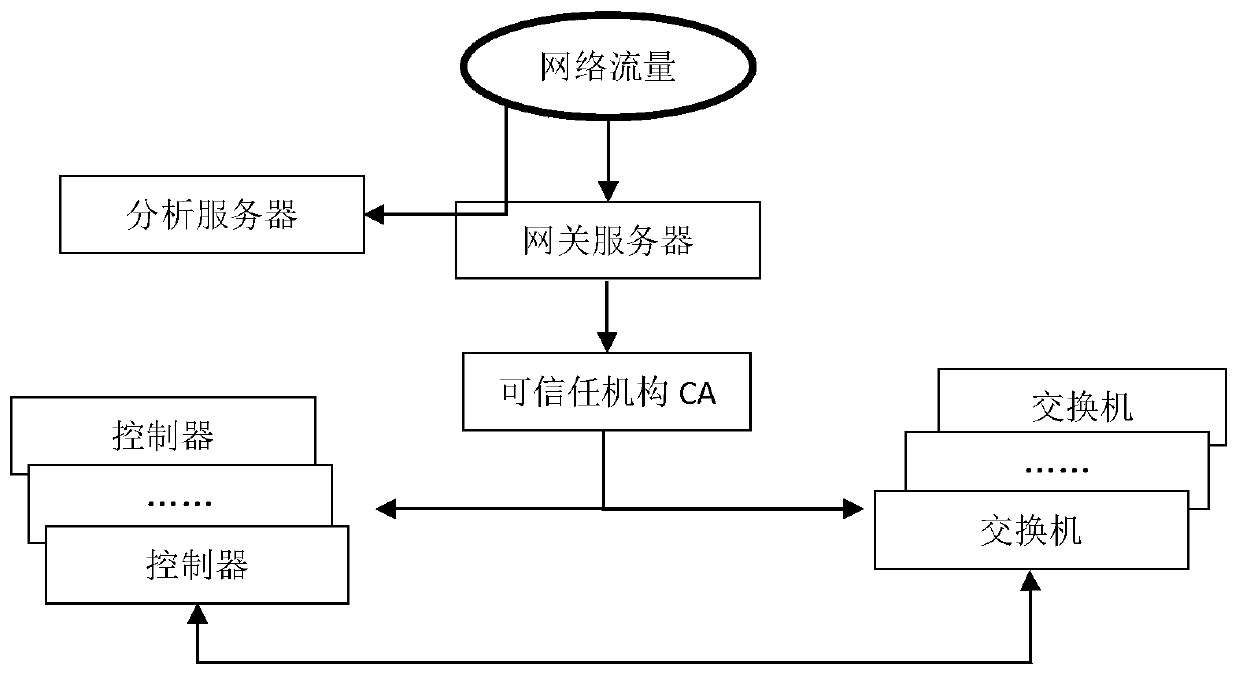
[0049] When the network is identified as an SDN network, a control command is sent to the controller and the switch, and the control command carries the identification and address of the trusted agency CA in the middle of the network;
[0050] The controller and the switch receive the control instruction, and respectively send an identity authentication request to the network intermediate trusted in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com