Safe clustering method and device based on wireless sensor network
A wireless sensor and clustering technology, which is applied in the computer field, can solve the problems of node attacks and the inability to guarantee the communication security of sensor nodes, and achieve the effects of preventing masquerade attacks, facilitating deployment, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
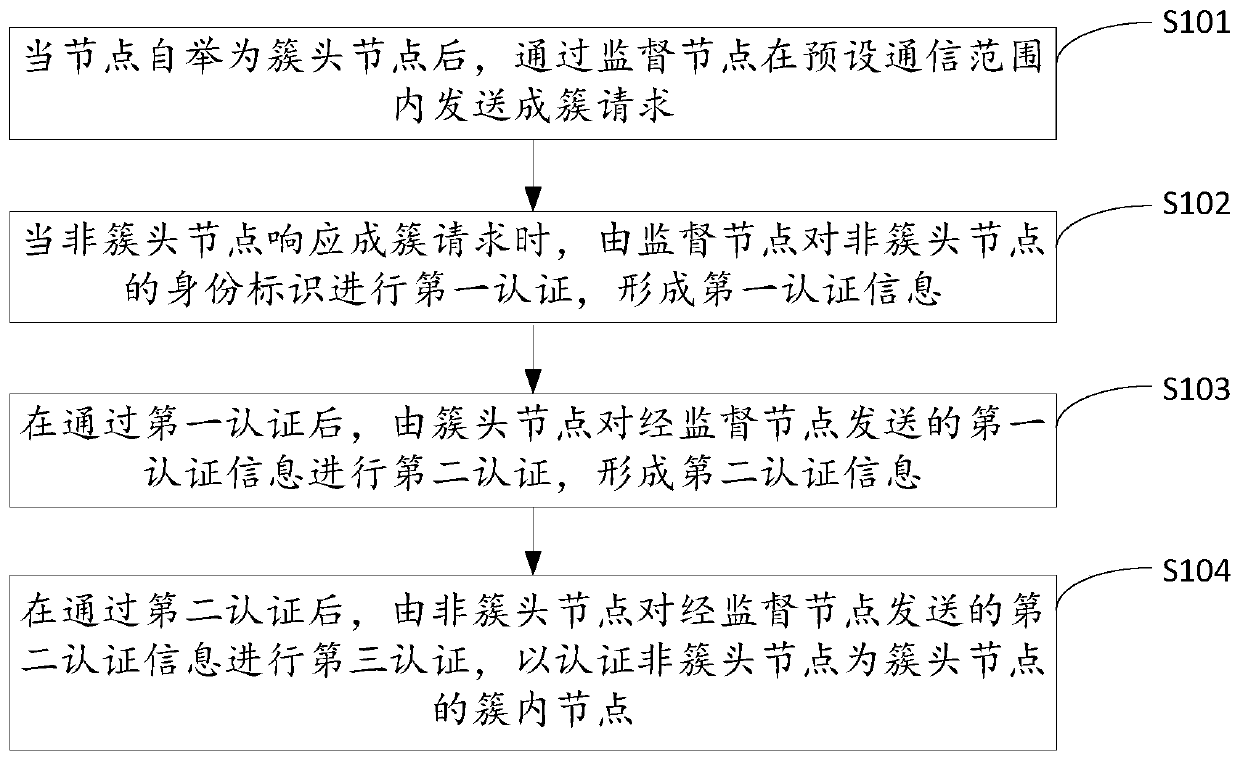
[0027] figure 1 It shows the implementation flowchart of the secure clustering method based on the wireless sensor network provided by Embodiment 1 of the present invention. For the convenience of description, only the parts related to the embodiment of the present invention are shown, and the details are as follows:
[0028] In step S101, after a node is bootstrapped as a cluster head node, a clustering request is sent through a supervisory node within a preset communication range.
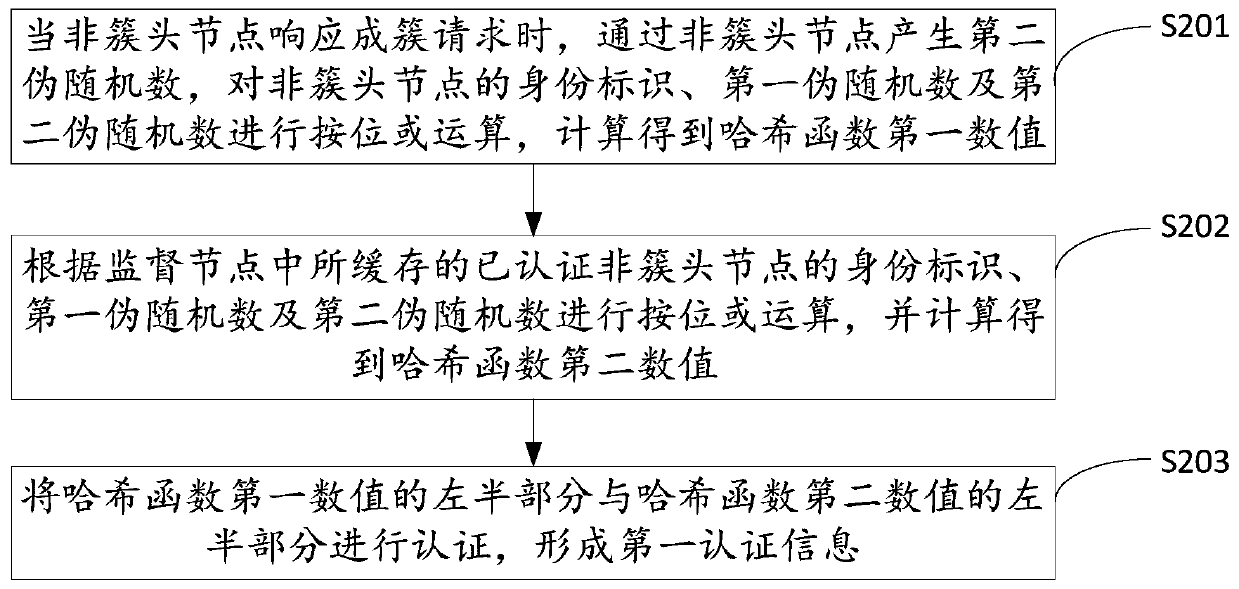
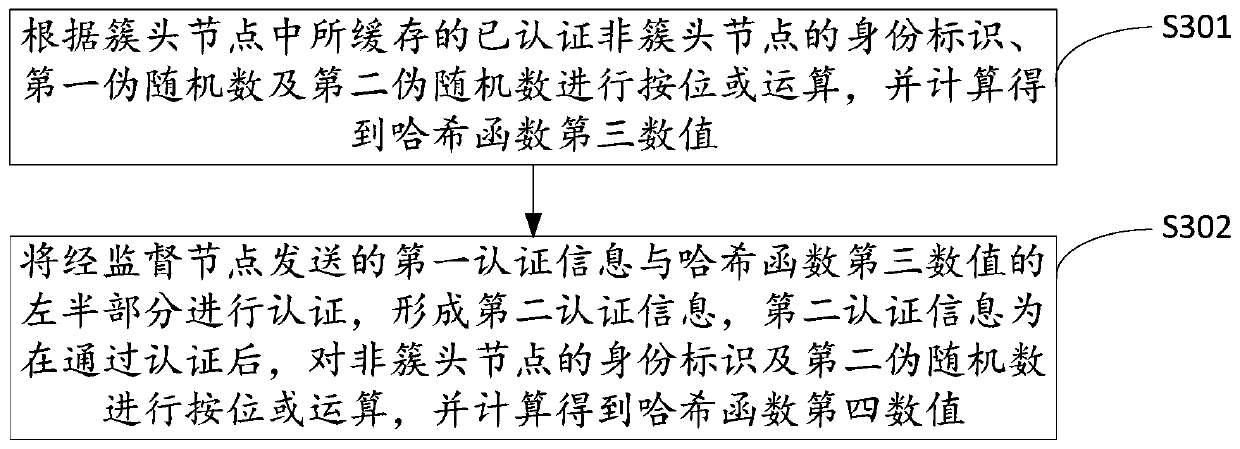
[0029] In the embodiment of the present invention, when a node in the wireless sensor network is bootstrapped as a cluster head node, the cluster head node broadcasts a clustering request to non-cluster head nodes within the preset communication range, and the clustering request is sent via The supervisory node sends to the non-cluster head node within the preset communication range to invite the non-cluster head node within the preset communication range to become the intra-cluster node of the c...
Embodiment 2
[0055] Figure 5 A schematic structural diagram of a wireless sensor network-based security clustering device provided by Embodiment 2 of the present invention is shown. For convenience of description, only parts related to the embodiment of the present invention are shown. In the embodiment of the present invention, the secure clustering device based on the wireless sensor network includes: a clustering request sending unit 51, a first authentication unit 52, a second authentication unit 53 and a third authentication unit 54, wherein:
[0056] The clustering request sending unit 51 is configured to send the clustering request through the supervisory node within the preset communication range after the node is bootstrapped as the cluster head node.
[0057] In the embodiment of the present invention, when a node in the wireless sensor network is bootstrapped as a cluster head node, the cluster head node broadcasts a clustering request to non-cluster head nodes within the prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com