Authentication method for Internet protocol multimedia service sub-system
A multimedia service and Internet protocol technology, applied in the field of Internet protocol multimedia service subsystem, can solve problems such as poor maintainability, and achieve the effects of small impact, prevention of NBA camouflage attacks, and avoidance of security loopholes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
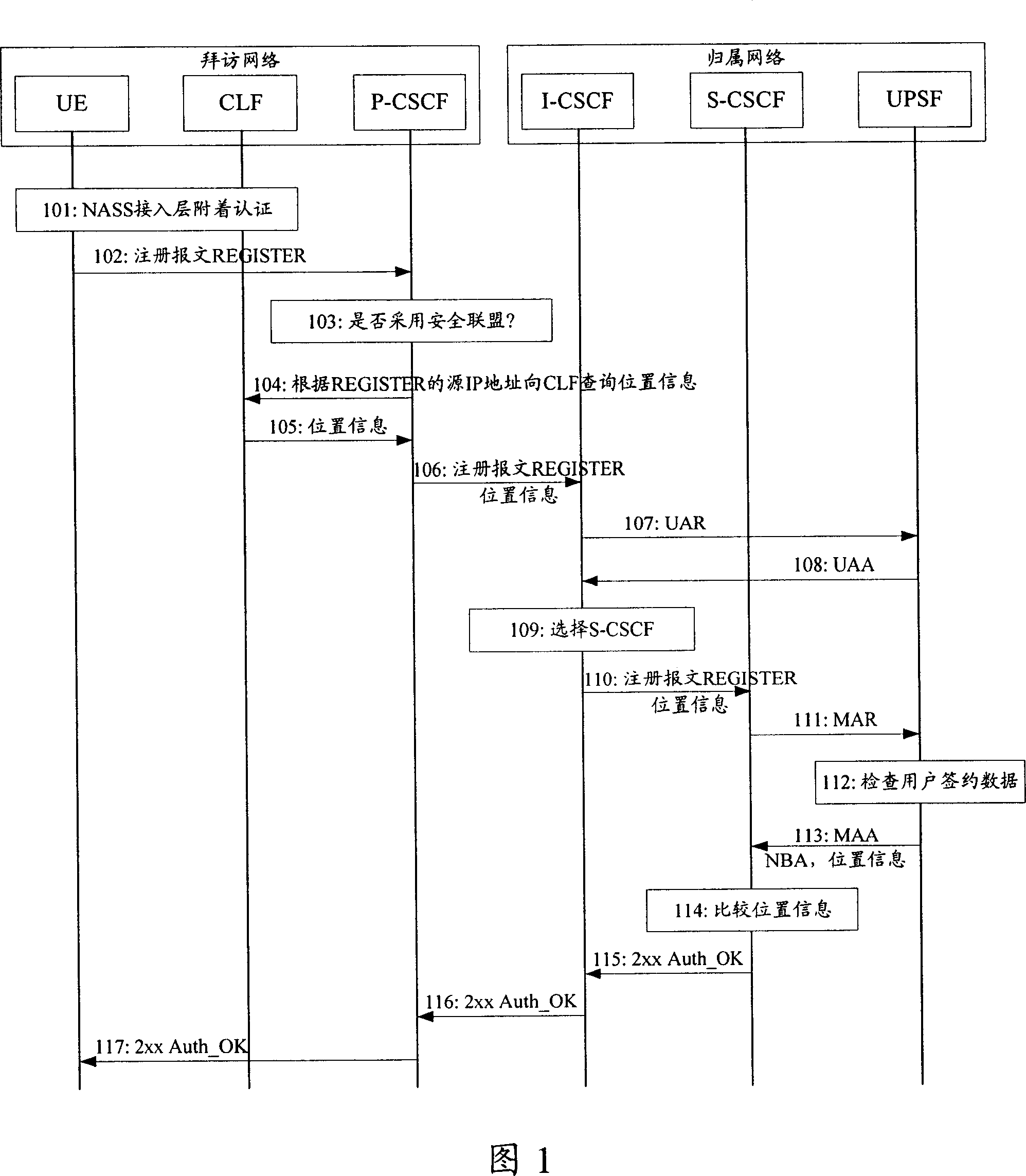
[0060] Referring to Fig. 2, the first embodiment of the present invention comprises the following steps:
[0061] Step 1101, NASS access layer attach authentication, record the corresponding relationship between the UE's IP address and location information on the CLF.
[0062] Step 1102, the UE sends a REGISTER message to the P-CSCF.
[0063] In step 1103, the P-CSCF judges whether it needs to establish a security association with the UE by checking whether the REGISTER message contains security negotiation parameters, such as Security-Client. There is no such parameter in the NBA authentication mode, so there is no need to establish a security association.
[0064] Step 1104, the P-CSCF queries the location information of the UE in the CLF according to the source IP address of the registration message.
[0065] Step 1105, since the location information corresponding to the source IP address is stored in the CLF in advance, so in this step, the CLF returns the corresponding ...
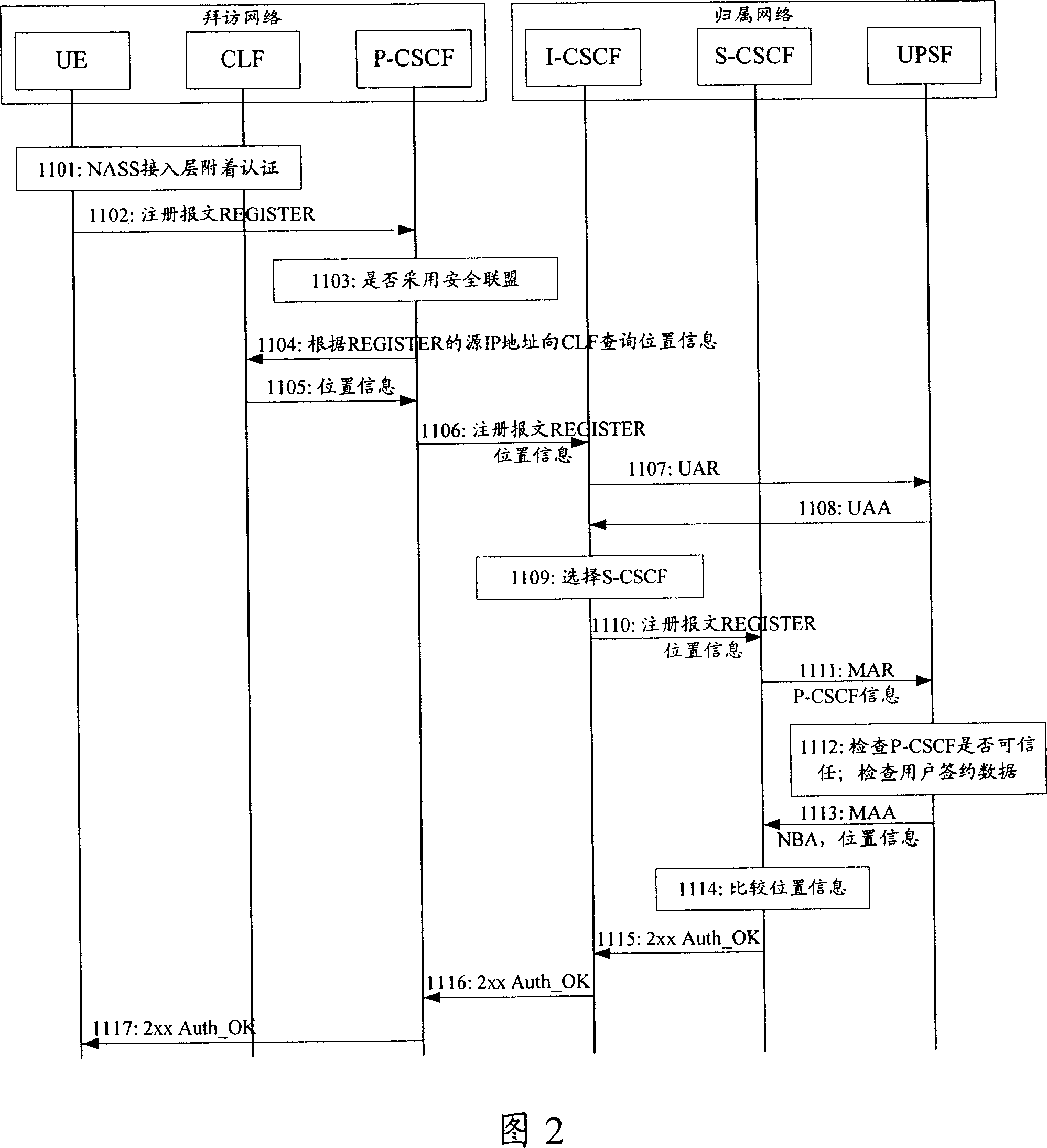
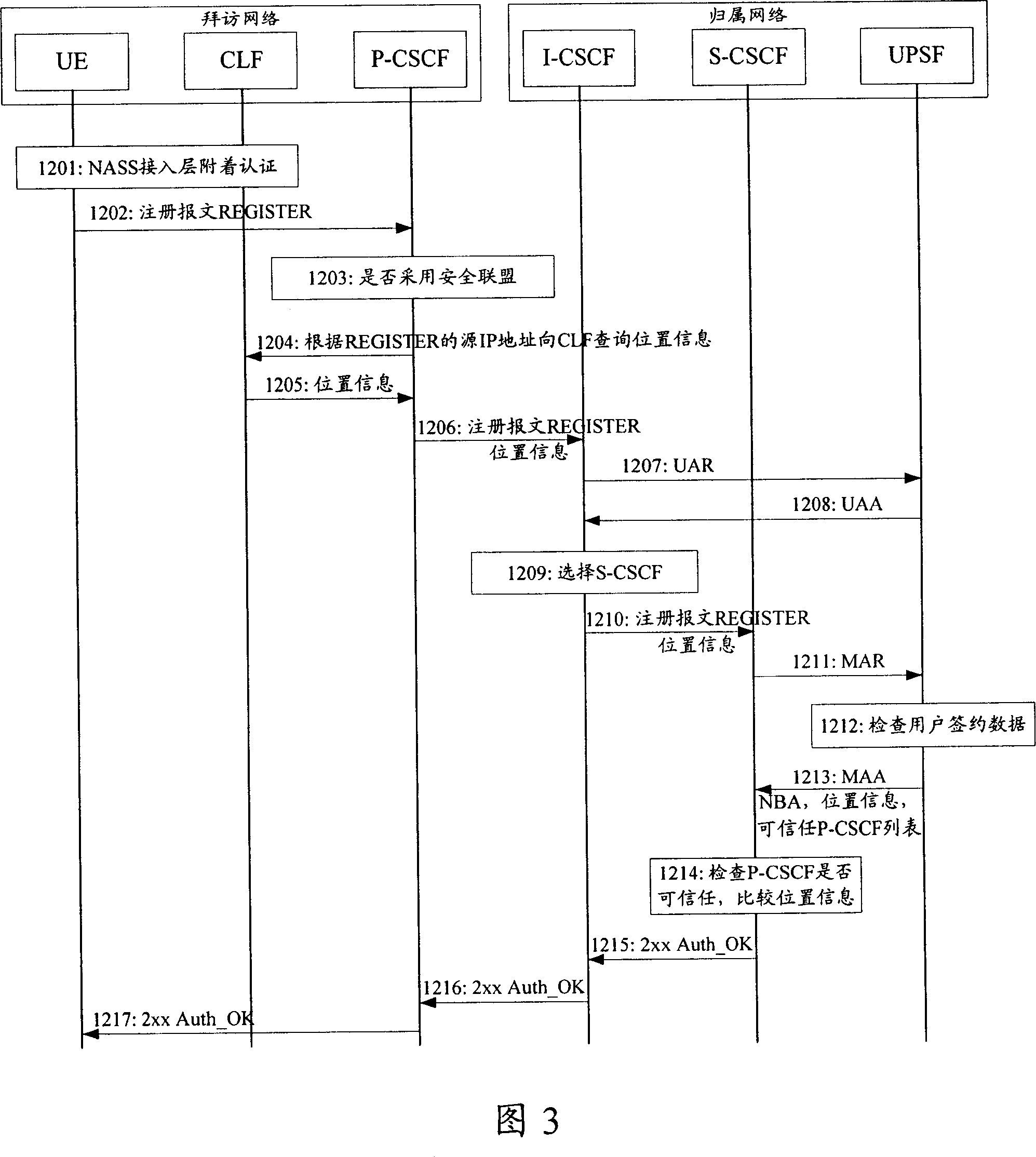
no. 4 example
[0119] Referring to Fig. 5, the fourth embodiment of the present invention comprises the following steps:
[0120] Step 1401, NASS access layer attach authentication, record the corresponding relationship between IP address and location information of UE on CLF.
[0121] Step 1402, the UE sends a REGISTER message to the P-CSCF.
[0122] In step 1403, the P-CSCF judges whether it needs to establish a security association with the UE by checking whether the REGISTER message contains security negotiation parameters, such as Security-Client. There is no such parameter in the NBA authentication mode, so there is no need to establish a security association.
[0123] Step 1404, the P-CSCF queries the location information of the UE in the CLF according to the source IP address of the registration message.
[0124] Step 1405, since the location information corresponding to the source IP address is stored in the CLF in advance, so in this step, the CLF returns the corresponding locati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com