Handshake negotiation method and system in safe grade
A security level, security protocol technology, applied in the field of mobile communication and information security, can solve the problems of increasing network security protocol parameters, security protocol signaling format restrictions, etc., to promote personalization, convenient billing, easy configuration and use. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] Below in conjunction with accompanying drawing, the implementation of technical scheme is described in further detail:
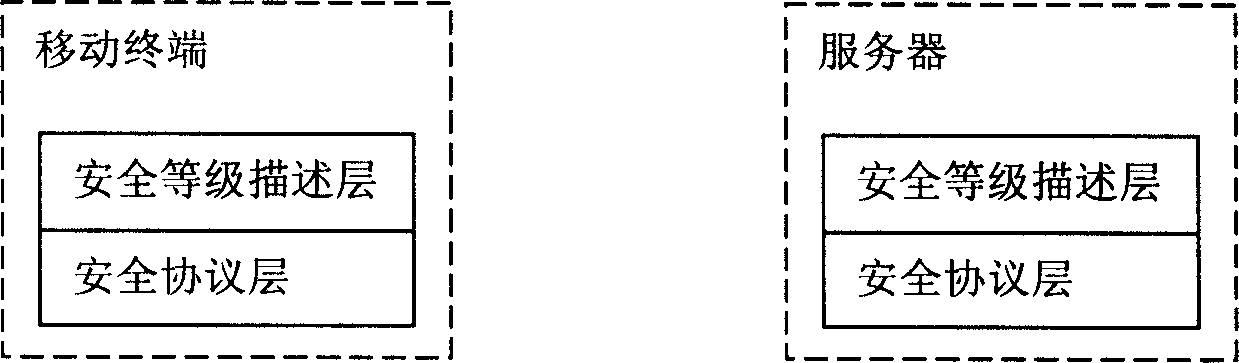
[0051] Add a security level description layer outside the security protocol layer, the rules are as follows figure 1 shown. The security protocol layer generally refers to the general term of security protocols that can be supported in mobile terminals and servers. It provides security technical support for the security level description layer. The functional entity of the security level description layer can divide the security level into n levels according to application requirements, where n is the level code. Each level of security level corresponds to specific protocol parameters to achieve a certain degree of security.
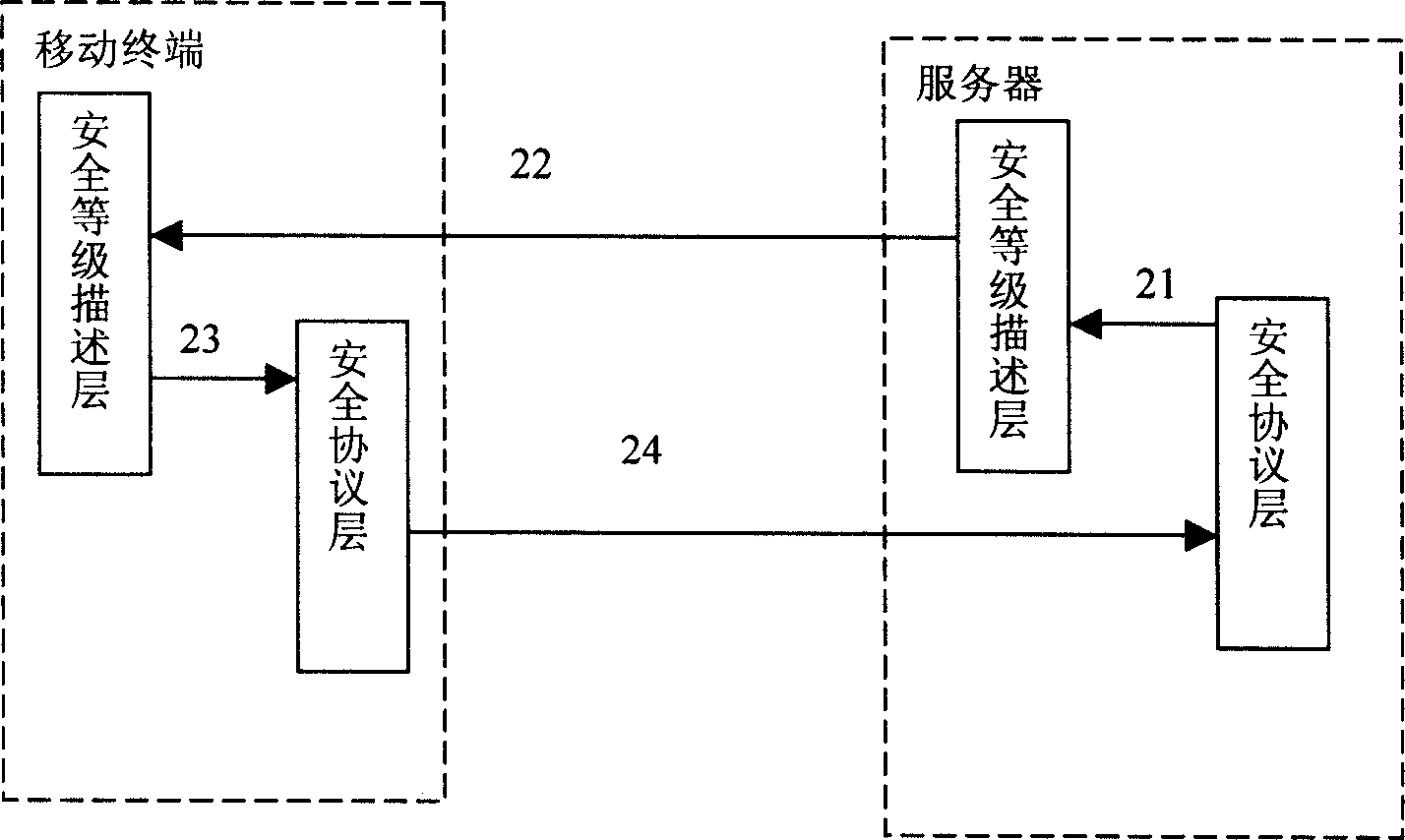
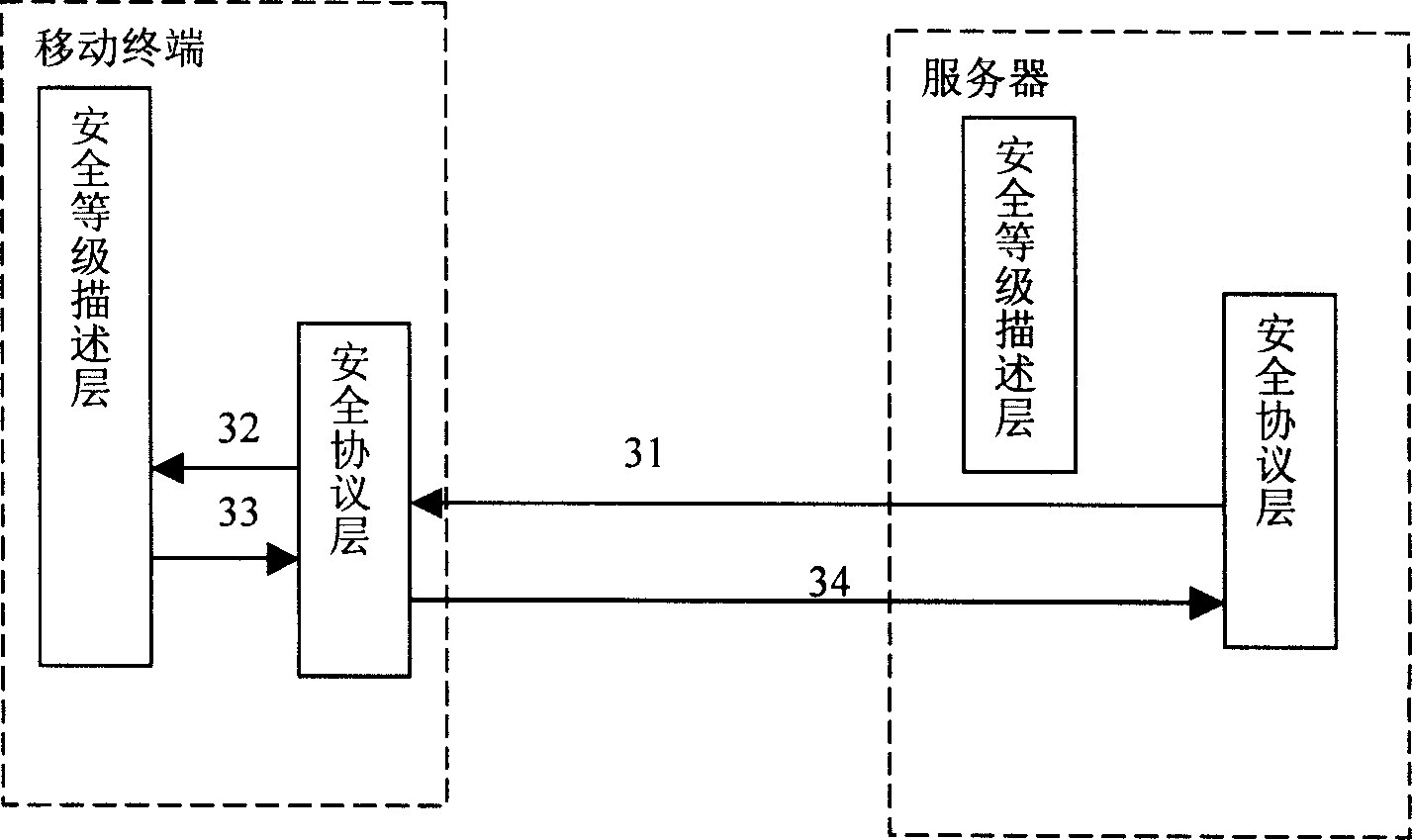
[0052] When the handshake signaling issued by the security protocol layer passes through the security level description layer, the security level description layer converts the protocol parameters into signaling with a level ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com