Secure transmission system for broadcast automatic monitoring information
A broadcast automatic and information security technology, applied in transmission systems, traffic control systems, aircraft traffic control and other directions, can solve the problems of no resistance to active attacks, no fixed objects, mutual authentication, etc., and achieve effective management and effective security authentication. , the effect of ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
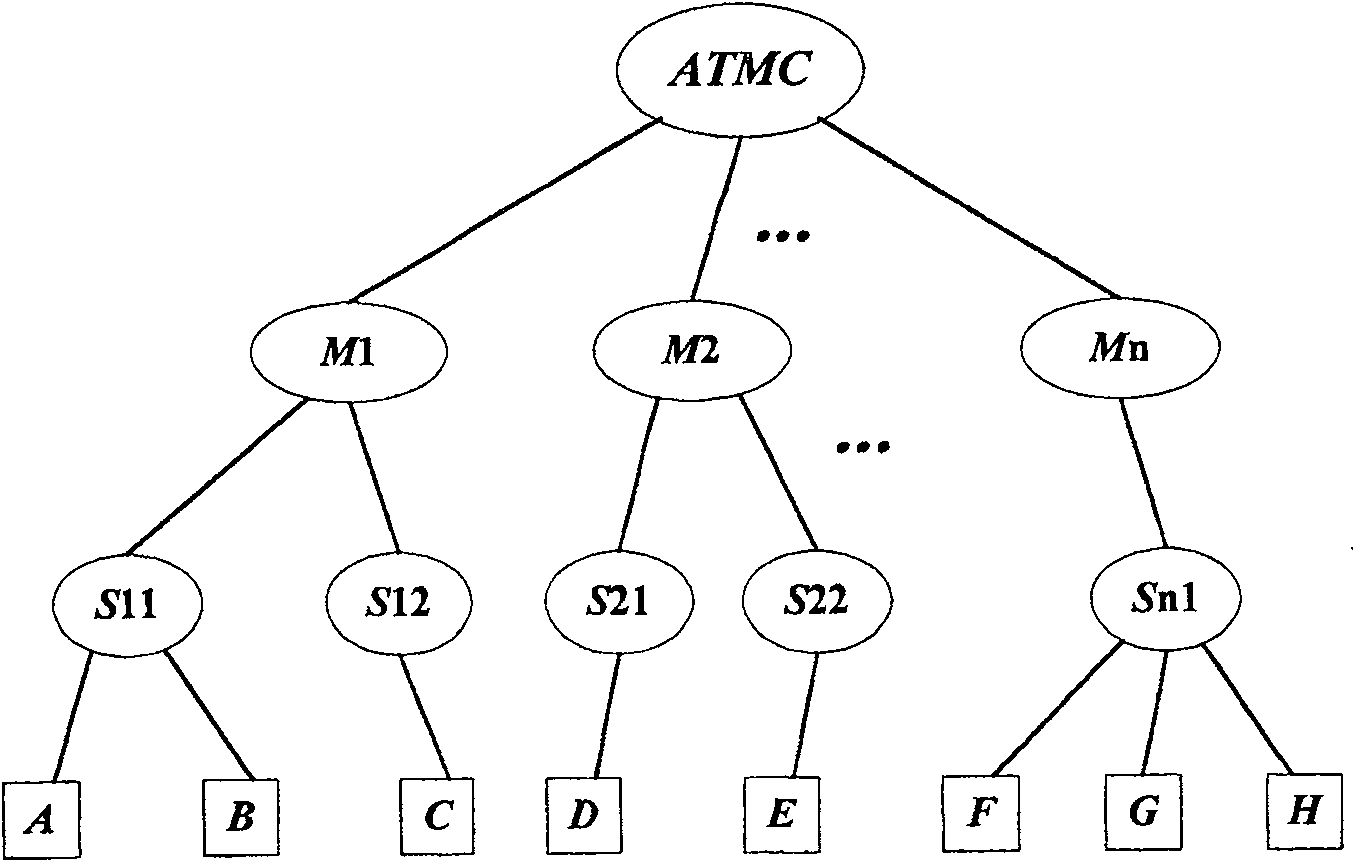
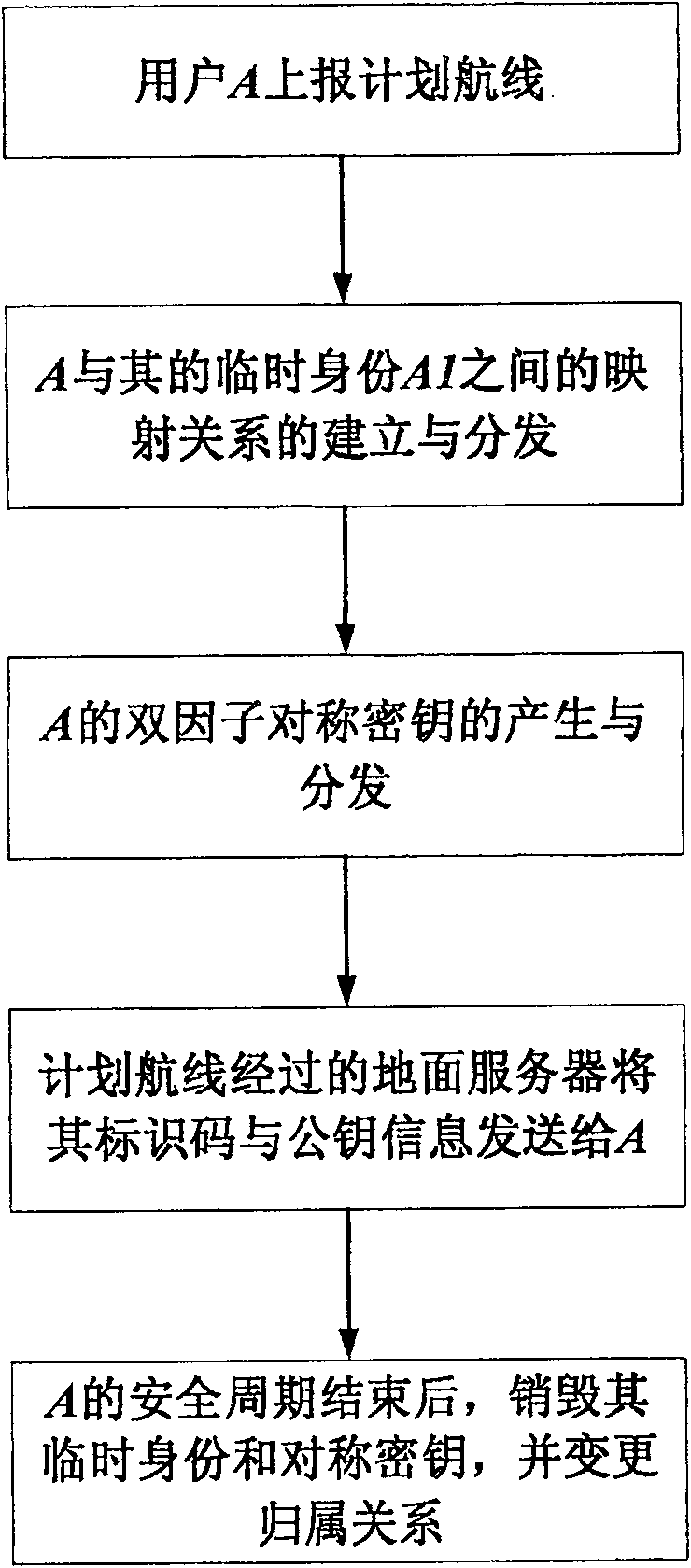
[0049] A reports the planned route at the beginning of the safety cycle, assuming it starts from S11, passes through S12, and ends at S21. Therefore, during this security period, A belongs to the user group managed by the starting point S11 and M1. User A's planned route is reported to the air traffic control center in the order of S11→M1→ATMC.
[0050] ATMC assigns a temporary identity A1 to A, and establishes a mapping from A1 to A; ATMC sends this mapping relationship to M1, M2; M1 sends it to S11, S12; M2 sends it to S21.
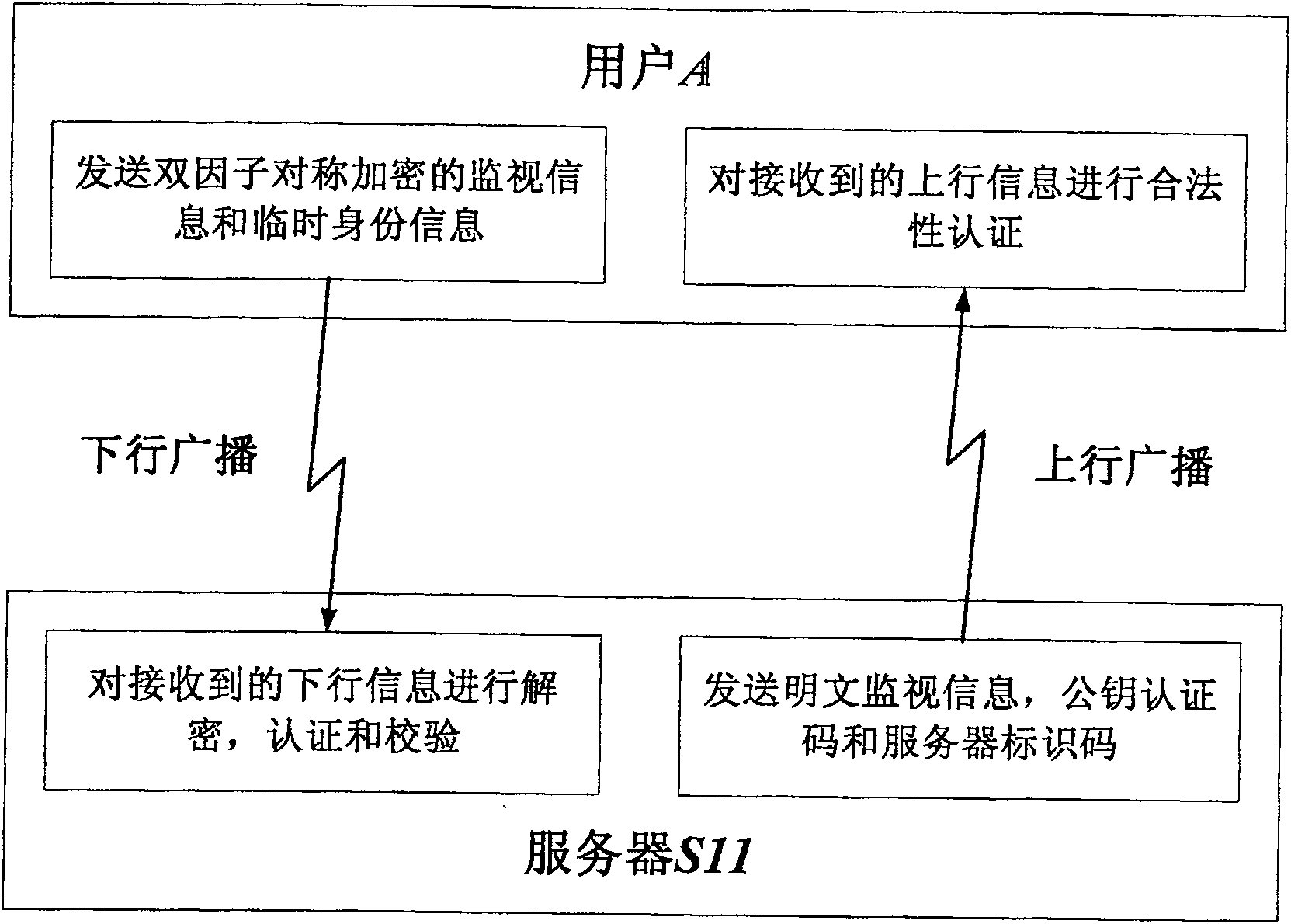
[0051] S11 generates a random number as the shared key K11, calculates the encryption factor N11=y11(K11), and then sends {A1, K11} and N11 to A through a secret channel before taking off; and passes through S11→M1→S12 and S11 respectively The order of →M1→ATMC→M2→S21 sends {A1, K11} and N11 to the control area S12, S21 server that A's planned route will pass through.
[0052] S11 directly assigns the server identification code S11 and the public key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com