Method and system for deploying third-party application to microcontroller by edge assistance
A technology of microcontrollers and edge servers, applied in software deployment, program control design, instruments, etc., can solve the problems of consuming large network bandwidth and exacerbation, so as to reduce software complexity and development burden, reduce usage, and increase code The effect of execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
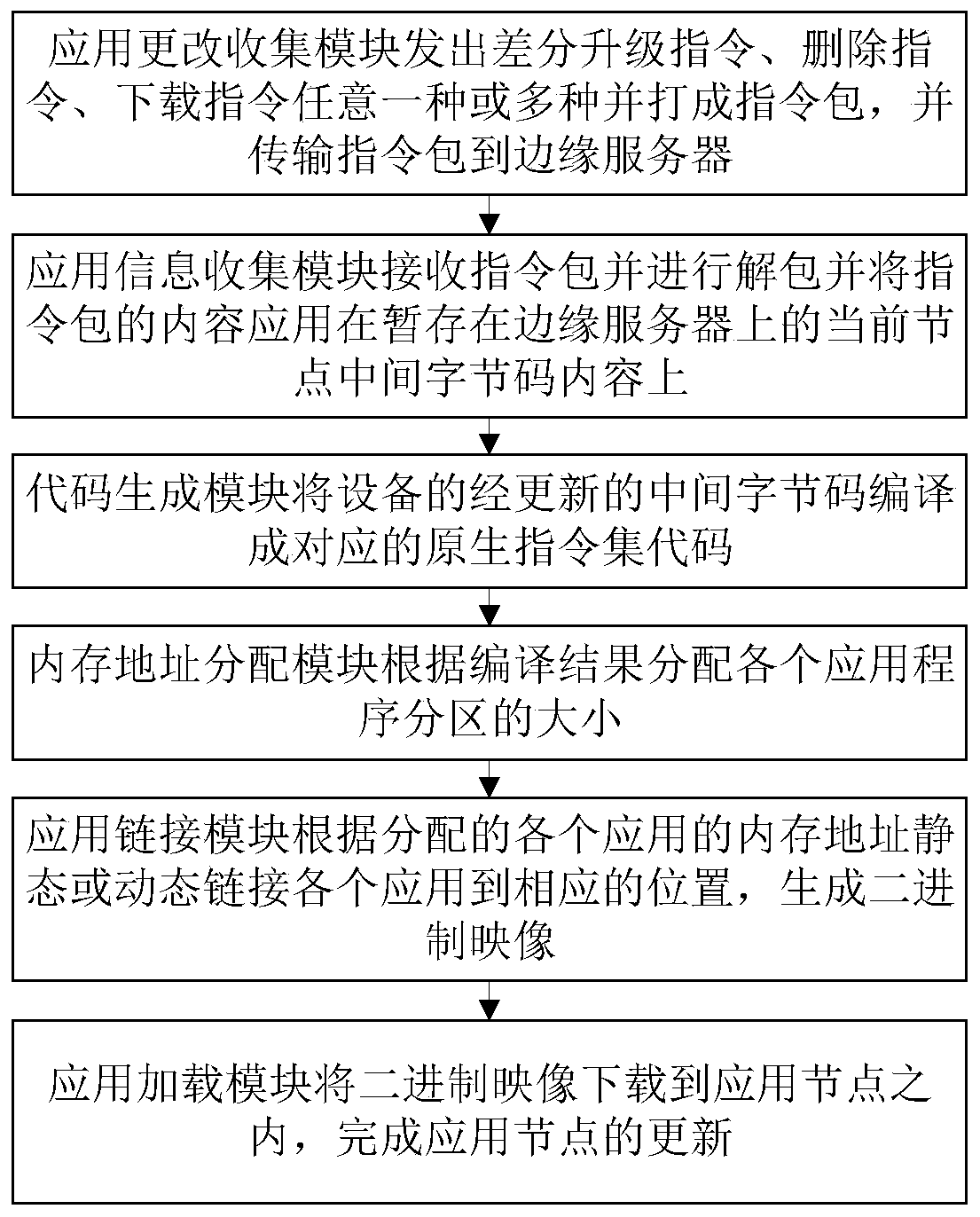
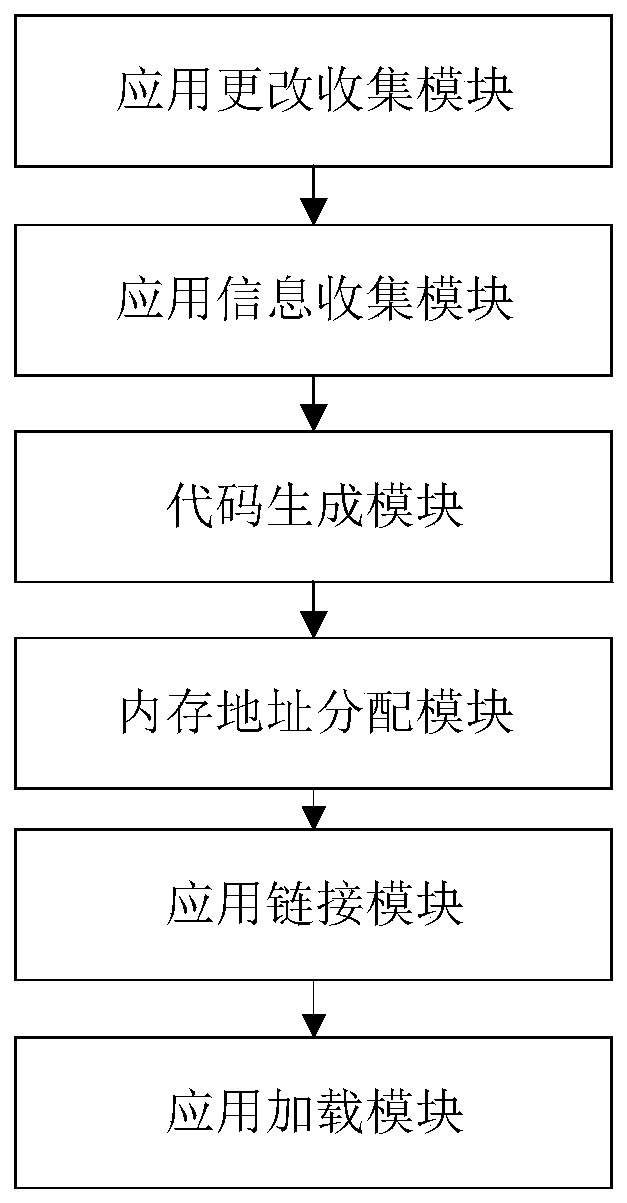
[0052] (1) When the user starts to deploy the three application programs A, B, and C to the IoT node, and sends the instruction to the application change collection module located on the development machine.
[0053] (2) The application change collection module receives the above instructions, and generates the download instructions Ad, Bd and Cd of the three application programs. These download instructions contain the intermediate bytecodes Ai, Bi and Ci of the three application programs of A, B and C respectively.
[0054] (3) The edge server receives Ad, Bd and Cd. Since the current IoT node is empty, the intermediate bytecode state of the temporary node is empty. At this point, the edge server updates the temporarily stored intermediate bytecode states to Ai, Bi, and Ci.
[0055] (4) The edge server compiles Ai, Bi, Ci into local codes Ac, Bc, and Cc that can be executed on the microcontroller through the code generation module.
[0056] (5) The edge server allocates a...
Embodiment 2
[0059] (7) When the user adds application D to the IoT node, and updates the version of C to C2, remove application B at the same time.
[0060] (8) The application change collection module obtains the above instructions, and generates the download instruction Dd of the application program D, the differential upgrade instruction Cu of the application program C, and the delete instruction Br of the application program B. Dd contains the intermediate bytecode Di of D, Cu contains those parts of C2's intermediate bytecode C2i that differ from Ci, and Br contains nothing but delete instructions.
[0061] (9) The edge server receives Dd, Cu and Br. Due to the currently temporarily stored intermediate bytecode state bits Ai, Bi, and Ci, the combination of Ai, Bi, Ci, and Di is obtained by applying Dd, the combination of Ai, Bi, C2i, and Di is obtained by applying Cu, and finally the combination of Ai, Bi is obtained by applying Br , C2i and Di are the final intermediate bytecode st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com