Message synchronization method and device
A message synchronization and message technology, applied in the field of communication, can solve problems such as data message forwarding failure, business cannot run normally, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] Hereinafter, some terms used in this application are explained to facilitate the understanding of those skilled in the art.
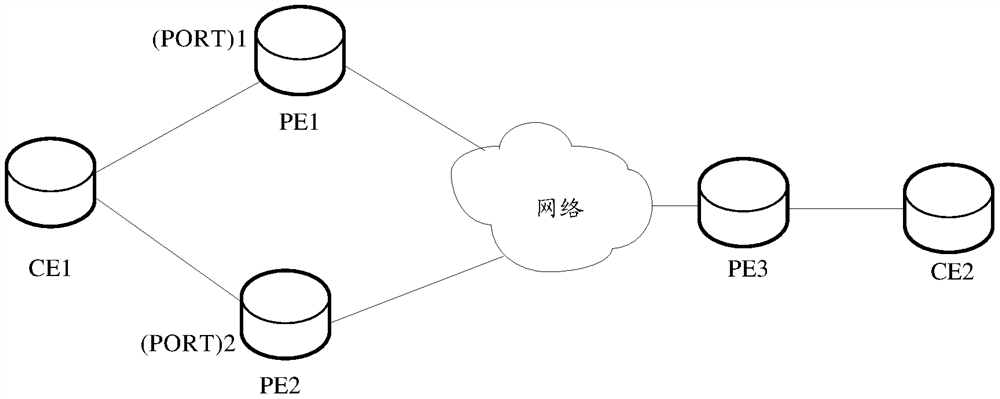
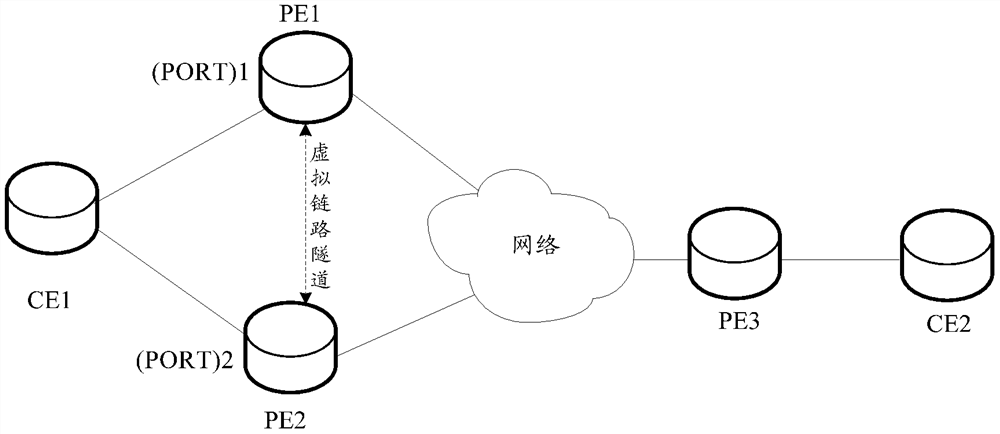
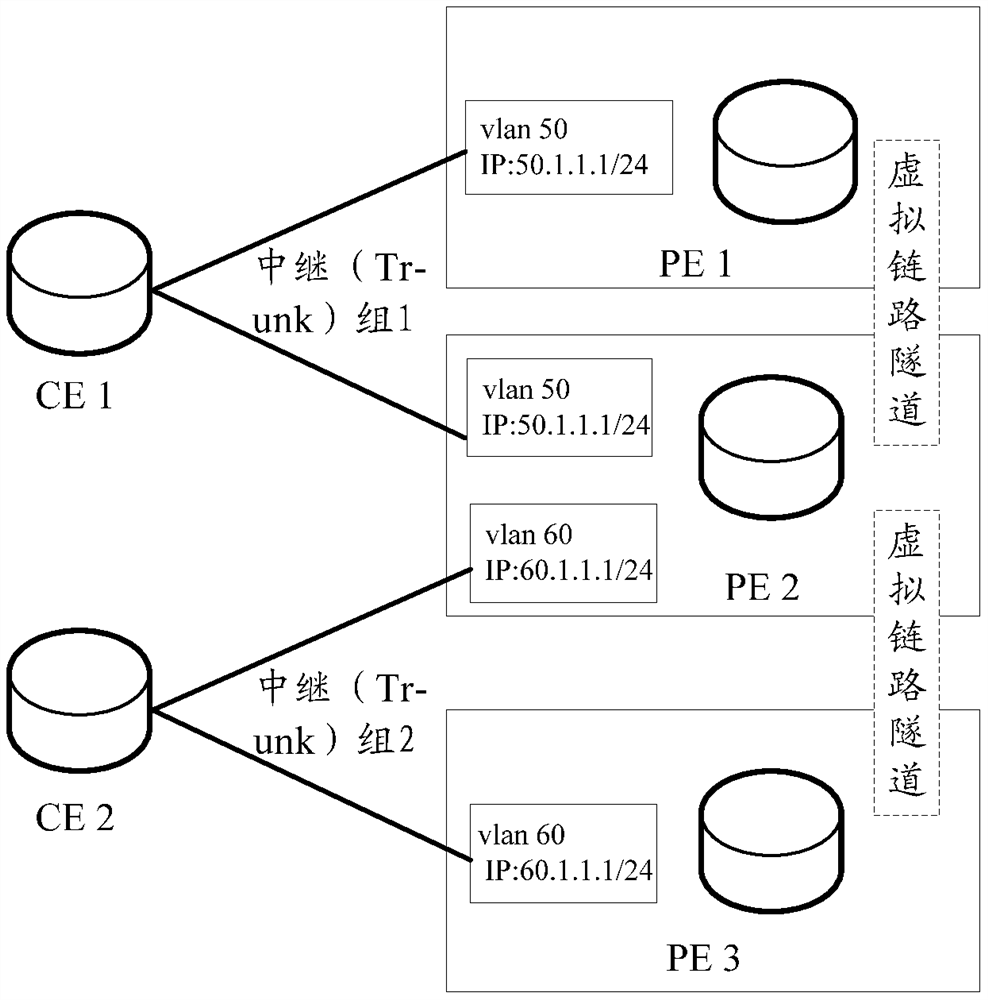
[0067] 1) Multi-homing networking, which is an emergency disaster recovery mechanism that can provide normal communication in the event of a sudden disaster in time. The multi-homing function means that one CE can belong to multiple different PEs at the same time. When one of the PEs fails, the services of the CE can be forwarded through other PEs.
[0068] 2) A unit in this application refers to a functional unit or a logic unit. It may be in the form of software, and its functions are realized through the processor executing program codes; it may also be in the form of hardware.
[0069] 3) "Multiple" refers to two or more than two, and other quantifiers are similar. "And / or" describes the association relationship of associated objects, indicating that there may be three types of relationships, for example, A and / or B may indicate: A exists ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com