Control method of building intercom system
A technology of a building intercom system and a control method, which is applied to closed-circuit television systems, televisions, instruments, etc., can solve problems that affect the safety of users' lives and property, misjudgments, and affect user safety, so as to reduce processor costs and reduce the chance of leaking secrets , The effect of ensuring the safety of residents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
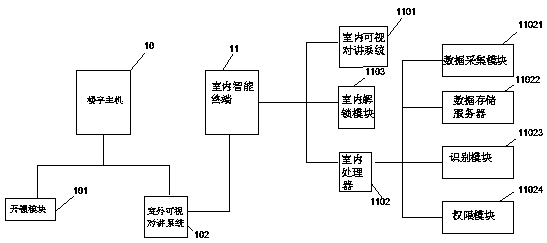
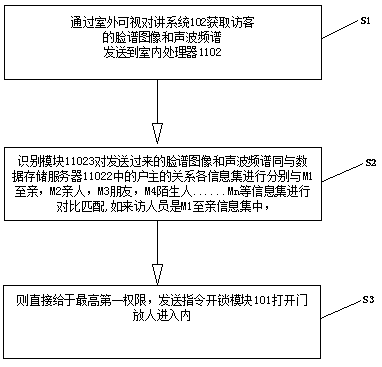
[0033] S1: Obtain the visitor's face image and sound wave spectrum through the outdoor video intercom system 102 and send them to the indoor processor 1102;
[0034] S2: Recognition module 11023 compares the sent Facebook image and sound wave spectrum with each information set related to the head of household in the data storage server 11022 with M1 relatives, M2 relatives, M3 friends, M4 strangers...Mn and other information sets for comparison and matching; if the visitor is an M1 close relative information set,
[0035] S3: The highest first authority is directly given, and an instruction is sent to the unlocking module 101 to open the door and let people in.
Embodiment approach 2
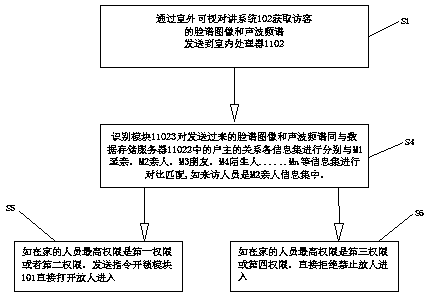
[0037] S1: Obtain the visitor's face image and sound wave spectrum through the outdoor video intercom system 102 and send them to the indoor processor 1102;
[0038] S4: Recognition module 11023 compares the sent Facebook image and sound wave spectrum with each information set related to the head of household in the data storage server 11022 with M1 relatives, M2 relatives, M3 friends, M4 strangers...Mn and other information sets for comparison and matching; for example, the visitor is M2 relative information set;
[0039] S5: If the highest authority of the person at home is the first authority or the second authority, send an instruction to the unlocking module 101 to directly open the door for the person to enter,
[0040] S6: If the highest authority of the person at home is the third authority or the fourth authority, directly refuse and prohibit people from entering.
Embodiment approach 3
[0042] S1: Obtain the visitor's face image and sound wave spectrum through the outdoor video intercom system 102 and send them to the indoor processor 1102;
[0043] S7: Recognition module 11023 compares the sent Facebook image and sound wave spectrum with each information set of the relationship with the head of household in the data storage server 11022 respectively with M1 close relatives, M2 relatives, M3 friends, M4 strangers...Mn and other information sets for comparison and matching; if the visitor is an M3 friend information set;
[0044] S8: If the highest authority of the person at home is the first authority, the unlocking module 101 sends an instruction to directly open and let the person enter,
[0045] S9: If the highest authority of the person at home is the second authority or the third authority or the fourth authority, directly refuse and prohibit people from entering.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com