Malicious program visual detection method based on deep learning
A malicious program and deep learning technology, applied in the field of network security, to achieve the effect of easy implementation, high reliability, and accurate detection results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
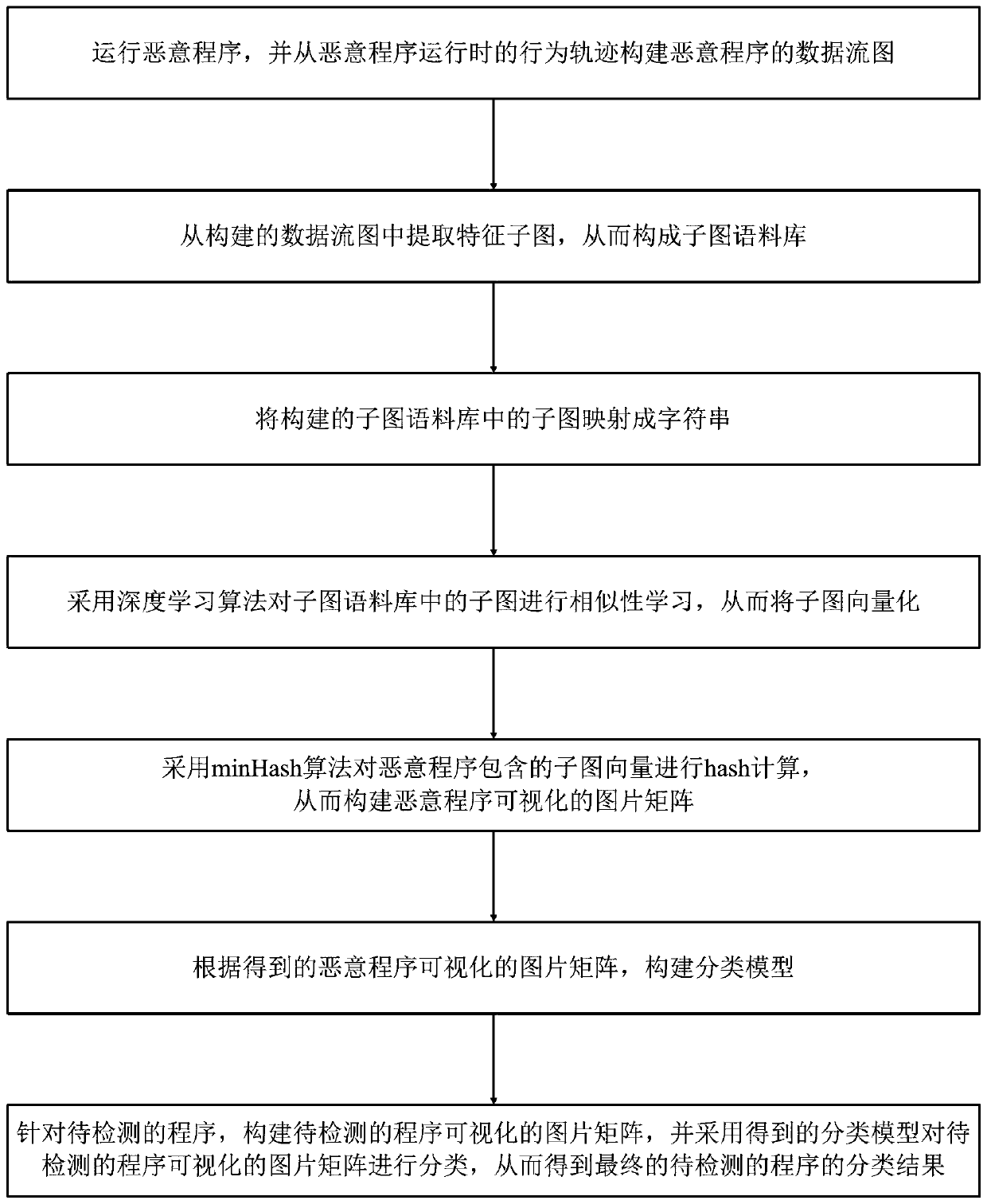
[0037] Such as figure 1 Shown is the method flow diagram of the method of the present invention: this deep learning-based malicious program visual detection method provided by the present invention comprises the following steps:
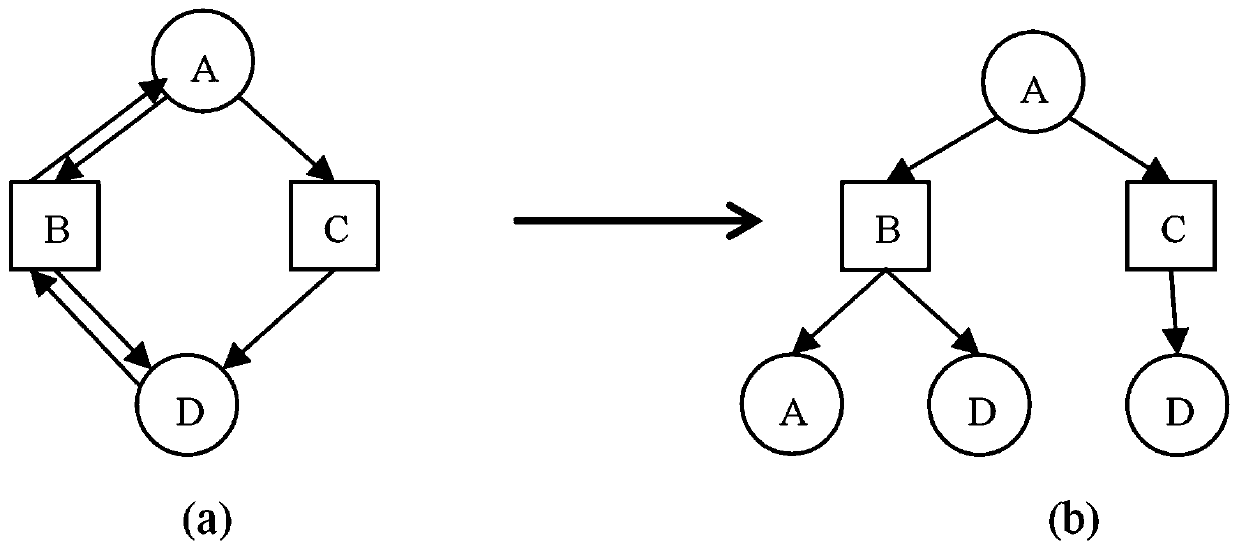
[0038] S1. Run the malicious program, and construct the data flow graph of the malicious program from the behavior track of the malicious program when it is running; specifically, run the malicious program in the virtual machine, and use Cuckoo to capture the runtime behavior track; the entity of the data flow graph includes the process PROCESS, registry REGISTRY, file File and network address URL;
[0039] In the specific implementation, the malicious program runs in the virtual machine to capture the runtime behavior track through Cuckoo, and builds the flow graph by monitoring the data interaction between system entities. The system entities in the data flow graph include process PROCESS, registry REGISTRY, file File and network address URL; and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com