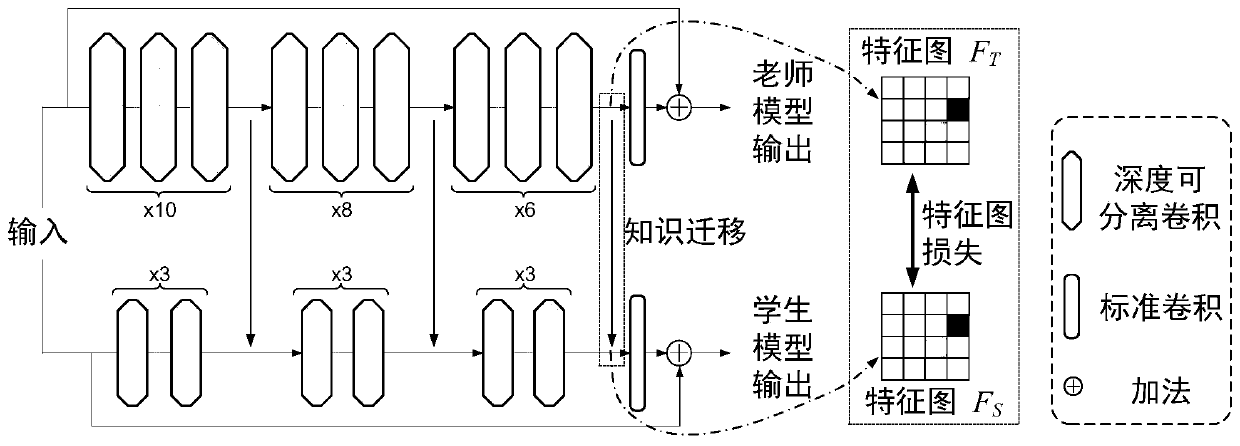
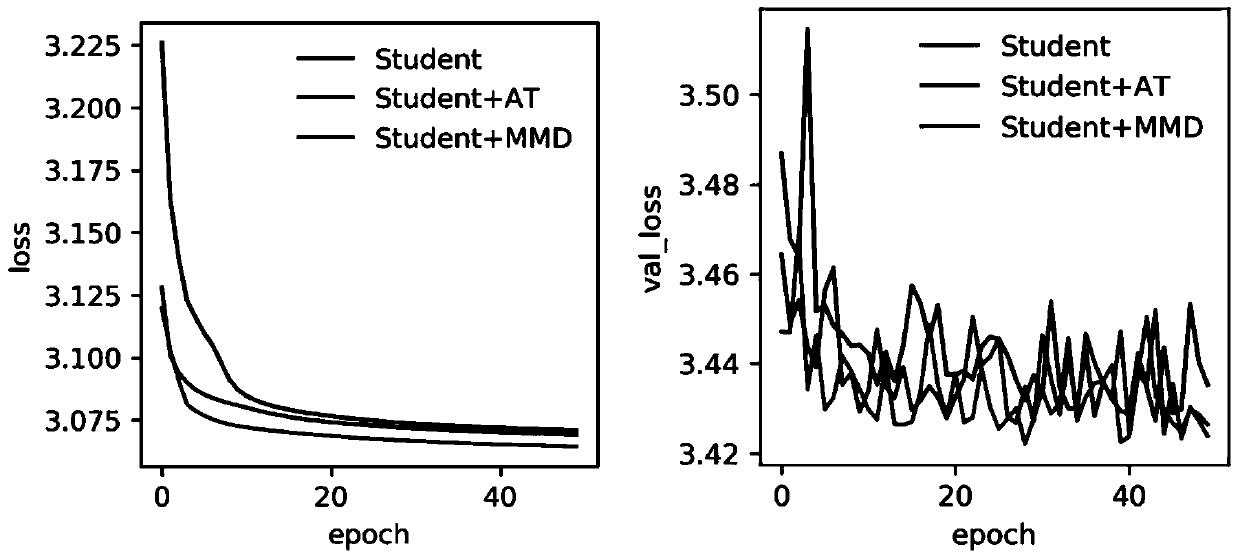
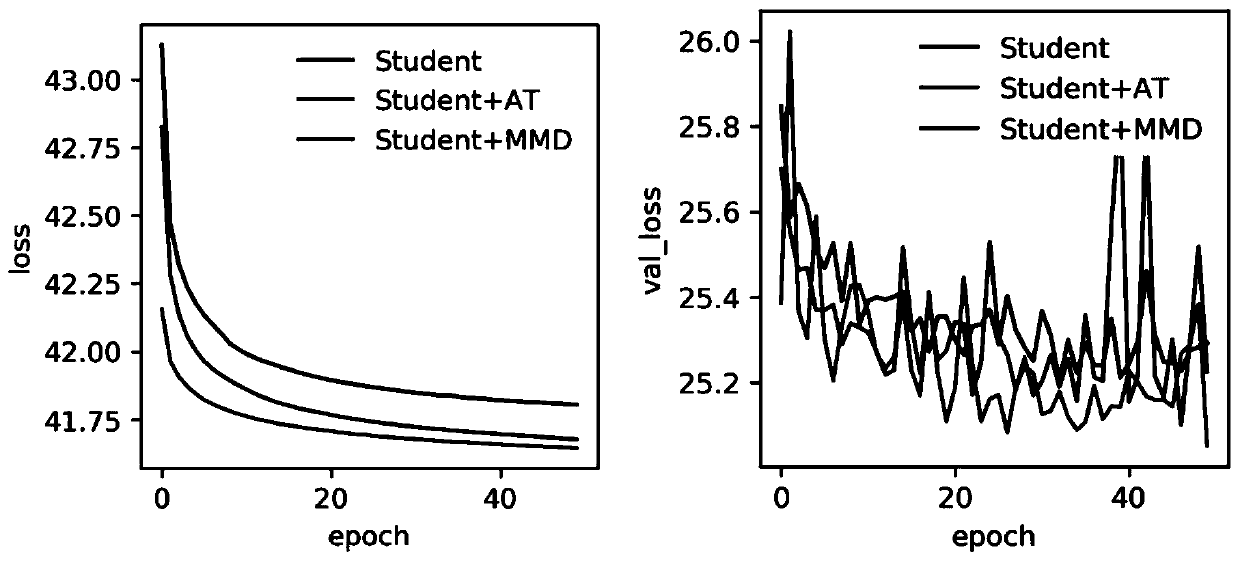
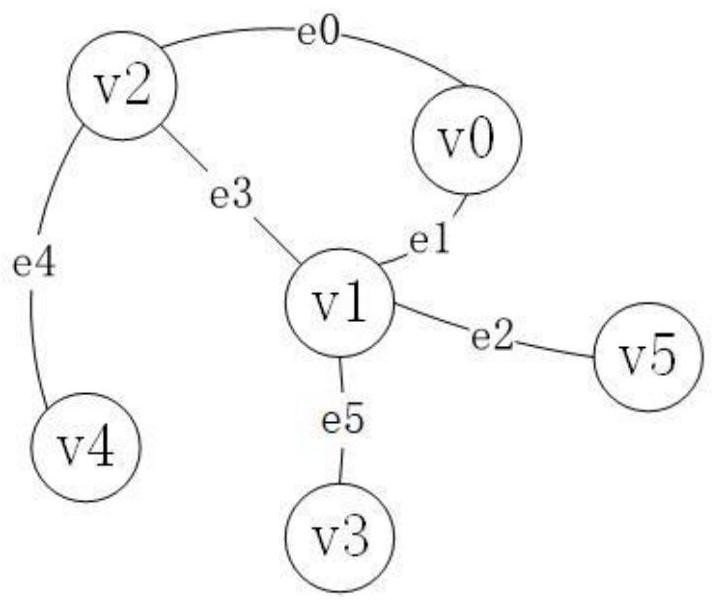
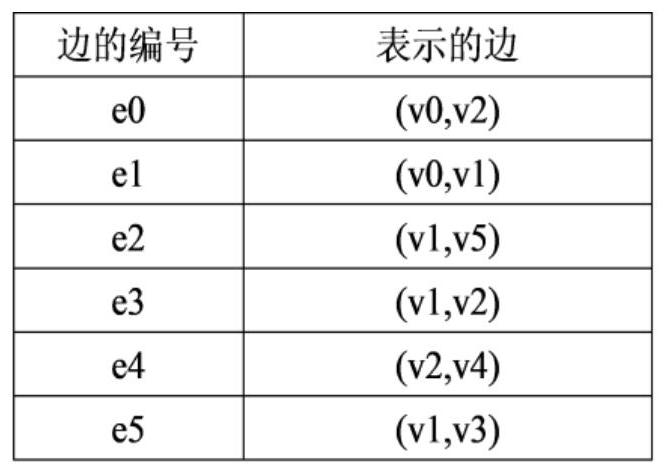
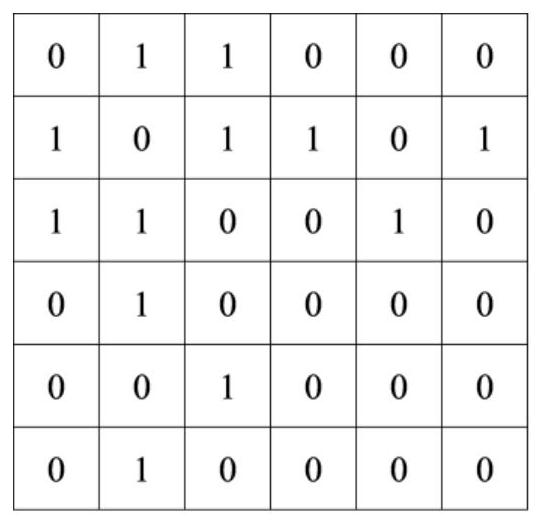
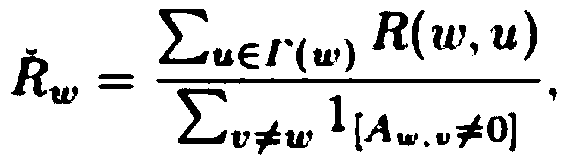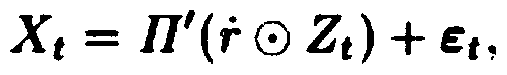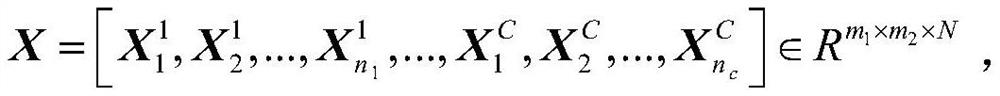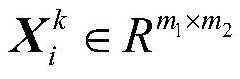Patents
Literature
83 results about "Graph mapping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
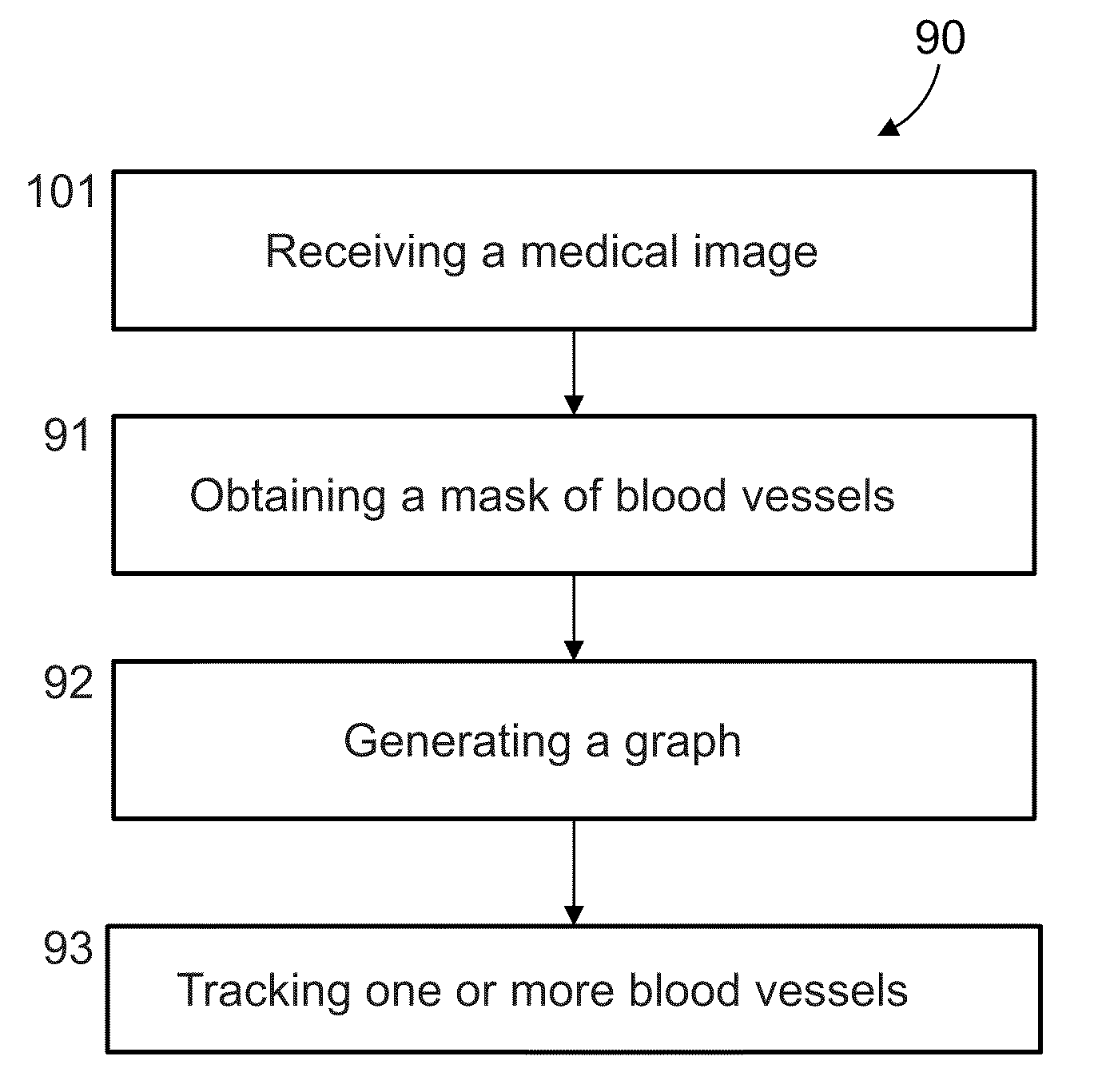
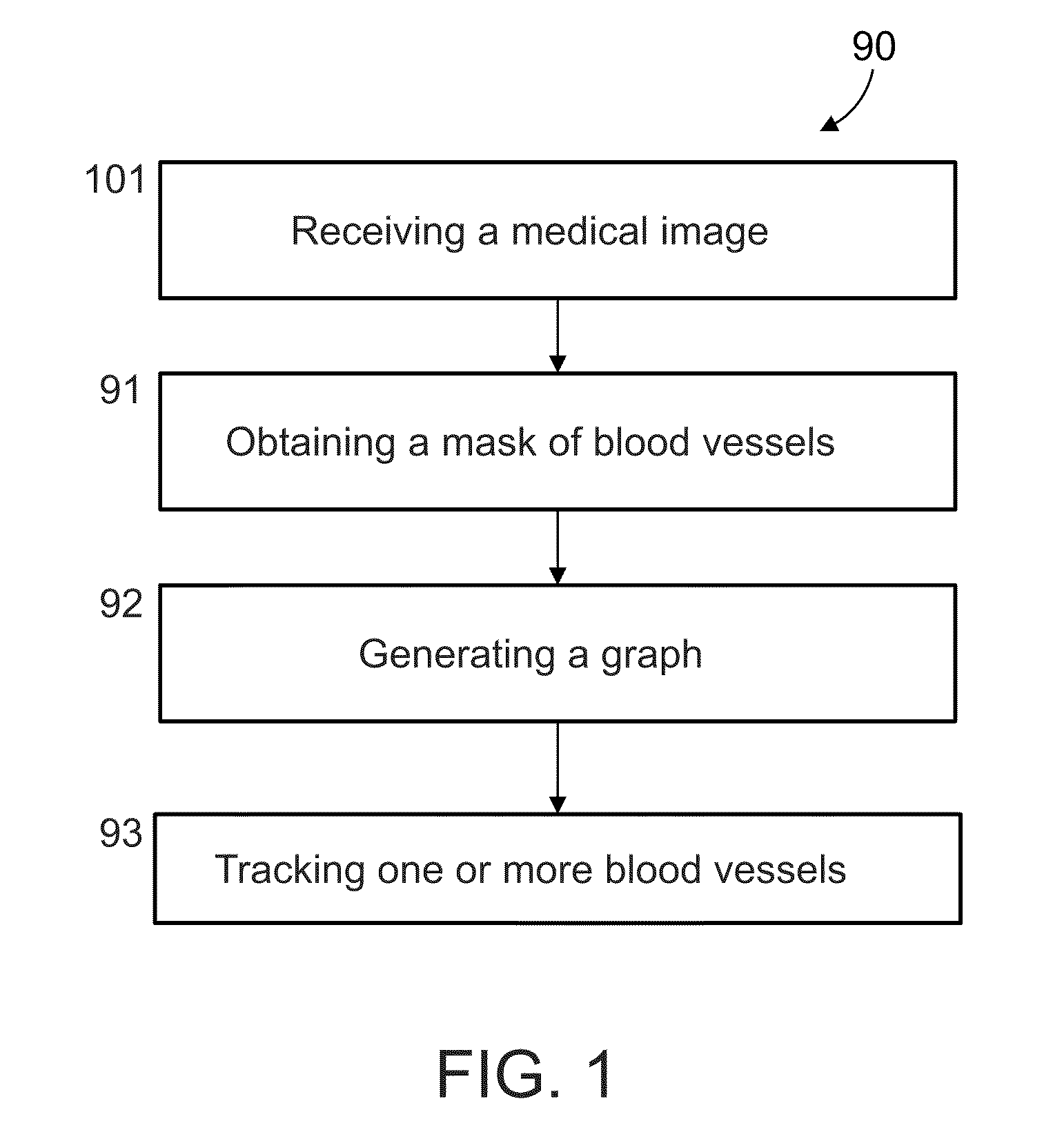
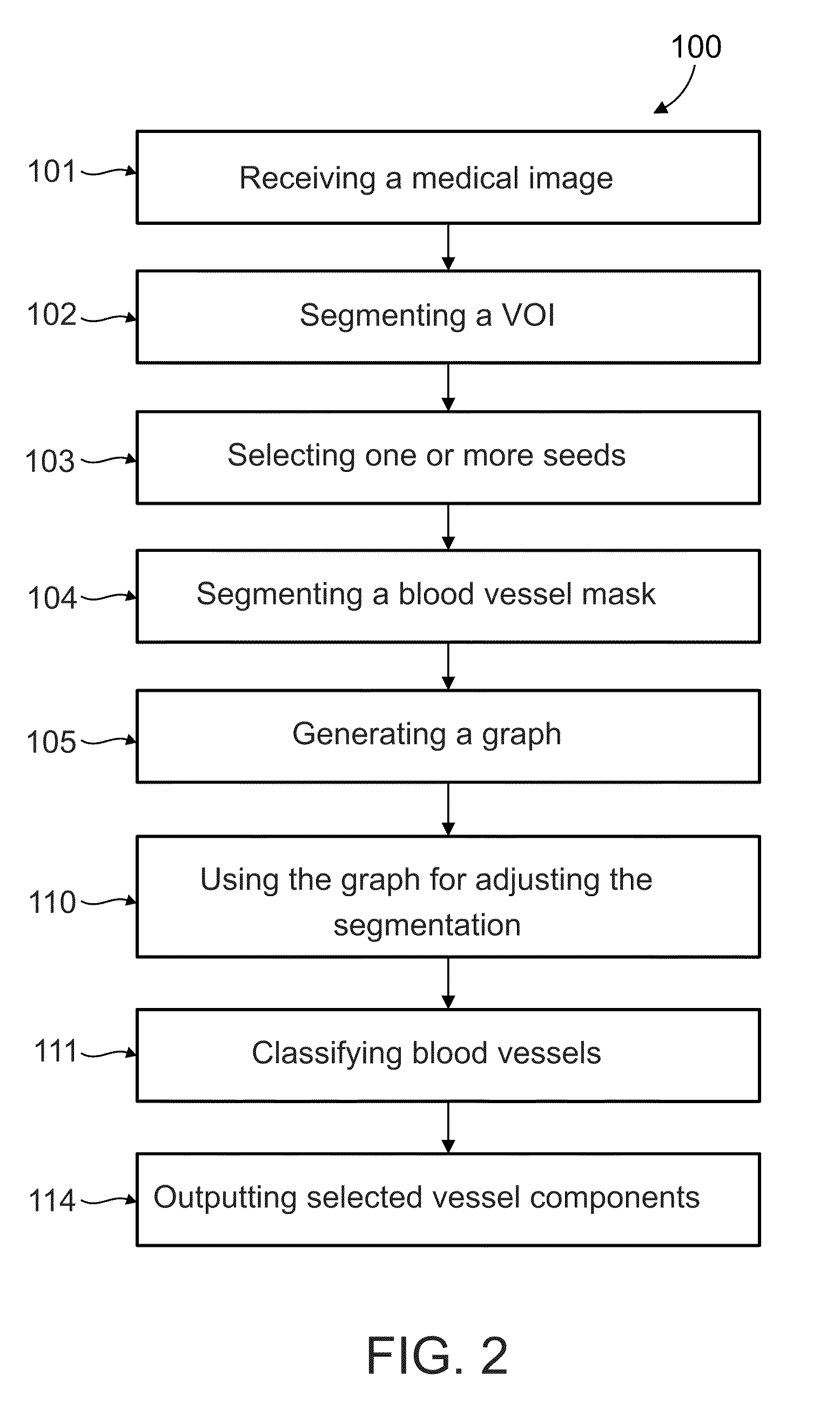
Method and system for blood vessel segmentation and classification
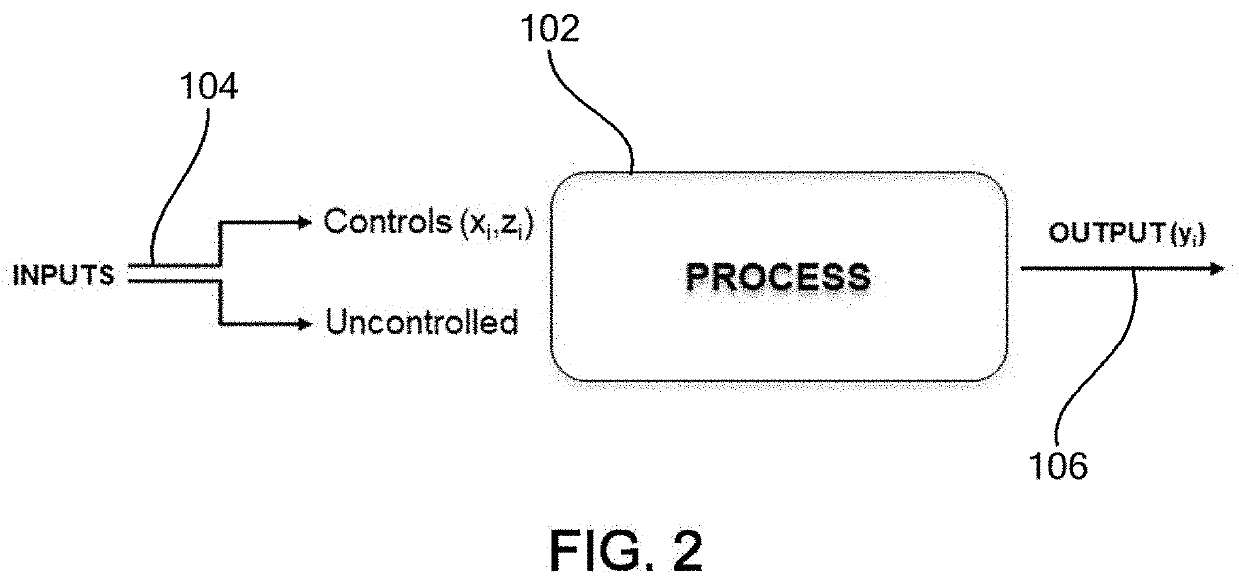
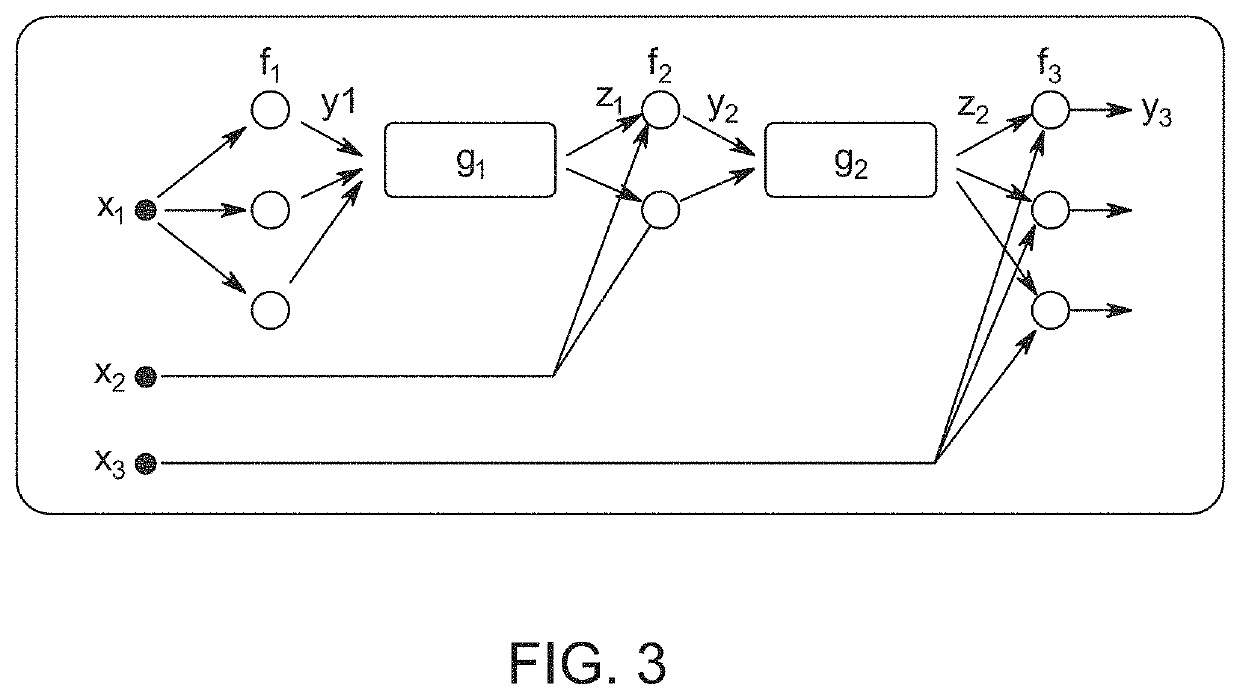
A method of analyzing structure of a network of vessels in a medical image, comprising:receiving the medical image depicting the network of vessels;obtaining a mask of the network of vessels in the image; andgenerating a non-forest graph mapping a plurality of paths of vessels in the network to directed paths in the graph, with each edge in the graph either directed to indicate a known direction of flow in the corresponding vessel, or undirected to indicate a lack of knowledge of direction of flow in the corresponding vessel, and with all directed edges in a path directed in a same direction as the path.
Owner:PHILIPS MEDICAL SYST TECH
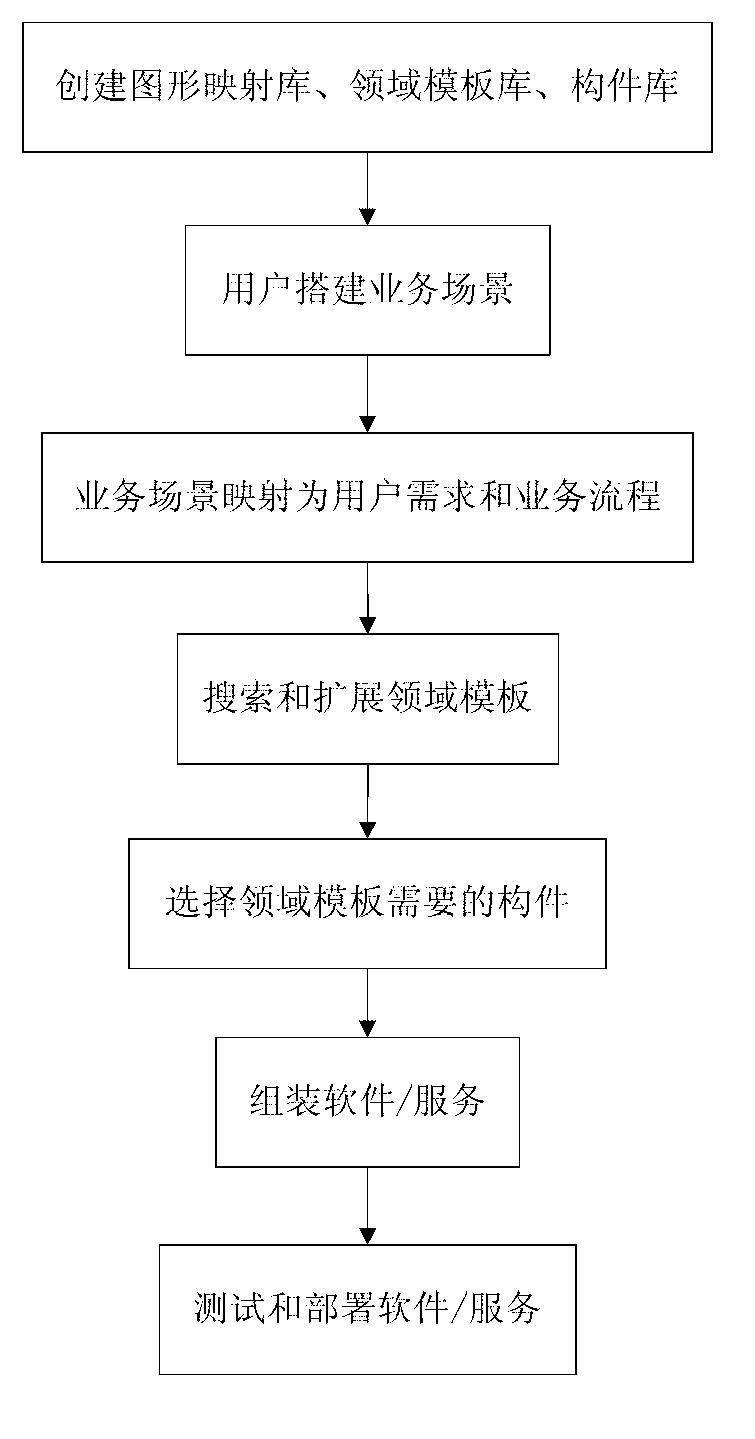
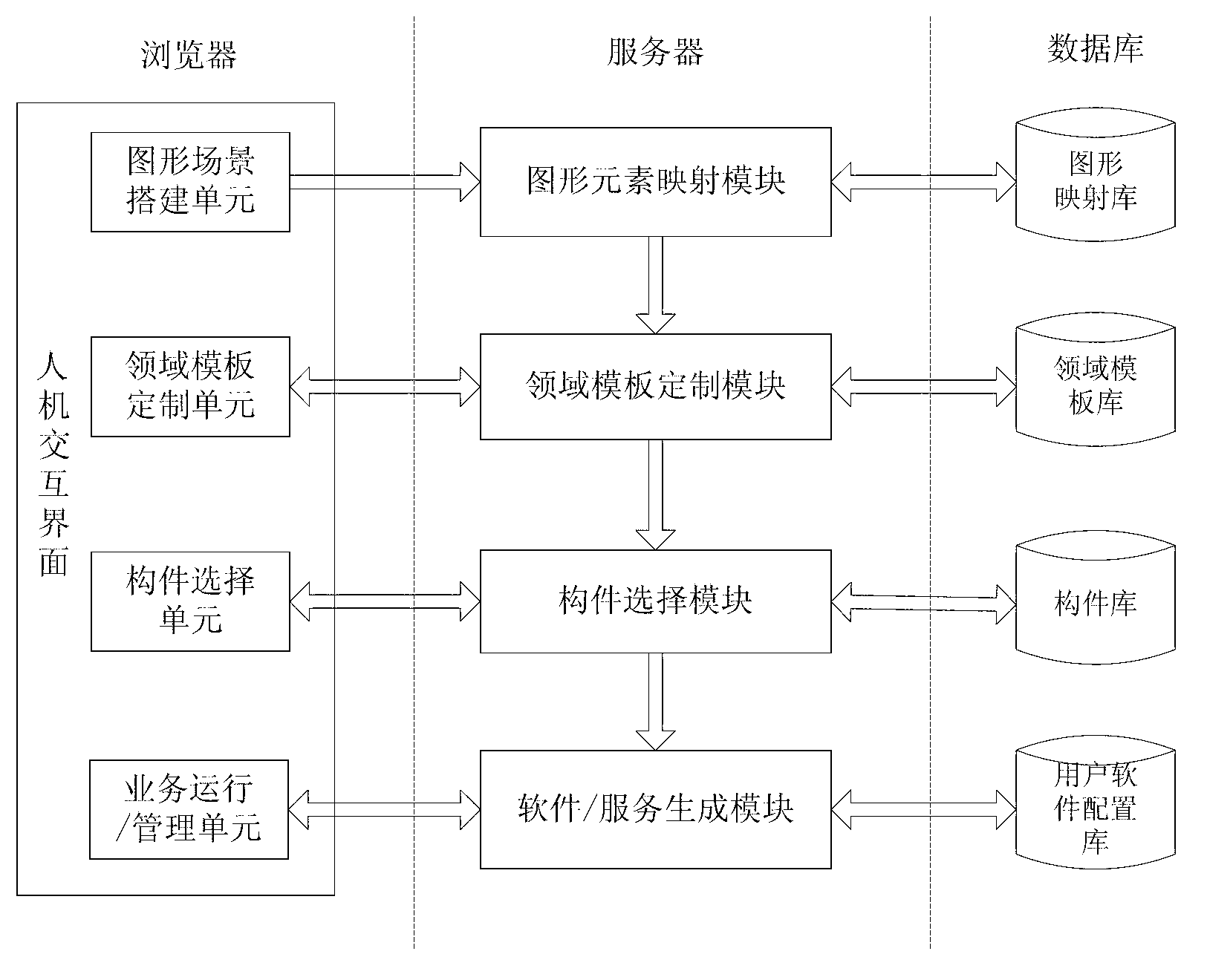
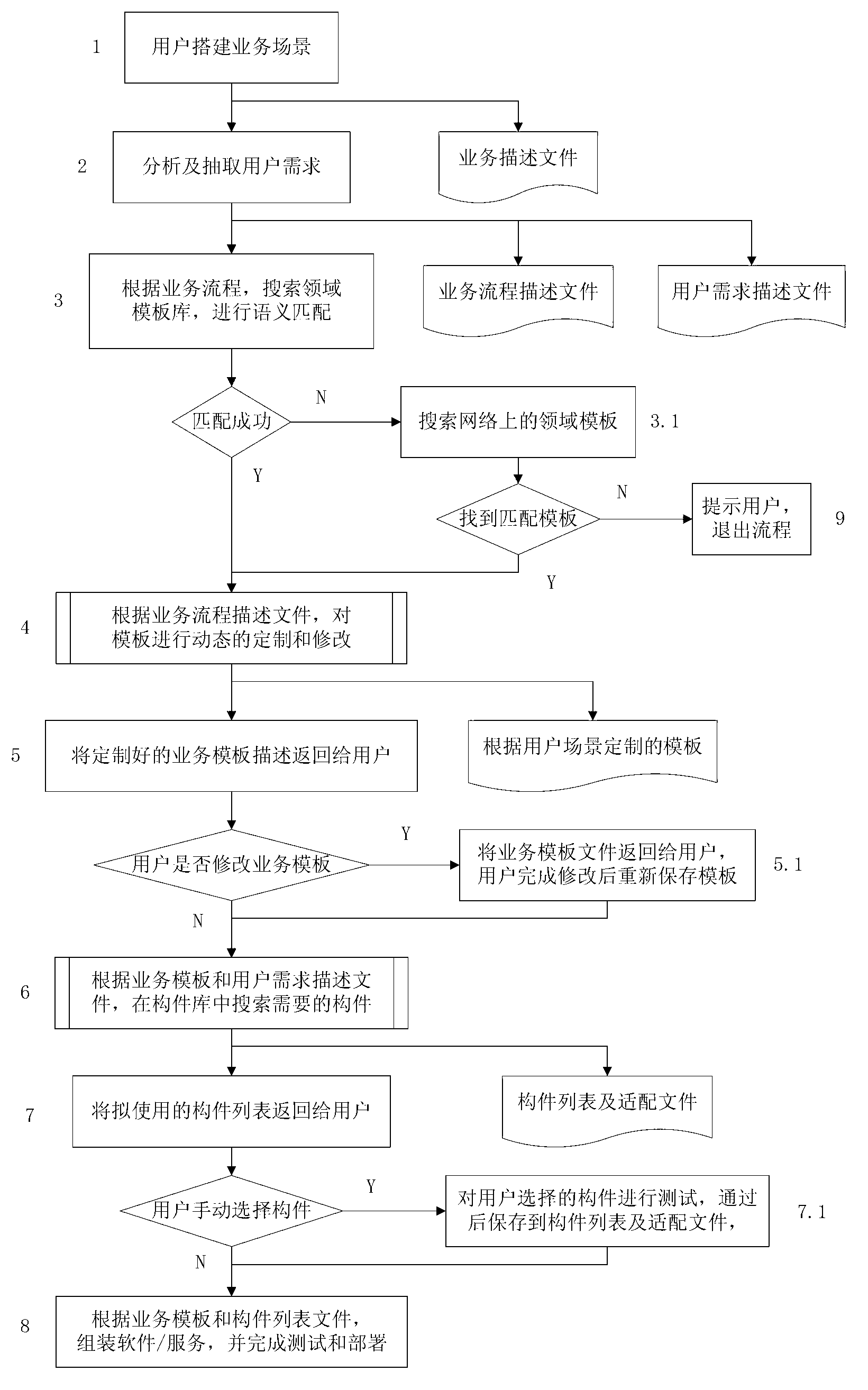
Automatic service generating system and automatic service generating method both of which are based on imaging service scene and field template
InactiveCN103294475ASimple and fast operationImprove scalabilitySpecific program execution arrangementsUser needsGraph mapping
The invention discloses an automatic service generating system and an automatic service generating method both of which are based on an imaging service scene and a field template. The automatic service generating system comprises a browser, a server and a database. When customizing software or a service, the user drags a graph tag in a graphic interface of the browser firstly and then establishes an application scenario of the software or the service. The system analyzes the application scenario into two description files including a service procedure and a user demand through a graph mapping library, finds the field template meeting the requirement of the user in a field template library through the analyzing result and carries out dynamic customization or extension on the field template. Through searching and testing, components which are found in a component library and can achieve the setting purpose are added into the field template which is customized and includes the software or the service procedure structure and the service description information of the service procedure structure, and the process of generating the software / the service is achieved. At last, the testing and deployment are carried on the generated software / the service to enable the user to be accessed to or to use the customized software or the service. The automatic service generating system is easy and convenient to operate and maintain, and the user coverage is wide.
Owner:BEIJING UNIV OF POSTS & TELECOMM
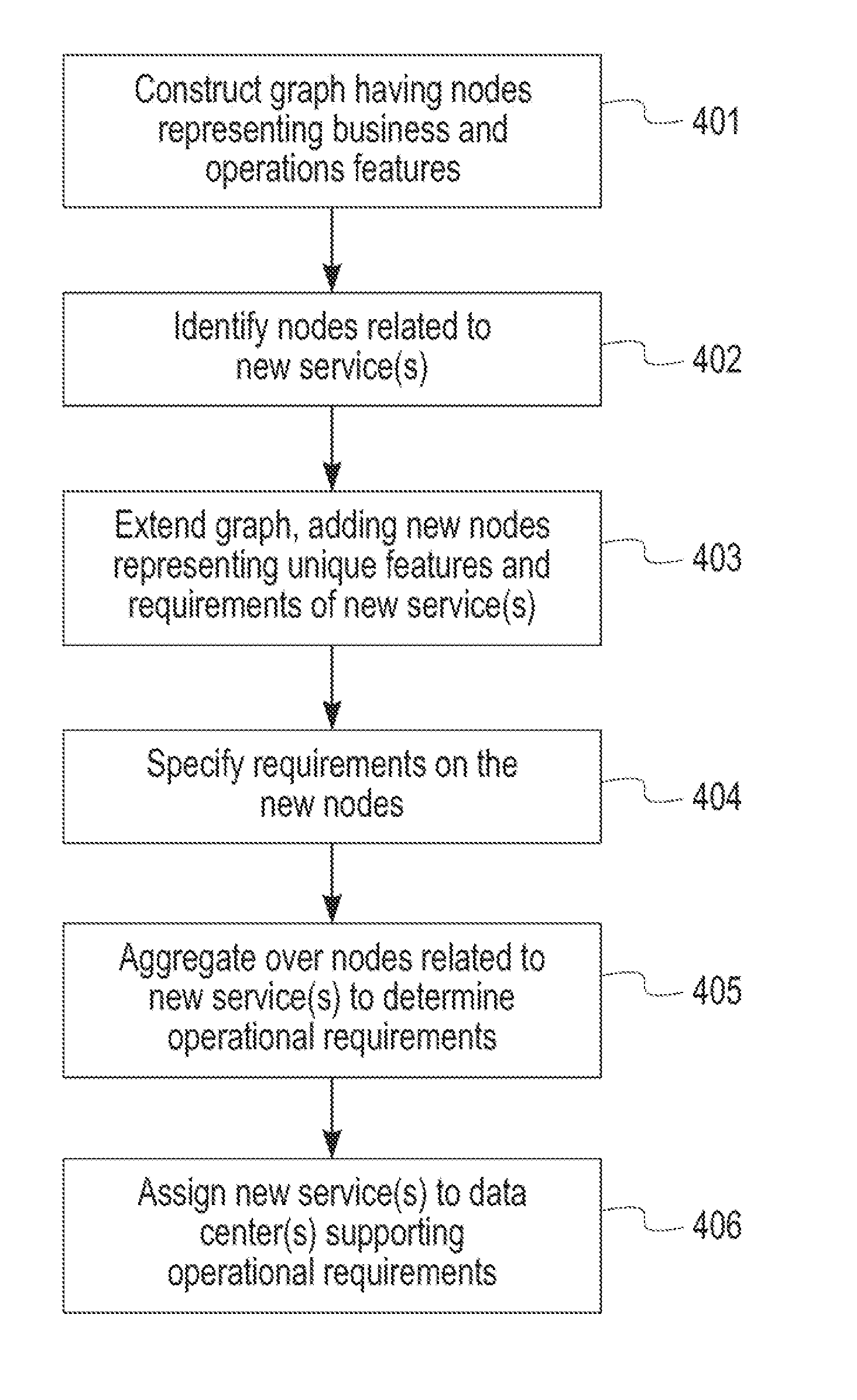
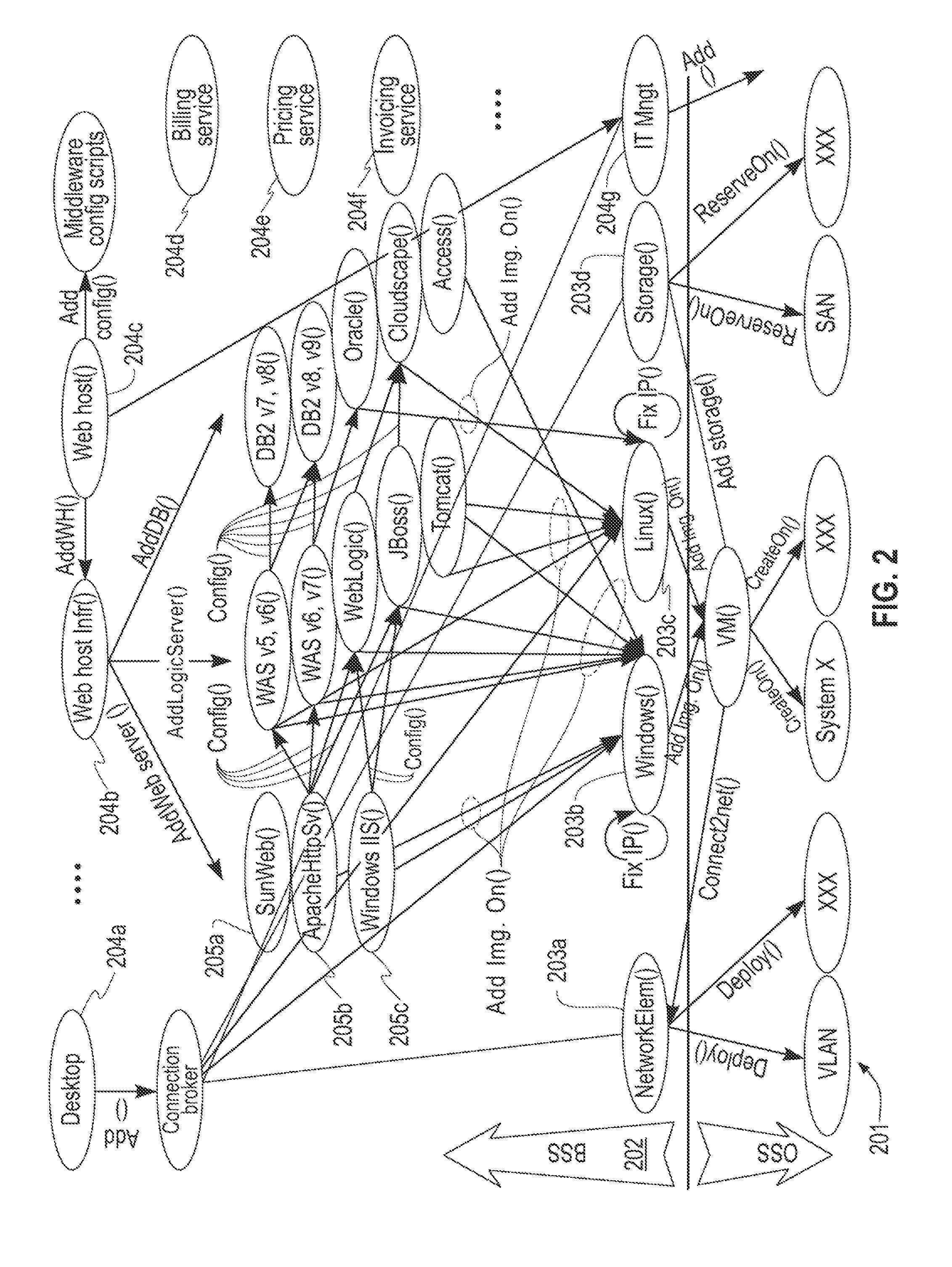
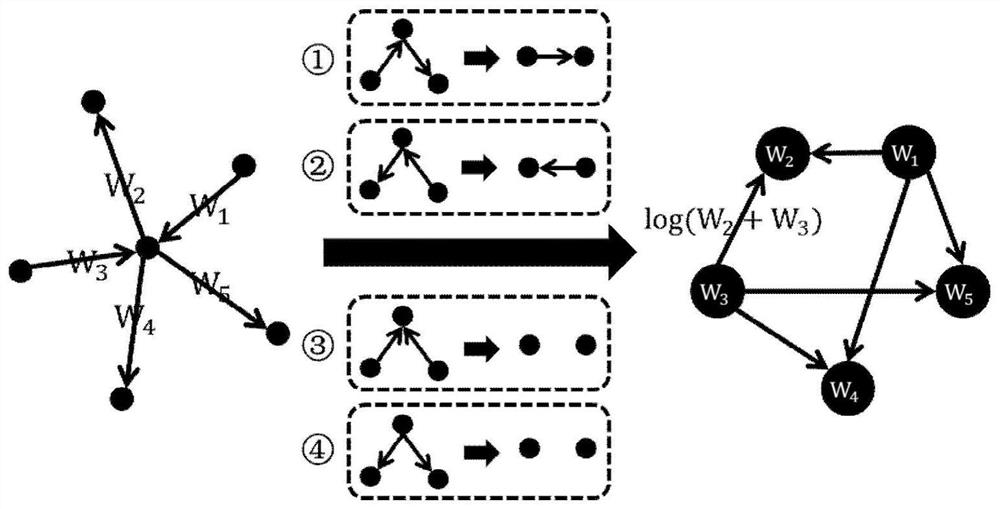
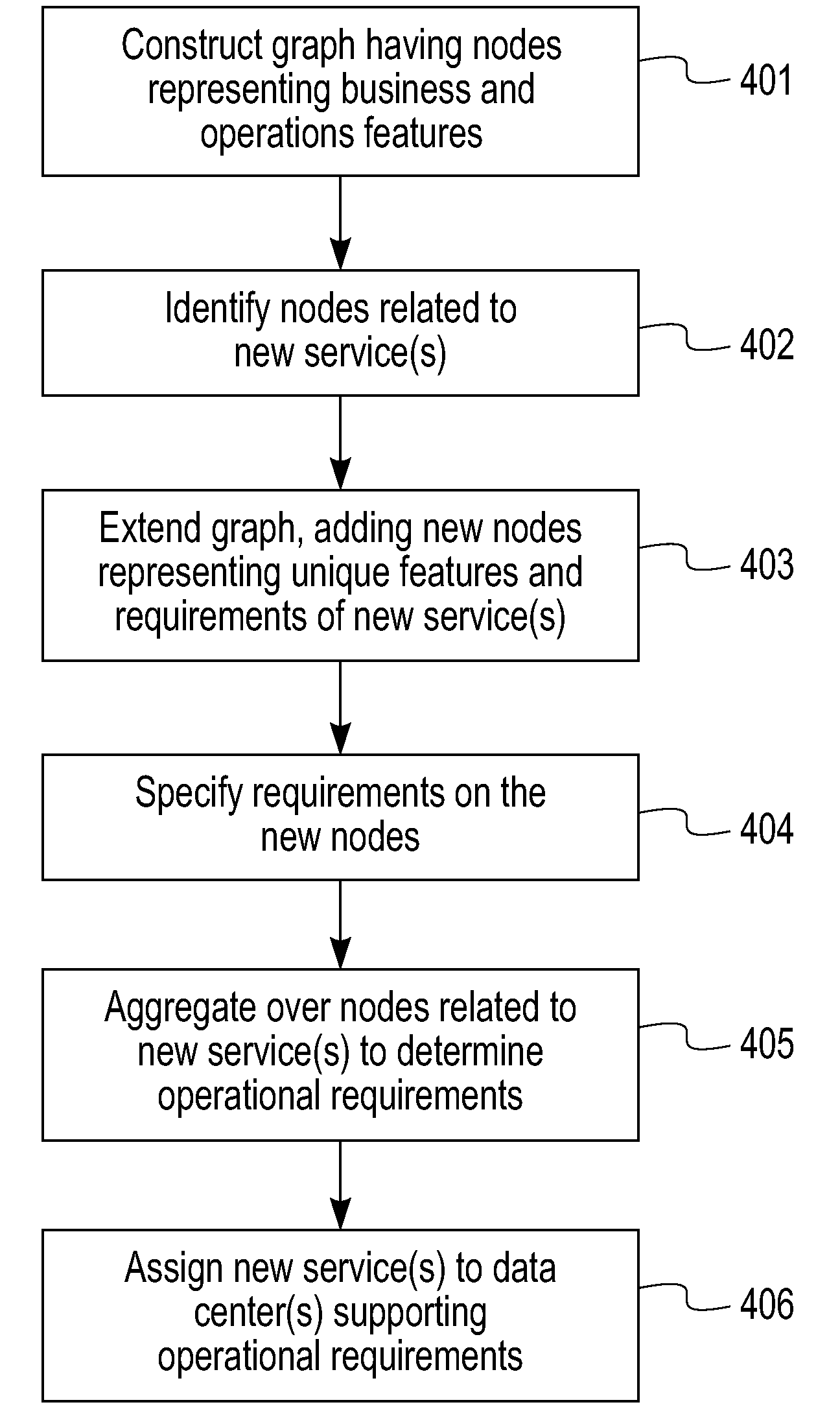
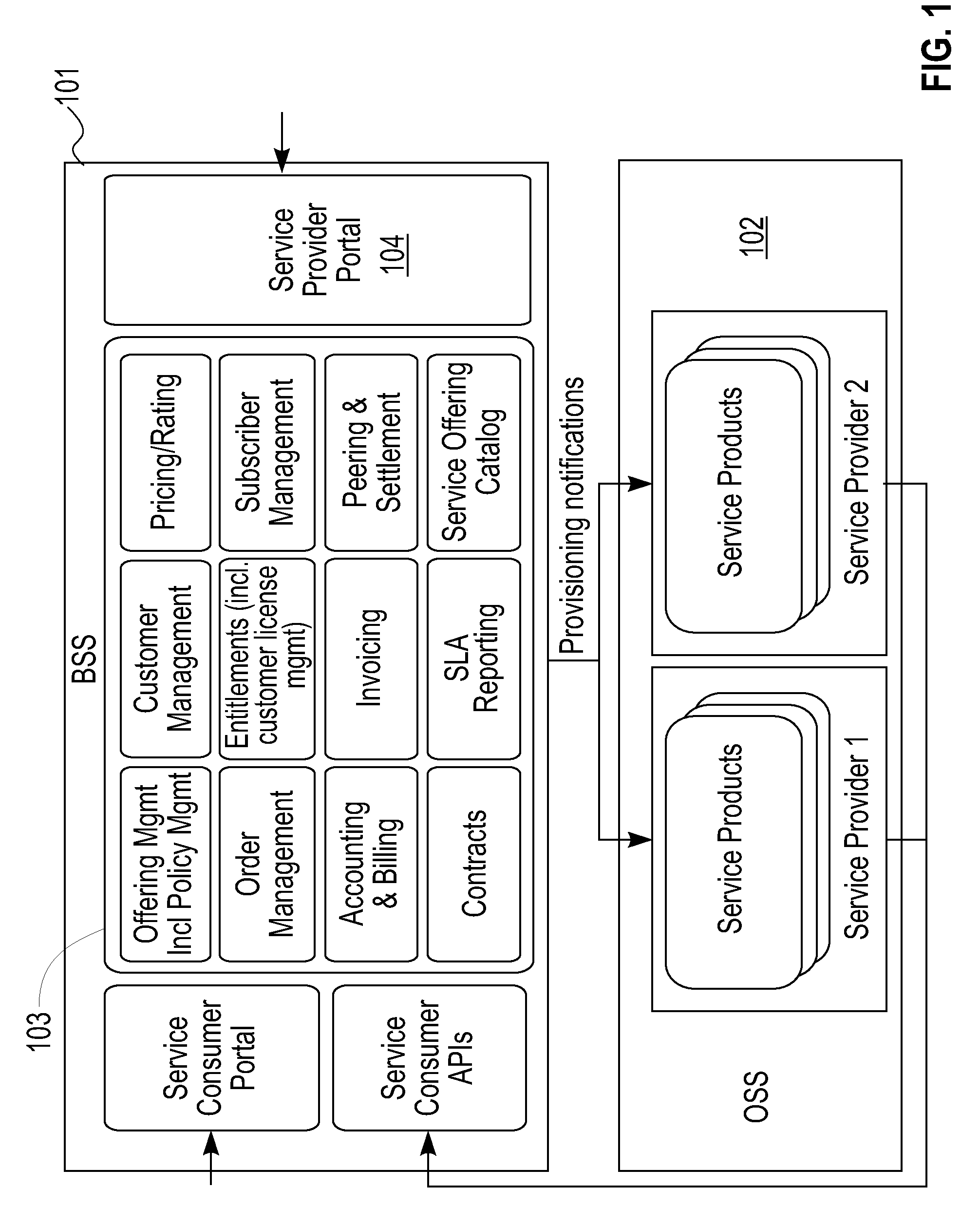
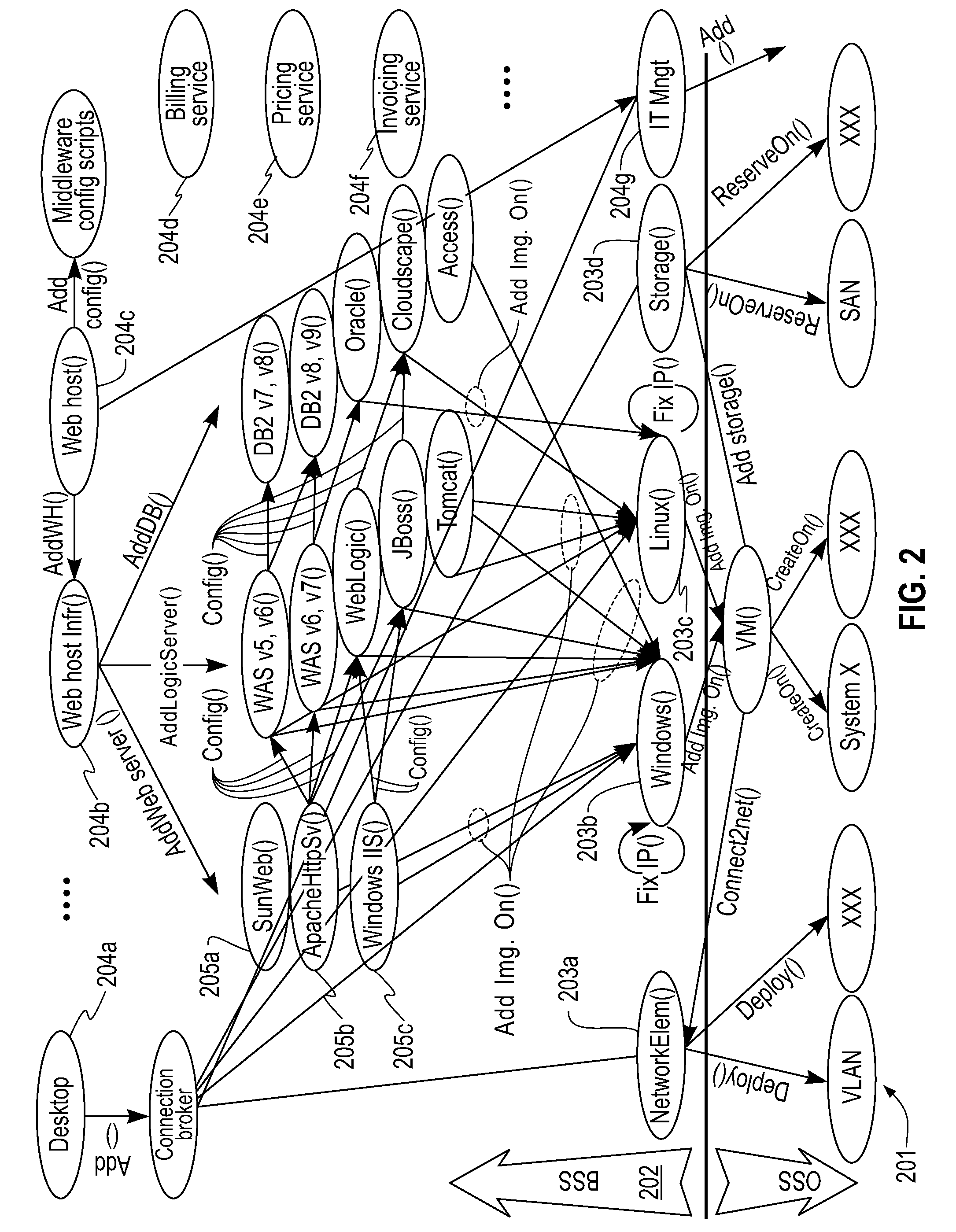
Cloud Services Creation Based on Graph Mapping
A method for service creation based on graph mapping including constructing a graph having leaf nodes in an environment including business support nodes associated with respective services and operations support nodes including attribute models, identifying a plurality of services at a level of the leafs in the graph, extending the graph by representing existing services offerings in terms of operation level service definitions and new services at the level of the leafs, and re-combining leaf nodes to define new services at service creation time.
Owner:IBM CORP
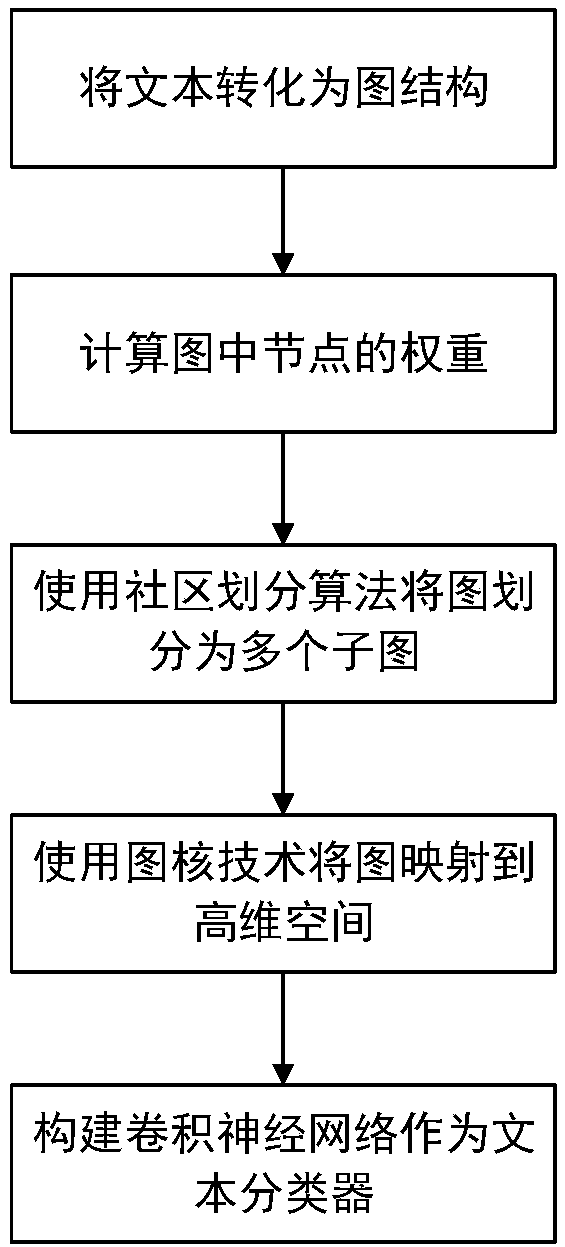
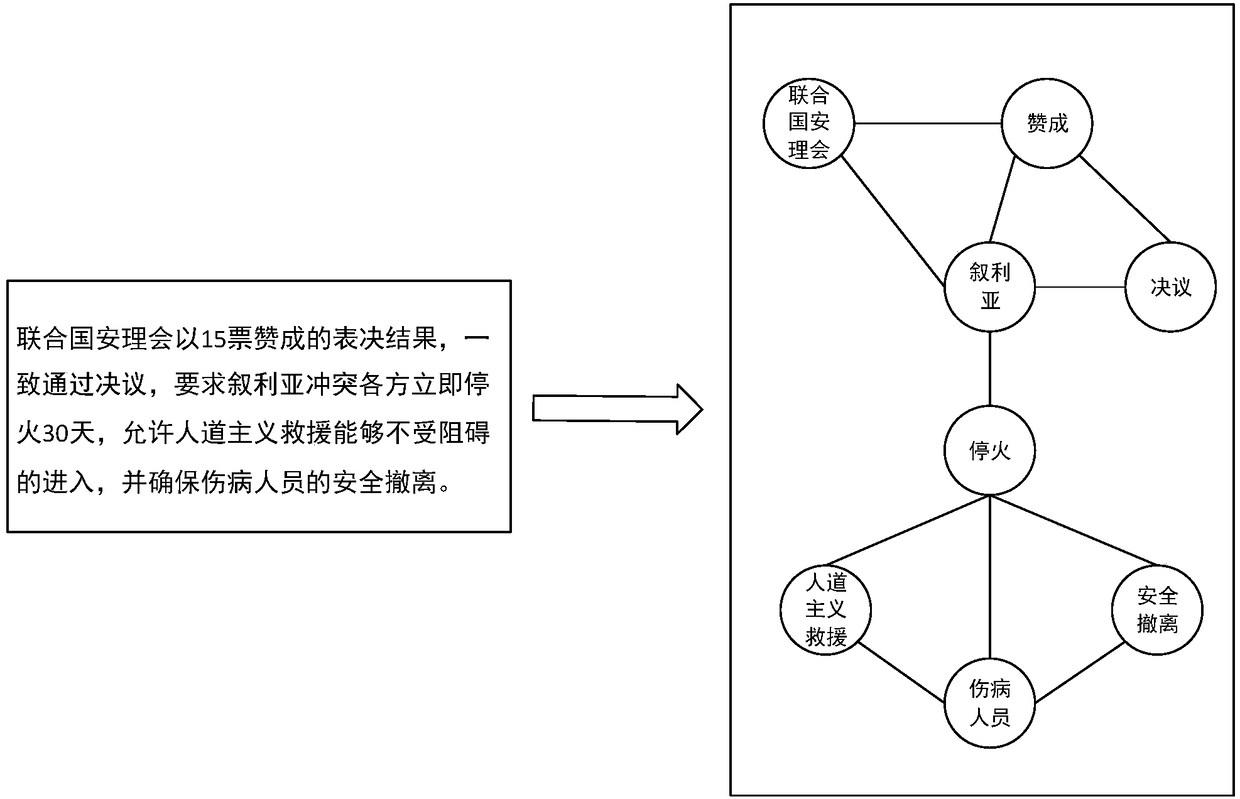
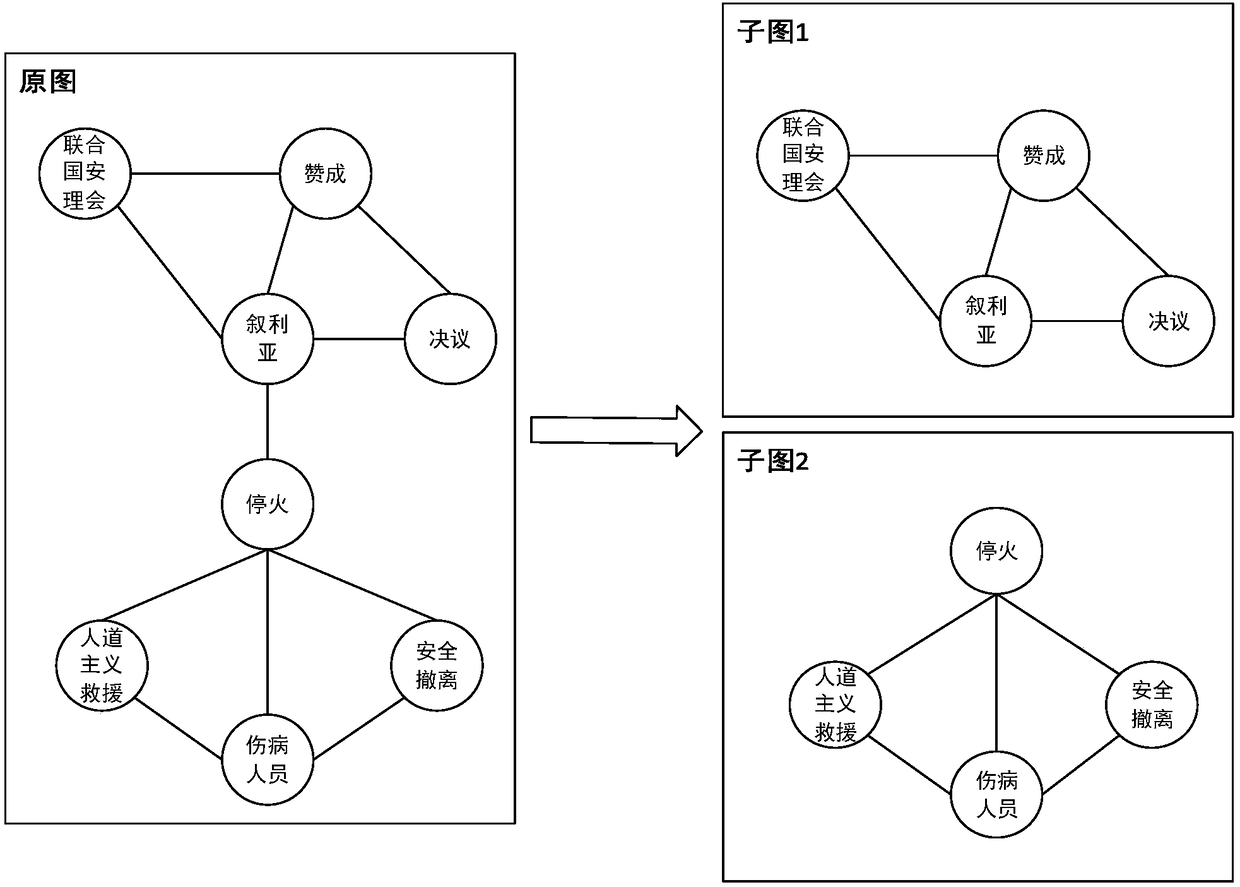
Text classification method based on graph kernel and convolutional neural network
InactiveCN108388651AEffective multidimensional featuresEffective mining of multi-dimensional featuresNatural language data processingSpecial data processing applicationsData dredgingNODAL
The invention relates to a text classification method based on a graph kernel and a convolutional neural network, and belongs to the technical field of data mining and information retrieval. The coreconcept is that: firstly, a text is preprocessed into an expression mode of a graph structure, wherein nodes in a graph correspond to words in the text; then weights of the nodes are calculated on thebasis of the graph structure, then the graph structure is decomposed into a plurality of sub-graphs by using a community discovery algorithm, the graph is mapped to a high-dimensional space by usinga graph kernel technology so as to obtain a tensor expression of the graph; finally, the tensor expression is input into the convolutional neural network, deep mining is carried out on graph features,and a category of the text is output. Compared with the prior art, according to the text classification method, an internal structure and context semantics of the text can be sufficiently utilized, so that text contents are sufficiently expressed; node information is more reasonable; the problem of complex and fussy processing process in the text classification is effectively solved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
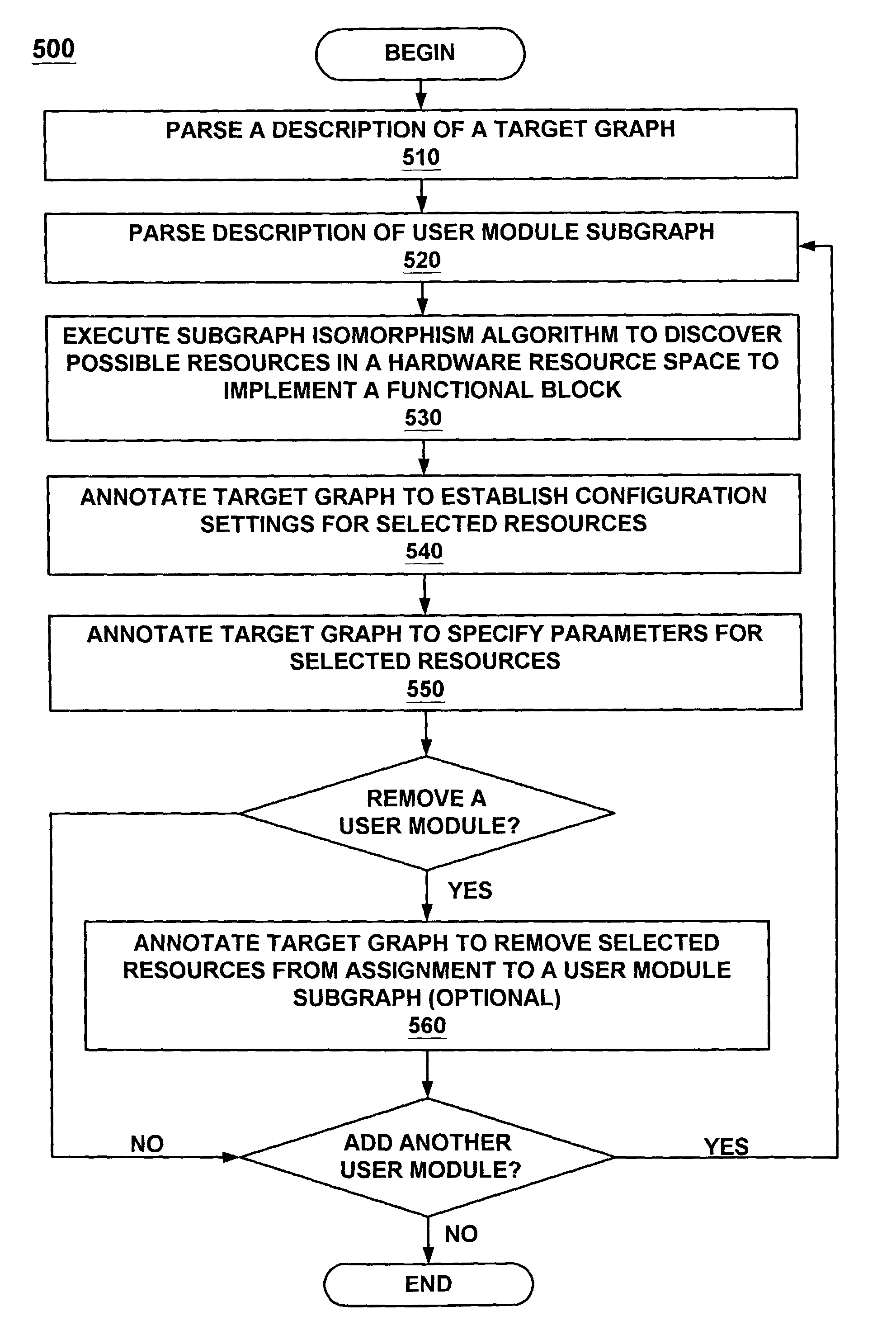
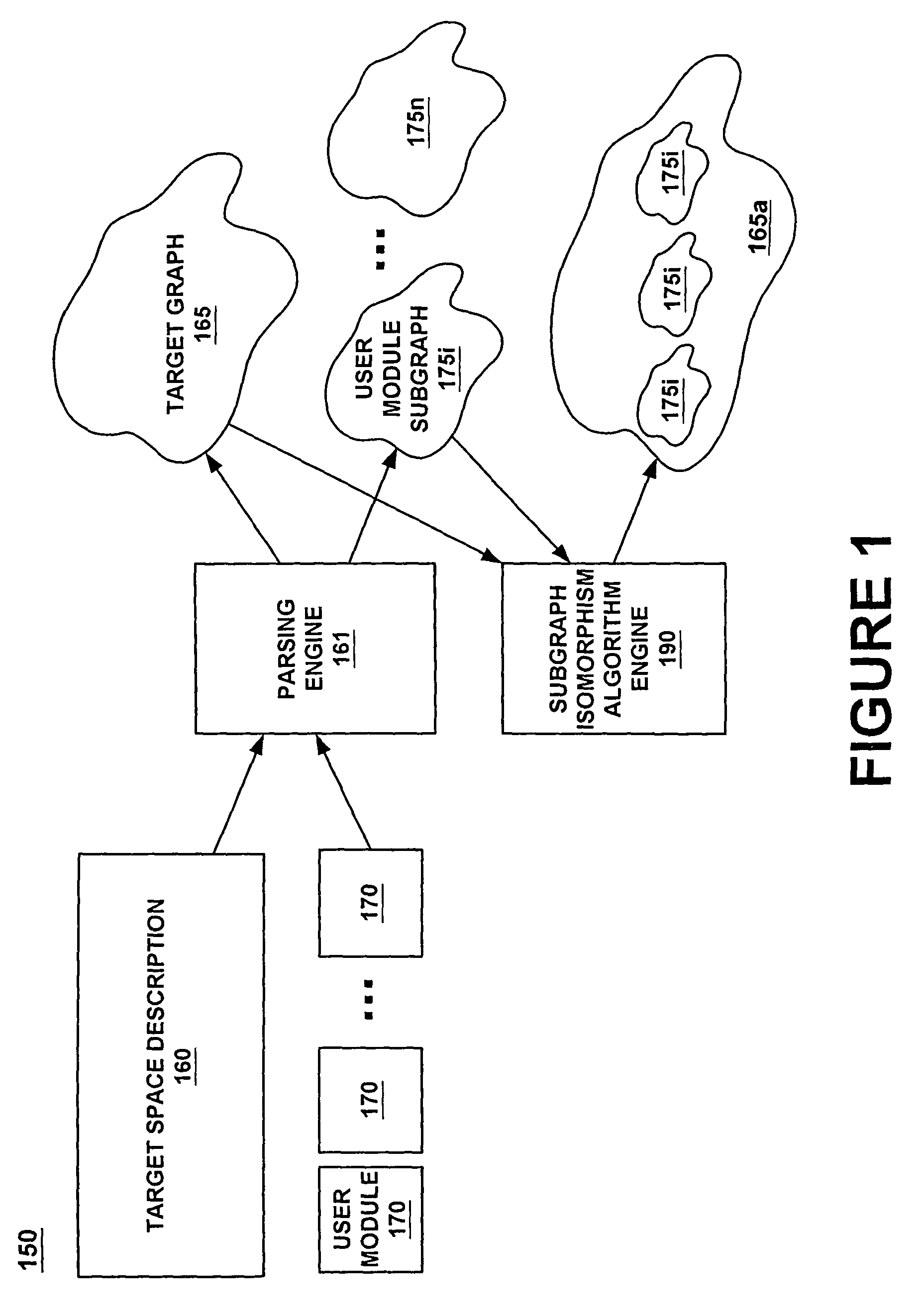
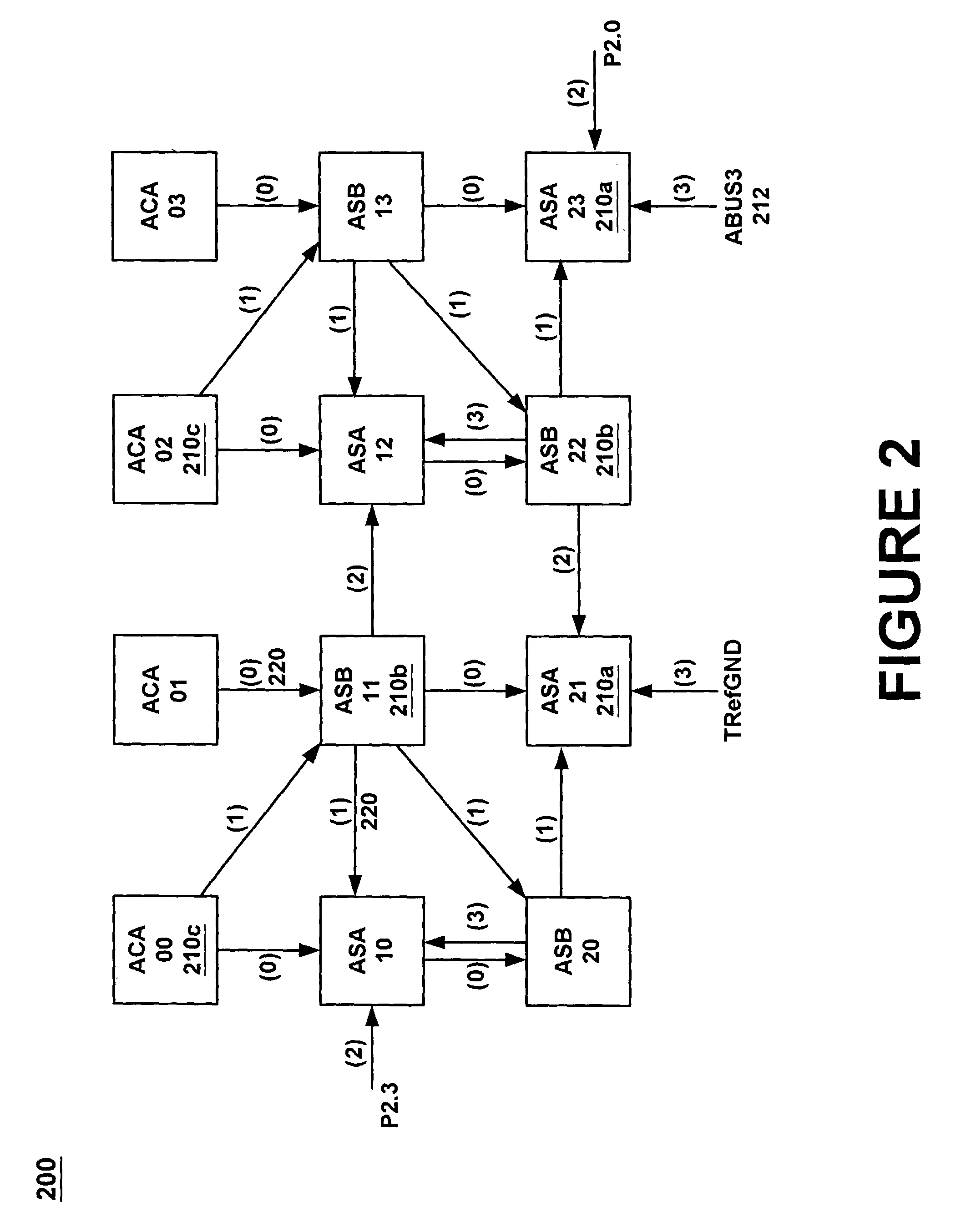
Method and system using subgraph isomorphism to configure hardware resources
InactiveUS8046206B1Provide goodProgramme controlAnalogue computers for electric apparatusOperating systemAnnotation
A method of defining a configuration of hardware resources, using a subgraph isomorphism process. The method executes a subgraph isomorphism process to discover possible resources in a hardware resource space that are suitable to implement a function. The hardware resource space may be defined by a target graph and the function may be defined by a subgraph. Next, the target graph is annotated to establish configuration settings for selected resources of the possible resources. The configuration settings may be established based on the subgraph mapping to the target graph. The target graph may also be annotated to specify parameters for the selected resources. This annotation may be performed in response to receiving parameters for the function.
Owner:MONTEREY RES LLC
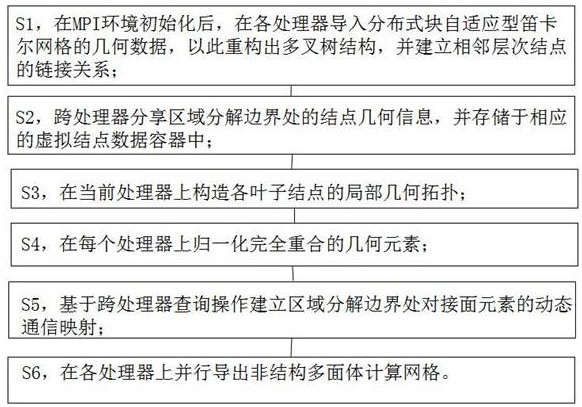
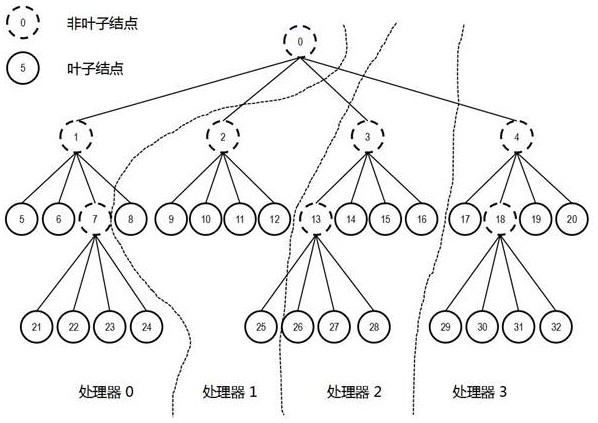
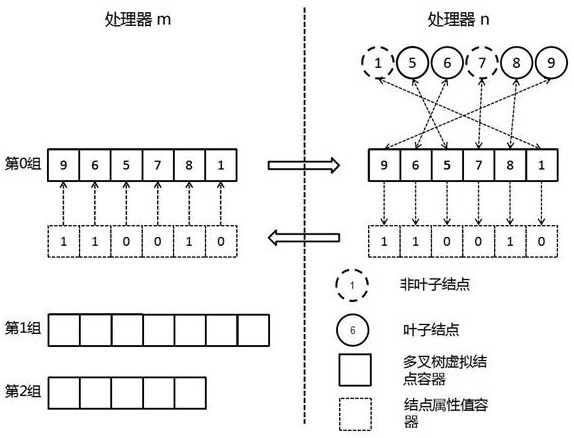
Block adaptive type Cartesian grid rapid graph mapping method and system
ActiveCN113689556APromote deep integrationAvoid complex modification workDesign optimisation/simulationSpecial data processing applicationsGraph mappingTheoretical computer science
The invention discloses a block adaptive type Cartesian grid rapid graph mapping method and system, and the method comprises the following steps: S1, after an MPI environment is initialized, importing geometric data of a distributed block adaptive type Cartesian grid into each processor so as to reconstruct a multi-way tree structure, and building a link relation of adjacent hierarchical nodes; S2, sharing node geometric information at a region decomposition boundary across processors, and storing the node geometric information in a corresponding virtual node data container; S3, constructing a local geometric topology of each leaf node on the current processor; S4, normalizing the completely overlapped geometric elements on each processor; S5, based on cross-processor query operation, establishing dynamic communication mapping of docking surface elements at the region decomposition boundary; and S6, exporting the non-structural polyhedron computational grids in parallel on each processor. The problems that in the prior art, a self-adaptive geometric module and a physical field numerical simulator are difficult to fuse, and the dynamic geometric data format conversion efficiency is low are solved.
Owner:CALCULATION AERODYNAMICS INST CHINA AERODYNAMICS RES & DEV CENT
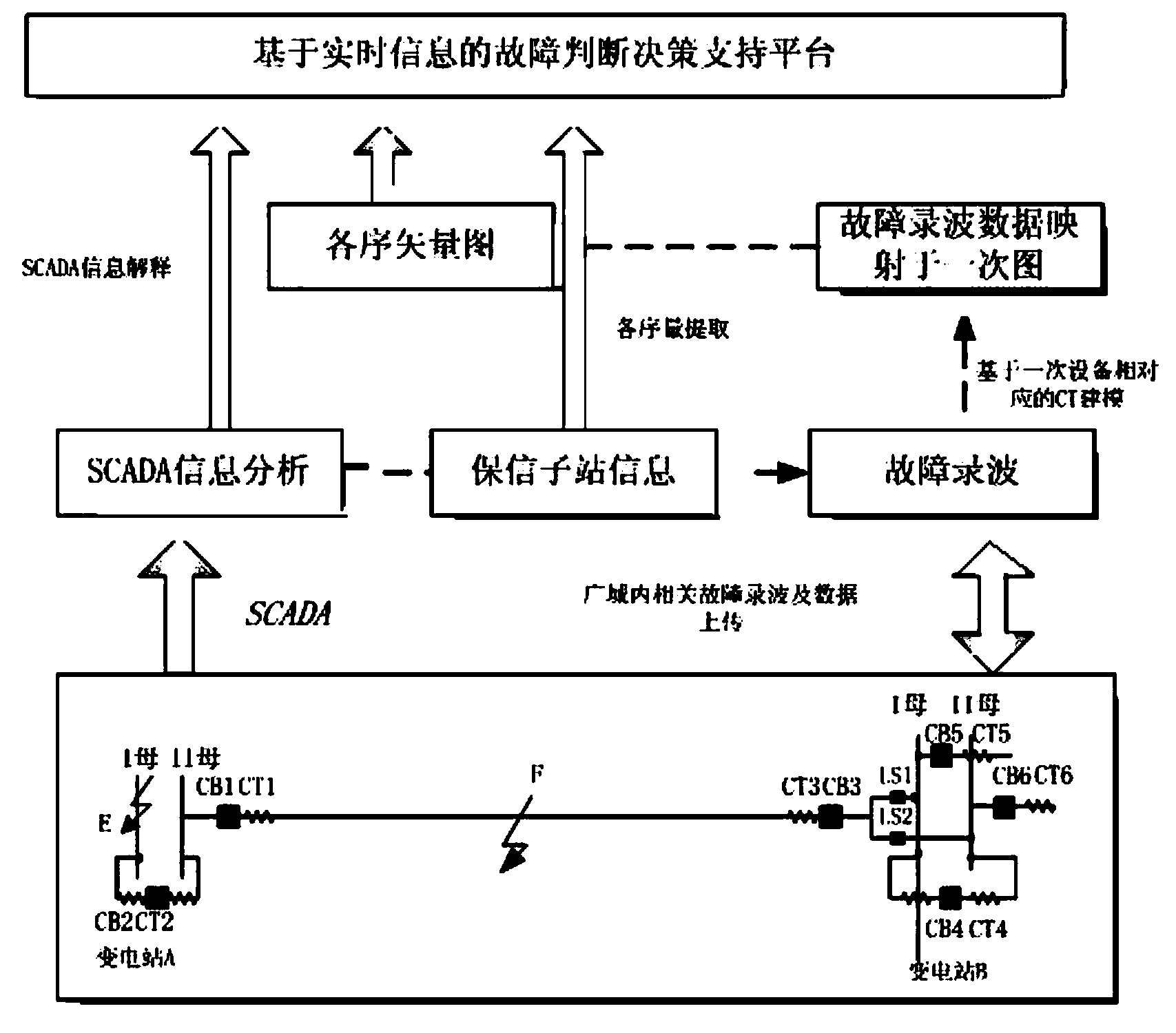
Fault accurate identification method based on real-time intra-station graph mapping
ActiveCN103971292ARealize automatic calculationQuick lockData processing applicationsInformation technology support systemGraph mappingTopological graph
The invention discloses a fault accurate identification method based on real-time intra-station graph mapping. A fault vector analysis and fault diagnosis platform based on a primary topological graph scalable vector graph and a universal information model is built; fault equipment substations needing fusing are determined for a search route through a fault amount flow direction, and a macrozone information fusion platform is formed; information fusion is carried out based on the macrozone information fusion platform, and an information closed loop and an oscillograph are fused into a vector analysis graph to carry out accident property analysis and assistant decision making; in the process of accident property analysis and assistant decision making, fault information is collected and fused in an expanded macrozone, and the fault property of a fault element is judged. On a fault scene, intra-station equipment serves as the background, the flowing direction of fault current serves as an analysis interface of a display mode, judgment of the fault element can be achieved rapidly, and the fault judgment on a multi-element connection device with a converge function is especially visual and effective.
Owner:STATE GRID CORP OF CHINA +2
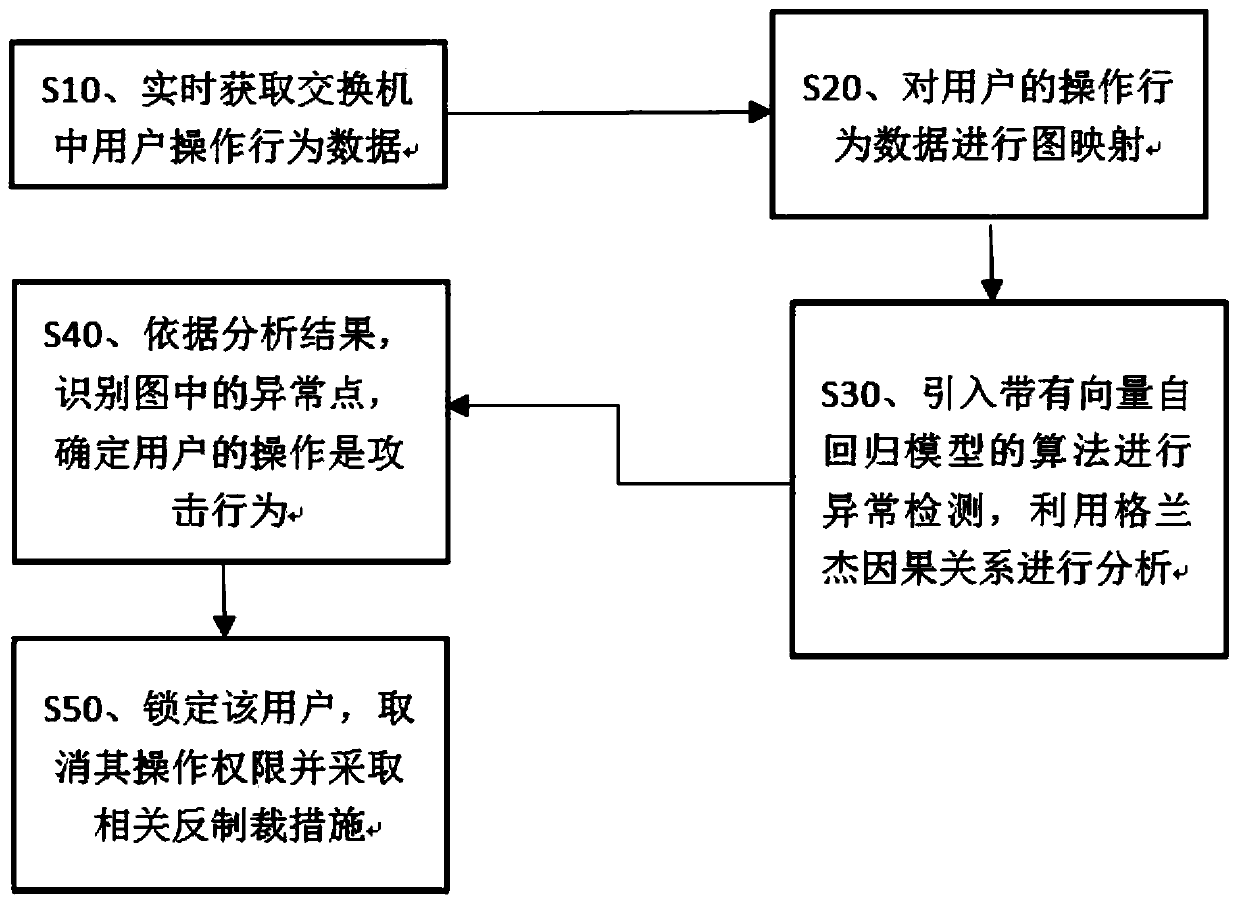
Switch data anomaly detection method based on vector autoregression model
ActiveCN110365708AAvoid misidentificationGood prevention effectData switching networksGraph mappingData set
The invention discloses a switch data anomaly detection method based on a vector autoregression model, and relates to the technical field of communication processing. Aiming at the defects of an existing anomaly detection method, the adopted technical scheme comprises the steps of obtaining operation behavior data of a login user in a switch in real time, and storing the operation behavior data ina data set; performing graph mapping on the operation behavior data contained in the data set, and converting the operation behavior data into a symbolic graph; for the symbolic graph, introducing analgorithm with a vector autoregression model to carry out anomaly detection, and carrying out analysis by utilizing a Granger causality; according to an analysis result, identifying abnormal points in the symbolic graph, and determining that the operation of the user belongs to an attack behavior; and locking the user, feeding a locking result back to the switch control part, and enabling the switch control part to cancel the operation authority of the user and take countermeasure. According to the method, improper behaviors of operation can be discovered in advance, wrong identification of normal users is avoided, and security holes in the industrial Internet are filled in a targeted manner.
Owner:SHANDONG INSPUR SCI RES INST CO LTD
Degree distribution histogram publishing method capable of meeting node differential privacy
ActiveCN110135180AReduce the impact of the distributionReduce Node Degree VariationImage enhancementDigital data protectionGraph mappingNODAL
The invention discloses a degree distribution histogram publishing method capable of meeting node differential privacy. The method comprises the step of carrying out graph mapping by adopting an edgeadding sequence; based on the observation, carrying out priority ranking based on the degrees of the nodes corresponding to the edges, wherein the smaller the sum of the degrees of the nodes is, the higher the priority is. The graph mapping optimization method disclosed by the invention has the beneficial effects that more edge information can be reserved, and the change of node degree is reduced.Meanwhile, a new histogram bucket division strategy is provided to reduce the influence of random noise added in the histogram publishing process on original data distribution.
Owner:SUZHOU UNIV
Graph isomorphism judging method based on spectrum analysis
ActiveCN104376139AThe result is accurateImprove efficiencySpecial data processing applicationsElectrical resistance and conductanceSimple graph
The invention belongs to the field of integrated circuits and relates to a graph isomorphism judging method based on spectrum analysis. The method includes: large-scale pure-resistor network graphs are modeled into non-mixing undirected simple graphs, two-dimensional planar graphs are mapped into one-dimensional distribution, and isomorphism of two graphs is judged according to processed one-dimensional distribution conditions. The method has the advantages that the method is accurate and fast in judging of the non-mixing undirected simple graphs, especially the large-scale non-mixing undirected simple graphs; the method is evidently faster than a Nauty method which is good in performance currently, and the method is well applicable to fields such as judging of identical sub-circuits in large-scale integrated circuits and judging the isomeride in organic chemistry.
Owner:FUDAN UNIV
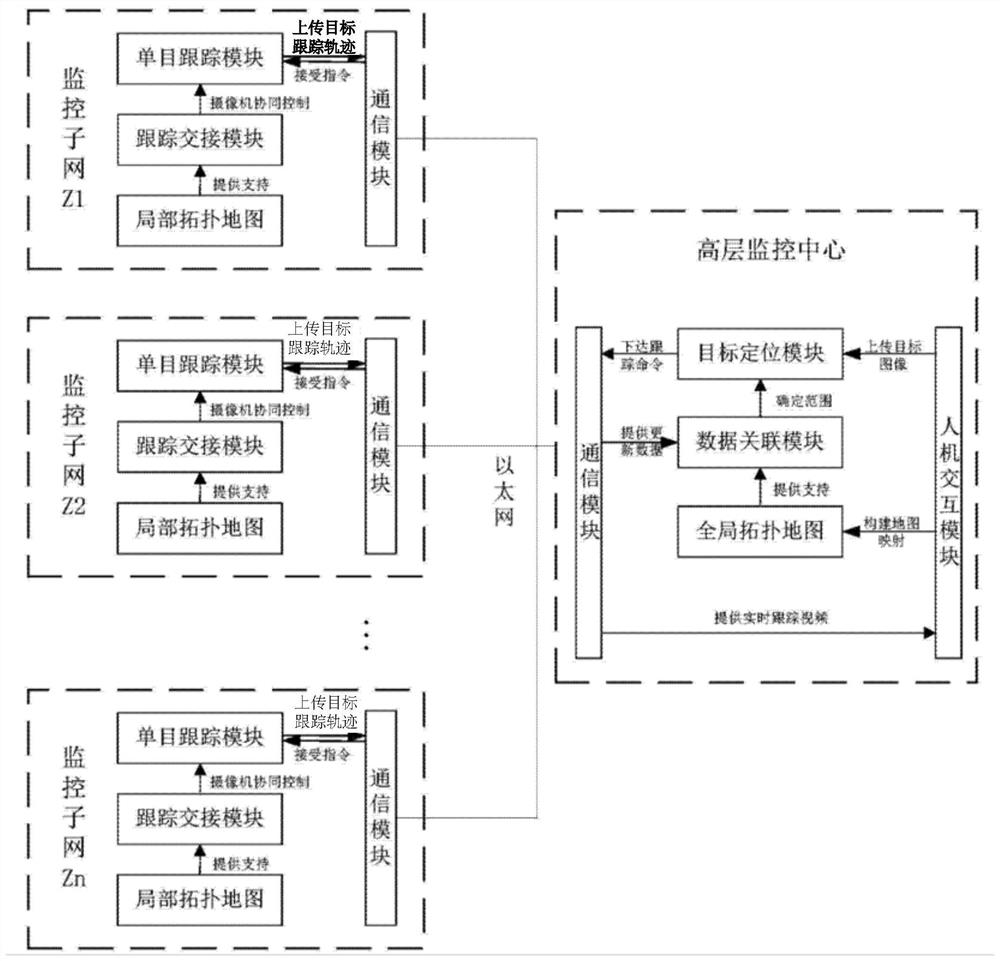
Multi-camera collaborative analysis method and system based on topological structure of network system
PendingCN112348856AHigh precisionAccurate trackingImage enhancementImage analysisGraph mappingGlobal topology
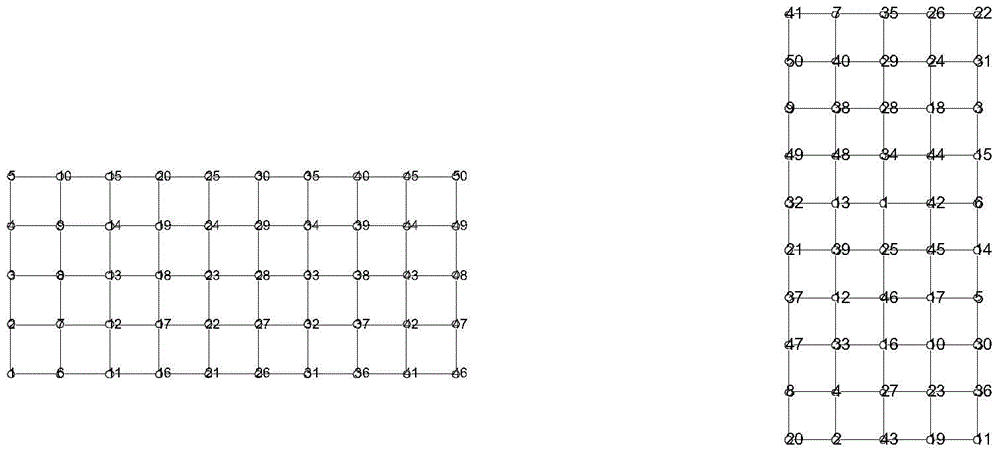
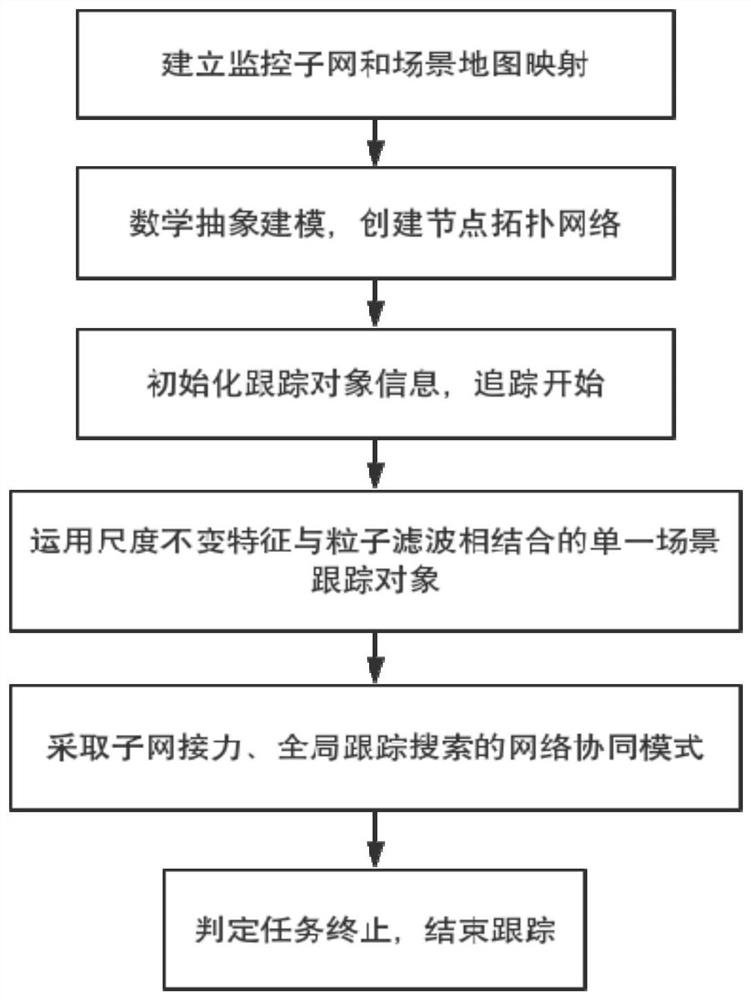
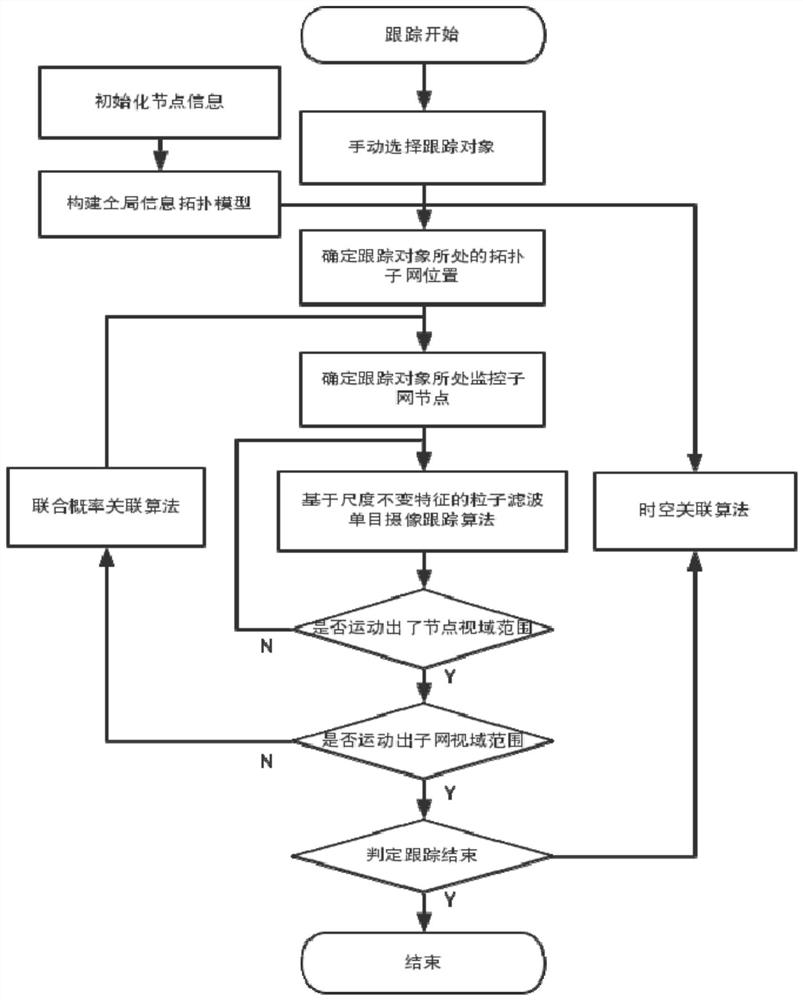
The invention discloses a multi-camera collaborative analysis method and system based on a topological structure of a network system, and the method comprises the steps: obtaining position informationof each camera and a monitoring subnet, and building the map mapping of the monitoring subnet and a global scene; carrying out mathematical abstract modeling on the monitoring subnet and the global scene map mapping to obtain a corresponding topology node connection graph; initializing tracking information, obtaining target information data, and determining the start of tracking; carrying out single-target tracking by adopting a particle filtering algorithm based on scale invariant features; adopting a hierarchical cascade tracking strategy and a joint data association algorithm in the topology subnet to cooperatively control each monitoring camera; searching in the global topological map by adopting a space-time association algorithm; and determining situations such as target tracking termination and loss, and stopping tracking. A suspicious target can be tracked across scenes, the system adopts a distributed hierarchical search method, the tracking cost is reduced, and the suspicious target can be tracked in real time.
Owner:盐城吉研智能科技有限公司
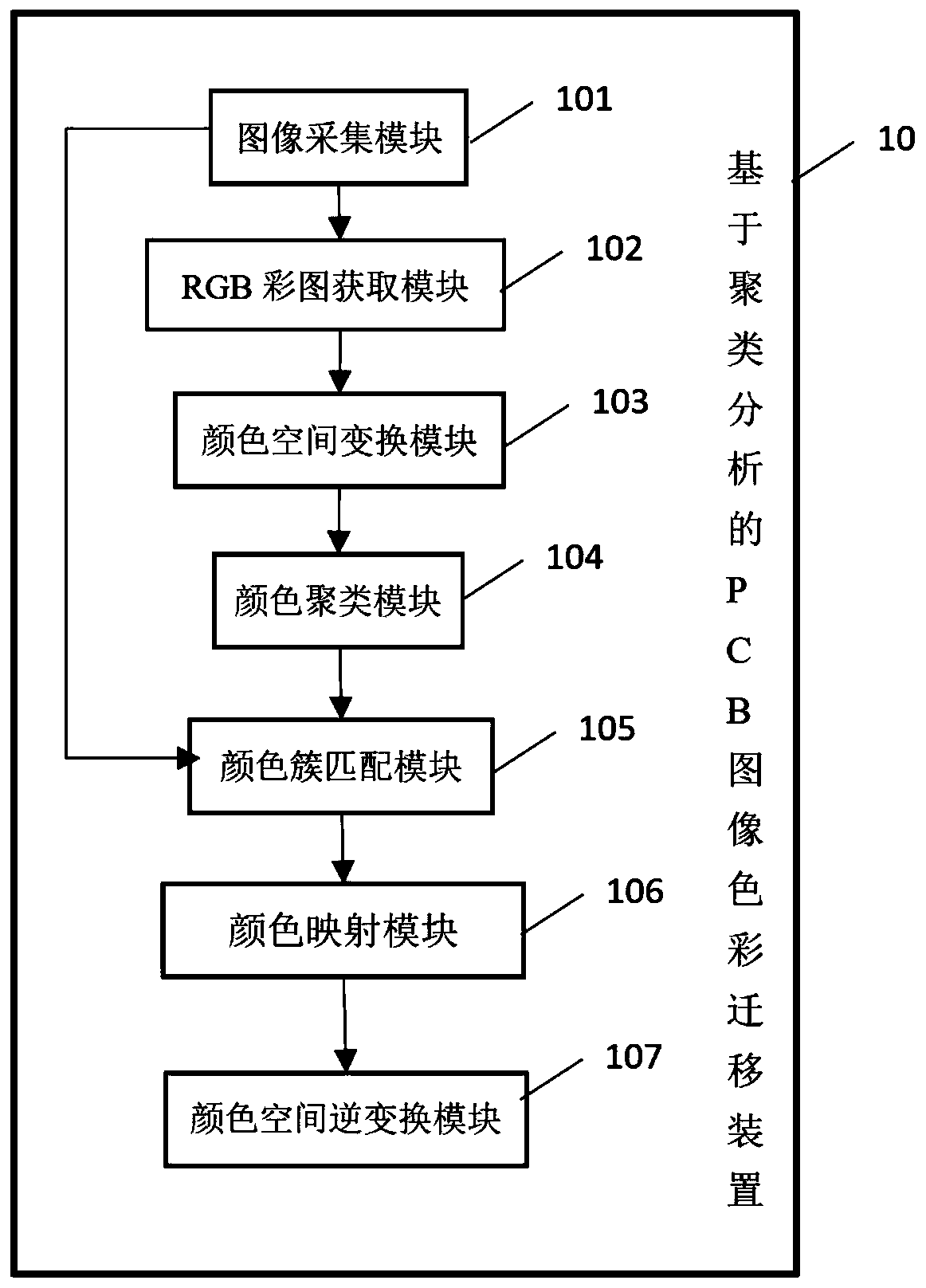
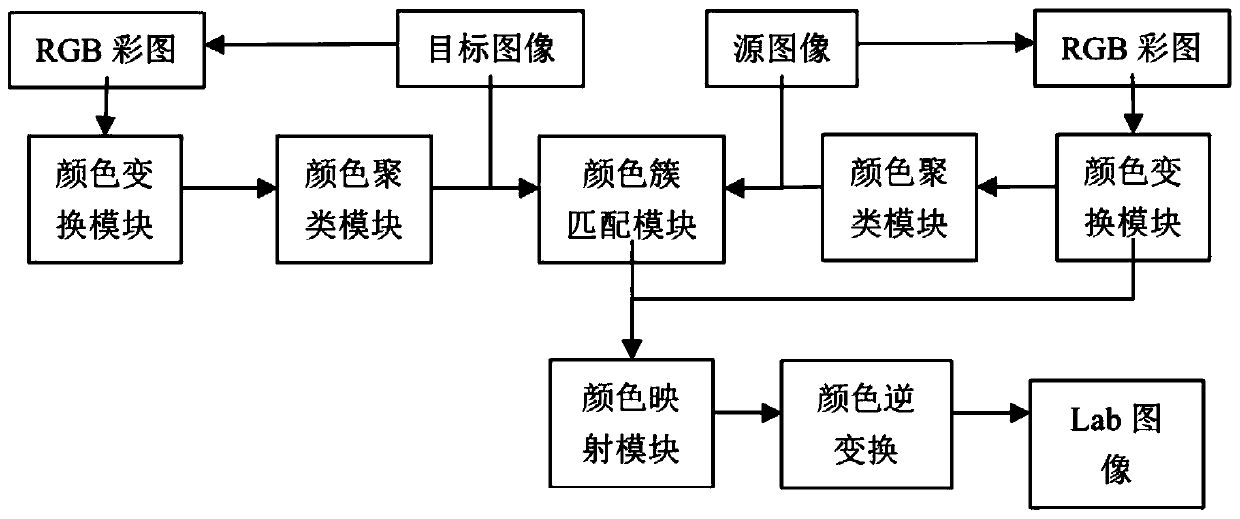
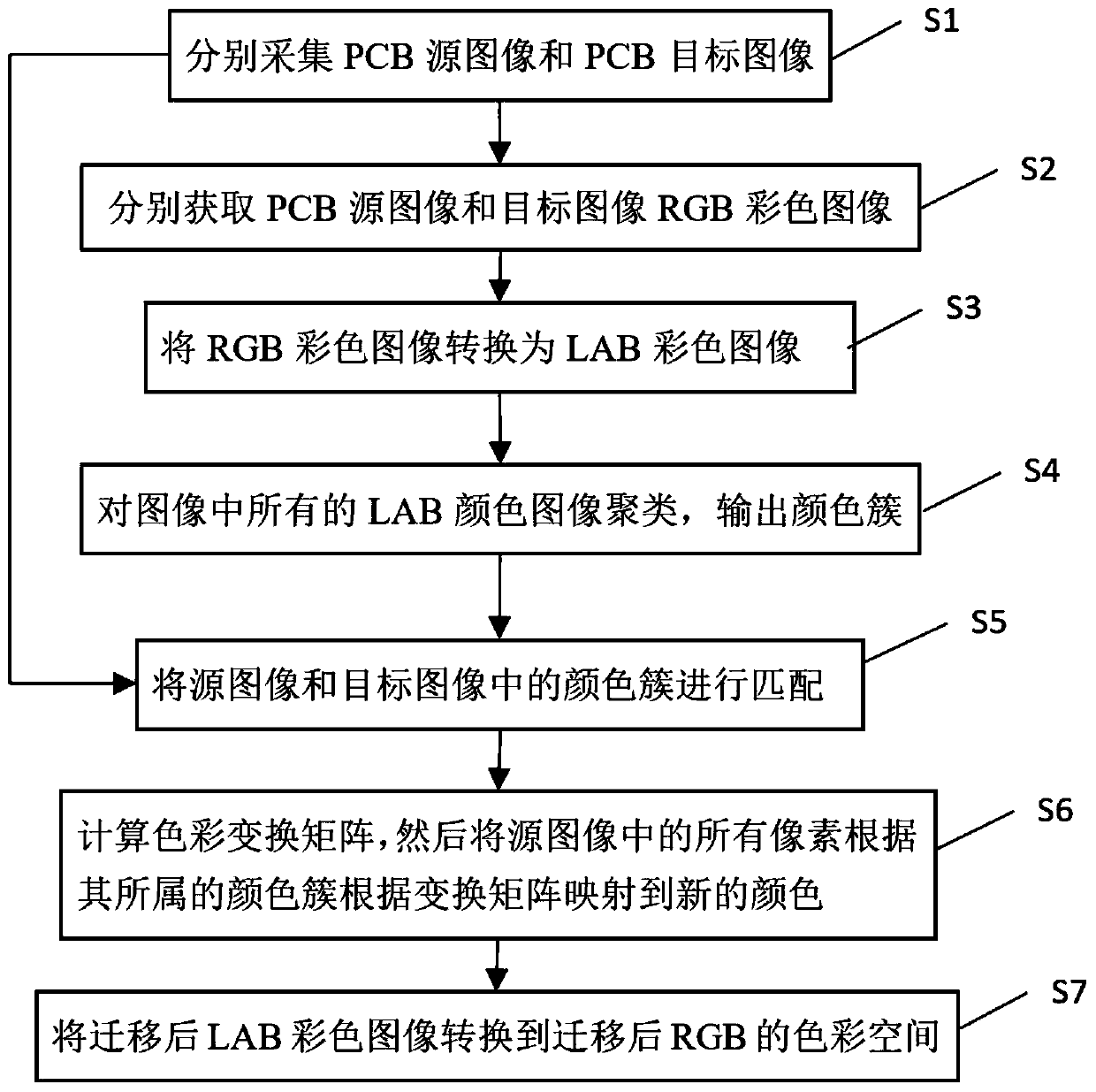
PCB image color migration device and method based on clustering analysis
ActiveCN111476831ARealize regulationImplement fixesImage analysisCharacter and pattern recognitionPattern recognitionColor image
The invention provides a PCB image color migration device and method based on clustering analysis, and the device comprises an image collection module which obtains a source image and a target image;a RGB color image acquisition module which is used for respectively acquiring RGB color images converted from the source image and the target image; a color space conversion module which converts theRGB color image into an LAB color image; a color clustering module which is used for setting and clustering the LAB color images by utilizing the number of color clusters to generate a color cluster category list; a color cluster matching module which performs PCB bipartite graph matching on the list of the source image and the target image to obtain a matching result; a color mapping module whichcalculates a transformation matrix according to a matching result, and maps the LAB color image to a new color according to the matrix; and a color space inverse transformation module which convertsthe mapped color into an image after RGB color migration. According to the device, colors in an image are divided into different categories by clustering, color migration is carried out on the colorsof the different categories respectively, and a good image registration effect is achieved.
Owner:TSINGHUA UNIV
Neural network weight initialization method based on transfer learning
ActiveCN111126599AGood weight initializationGood global convergenceImage codingDigital video signal modificationGraph mappingAlgorithm
The invention belongs to the technical field of neural network models, and particularly relates to a neural network weight initialization method based on transfer learning. According to the method, for a specified target task, a neural network model, namely a teacher model, with high complexity is designed, the teacher model is trained, and after training is completed, a generated feature graph isused for guiding weight initialization of a student model; the difference between the feature maps is calculated or the feature maps are mapped into a regeneration kernel Hilbert space, the difference of the feature maps in the regeneration kernel Hilbert space is calculated, and the calculation is simplified by adopting a kernel function method. According to the method, a simple student model isenabled to achieve a better weight initialization effect, and general training is performed on the student model after weight initialization is completed so that the student model is enabled to achieve a better global convergence point and the performance of the student model is enabled to be more excellent. According to the method, the performance of the student model can be effectively improvedon the premise of not increasing the complexity of the student model.
Owner:FUDAN UNIV
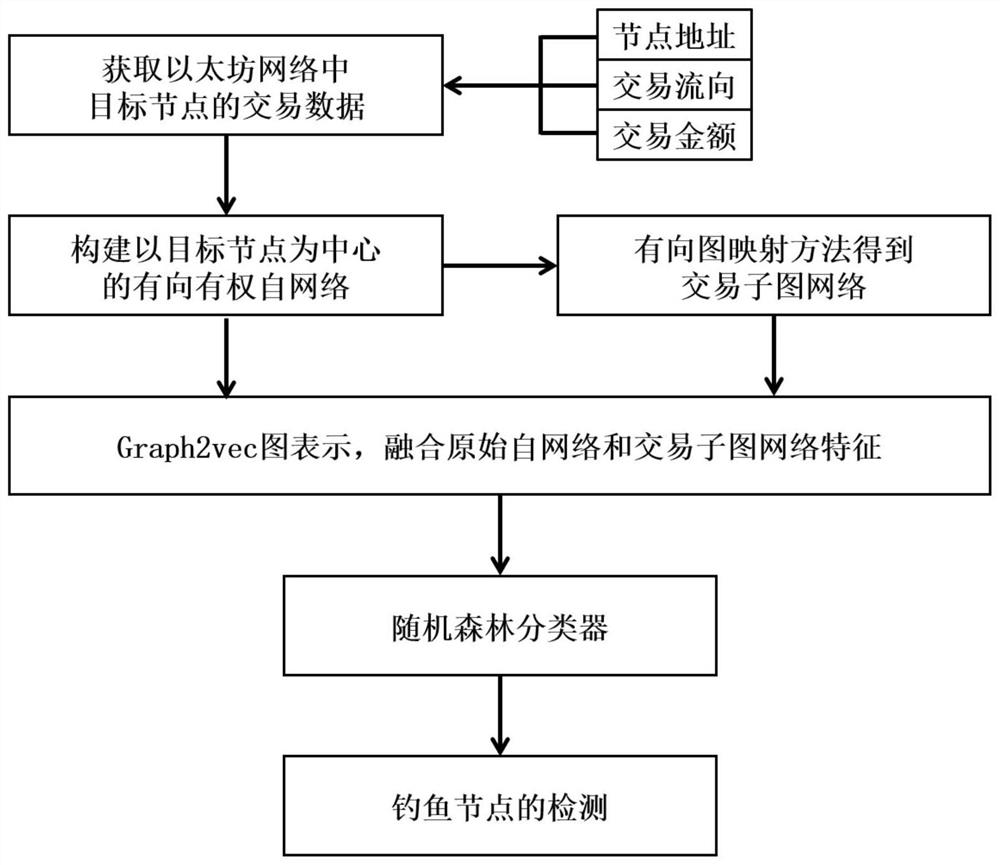
Transaction subgraph network-based Ethereum phishing node detection method and system
ActiveCN113364748AReduce workloadImprove detection accuracyFinanceCharacter and pattern recognitionGraph mappingNetwork Convergence
An Ethereum phishing node detection method based on a transaction subgraph network comprises the following steps: 1) acquiring data; 2) constructing a network, and constructing a target node self-network according to transaction information of an Ethereum external account; 3) performing graph mapping: processing the self-network according to a novel directed graph mapping method to obtain a mapping graph containing intrinsic implicit information, namely a transaction sub-graph network; 4) performing graph feature extraction and fusion: performing feature extraction on the original self-network and the transaction sub-graph network by using a Graph2vec model, and splicing the features of the original self-network and the transaction sub-graph network; 5) classifying a detection model, taking the network fusion features as input, and training a random forest model to detect the phishing attribute of the target node. The invention further discloses an accurate fishing fraud detection system based on the method. According to the method, the self-network is constructed, the corresponding graph mapping technology is combined, the phishing node detection task is lightly and accurately completed, and the method is different from most researches based on extraction of a large amount of or higher-order neighbor information.
Owner:ZHEJIANG UNIV OF TECH
Cloud services creation based on graph mapping
A method for service creation based on graph mapping including constructing a graph having leaf nodes in an environment including business support nodes associated with respective services and operations support nodes including attribute models, identifying a plurality of services at a level of the leafs in the graph, extending the graph by representing existing services offerings in terms of operation level service definitions and new services at the level of the leafs, and re-combining leaf nodes to define new services at service creation time.
Owner:INT BUSINESS MASCH CORP
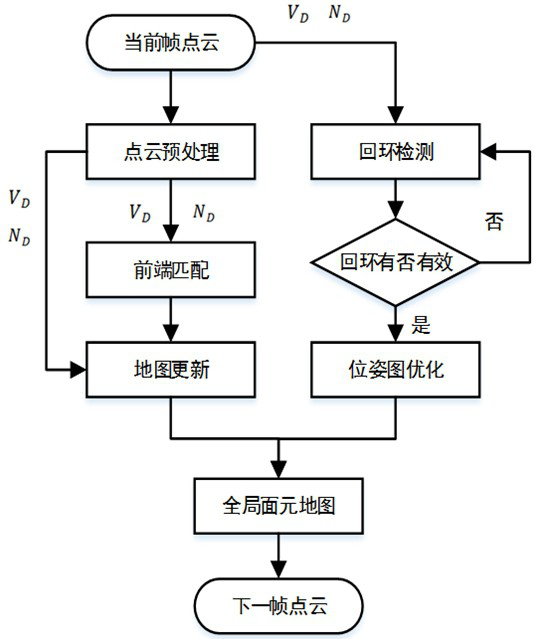
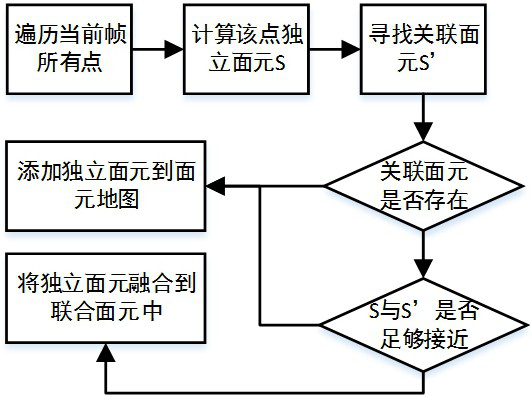
Semantic segmentation method and system for removing dynamic objects
ActiveCN113570629AReliable Semantic SLAM MappingStable Semantic SLAM MappingImage enhancementImage analysisGraph mappingImaging processing
The invention belongs to the field of image processing, and provides a semantic segmentation method and system for removing dynamic objects. The semantic segmentation method comprises the following steps: acquiring a scene 3D point cloud, projecting the scene 3D point cloud into a 2D depth map, calculating normal vector information of the point cloud, and constructing a surface element map with a loop; carrying out point cloud semantic segmentation on the surface element map with the loop, constructing a semantic point cloud map, mapping the semantic point cloud map to a 3D point cloud map, and removing edge shadows and point cloud discretization phenomena; and removing the dynamic object by utilizing semantic point cloud information in the semantic point cloud map, and adding semantic iteration nearest point constraint to obtain an optimized semantic point cloud map.
Owner:SHANDONG UNIV +1
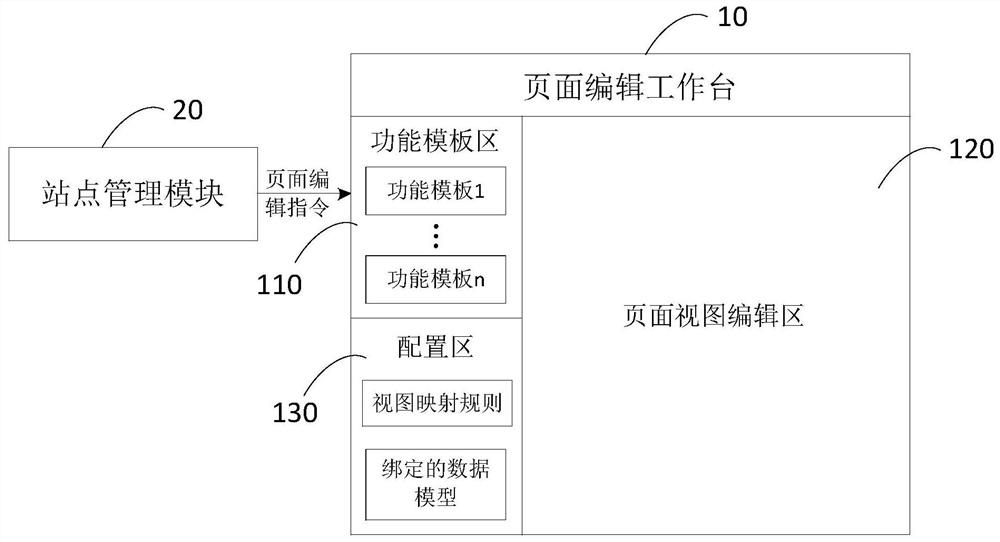
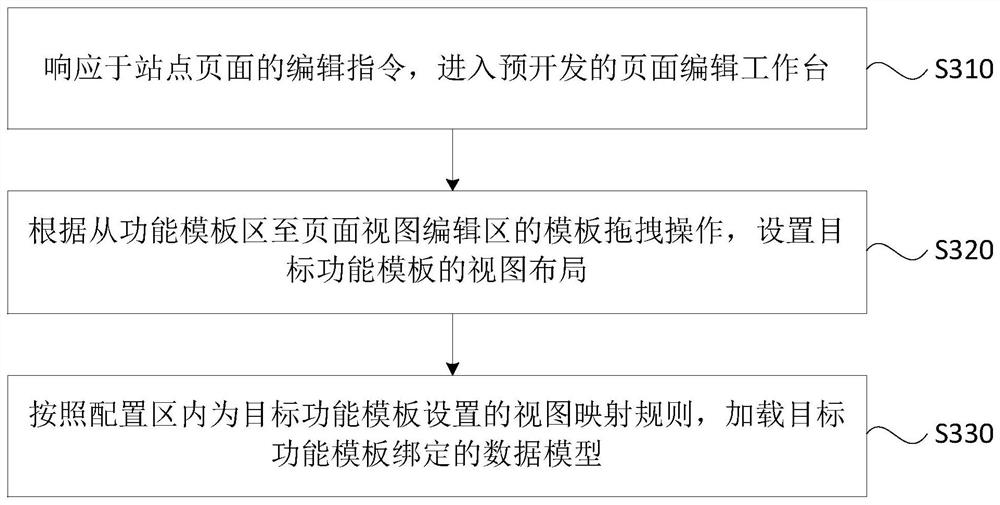
Site page processing system, method and equipment and storage medium
PendingCN113448569AImprove the convenience of optimizationAchieve separationVisual/graphical programmingGraph mappingSoftware engineering
The embodiment of the invention discloses a site page processing system and method, equipment and a storage medium. The system comprises a page editing workbench, wherein the page editing workbench comprises a function template area, a page view editing area and a configuration area; the function template area is provided with function templates supported in different site pages; the page view editing area is used for setting a view layout of a target function template; the target function template is a function template dragged from the function template area to the page view editing area; the configuration area is used for setting a view mapping rule of the target function template and loading a data model bound with the target function template according to the view mapping rule. According to the technical scheme provided by the embodiment of the invention, complete function separation between the front-end view and the rear-end data in the site page is realized, and a developer does not need to specially write configuration codes between the view of each component template in the site page and the data model, so that the optimization convenience of the site page is improved.
Owner:TIANWEN DIGITAL MEDIA TECH HUNAN
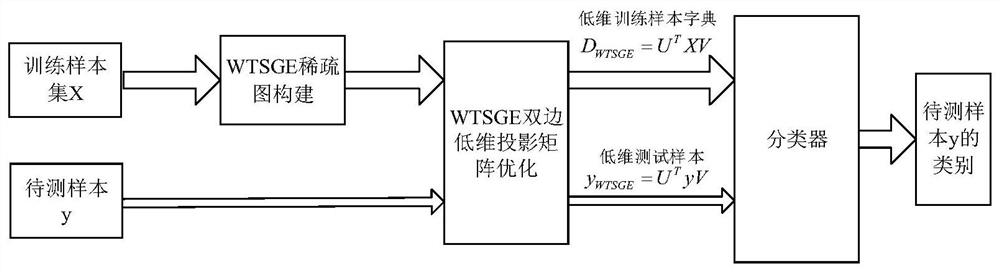
Unconstrained face recognition method based on weighted tensor sparse graph mapping
ActiveCN111723759ARetain internal structure informationOvercoming the Curse of DimensionalityInternal combustion piston enginesCharacter and pattern recognitionGraph mappingAlgorithm
The invention discloses an unconstrained face recognition method based on weighted tensor sparse graph mapping, and relates to the technical field of face recognition methods. In the sparse graph construction stage, training samples (images) are represented by second-order tensors, a supervised over-complete tensor dictionary is constructed, and similar sparse reconstruction coefficients of the samples are optimized and solved; and a more accurate tensor sparse neighbor graph is constructed in a self-adaptive manner. In a bilateral low-dimensional projection stage, low-dimensional tensor subspace distribution is obtained by utilizing identification information implied in sample global distribution. And low-dimensional mapping yWTSGE = UTyV is performed on the to-be-tested sample y by adopting the optimal WTSGE bilateral projection matrixes U and V, and a classifier is trained by using a low-dimensional training sample DWTSGE = UTXV to realize accurate identity authentication of the non-constrained face. According to the method, the complexity of the non-constrained face image data is fully considered, the neighbor distribution diagram of the high-dimensional tensor data is obtainedin a self-adaptive mode through the sparse representation technology, the low-dimensional manifold essential structure of the highly-distorted non-constrained face data is effectively extracted, andthe accuracy of non-constrained face recognition is greatly improved.
Owner:NANJING INST OF TECH
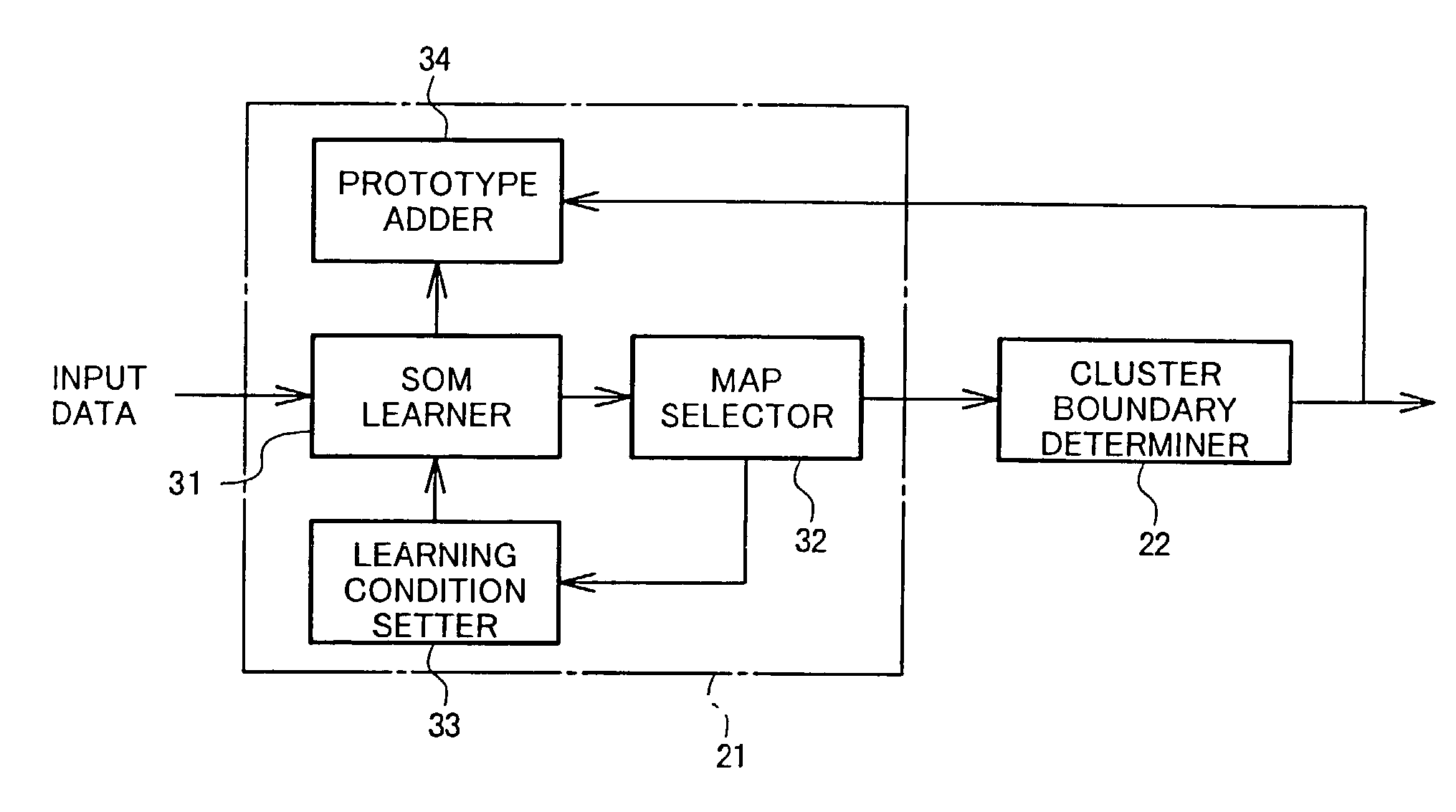
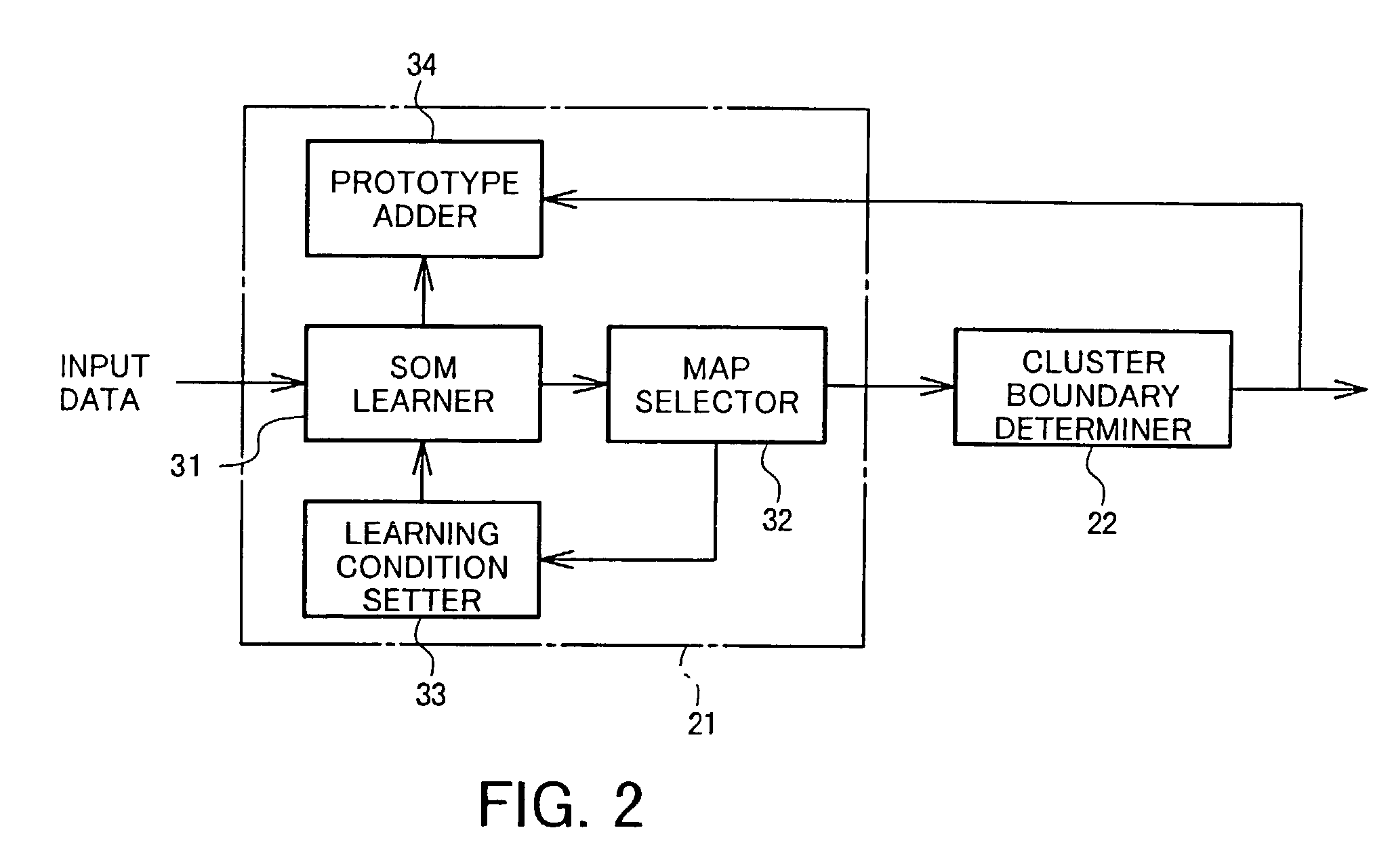
Data classifier using learning-formed and clustered map
Owner:FUJIFILM BUSINESS INNOVATION CORP
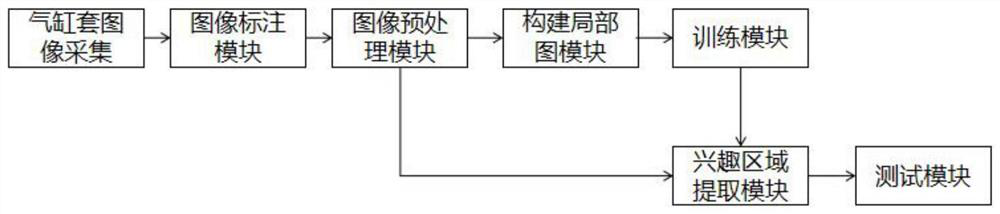
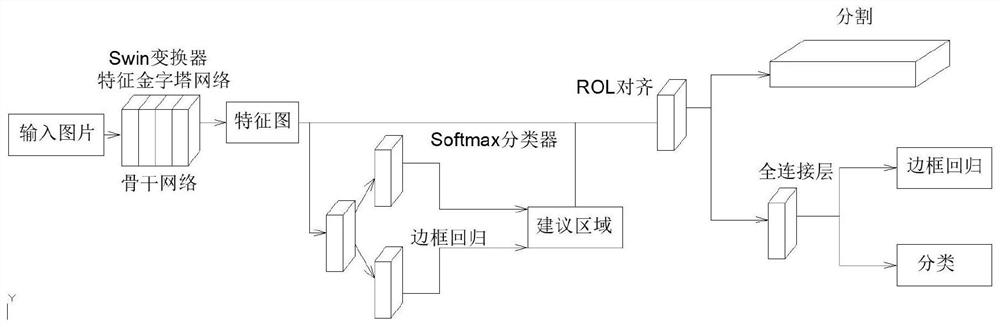
Cylinder sleeve defect mark detection method based on deep learning
PendingCN114549446AReduce search timeHigh precisionImage enhancementImage analysisGraph mappingAlgorithm
The invention provides a cylinder sleeve defect mark detection method based on deep learning, and the method comprises the following steps: collecting a cylinder sleeve image to construct an original data set, carrying out the preprocessing and marking of the images in the original data set, and obtaining a local defect graph of a training set; carrying out modeling by using a Mask R-CNN algorithm based on a Swin converter to obtain a network model; detecting the images of the test set through the obtained network model; extracting a region of interest from a detection result through a mask mechanism to enhance a detection effect; evaluating the detection performance of the network model; and performing defect mark detection on the acquired cylinder sleeve image through the obtained network model. According to the invention, through image preprocessing, cylinder liner noise influence reduction, local graph construction of an original graph, obtaining of a new batch of training data, through a method of mapping a large graph with a small graph, obtaining of a detection result of the original graph, through a mask mechanism, filtering of a noise area, and improvement of small target detection precision.
Owner:NANJING INST OF TECH
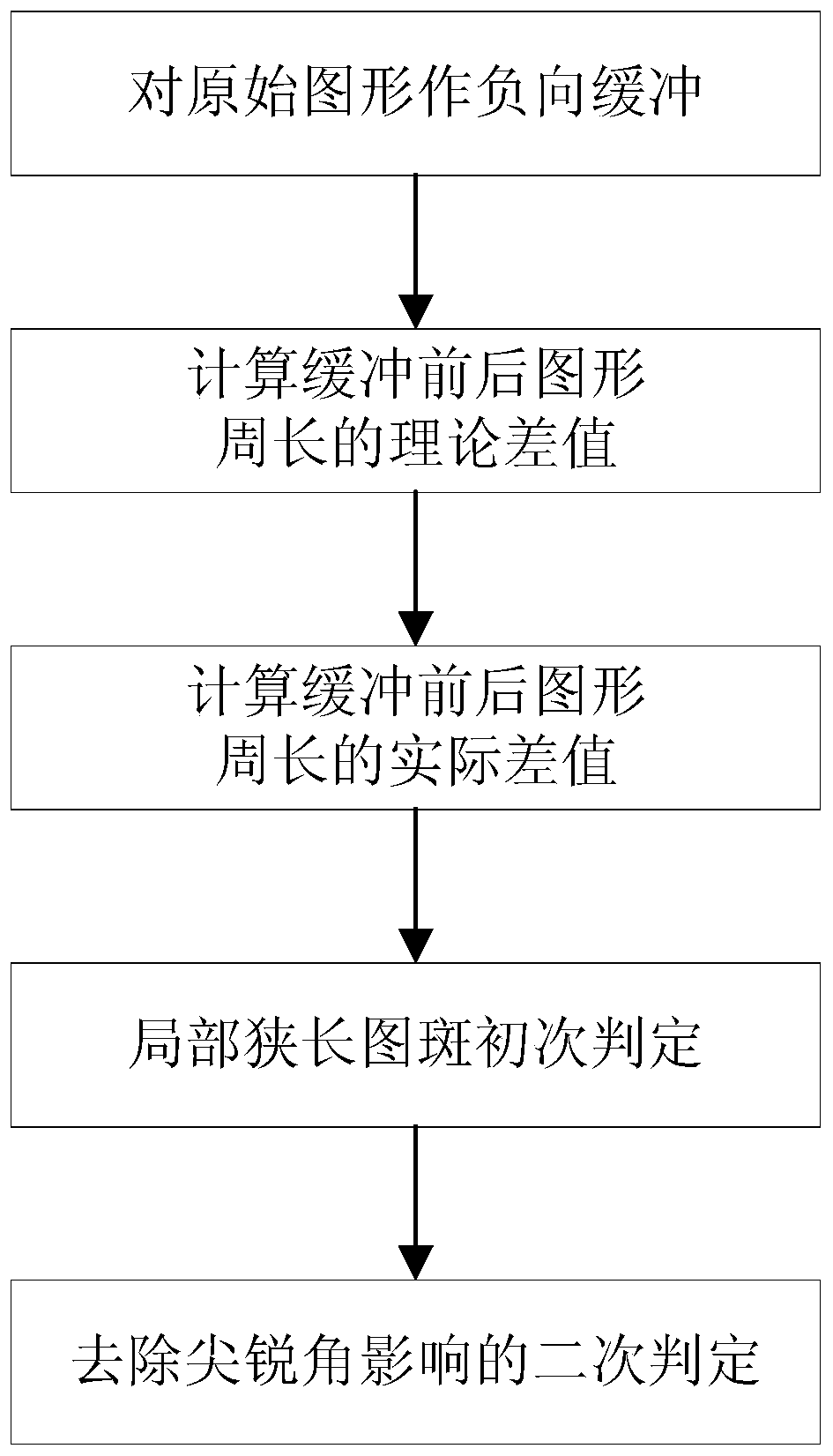
Method for detecting local long and narrow land utilization vector graph
ActiveCN111340757AWiden perspectiveImprove methodImage analysisVectoral format still image dataGraph mappingGraphics
The invention discloses a method for detecting a local long and narrow land utilization vector graph. The method comprises the following steps of: negatively buffering an original graph; calculating atheoretical difference value of the perimeter of the graph before and after buffering; calculating an actual difference value of the perimeter of the graph before and after buffering; and judging thelocal long and narrow pattern spots according to the relationship between the perimeter theoretical difference value and the actual difference value. By means of the method, on one hand, a formula for effectively calculating the theoretical difference value of the perimeter of the graph before and after buffering is provided, and the view angle and method of graph research are expanded; and on the other hand, the local long and narrow graph can be automatically detected through a computer program without depending on manual visual identification, so that non-standard graph mapping is effectively avoided, and the data quality is improved.
Owner:中国国土勘测规划院
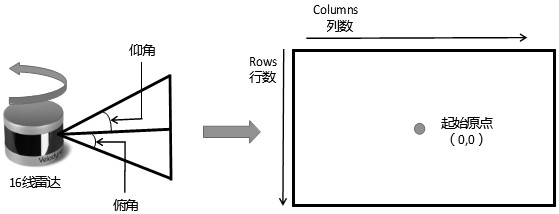
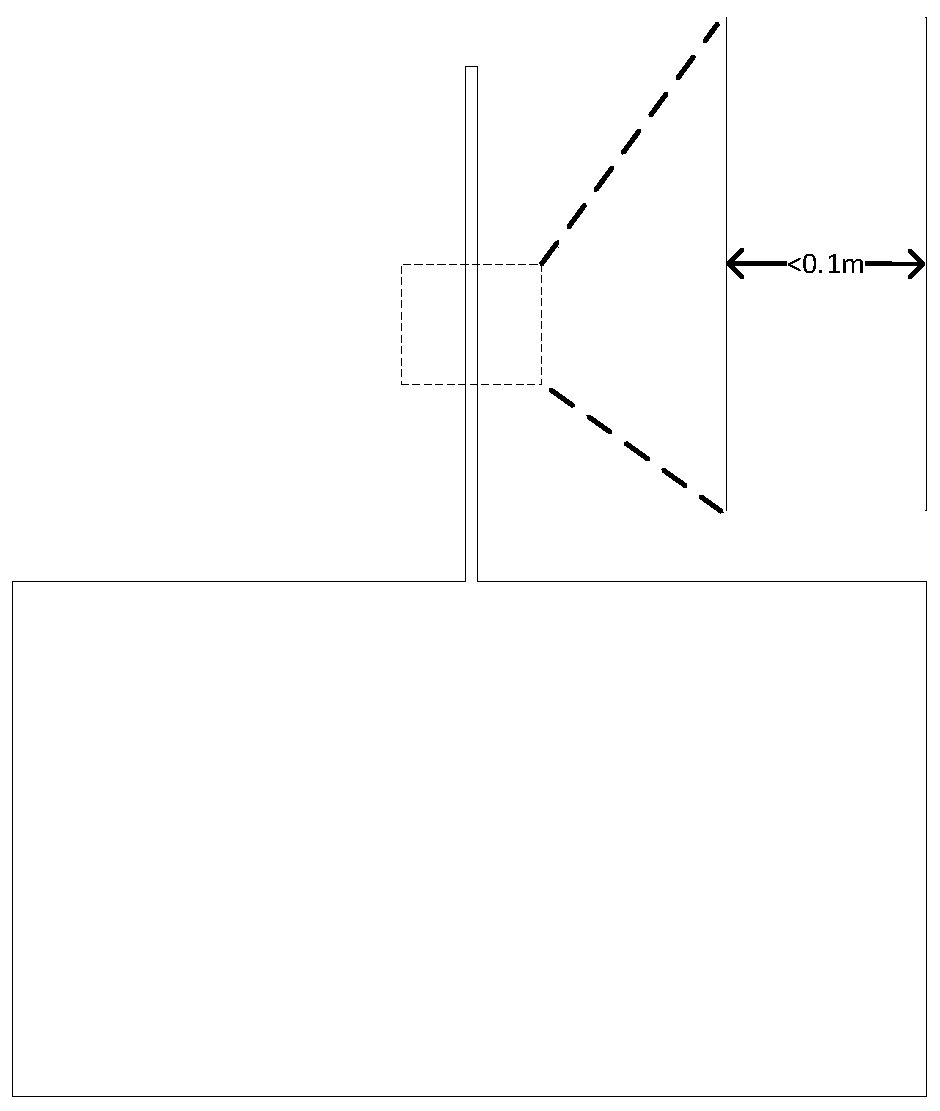
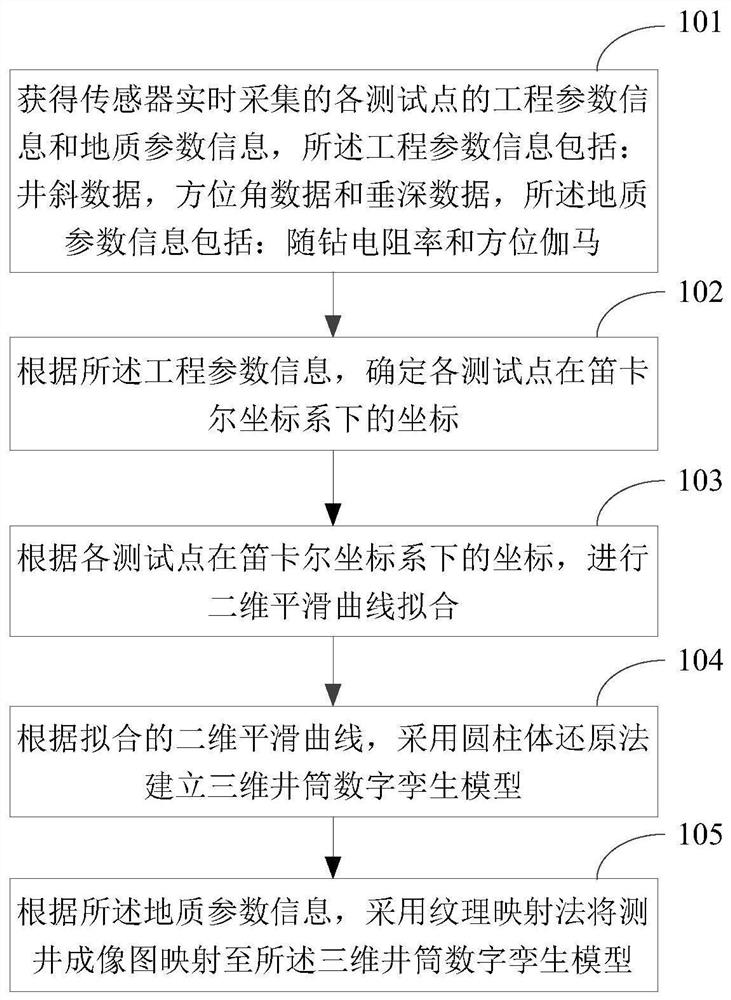
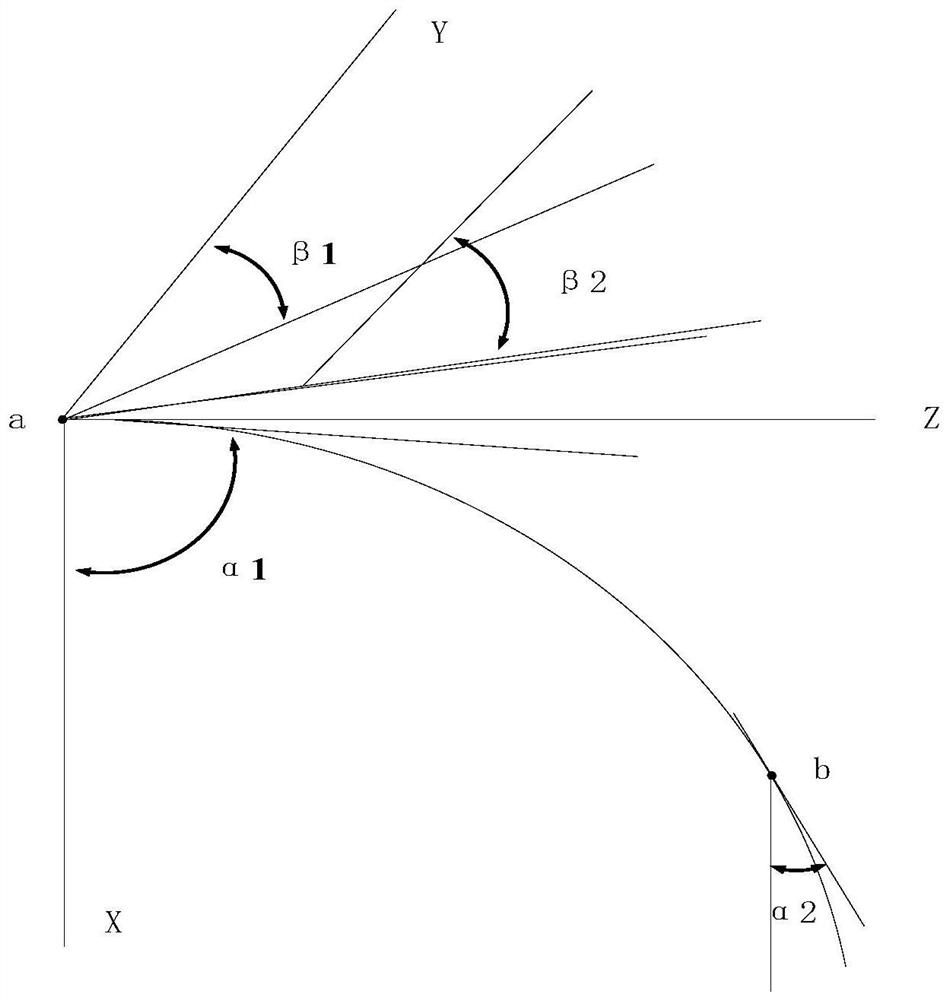
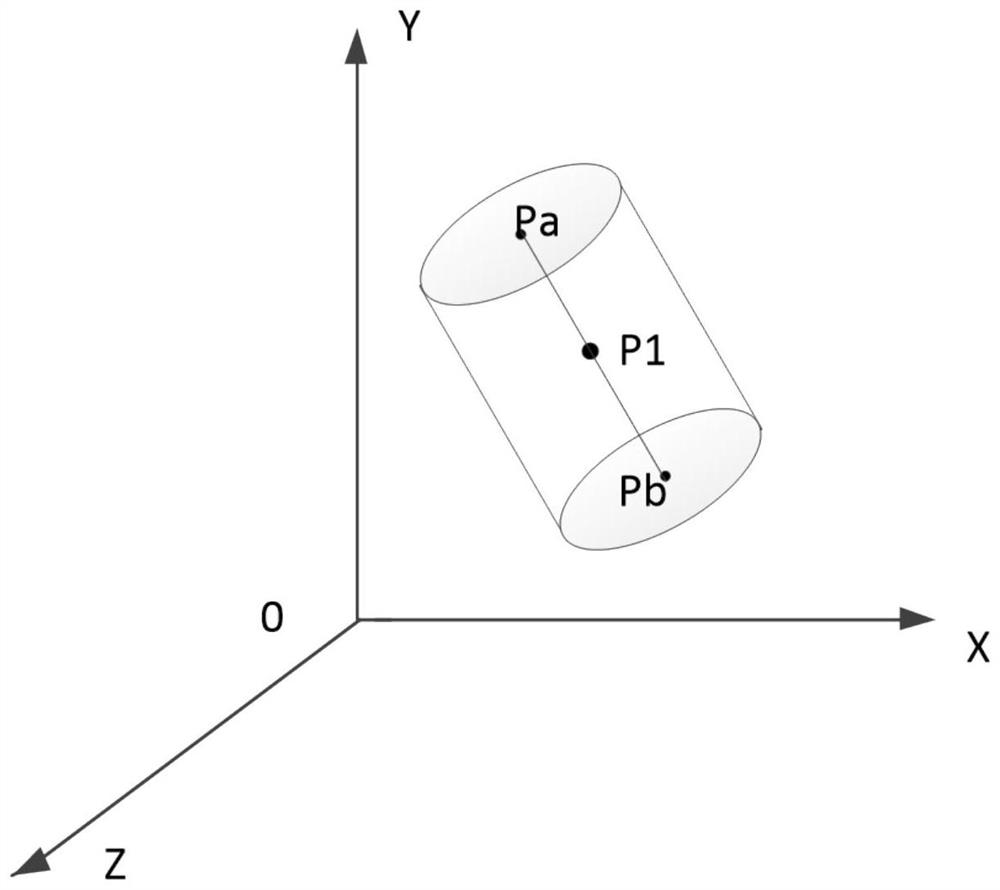
Shaft three-dimensional visualization method and device
PendingCN114758056ARealize 3D visualizationLower Drilling Costs3D modellingGraph mappingDimensional simulation
The invention discloses a shaft three-dimensional visualization method and device.The method comprises the steps that engineering parameter information and geological parameter information, collected by a sensor in real time, of all test points are obtained, the engineering parameter information comprises well deviation data, azimuth angle data and vertical depth data, and the geological parameter information comprises resistivity while drilling and azimuth gamma; determining coordinates of each test point in a Cartesian coordinate system according to the engineering parameter information; performing two-dimensional smooth curve fitting according to the coordinate of each test point in the Cartesian coordinate system; according to the fitted two-dimensional smooth curve, establishing a three-dimensional shaft digital twinborn model by adopting a cylinder reduction method; and according to the geological parameter information, mapping a logging imaging graph to the three-dimensional shaft digital twinborn model by adopting a texture mapping method. Three-dimensional visualization of the shaft can be achieved, and important reference is provided for engineering application such as well track monitoring, shaft three-dimensional simulation and well collision prevention.
Owner:BC P INC CHINA NAT PETROLEUM CORP +2
Graph similarity calculation method and device based on graph convolution network
InactiveCN112529057AImprove effectivenessCharacter and pattern recognitionNeural architecturesGraph mappingAlgorithm
The invention discloses a graph similarity calculation method and device based on a graph convolution network, can overcome the defect that an existing GNN-based graph similarity calculation model cannot well learn the hierarchical structure of a graph, and improves the effectiveness of graph similarity calculation by combining the flatness and hierarchical representation of the graph together within reasonable time. Specifically, the embodiment of the invention provides a function which completely supports back propagation and is based on an end-to-end ground neural network, each part of thefunction is carefully designed, so that the function can learn flat and hierarchical information of graphs, and finally, a pair of graphs is mapped into similarity scores. The defects that in the prior art, consumed time is long, and the hierarchical structure of a graph cannot be captured are overcome.
Owner:SUN YAT SEN UNIV
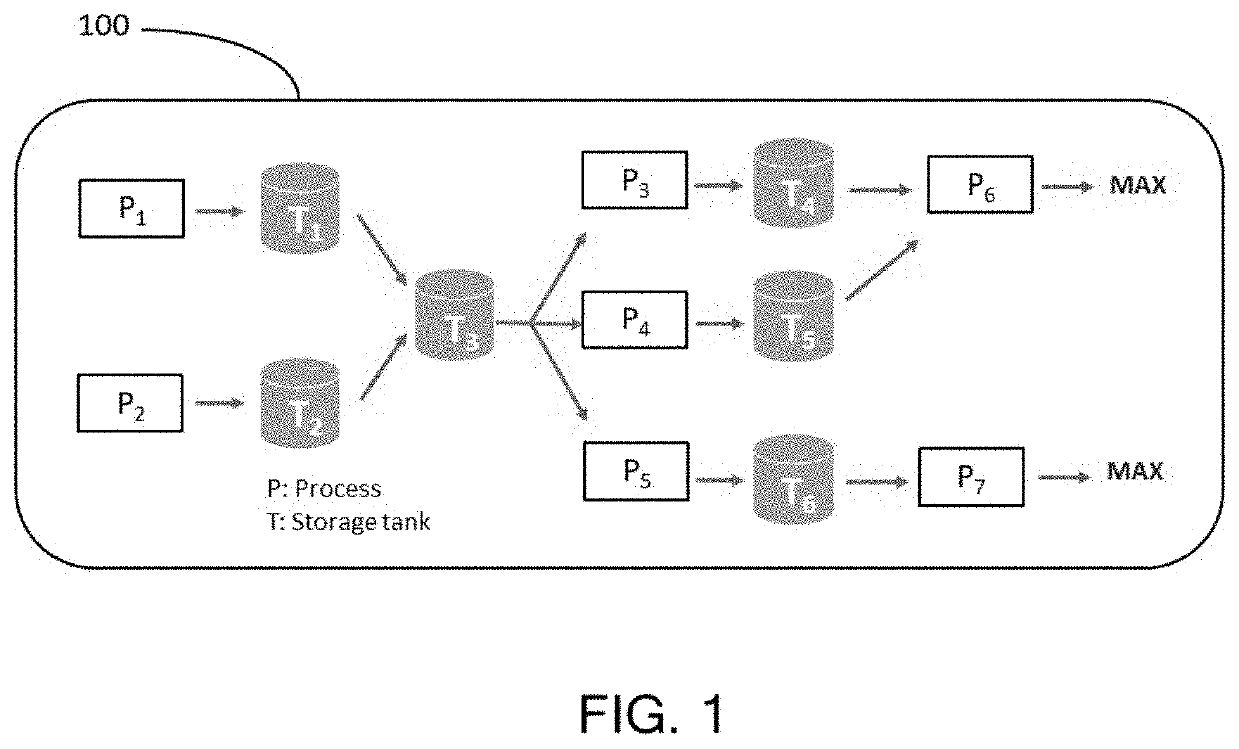
Automated generation of optimization model for system-wide plant optimization
PendingUS20220027685A1Improve computing efficiencyShort calculation timeEnsemble learningForecastingGraph mappingTheoretical computer science
A computer implemented method for automatically generating an optimization model for site-wide plant optimization includes mapping a process flow diagram of a plant process to a graph comprising nodes and edges, wherein the nodes represent processes and the edges represent flows between processes. A behavior is learned for each node of the graph based at least on historic data of the plant process. One or more regression functions are modeled for each node to predict an output of each of the processes, wherein the one or more regression functions are modeled based on the learned behavior for each node.
Owner:IBM CORP
Application system performance bottleneck determination method and device, equipment and medium
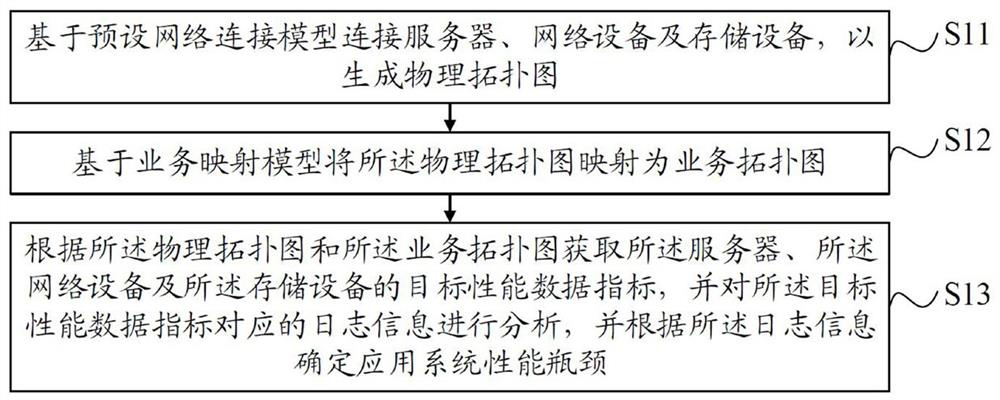
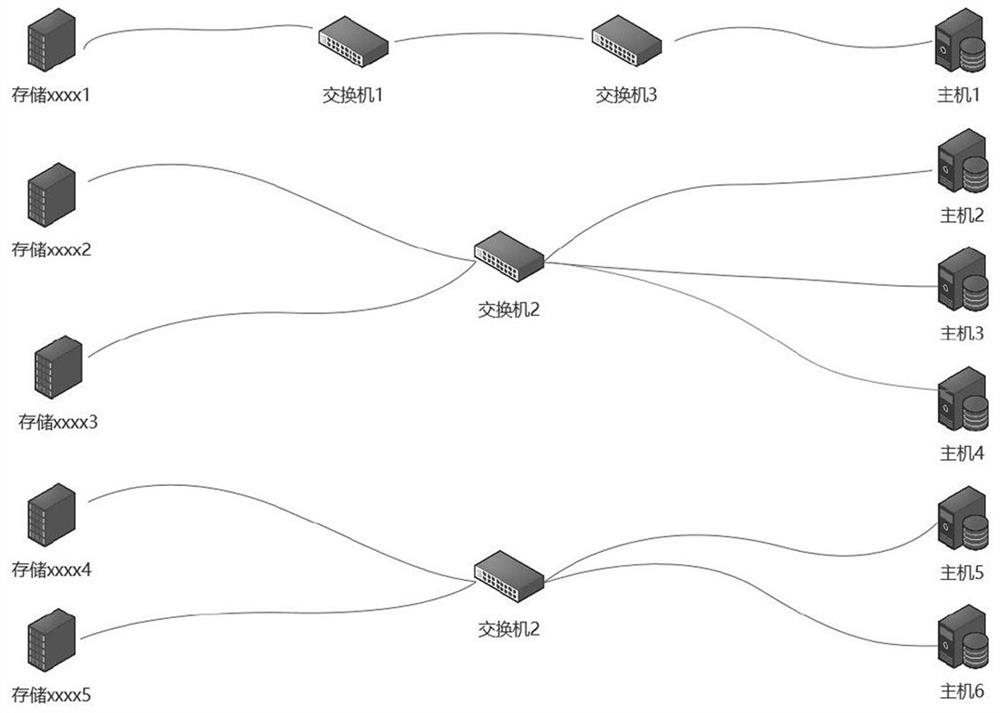
ActiveCN114553672AImproved ease of maintenanceImprove stabilityTransmissionGraph mappingComputer network technology
The invention discloses an application system performance bottleneck determination method, and relates to the technical field of computer networks, and the method comprises the steps: connecting a server, network equipment and storage equipment based on a preset network connection model, so as to generate a physical topological graph; mapping the physical topological graph into a service topological graph based on a service mapping model; and obtaining target performance data indexes of the server, the network equipment and the storage equipment according to the physical topological graph and the service topological graph, analyzing log information corresponding to the target performance data indexes, and determining the performance bottleneck of the application system according to the log information. According to the invention, the performance bottleneck of the application system is determined through the monitored log information of all performance fault suspicious points, and analysis is carried out according to the performance bottleneck of the server, the network equipment and the storage equipment, so that the performance analysis time is greatly shortened, the fault positioning and solving efficiency is improved, and the user experience is improved. And the maintainability and the stability of the application system are further improved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
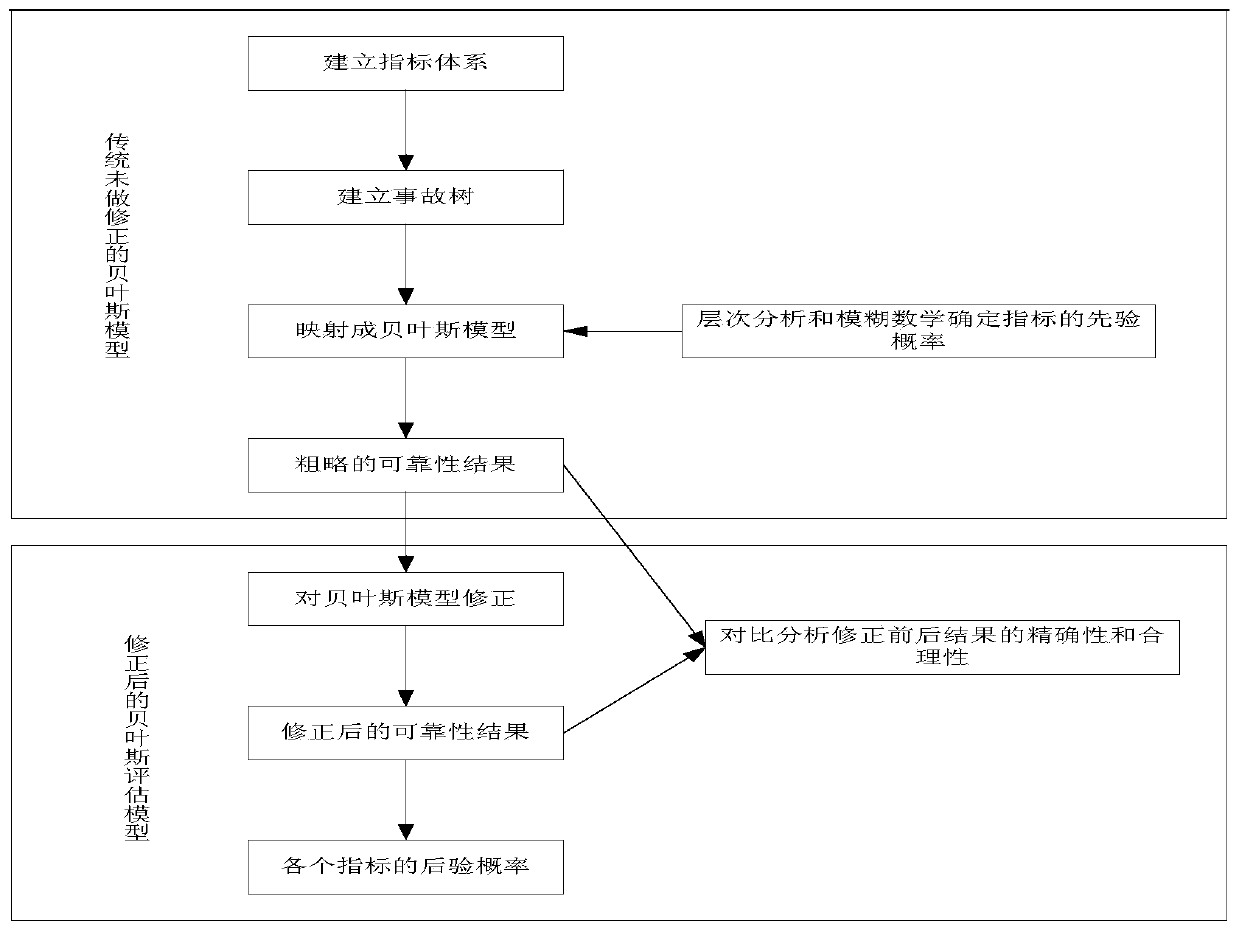
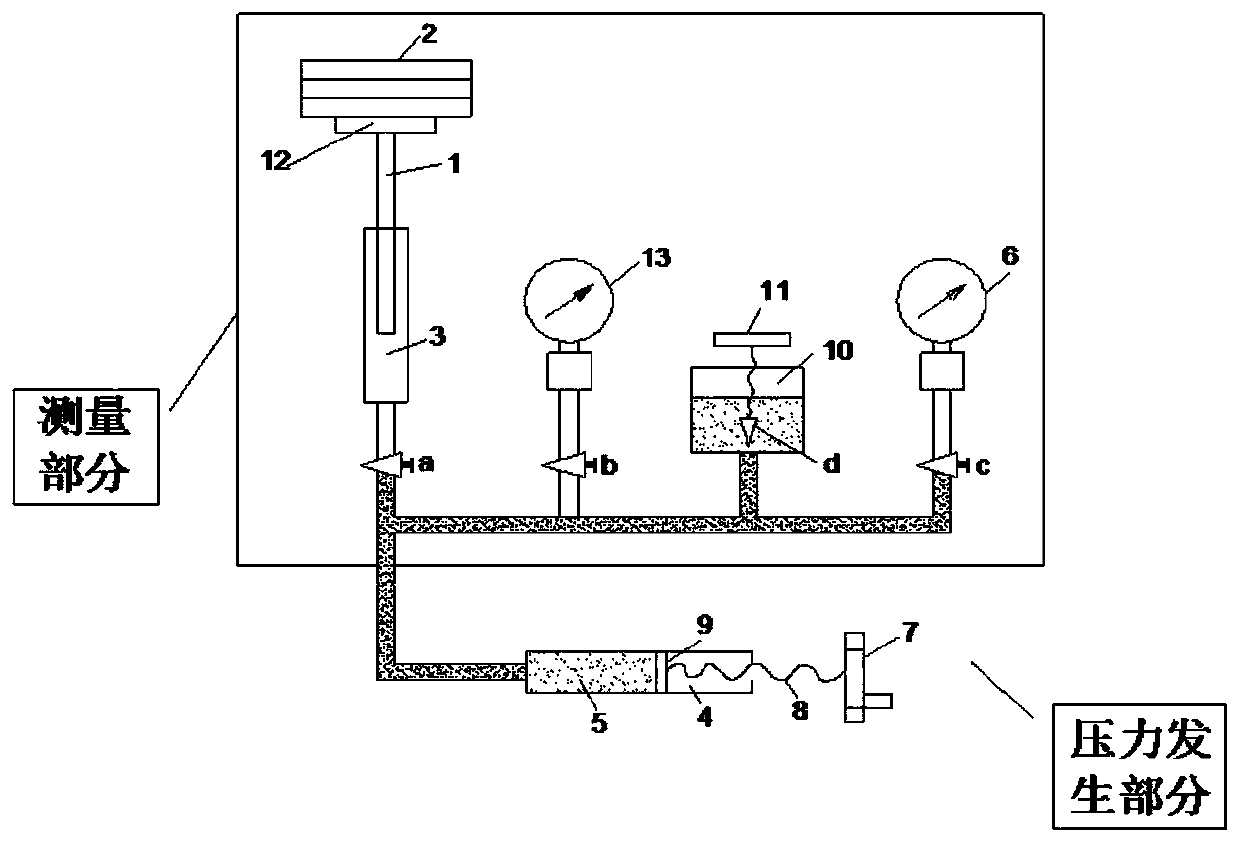
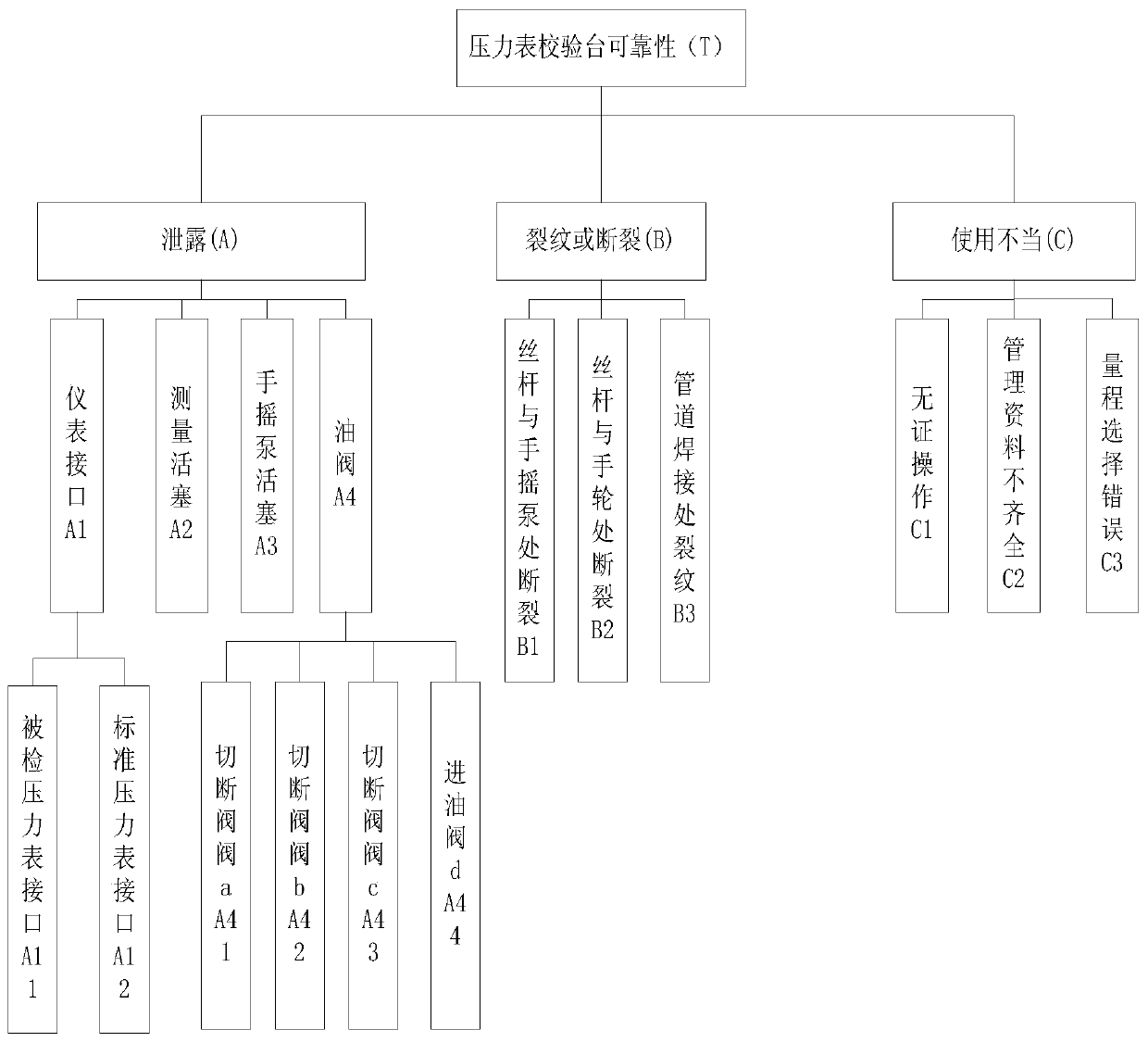
Pressure gauge calibration table reliability evaluation method based on Bayesian correction model
The invention discloses a pressure gauge calibration table reliability evaluation method based on a Bayesian correction model. The method comprises the following steps: establishing a fault characteristic index system capable of representing a pressure gauge calibration table; constructing an accident tree model of the pressure gauge calibration console; establishing a BN model graph of the pressure gauge calibration console, and directly mapping the FTA model graph into the BN model graph through a graph mapping method; determining a prior probability of a bottom event and a conditional probability between layers; correcting the Bayesian model according to the actual situation; calculating a failure probability; and calculating the posterior probability of the bottom event, and searchingthe maximum risk bottom event causing failure. Compared with a traditional simplex qualitative and simplex quantitative reliability evaluation method, the method has the advantages that the accuracy is high; fuzzy mathematics and quantitative data analysis are fused, the defects that qualitative analysis lacks data support and pure data analysis is too absolute are overcome, and compared with a traditional Bayesian network model, the variable correction process of the Bayesian network is added, and the obtained evaluation result can be closer to the actual engineering situation.
Owner:NANJING INST OF MEASUREMENT & TESTING TECH
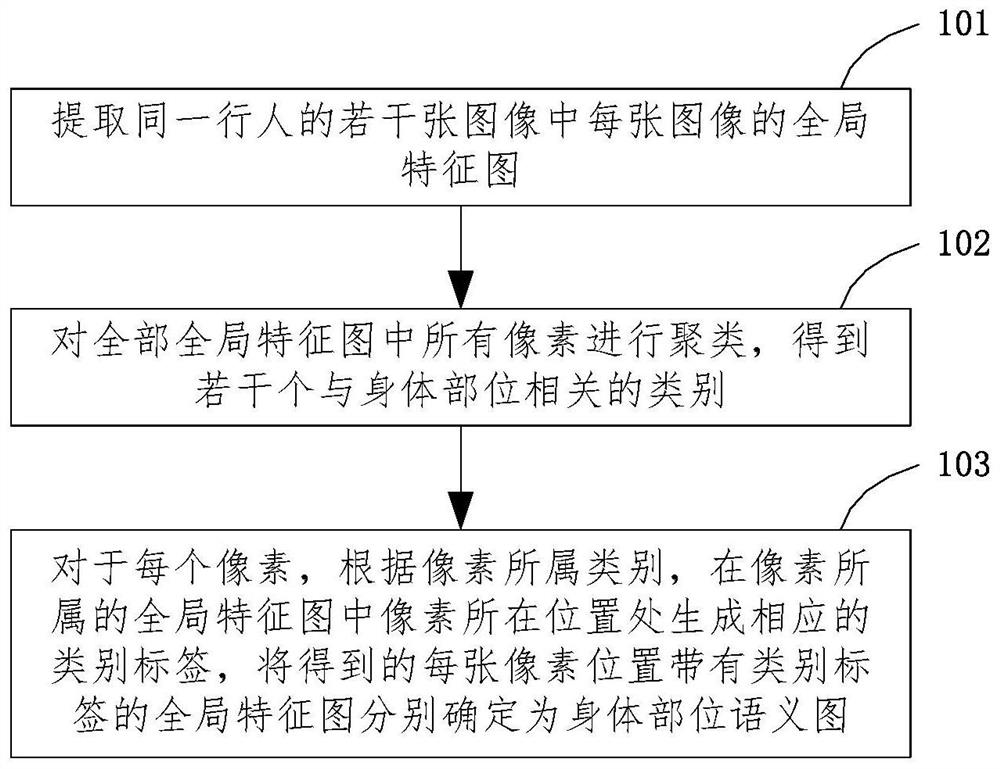
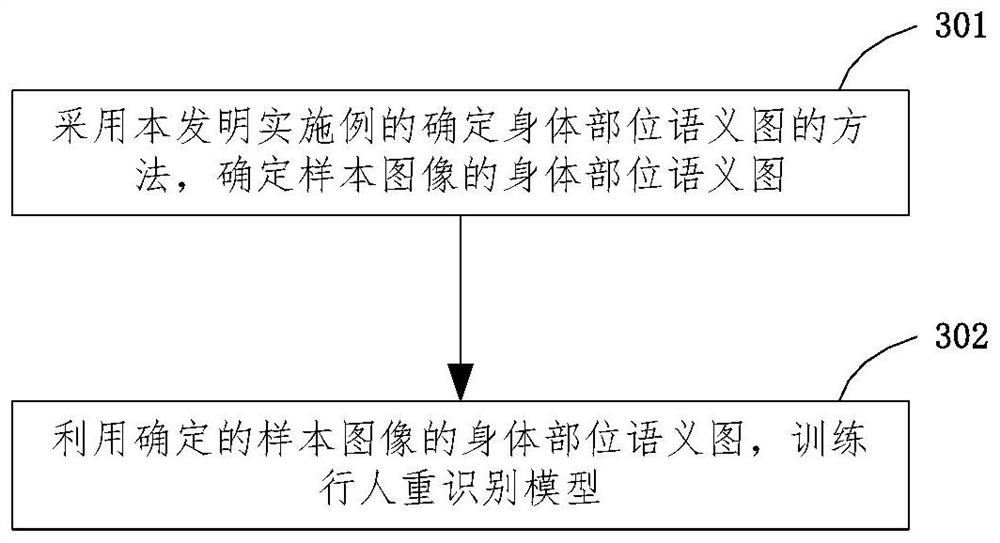
Method and device for determining body part semantic graph, model training method and pedestrian re-identification method
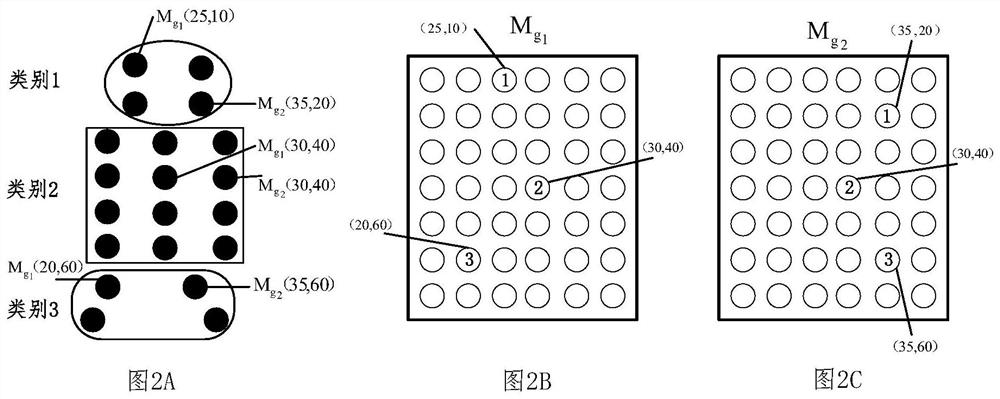
PendingCN112836611AImprove acquisition efficiencyBiometric pattern recognitionPattern recognitionGraph mapping
The invention discloses a method for determining a body part semantic graph. The method comprises the following steps of: extracting a global feature graph of each image in a plurality of images of the same pedestrian; clustering all pixels in all the global feature maps to acquire a plurality of categories related to the body parts; for each pixel, according to the category to which the pixel belongs, generating a corresponding category label at the position of the pixel in the global feature map to which the pixel belongs, and respectively determining the obtained global feature map with the category label at each pixel position as a body part semantic map mapped by the global feature map, therefore, the acquisition efficiency of the image with the body part label is improved.
Owner:上海眼控科技股份有限公司
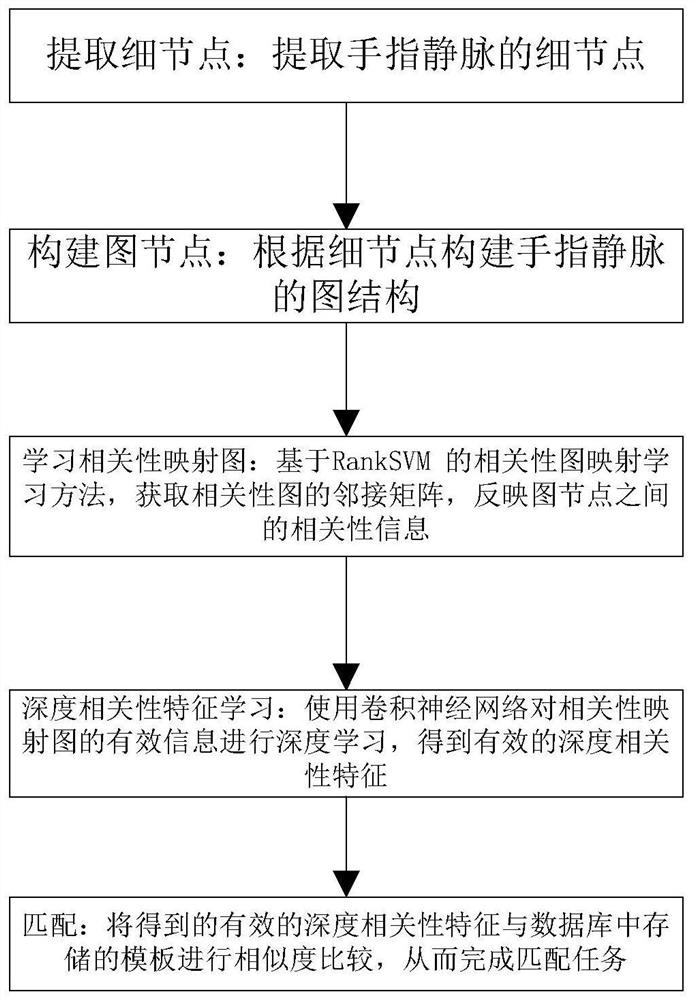
A finger vein recognition method and device based on deep correlation feature learning
ActiveCN110263726BSolve the problem of accurate identificationHelp flourishNeural architecturesSubcutaneous biometric featuresGraph mappingFinger vein recognition
The invention discloses a finger vein recognition method and device based on deep correlation feature learning, which belongs to the field of biometrics. The technical problem to be solved by the invention is how to effectively and precisely identify finer veins, and establish the relationship between detail points. Relevance information to ensure strong recognition performance. The technical solution adopted is: ①The steps of the method are as follows: S1. Extract detail points; S2. Build graph nodes; S3. Learn correlation map: correlation based on RankSVM Graph mapping learning method, obtaining the adjacency matrix of the correlation graph, reflecting the correlation information between graph nodes; S4, deep correlation feature learning; S5, matching: combining the obtained effective deep correlation features with the templates stored in the database Perform similarity comparison to complete the matching task. ② The device includes a minutiae point extraction module, a graph node construction module, a correlation map learning module, a deep correlation feature learning module, and a matching module.
Owner:INSPUR GROUP CO LTD
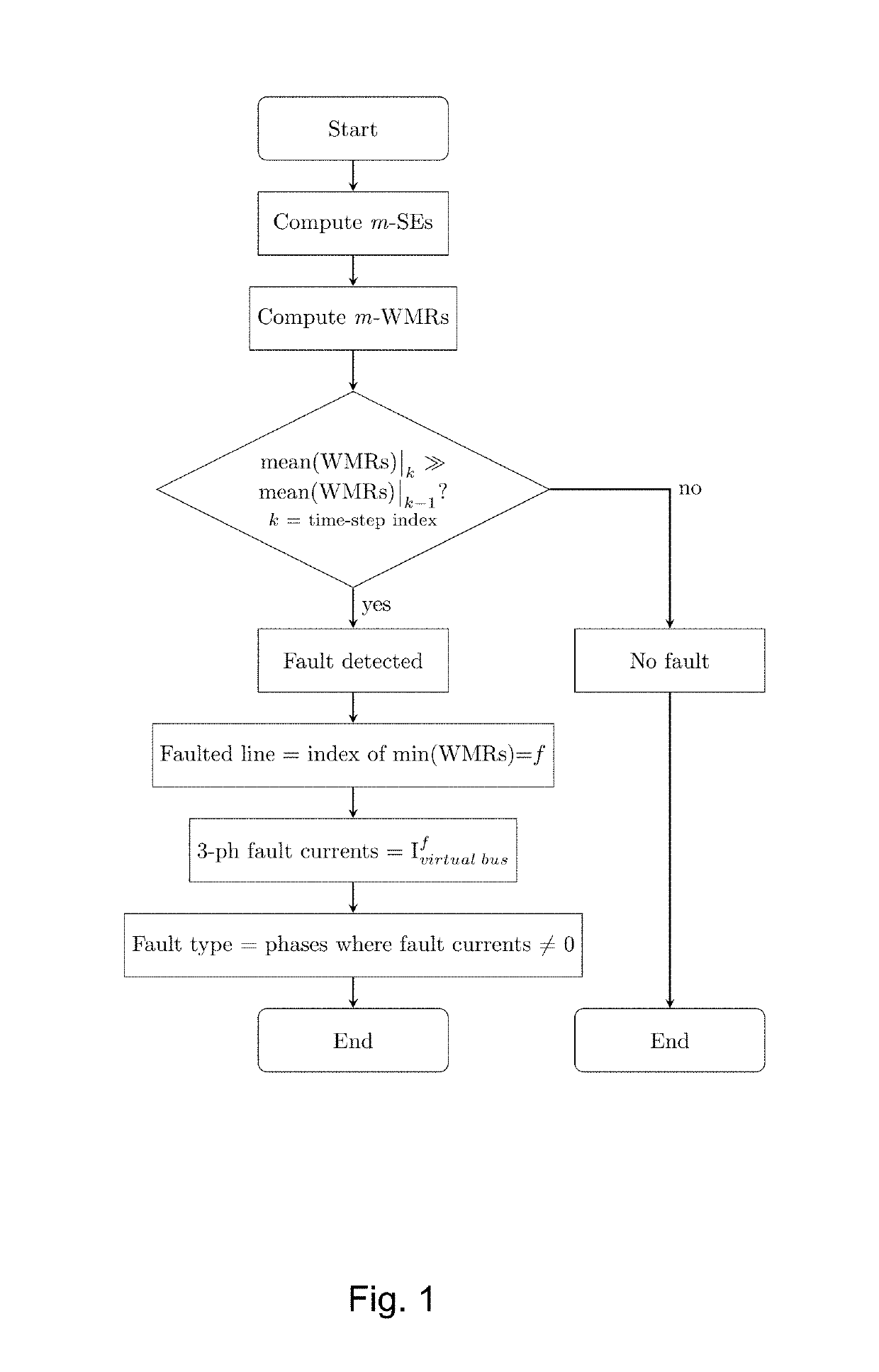
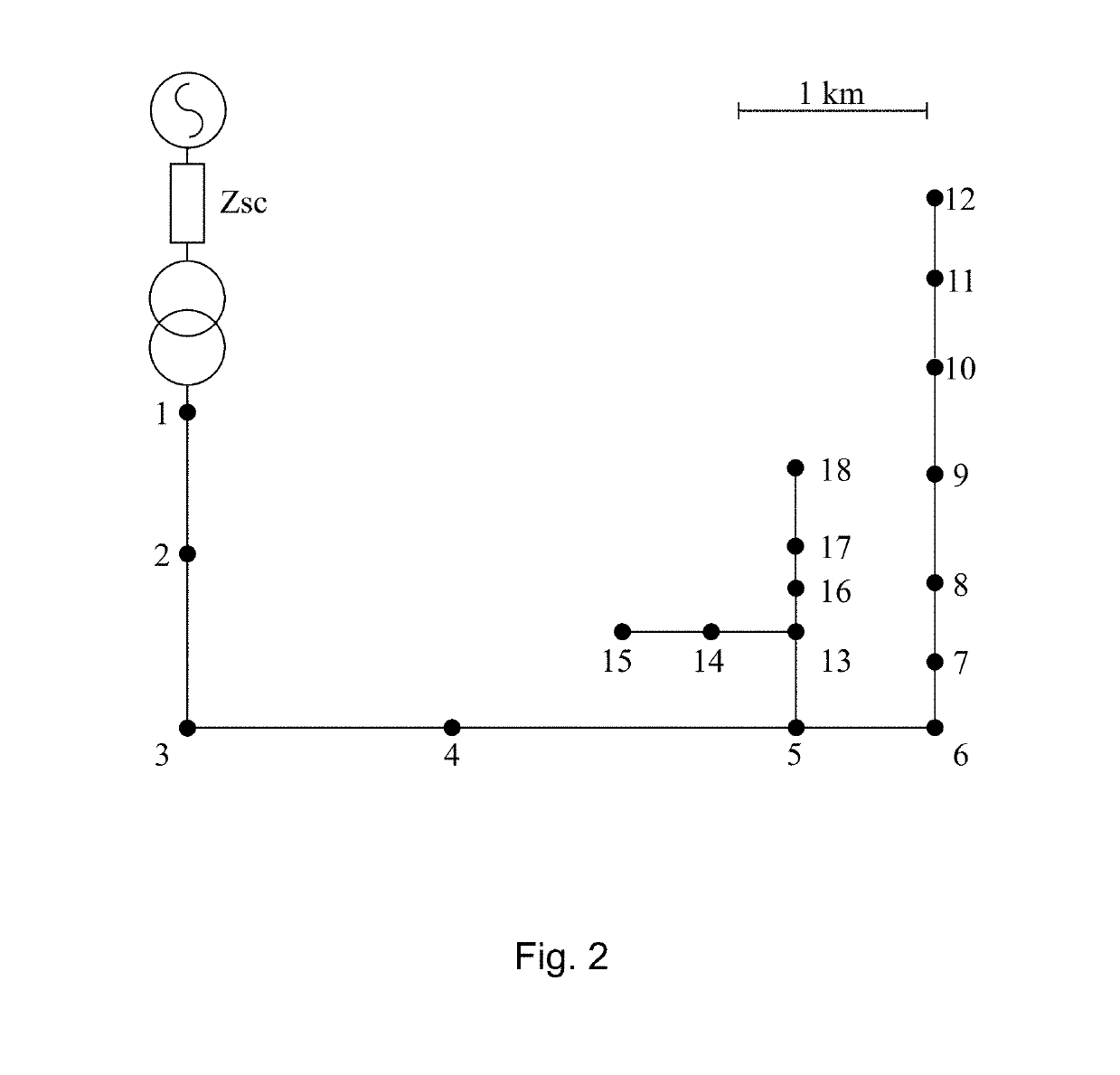
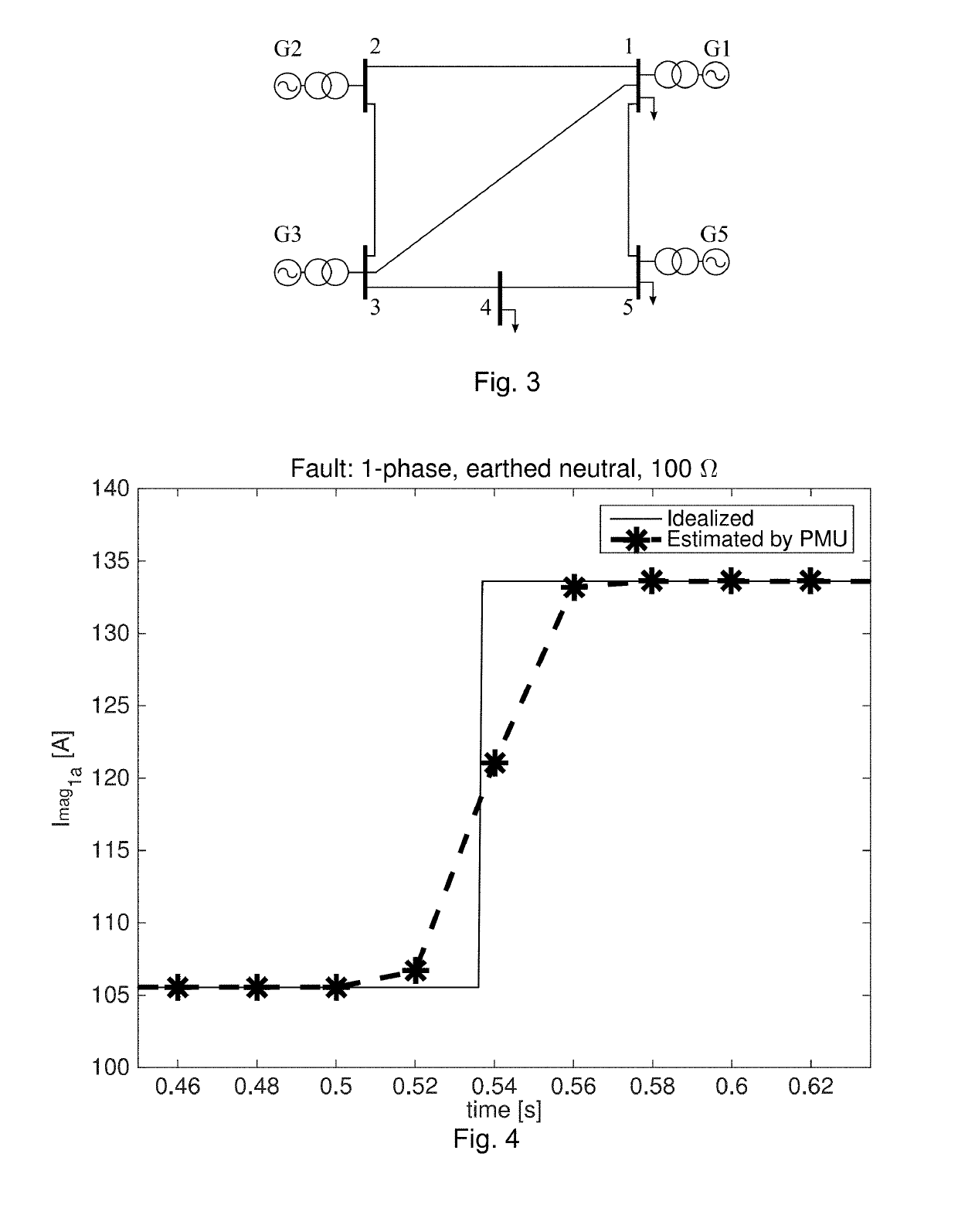
Method and system for fault detection and faulted line identification in power systems using synchrophasors-based real-time state estimation
ActiveUS10288667B2Fault location by conductor typesSystems intergating technologiesPower gridNetwork topology
A method for a faulted line identification in a power network, including, at a generic time-instant, solving a plurality of parallel phasor measurement units based real-time state estimators, the state estimators having among each other different and augmented network topologies, each of the augmented network topologies comprises an original network topology, which includes a plurality of real buses and real lines forming a connected graph mapping the real network topology, and a single additional virtual bus located along one of the real lines, the line in which the virtual bus is located has to be different for each of the augmented network topologies.
Owner:ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL)
Graph width learning classification method and system based on global sampling sub-graphs
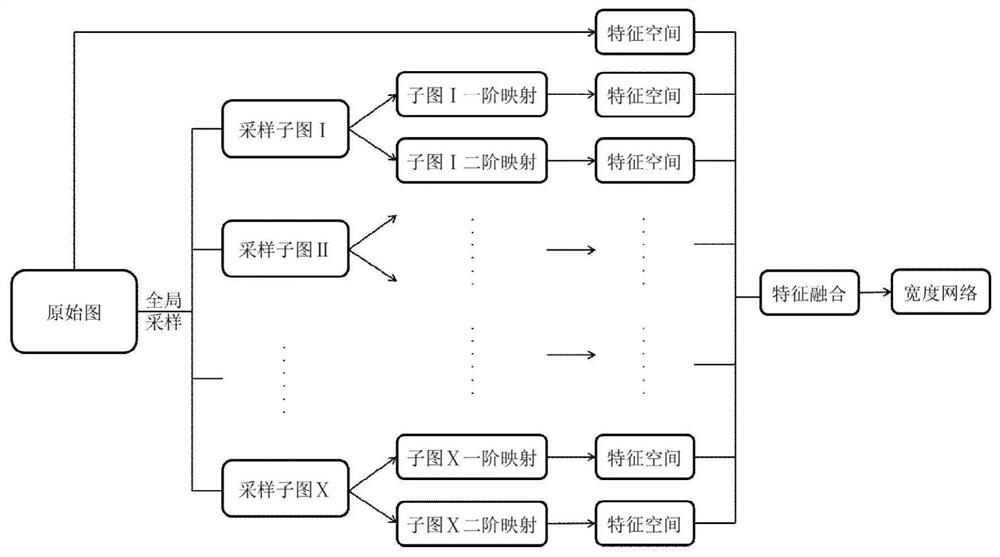
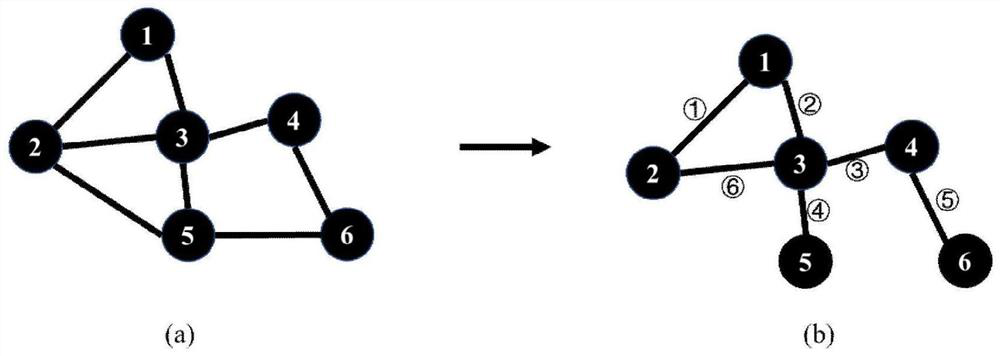
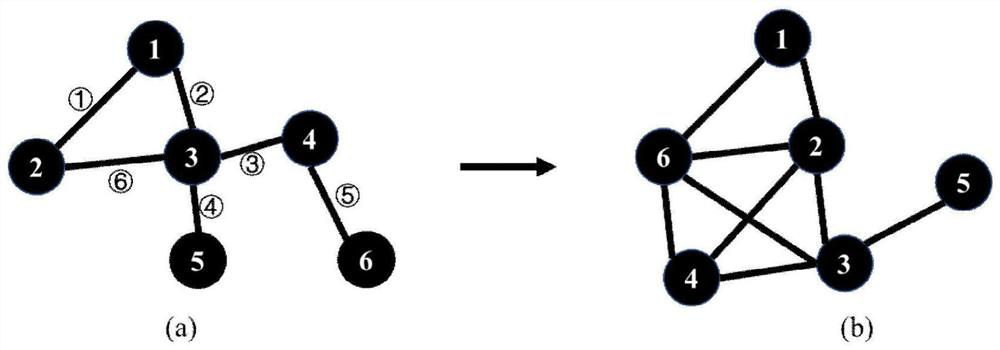
InactiveCN113111914AImprove classification accuracyImprove classification efficiencyCharacter and pattern recognitionMolecular structuresGraph mappingFeature extraction
A graph width learning classification method based on global sampling sub-graphs comprises the following steps: 1) global sampling: performing global sampling on an original network by using a connected edge sampling method to obtain sub-graphs; 2) sub-graph mapping: mapping the sub-graphs once or twice through a mapping mechanism from connecting edges to nodes to obtain a first-order network and a second-order network; 3) graph feature extraction and fusion: extracting features of an original network and all mapped networks through a Graph2vec model, and then splicing the extracted original network features and first-order and second-order network features after each sampling mapping as feature representation of an original graph; and 4) classifying a width network. The invention further discloses an efficient and accurate graph classification system based on the method. A weight matrix in a width network classifier is trained in a supervised manner by combining the fused graph features and the known graph labels. Finally, effective classification of the graphs is realized according to the weight matrix in the width network and the input graph features.
Owner:ZHEJIANG UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com