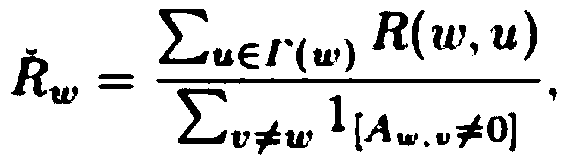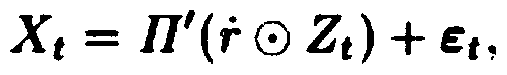Switch data anomaly detection method based on vector autoregression model
A technology of autoregressive models and detection methods, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as lack of analysis, and achieve the effect of filling security loopholes, reducing serious losses, and avoiding misidentification of normal users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
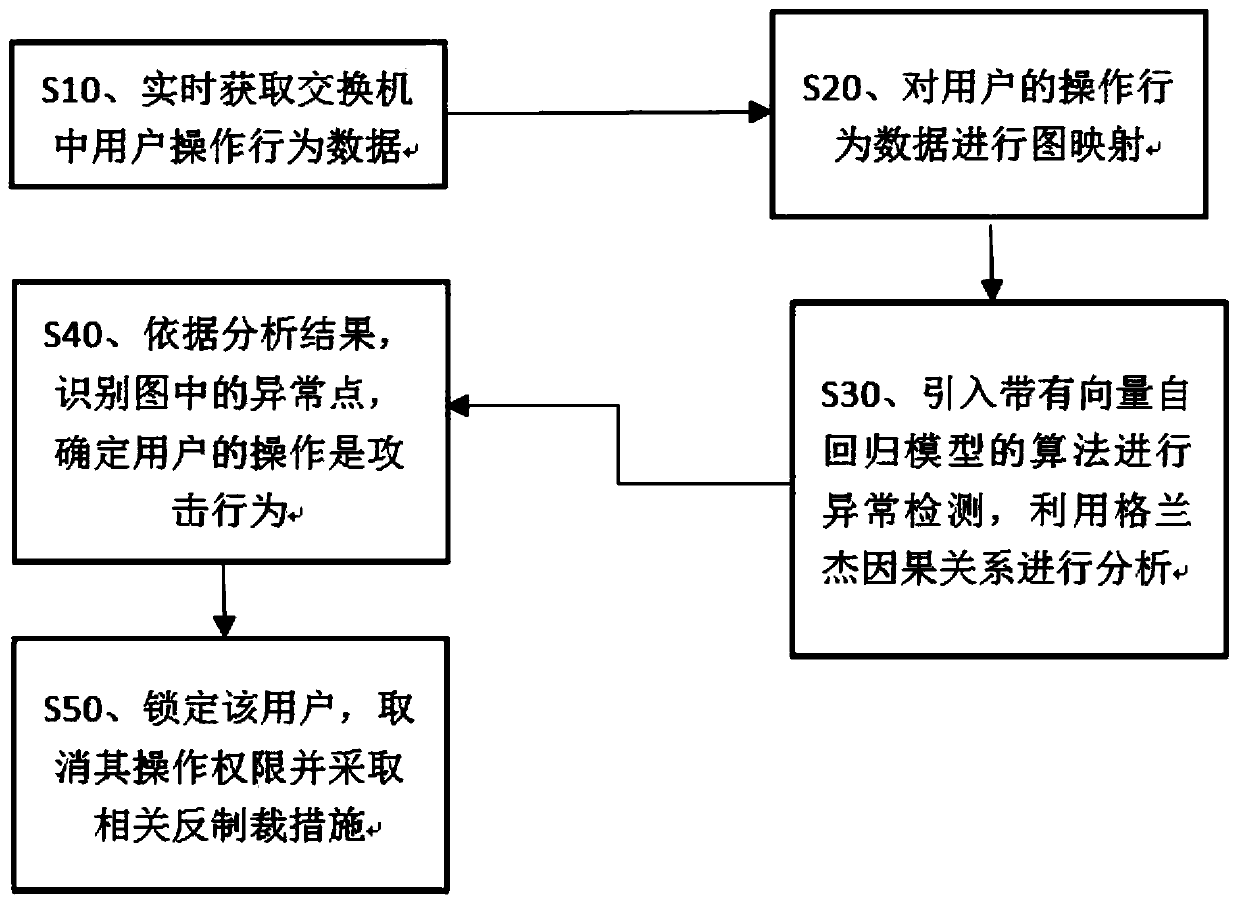
[0061] combined with figure 1 , the present embodiment proposes a switch data anomaly detection method based on a vector autoregressive model, and the detection method includes the following steps:
[0062] S10. Obtain in real time the operation behavior data of the logged-in user in the exchange, and store it in the data set.
[0063] S20. Perform graph mapping on the operational behavior data contained in the data set, and convert it into a signed graph. The specific execution process includes:
[0064] S21. Transform the operational behavior data contained in the data set into a series of signed graphs G under the time dimension t , where t=1,2,...,T, at this time, each signed graph is regarded as a mapping of data at time point t;
[0065] S22. Consider each mapping at time point t as a change at the previous time point t-1, and the adjacency matrix associated with it can be written as A t =A t-1 +E t , where Et is the change of two mappings Gt-1 and Gt;
[0066] S23...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com