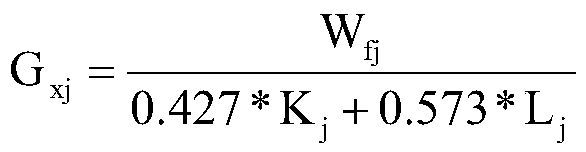Computer storage system capable of ensuring information security
A technology of computer storage and information security, applied in internal/peripheral computer component protection, digital data authentication, instruments, etc., can solve problems such as unreasonable information security, concealment of real memory, and no comprehensive consideration of customary input methods, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
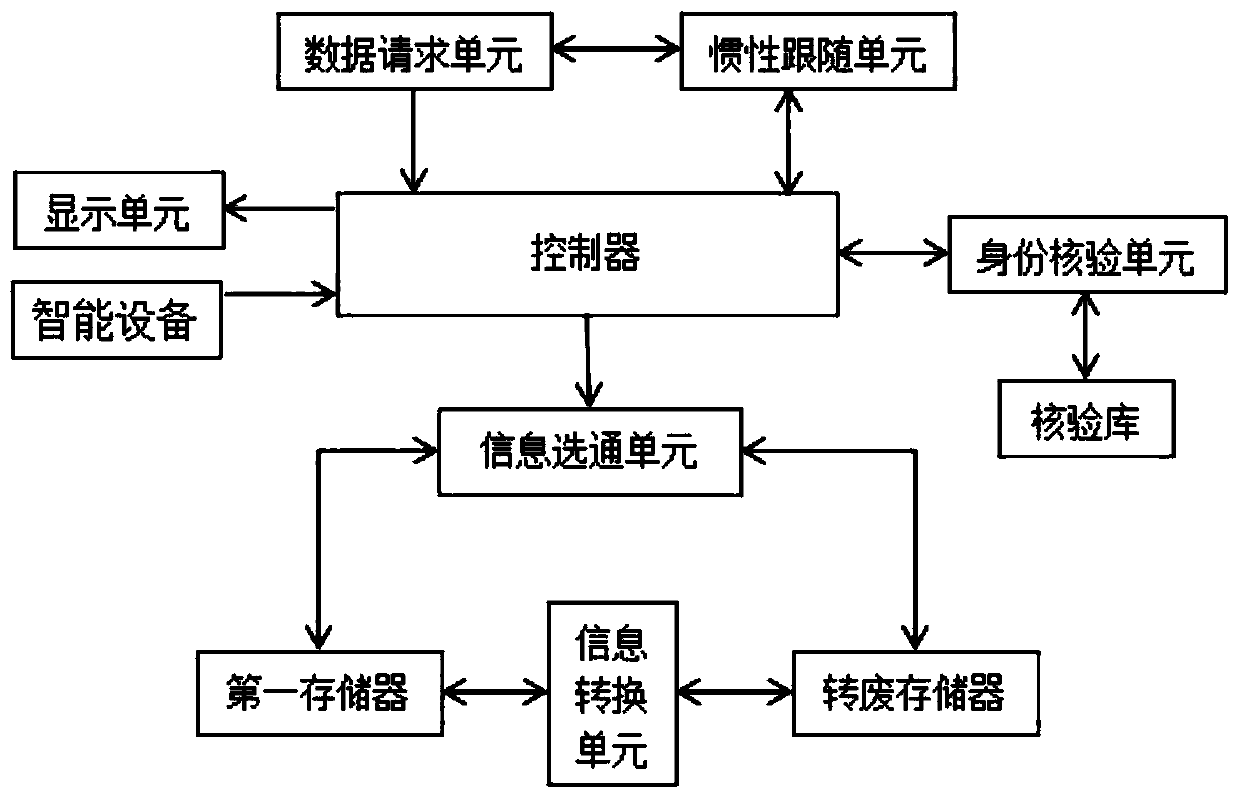
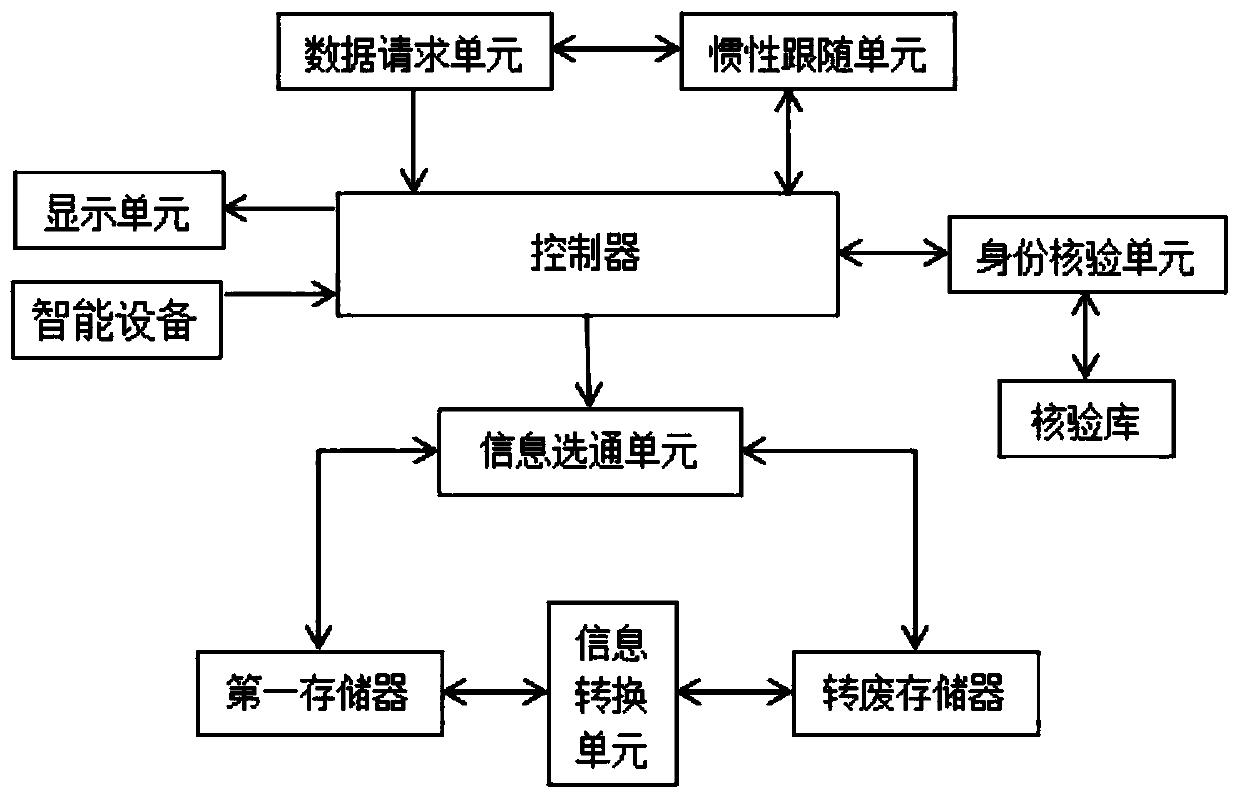
[0065] Such as figure 1 As shown, a computer storage system for ensuring information security includes a data request unit, an inertia following unit, a controller, a display unit, an identity verification unit, a verification library, an information gating unit, a first memory, an information conversion unit and a waste transfer unit memory;
[0066] Wherein, the data request unit is used for the user to enter request information, and the request information includes the requester and the corresponding request password; the data request unit is used for transmitting the request information to the controller;
[0067] The inertia following unit is used to monitor the inertial time difference of the user requesting the secret order according to the time difference analysis step, and the time difference analysis step is specifically:
[0068] Step 1: first obtain the number of times the user inputs request information, and mark it as the number of requests Qq;
[0069] Step 2:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com