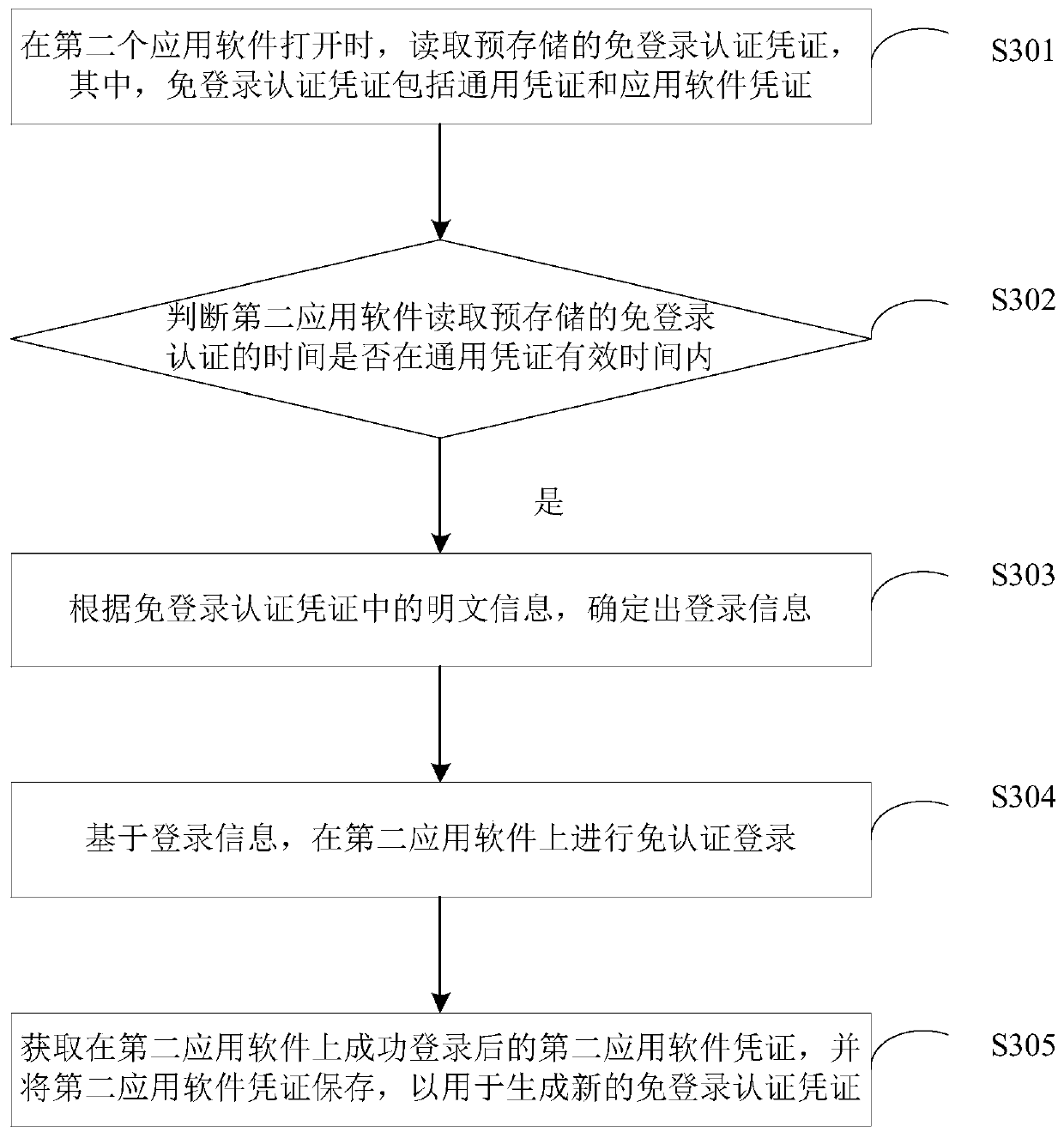
Login method, storage medium and computer equipment
A login method and technology of storage medium, applied in the field of storage medium, computer equipment, and login method, can solve the problems of cumbersome process, unable to achieve a quick experience of opening and logging in, etc., and achieve the effect of simplifying the login process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
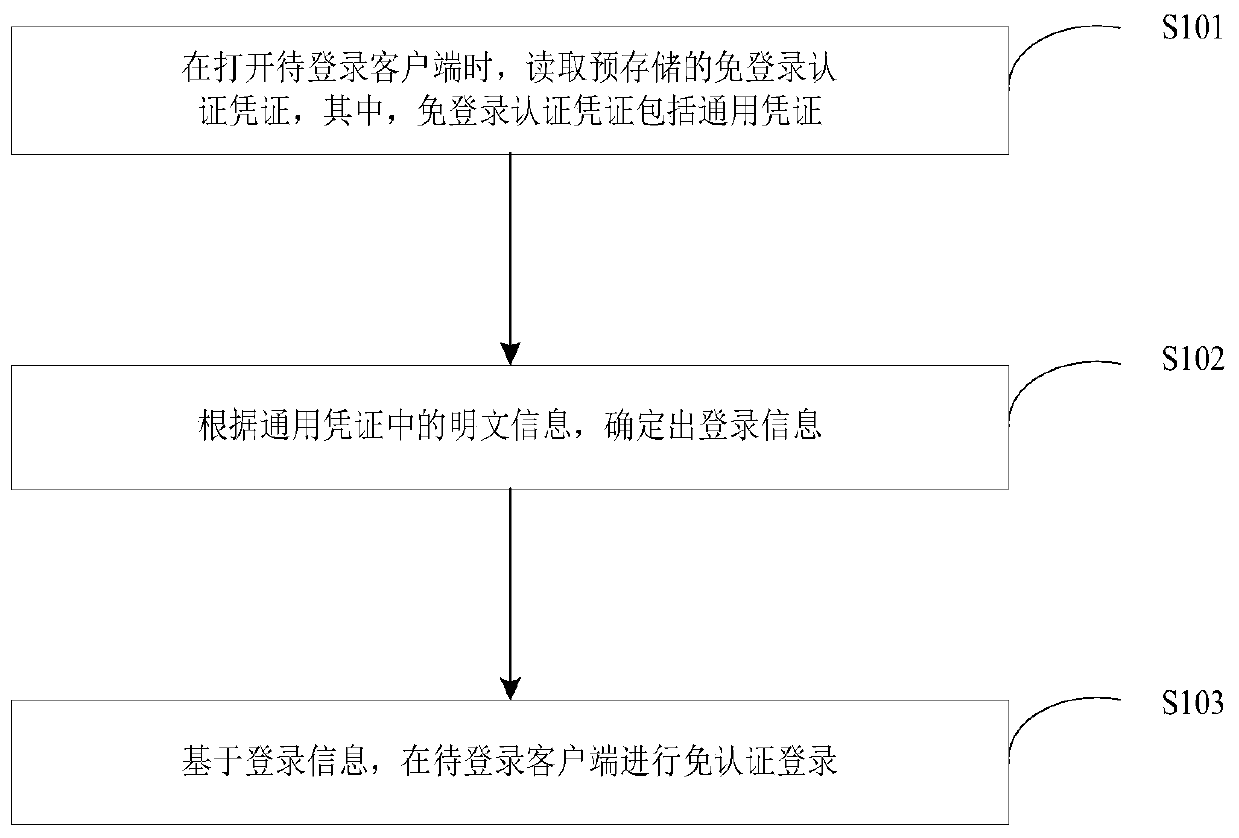
[0037] see figure 1 as shown, figure 1 A schematic flowchart of a login method provided by the embodiment of the present application is shown, which includes steps S101 to S103.
[0038] In step S101, when the client terminal to be logged in is opened, the pre-stored login-free authentication credentials are read, wherein the login-free authentication credentials include general credentials.
[0039] Wherein, the pre-stored login-free authentication credential may be generated based on the account information of the client that completes the login with the account. Among them, the account information of the client that completes the login with the account includes at least user identification information, for example, the mobile phone number and / or email address with the user's unique identification, and the account information can also include the user's basic information, such as the account information of the client that has completed the login. end user name, user gender...
Embodiment 2
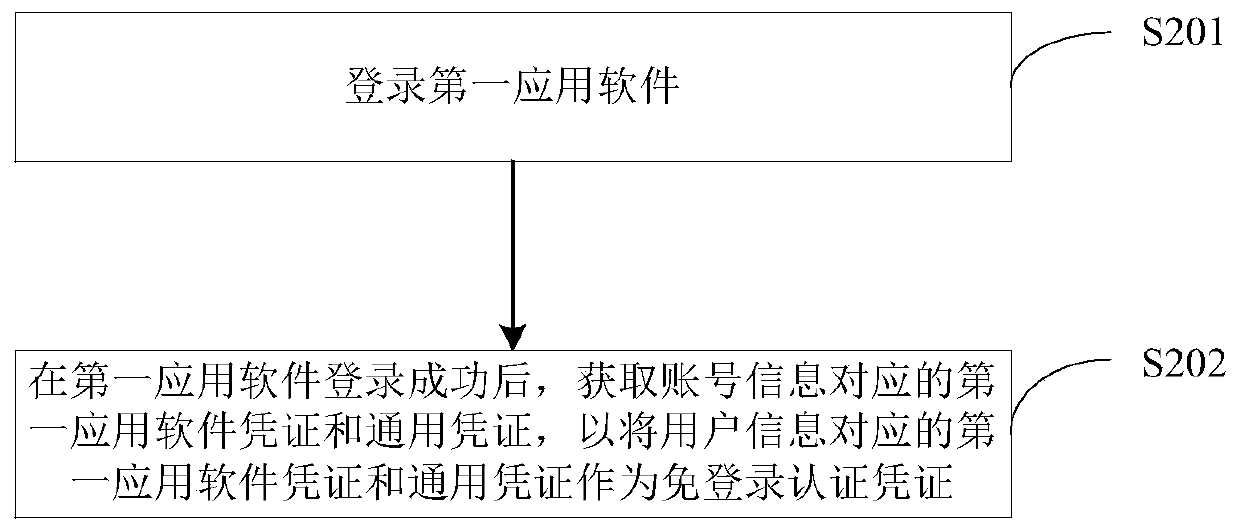
[0053] see figure 2 as shown, figure 2 A schematic flowchart of a method for generating a login-free authentication credential provided by an embodiment of the present application is shown.
[0054] Step S201: Logging into the first application software.
[0055] When the first application software on the mobile phone logs in for the first time, a preset database is read to determine whether there is a login-free authentication certificate. It should be noted that other terminals may also be used. In this application, a mobile phone will be used as an example for illustration.
[0056] When there is no login-free authentication credential, use account number, password and other user information to log in to the first application software, and when the login is successful, the server of the first application software will generate encrypted data of its own credentials corresponding to the user information logged in to the first application software Bag.
[0057] By decryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com