Method and system for logging in client by using graphical identification code, and terminal
A graphic identification and client technology, applied in transmission systems, electrical components, etc., can solve problems such as complex processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
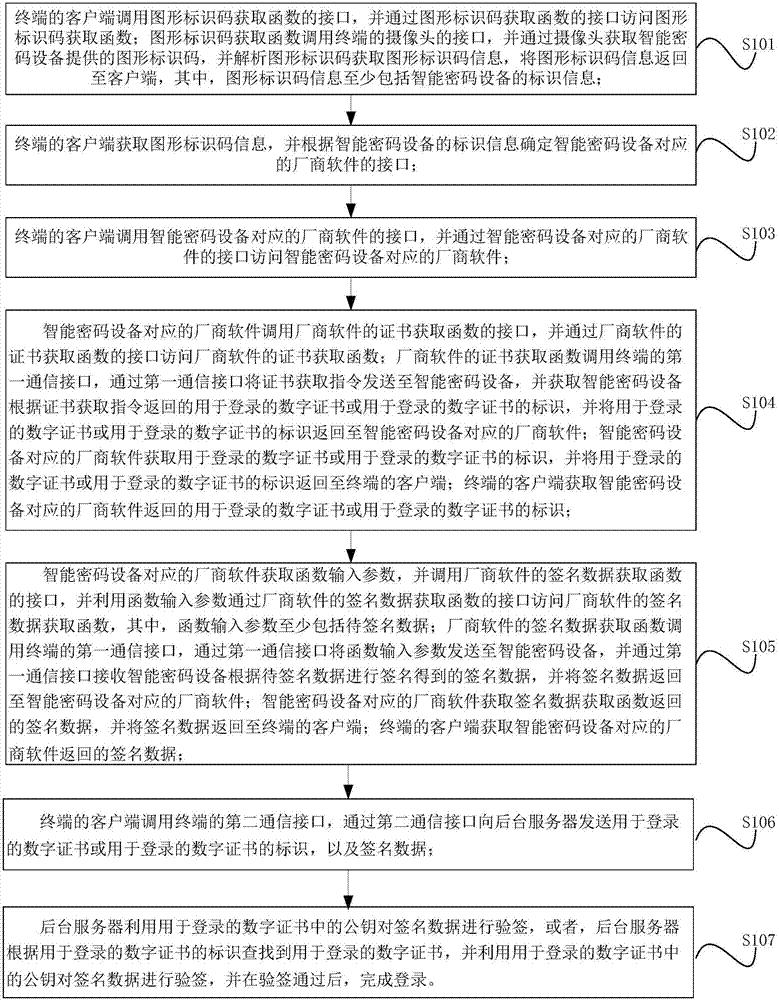
[0033] This embodiment provides a method for logging in to a client using a graphic identification code, such as figure 1 As shown, the login method includes steps S101-S107.
[0034] Step S101: the client of the terminal calls the interface of the graphic identification code acquisition function, and accesses the graphic identification code acquisition function through the interface of the graphic identification code acquisition function; the graphic identification code acquisition function calls the interface of the camera of the terminal, and obtains the smart password through the camera The graphic identification code provided by the device, and analyzing the graphic identification code to obtain graphic identification code information, and returning the graphic identification code information to the client, wherein the graphic identification code information includes at least the identification information of the smart password device;
[0035] In this embodiment, the ter...
Embodiment approach
[0056] Before the smart cryptographic device signs the received data to be signed, it is necessary to determine whether the user has the right to use the smart cryptographic device to prevent illegal elements from using the lost smart cryptographic device to log in if the smart cryptographic device is lost. In order to ensure that the user has the authority to use the smart cryptographic device, the following optional implementation is provided: the function input parameters also include: prompt information prompting the user to input the verification code; the signature data of the manufacturer's software obtains the first communication interface of the function call terminal , after the function input parameters are sent to the smart cryptographic device through the first communication interface, the method provided in this embodiment further includes: the smart cryptographic device receives the function input parameters, prompts the user to input a verification code, and veri...
Embodiment 2
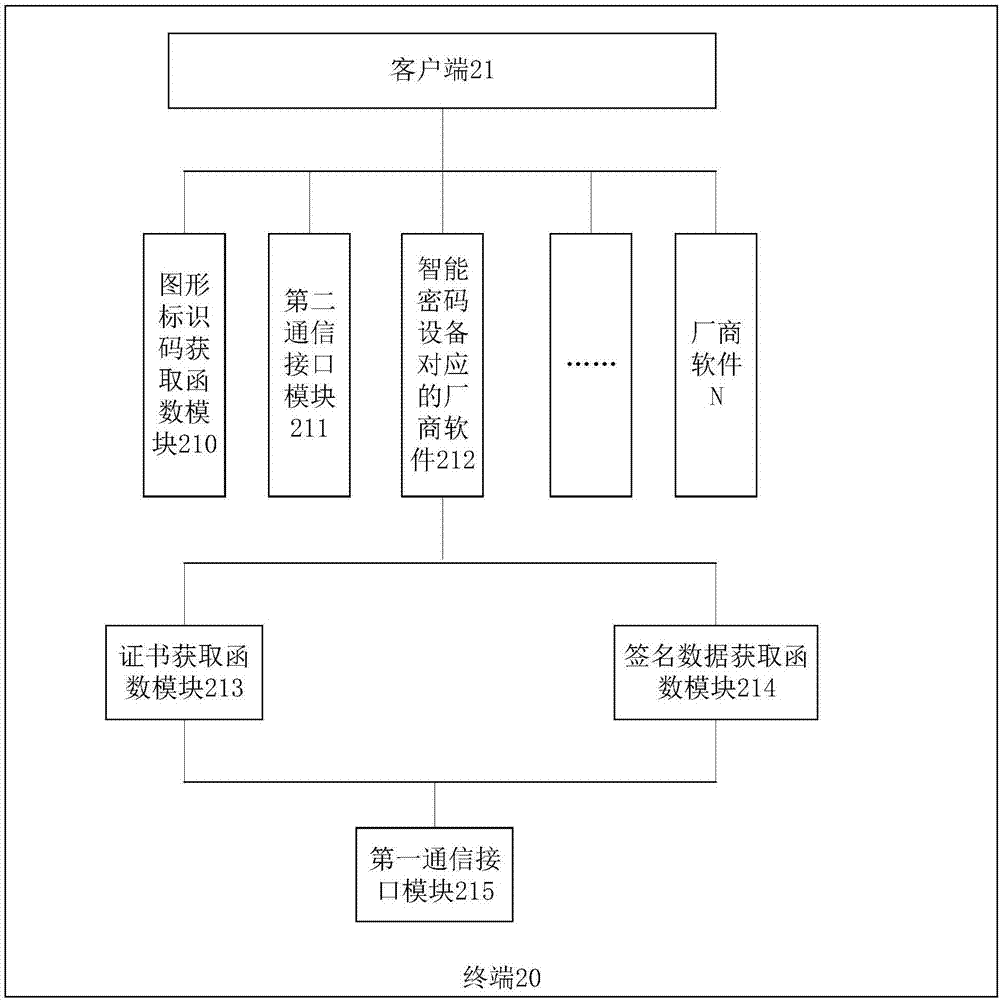
[0065] This embodiment provides a terminal that uses a graphic identification code to log in to a client, such as figure 2As shown, the terminal 20 of this embodiment includes: a client 21, which is used to call the interface of the graphic identification code acquisition function module 210, and access the graphic identification code acquisition function module 210 through the interface of the graphic identification code acquisition function module 210, and obtain The graphic identification code acquisition function module 210 returns the graphic identification code information, and the graphic identification code information includes at least the identification information of the smart cryptographic device; it is also used to determine the interface of the vendor software 212 corresponding to the smart cryptographic device according to the identification information of the smart cryptographic device, and calls The interface of the vendor software 212 corresponding to the sma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com