Login verification method and device for operation analysis service application
A technology of service application and login verification, applied in the direction of electrical components, transmission systems, etc., can solve problems such as difficulty in keeping up with the Internet, cumbersome login process, and affecting user enthusiasm for use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
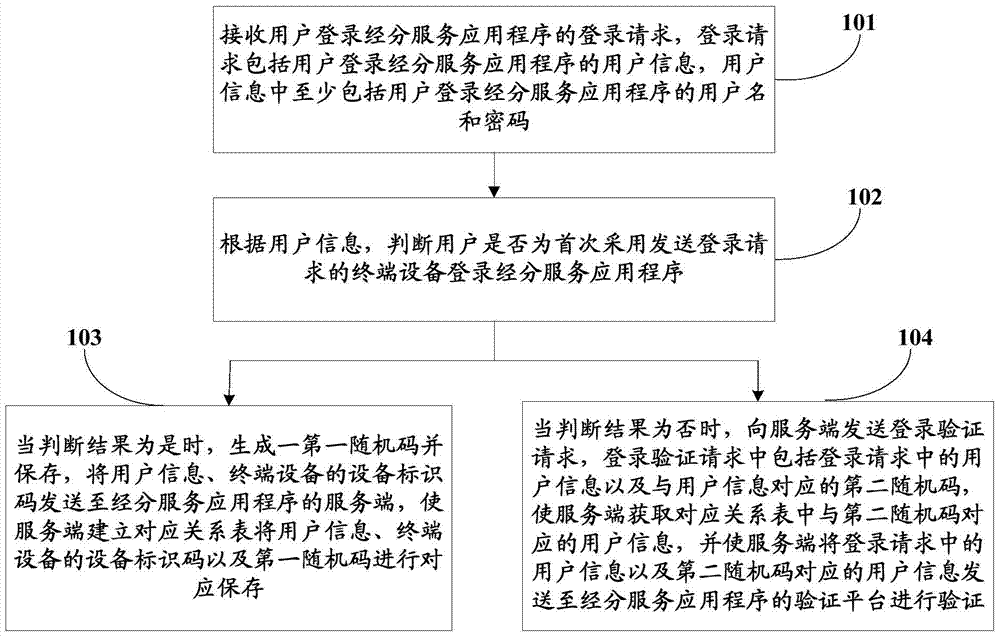
[0093] see figure 1 , the first embodiment of the present invention provides a login verification method via sub-service application, which is applied to the client, including:
[0094] Step 101: Receive a login request for a user to log in to the service application program, the login request includes user information for the user to log in to the service application program, and the user information includes at least the user name and password for the user to log in to the service application program.
[0095] Wherein, when a user logs in to the application client, the terminal device will send to the client a login request including at least a user name and a password for logging in to the sub-service application.
[0096] Step 102: According to the user information, it is judged whether the user logs in to the sub-service application for the first time using the terminal device that sends the login request.
[0097] Wherein, the client judges whether it is the first login...
no. 2 example
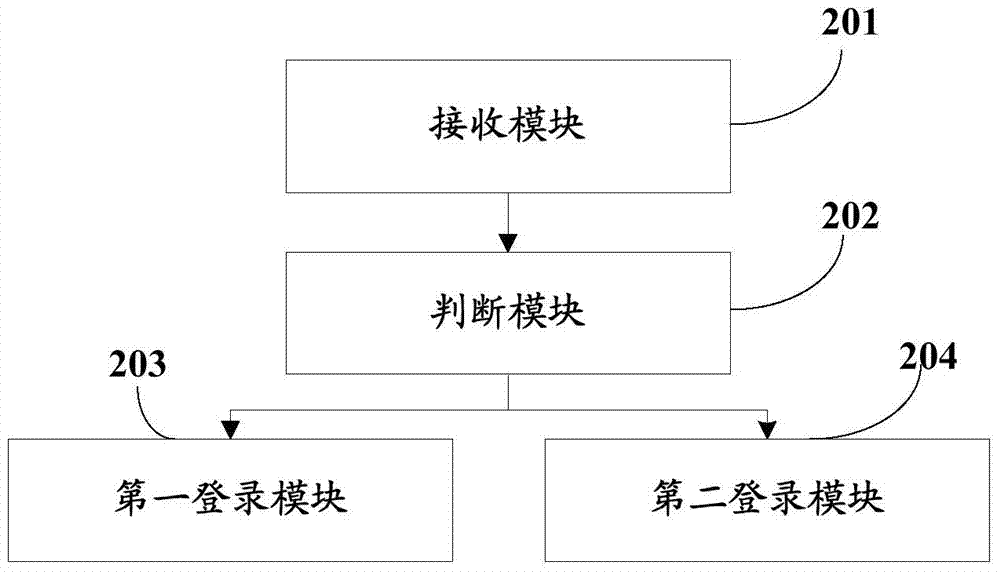
[0126] see figure 2 , the second embodiment of the present invention provides a login verification device via sub-service application, which is applied to the client, including:
[0127] The receiving module 201 is used to receive a login request for the user to log in to the service application program, the login request includes user information for the user to log in to the service application program, and the user information includes at least the user name and password for the user to log in to the service application program;
[0128] Judgment module 202, for judging whether the user is the first time to log in via the sub-service application using the terminal device that sends the log-in request according to the user information;
[0129] The first login module 203 is used to generate a first random code and save it when the judgment result is yes, and send the user information and the device identification code of the terminal device to the service end of the sub-ser...
no. 3 example
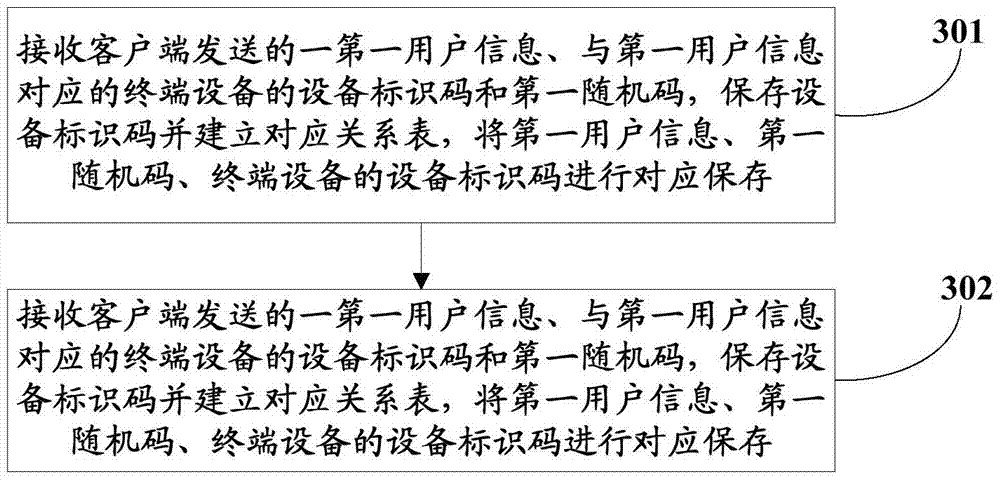
[0155] see image 3 , the third embodiment of the present invention provides a login verification method via a sub-service application, which is applied to the server, including:
[0156] Step 301, receiving the first user information sent by the client, the device identification code of the terminal device corresponding to the first user information, and the first random code, saving the device identification code and establishing a correspondence table, and storing the first user information, the second A random code and the device identification code of the terminal device are stored correspondingly.
[0157] Wherein, the first random code is randomly generated by the client; the device identification code is encrypted and generated by the client according to the IMEI and IMSI according to the first encryption method.
[0158] When the client confirms that it is the first login, it will send a first user information to the server, and when receiving the first user informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com