Firewall security policy opening method and device based on simulation path analysis
A security strategy and path analysis technology, applied in the field of network security, can solve problems such as low efficiency and time-consuming
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054]In order to solve the problem that it will take a lot of time to manually find firewall devices that block access, especially in the case of many firewall devices, the existing policy activation method is inefficient. This application discloses a simulation-based A method and device for enabling a firewall security policy for path analysis.
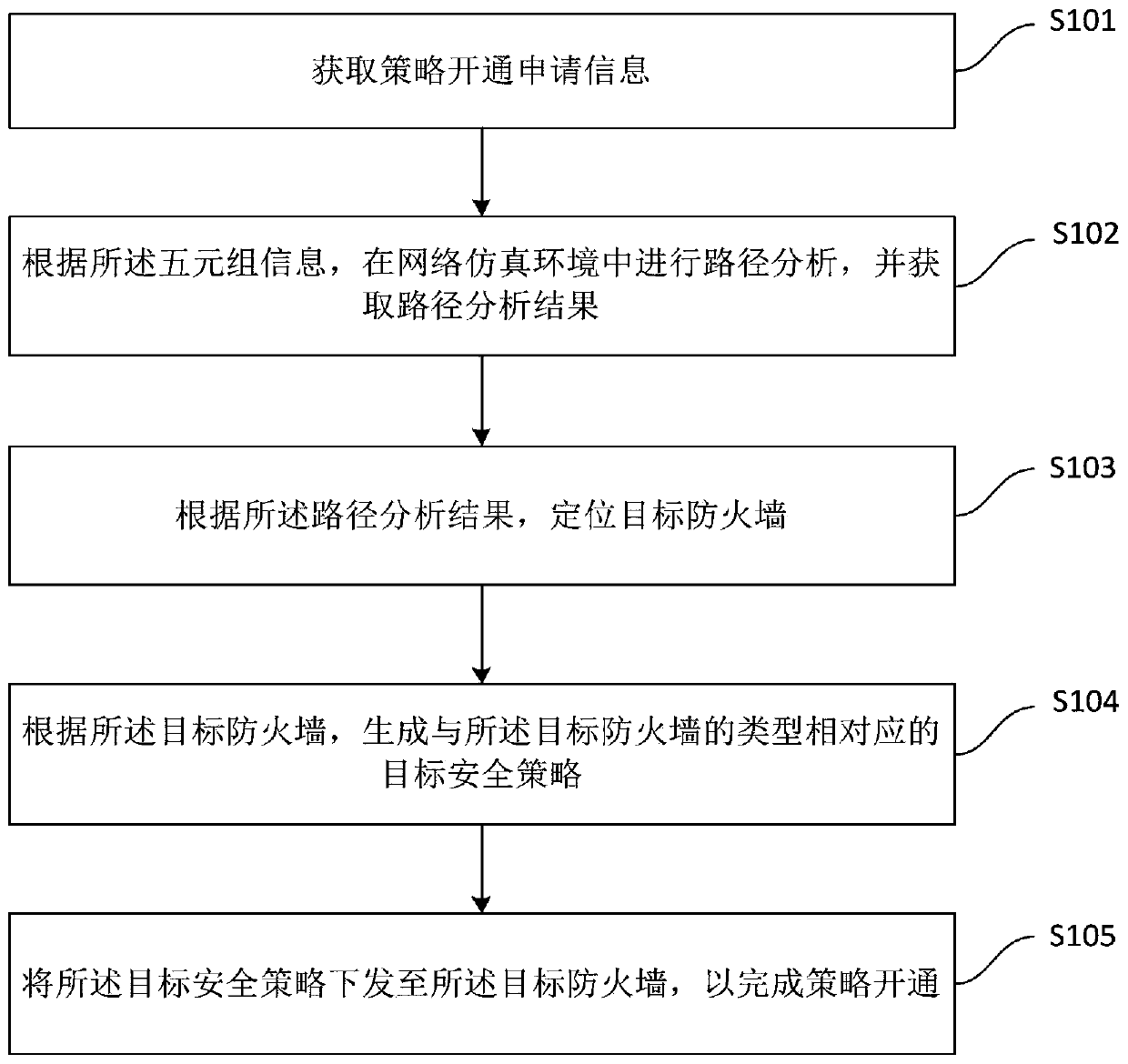
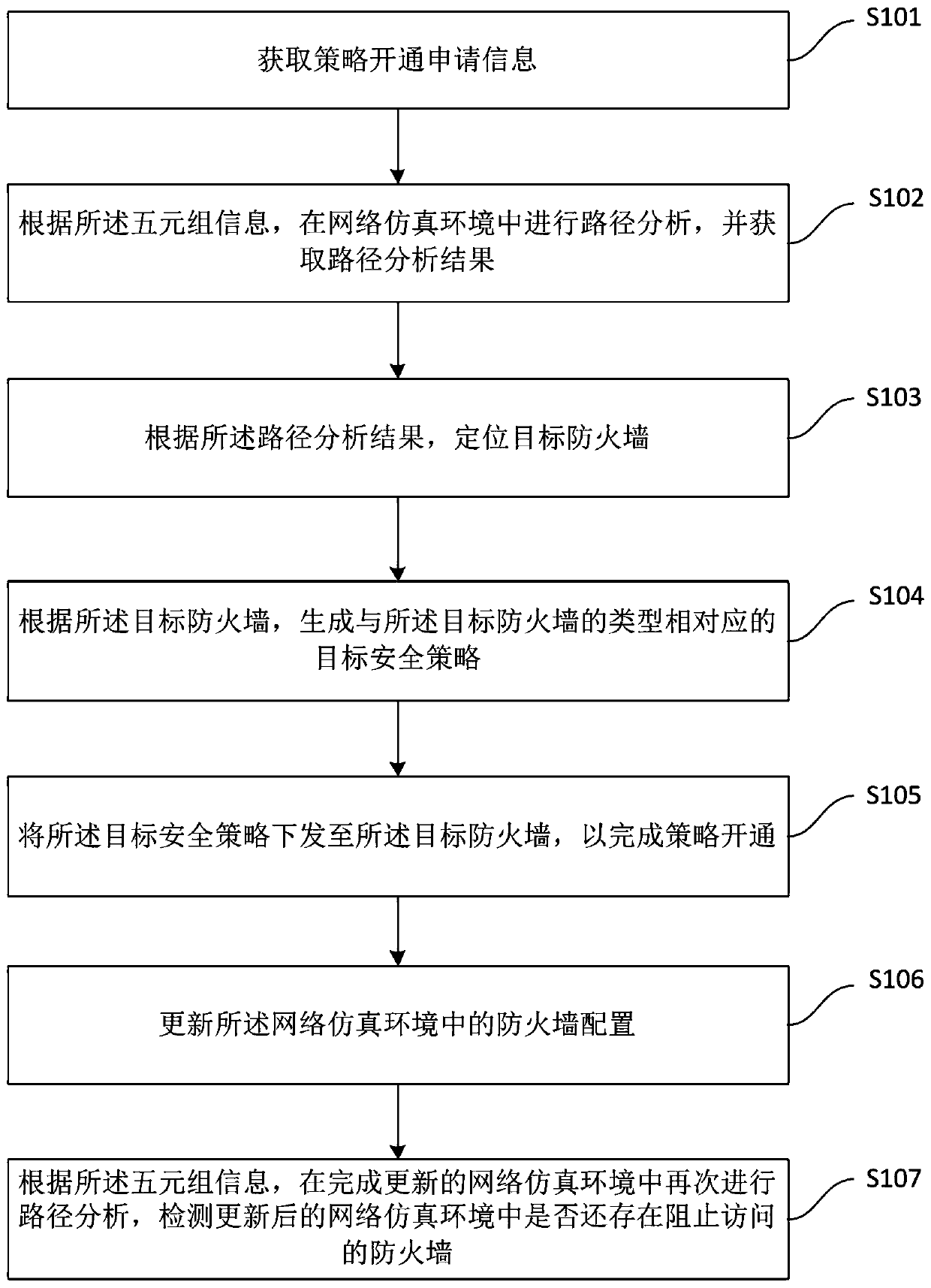
[0055] see figure 1 , the first embodiment of the present application discloses a method for enabling a firewall security policy based on simulation path analysis, including:
[0056] Step S101, acquire policy activation application information, the policy activation application information includes 5-tuple information, and the 5-tuple information includes source address, destination address, source port number, destination port number and protocol type.
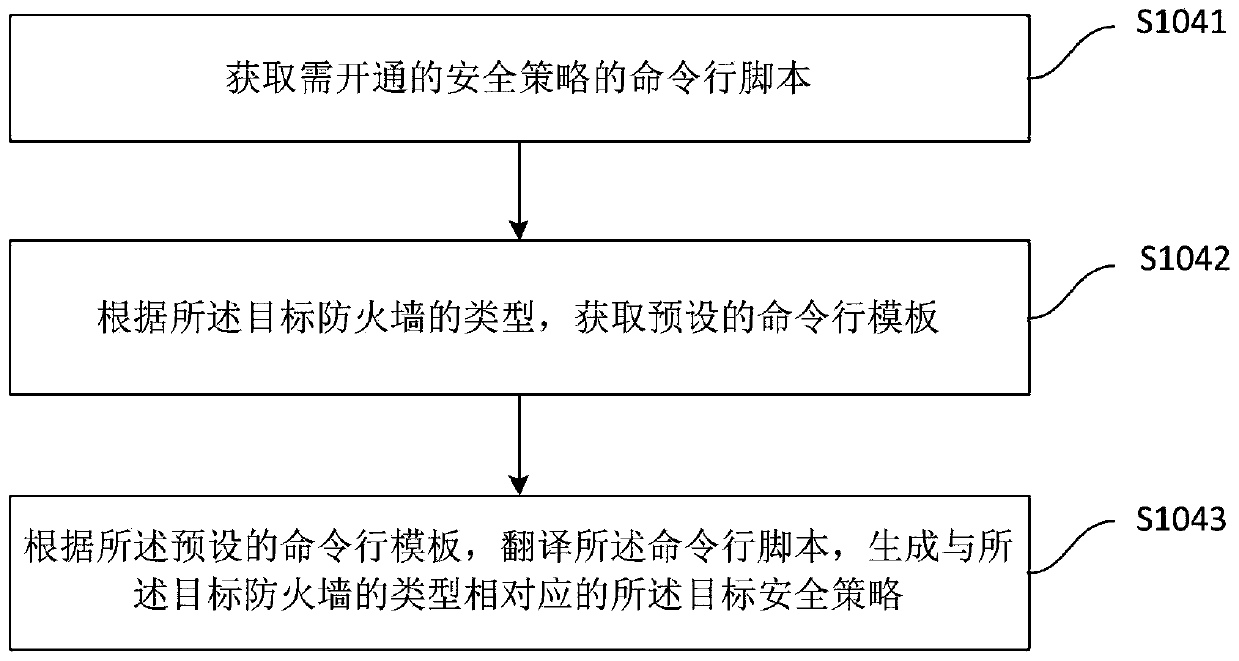
[0057] Step S102, according to the quintuple information, perform path analysis in the network simulation environment, and obtain the path analysis result, the network simulation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com