A secure image steganography method and electronic device based on style transfer
A style conversion and security technology, applied in the field of information security, can solve the problems of small steganography capacity, pixel or coefficient correlation change, poor imperceptibility, etc., to achieve the effect of improving security, realizing secure transmission, and increasing versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The method of the present invention will be further described below with reference to the accompanying drawings and specific embodiments.
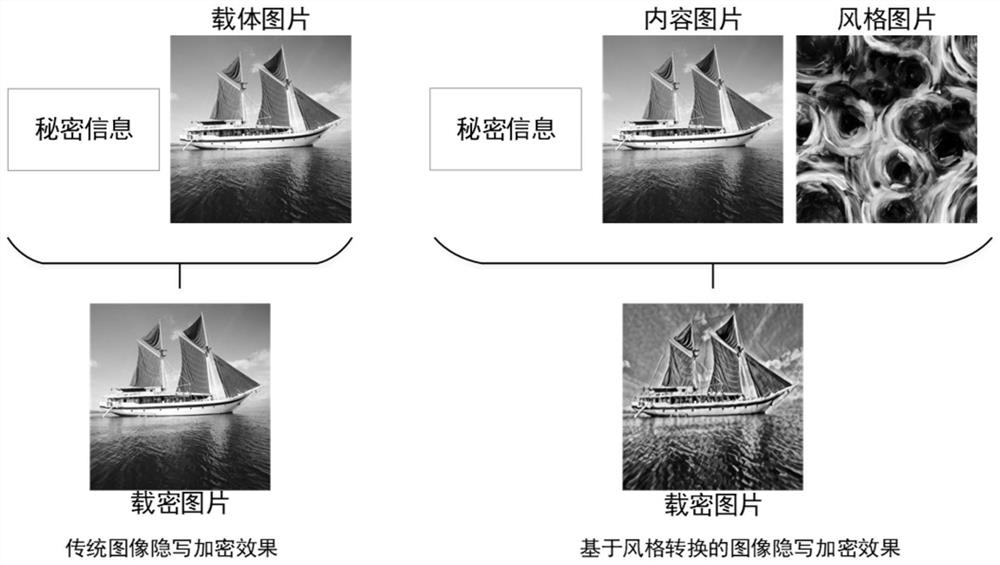
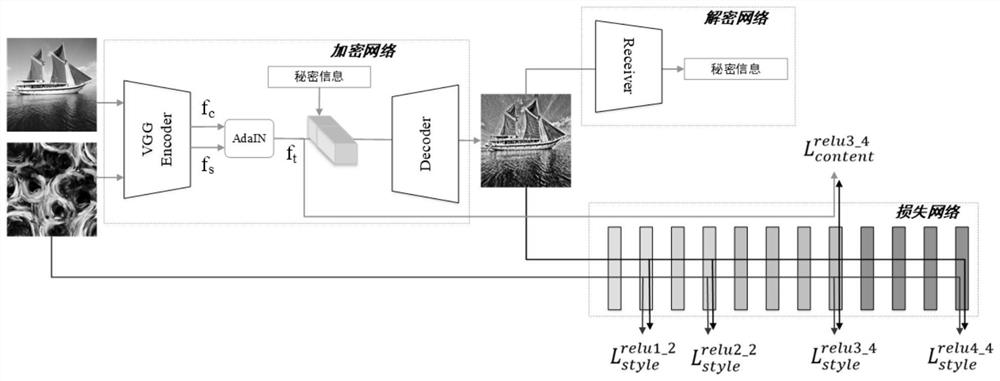
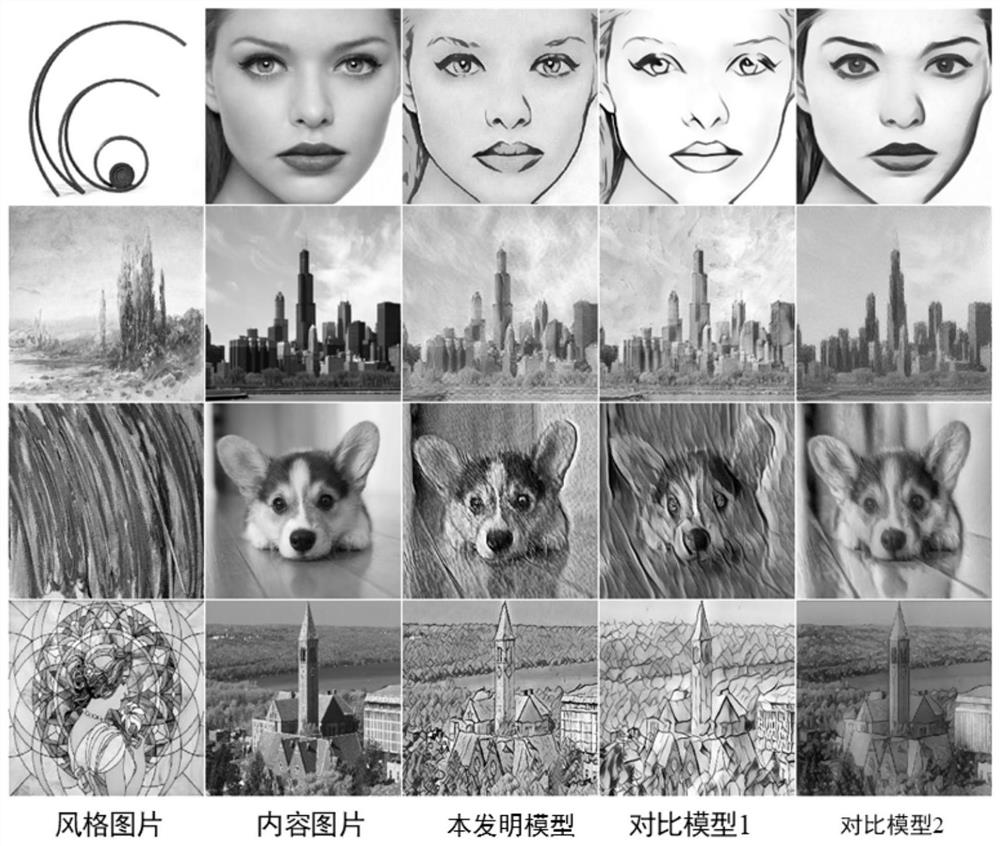
[0031] In the design process of the present invention, it is found that style transfer models such as CycleGAN (Li X, Liu S, Kautz J, et al. Learning linear transformations for fast arbitrary style transfer [J]. arXiv preprint arXiv: 1808.04537, 2018) are more vulnerable to adversarial sample attacks Impact. Because when it converts the image to the target domain image, in order to restore the original image from the domain converted image later, it hides the information about the original image invisible in the domain converted image. Linking this phenomenon with steganography, while performing domain transformation or style transformation on the image, the secret information is hidden into the style texture, so as to realize the secure transmission of the secret information. In addition, software such as image style conversion an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com