A method and system for identifying vulnerable nodes in a power distribution system of a data center
A technology for power distribution systems and nodes, applied in electrical components, circuit devices, AC network circuits, etc., can solve the problems of low accuracy of identification results and failure to consider the classification characteristics of load equipment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
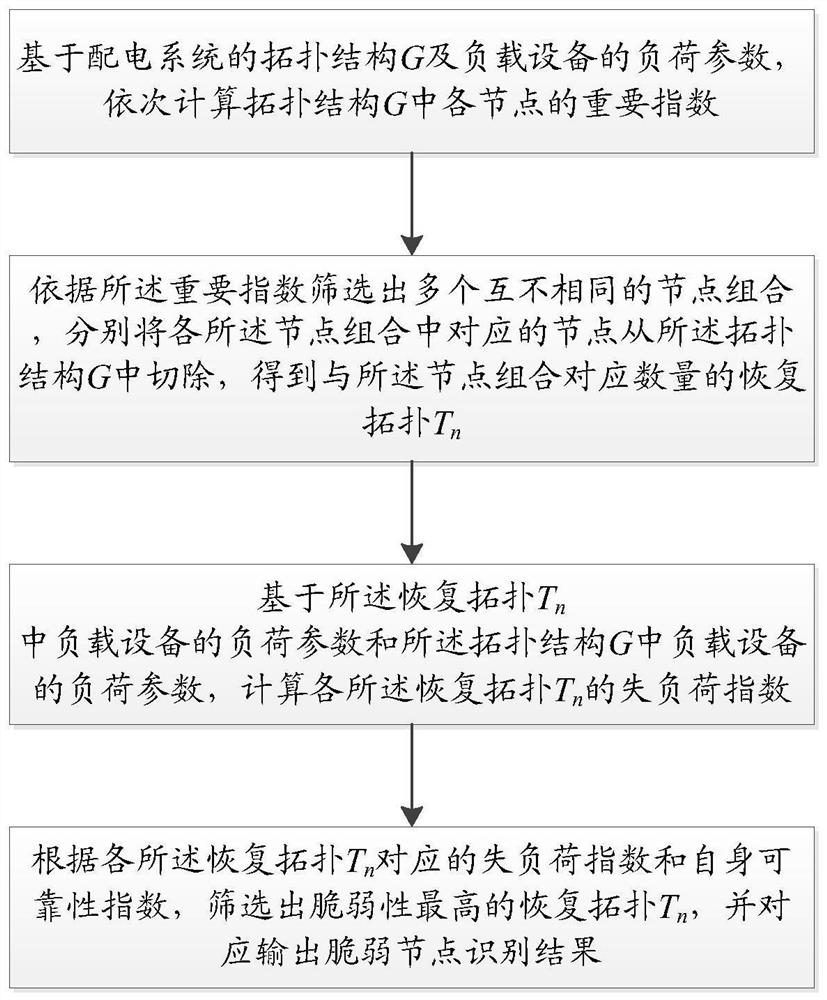
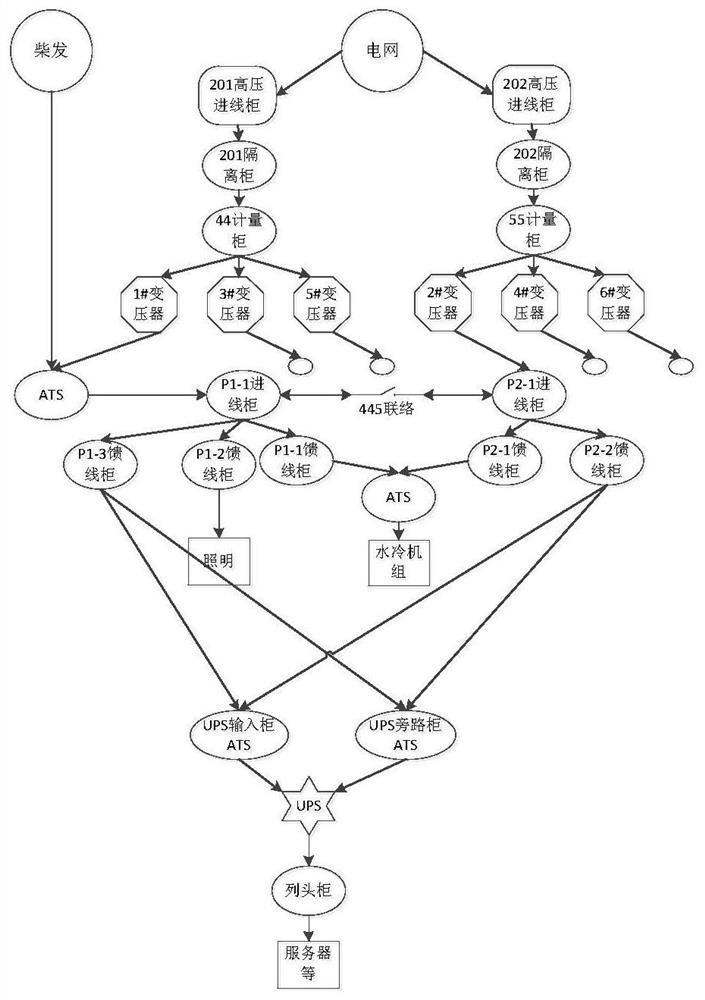
[0058] see figure 1 with figure 2 , this embodiment provides a method for identifying vulnerable nodes in a power distribution system of a data center, including:
[0059] Based on the topological structure G of the power distribution system and the load parameters of the load equipment, the importance index of each node in the topological structure G is calculated sequentially. The load parameters include the load amount and load level; multiple different node combinations are screened out according to the importance index, Respectively cut off the corresponding nodes in each node combination from the topology G, and obtain the recovery topology T corresponding to the number of node combinations n ; Based on the recovery topology T n The load parameters of the medium load equipment and the load parameters of the load equipment in the topology G are calculated for each restoration topology T n The load loss index; according to each recovery topology T n Corresponding load...
Embodiment approach
[0066] Select the top m nodes in the order of importance index ranking, m1 , restore the topology T 2 , ..., restore topology T m , and then restore the topology T based on 1 The load parameters of the medium load equipment and the load parameters of the load equipment in the topology G are calculated to restore the topology T 1 The loss of load exponent, based on the restoration topology T 2 The load parameters of the medium load equipment and the load parameters of the load equipment in the topology G are calculated to restore the topology T 2 The load loss index of , ... until the topology T is restored mAfter the load loss index is calculated, the vulnerability values of each recovery topology are calculated separately, and the output of the recovery topology with the highest vulnerability value is screened out to obtain the identification results of vulnerable nodes.
[0067] Specifically, based on the recovery topology T in the above embodiments n The load paramet...
Embodiment 2
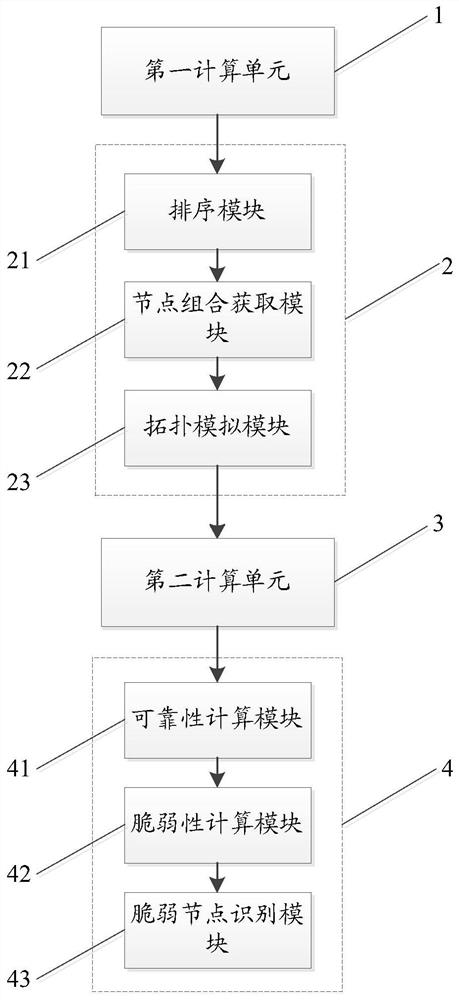
[0076] see figure 1 with image 3 , this embodiment provides a power distribution system fault simulation system for data centers, including a first calculation unit 1, a topology simulation unit 2, a second calculation unit 3 and a result output unit 4 connected in sequence;
[0077] The first calculation unit 1 is used to sequentially calculate the importance index of each node in the topology G based on the topology G of the power distribution system and the load parameters of the load equipment, and the load parameters include the load amount and the load level;
[0078] The topology simulation unit 2 is used to screen out a number of different node combinations according to the importance index, respectively cut off the corresponding nodes in each node combination from the topology structure G, and obtain the restoration topology T corresponding to the number of node combinations n ;
[0079] The second calculation unit 3 is used to restore the topology T based on n Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com