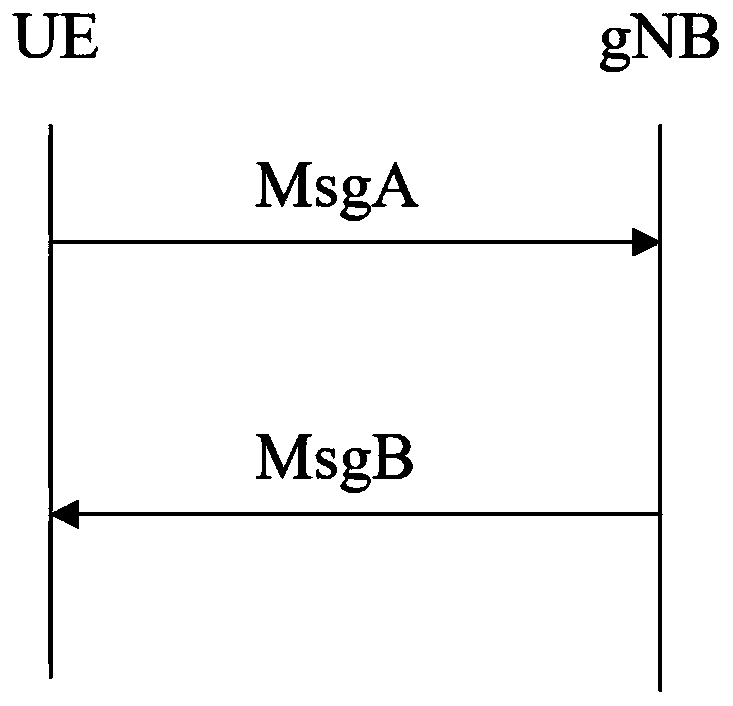
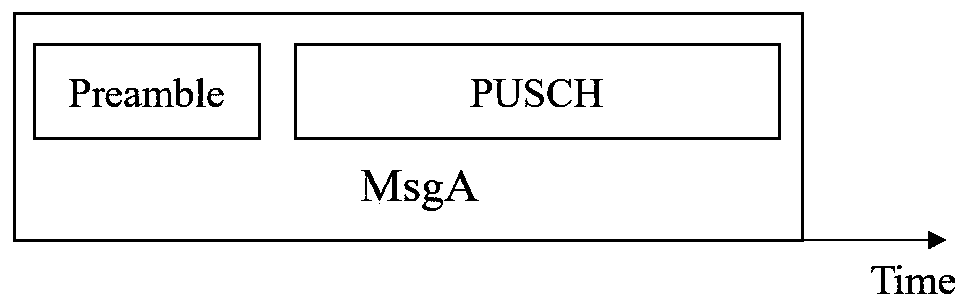
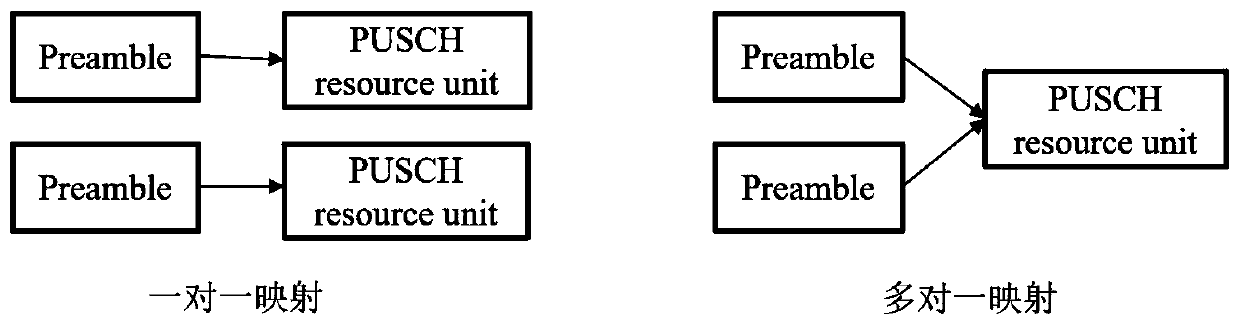
Resource allocation and transmission method of MsgA in two-step random access
A technology of random access and resource allocation, which is applied in the field of mobile communication, can solve problems such as the reduction of PUSCH decoding success rate, PUSCH resource conflict, and reduce the complexity of PUSCH decoding, so as to achieve a balance between resource utilization and random access success rate, and improve Probability of success, effect of improving utilization efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0034] A resource configuration and transmission method for MsgA in two-step random access, comprising the following steps:
[0035] Step 1, group the preamble under each RO;
[0036] Step 2, dividing the time-frequency domain resources of one or more POs corresponding to the RO according to the time domain to form L sets of continuous PUSCH resources in the time domain, wherein each set of continuous PUSCH resources in the time domain includes several PRUs;
[0037] Step 3, when the UE chooses to send a certain preamble on the RO, then repeatedly send the MsgA payload L times on the PRU corresponding to the L PUSCH resource sets of the PO;
[0038] Step 4, each time the MsgA payload is sent, a set of preambles is mapped to a PRU of the PUSCH resource set;
[0039] Step 5, when sending the MsgA payload repeatedly, a different mapping relationship between preamble and PRU is used for each sending.
[0040] In this embodiment, the preambles under each RO are grouped at equal i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com