Data permission processing method, device and equipment
A technology of data rights and processing methods, applied in the computer field, can solve the problems of high system intrusion, strong coupling between rule logic and business code, and high cost of rights modification, and achieve the effect of solving strong coupling
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
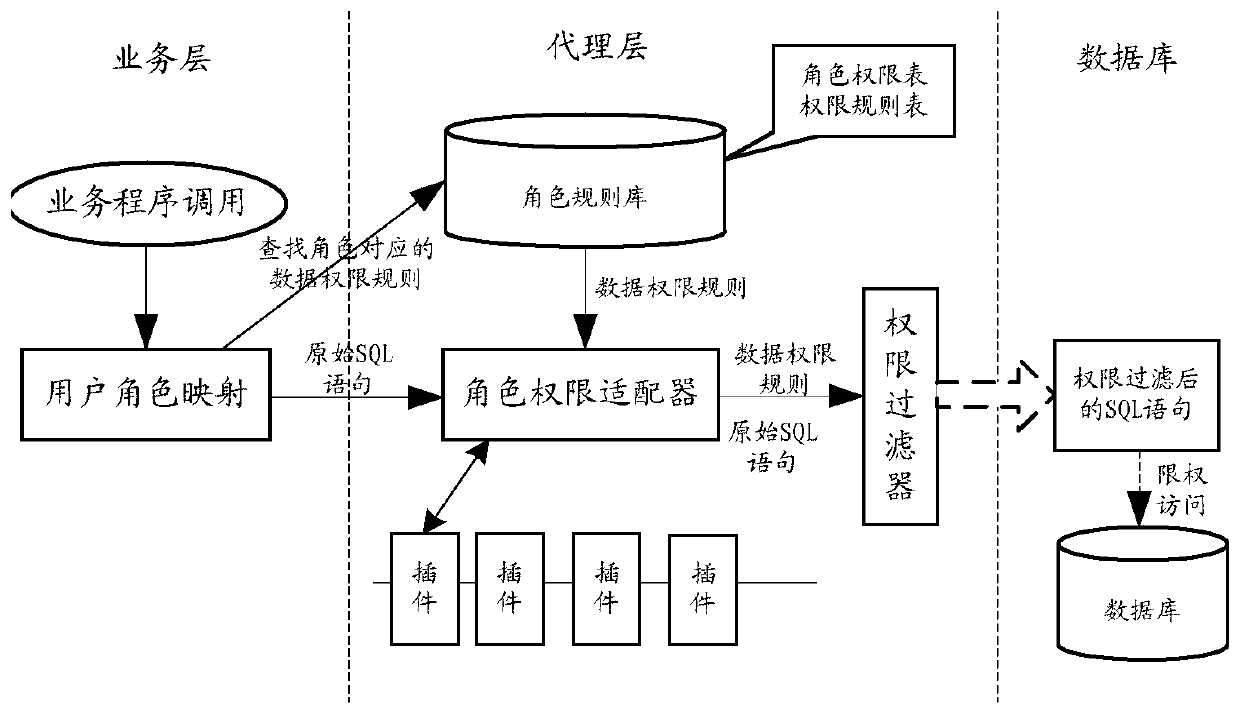
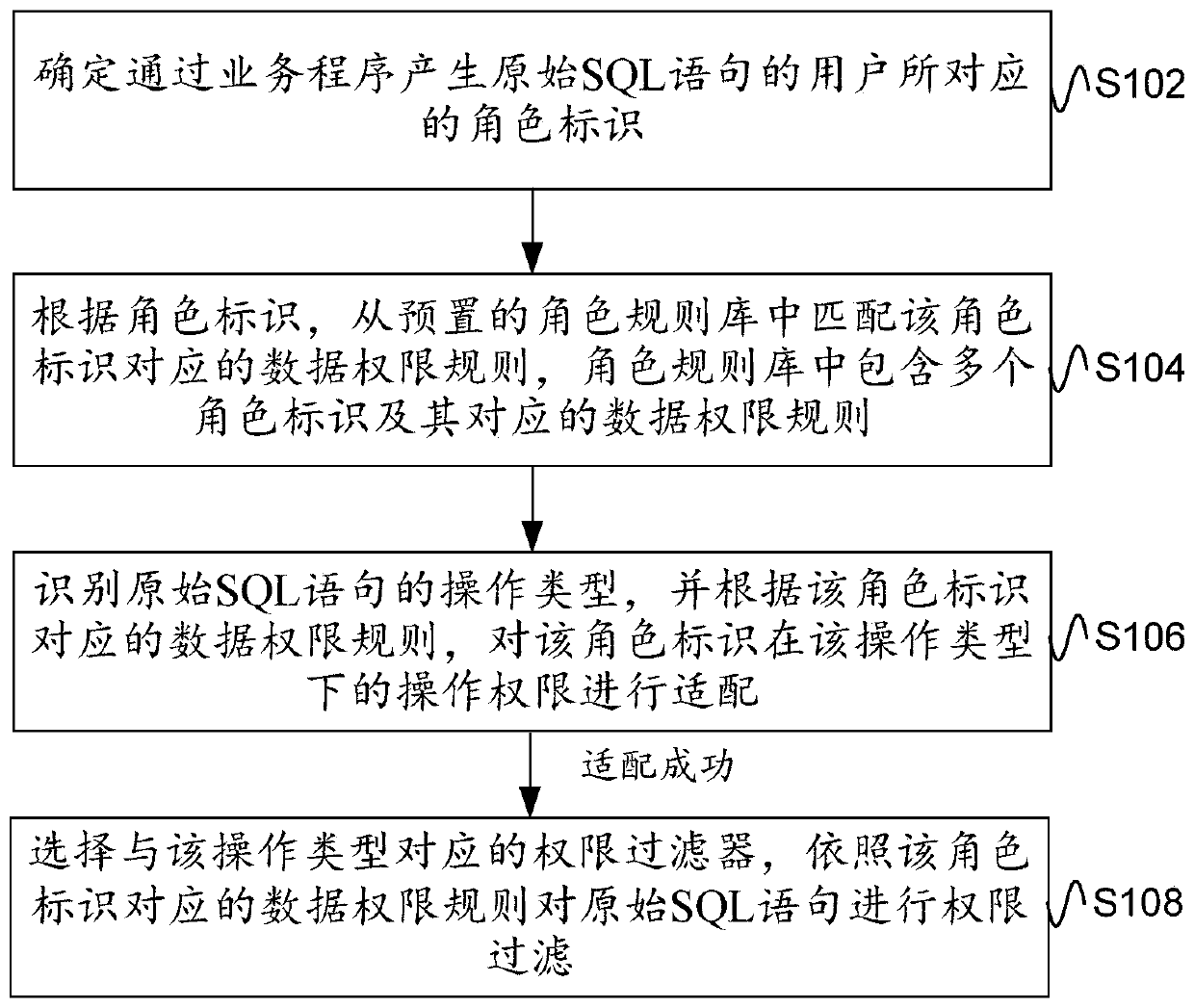
[0053] Based on the above application scenario architecture, figure 2 Schematic flowchart of the data rights processing method provided by the embodiment of this specification Figure 1 , figure 2 methods in figure 1 The proxy layer in the implementation, such as figure 2 As shown, the method includes the following steps:
[0054] Step S102, determining the role identifier corresponding to the user who generates the original SQL statement through the business program.
[0055] Among them, the role identifier is used to represent the role category to which the user belongs. For example, in an enterprise, the role category can be divided based on the user's rank, for example, it can be divided into roles such as: employee, middle-level leader, senior leader, boss, etc. Each role corresponds to a unique Role ID. The role identifier corresponding to the user can be set in advance through user role mapping at the business layer.
[0056] When the user initiates a data acce...
Embodiment 2
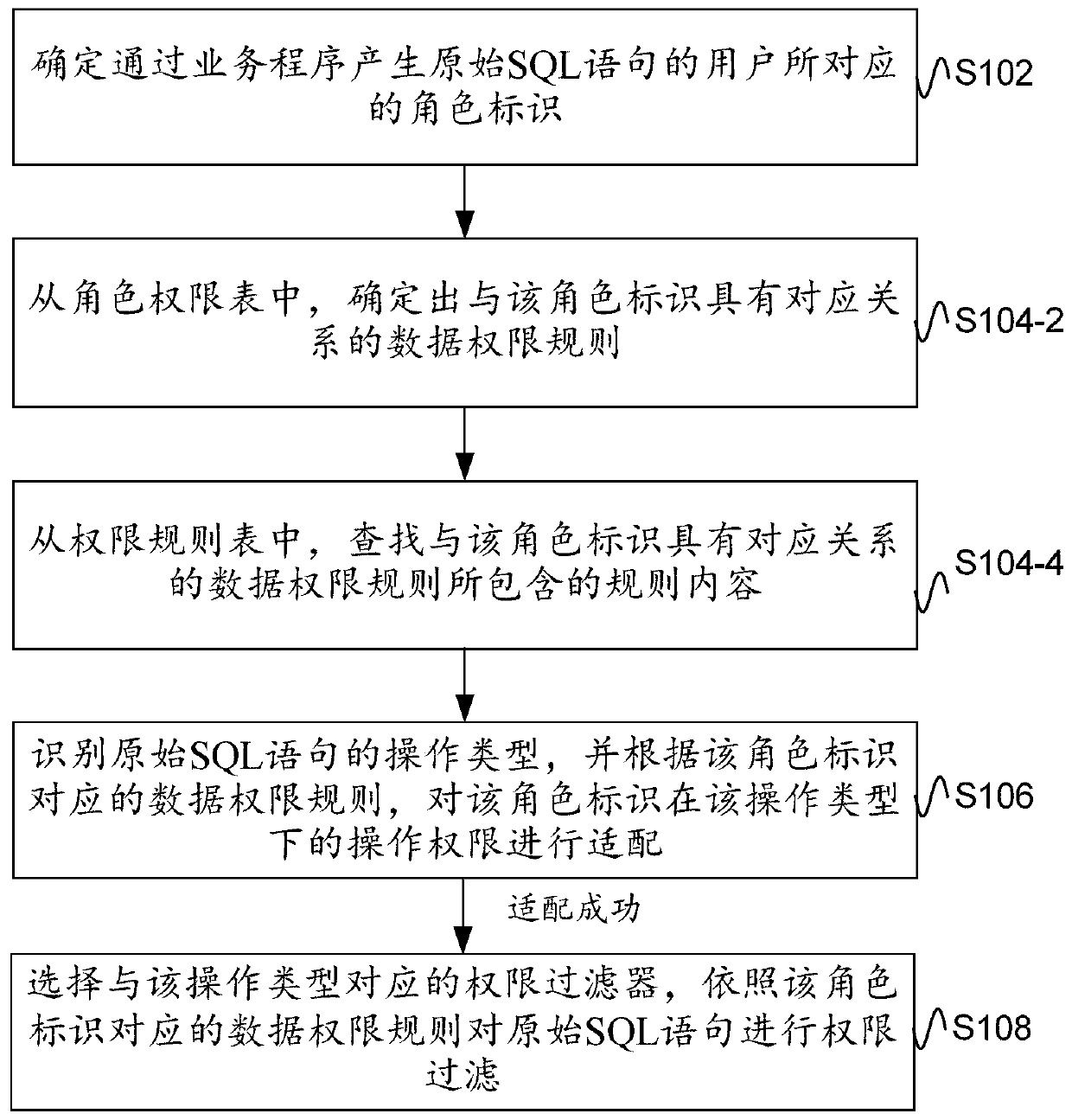
[0068] This embodiment is on the basis of embodiment one, to figure 2 The data permission processing method shown in the figure is expanded and supplemented.
[0069] exist figure 2 In the method shown, the role rule base may include a role permission table and a permission rule table, the role permission table is used to identify the corresponding relationship between the role identifier and the data permission rule, and the permission rule table is used to store the rule content of the data permission rule;
[0070] Correspondingly, as image 3 As shown, the step S104 may include:
[0071] S104-2. Determine a data permission rule corresponding to the role identifier from the role permission table.
[0072] In the role permission table, each role identifier can correspond to at least one data permission rule, and only the corresponding relationship between the role identifier and the data permission rule is recorded in the role permission table. Since only this correspo...
Embodiment 3
[0101] corresponding to the above Figure 2 to Figure 7 The described data rights processing method is based on the same technical concept, and the embodiment of this specification also provides a data rights processing device. Figure 8 A schematic diagram of the module composition of the data rights processing device provided by the embodiment of this specification, the device is used to execute Figure 2 to Figure 7 Describe the data rights processing method, such as Figure 8 As shown, the device includes:
[0102] The role determination module 201 determines the corresponding role identification of the user who generates the original SQL statement through the business program;
[0103] The authority matching module 202, according to the role identifier, matches the data authority rule corresponding to the role identifier from the preset role rule library, and the role rule library includes a plurality of role identifiers and corresponding data authority rules;
[0104]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com