Risk assessment model training, risk assessment method and device
A risk assessment model and risk assessment technology, applied in the field of risk assessment methods and devices, and risk assessment model training, can solve problems such as low efficiency, reduce costs and expenses, improve utilization, and improve risk assessment efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The solution provided in this specification will be described below with reference to the accompanying drawings.
[0039] Before describing the solution provided by this specification, the inventive concept of the solution is described as follows.
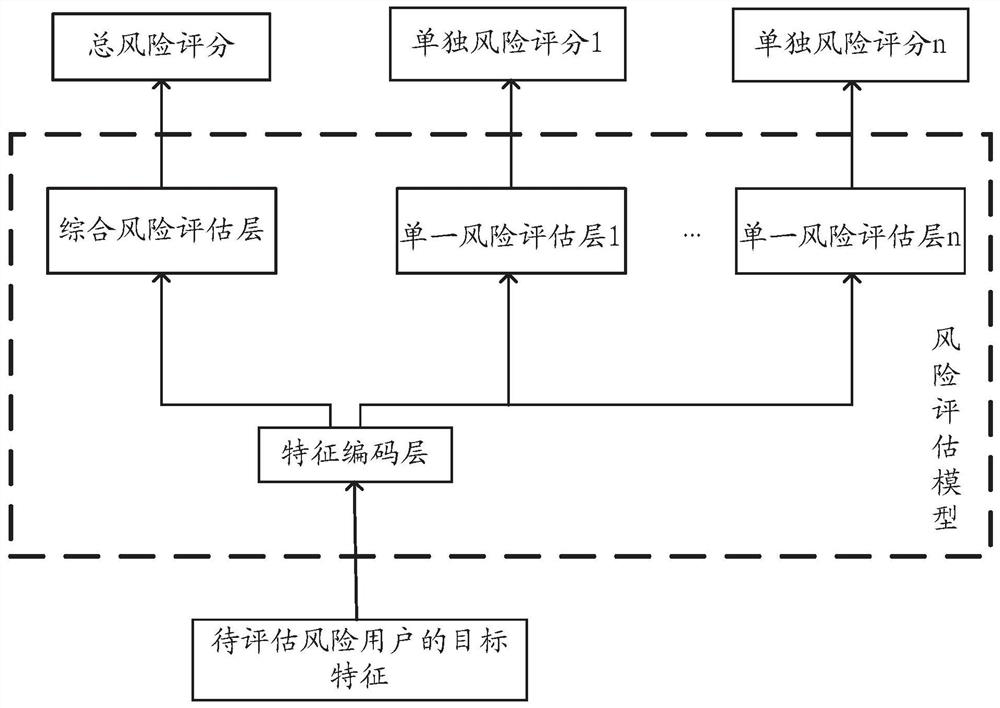
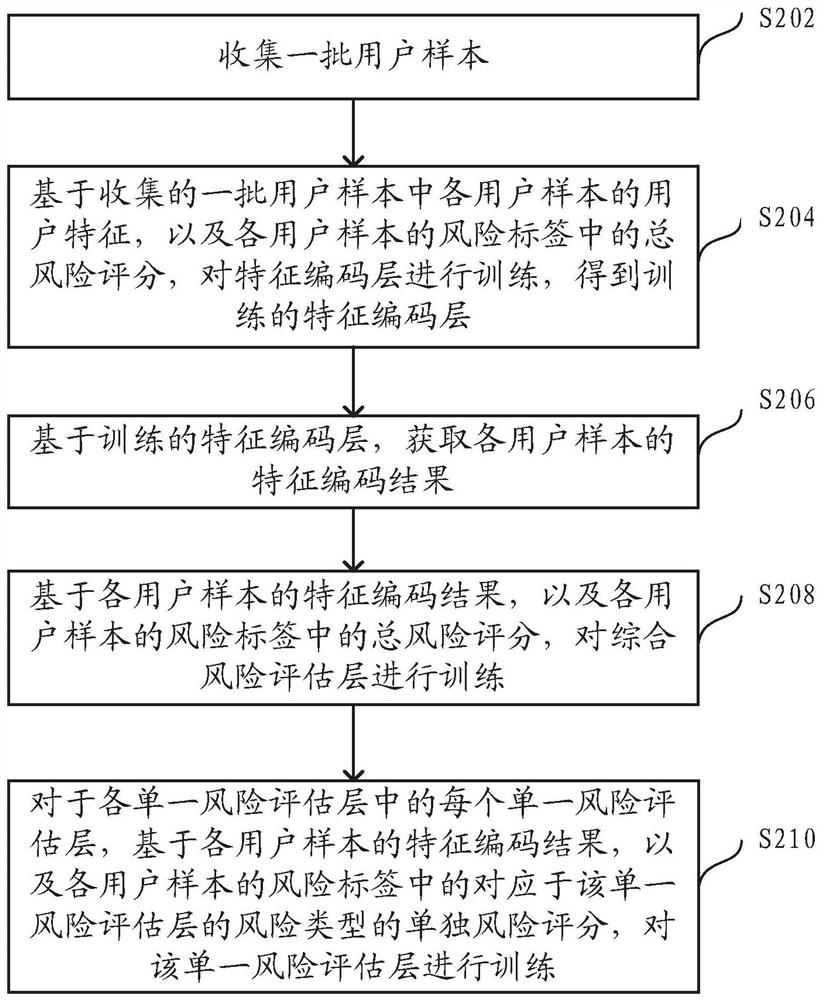
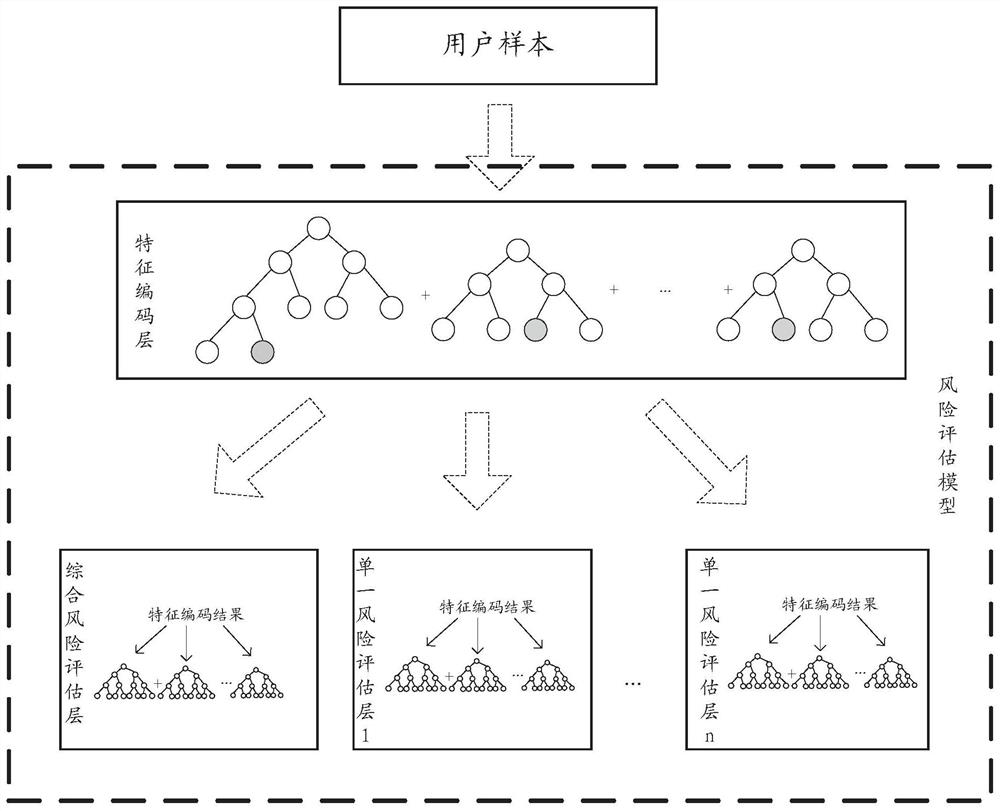
[0040] As mentioned above, in the traditional technology, the trained risk assessment model can usually only realize the assessment of a single risk type, that is to say, the risk assessment model trained by the traditional method is usually a single-task model, which will greatly waste the training. resource. Applicants of the present application have taken into account that there are often similarities between the tasks of assessing different risk types. For example, 48% of fraudulent users are high-risk users who violate the rules and regulations. Furthermore, there is a strong correlation between the task of assessing combined risks and the task of assessing individual risks. For example, a user with a higher individu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com