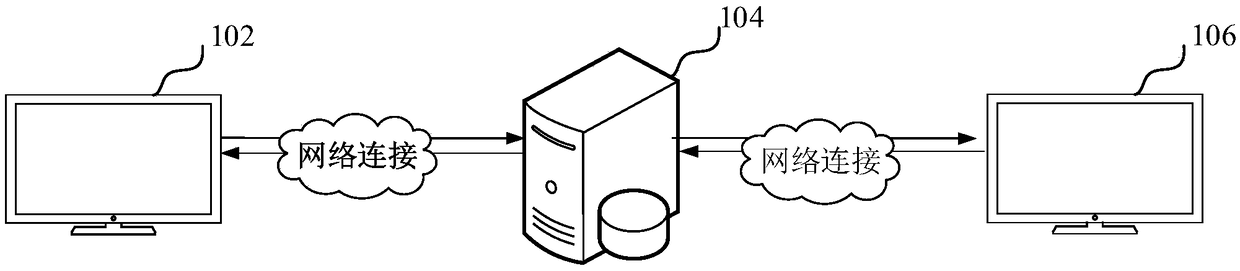
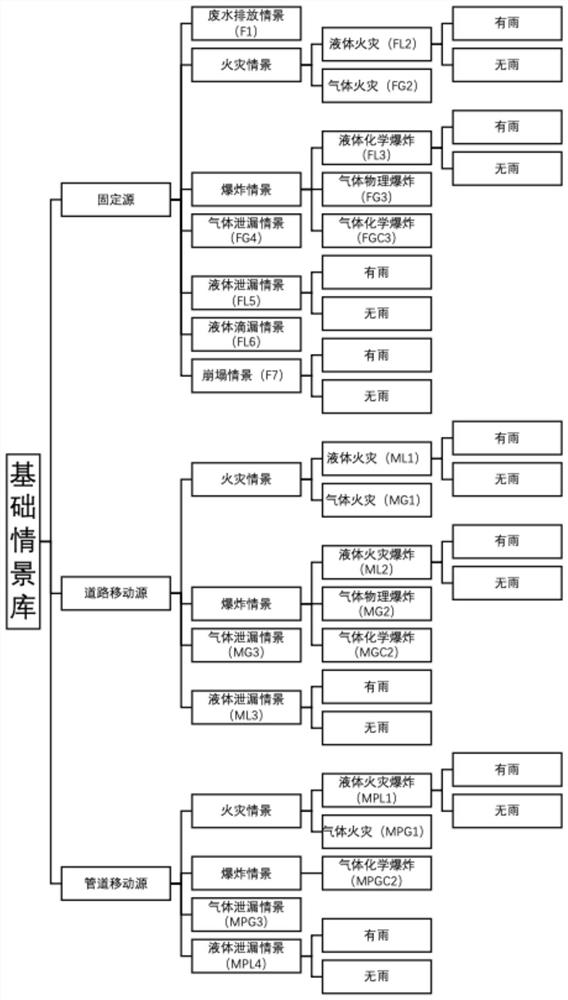
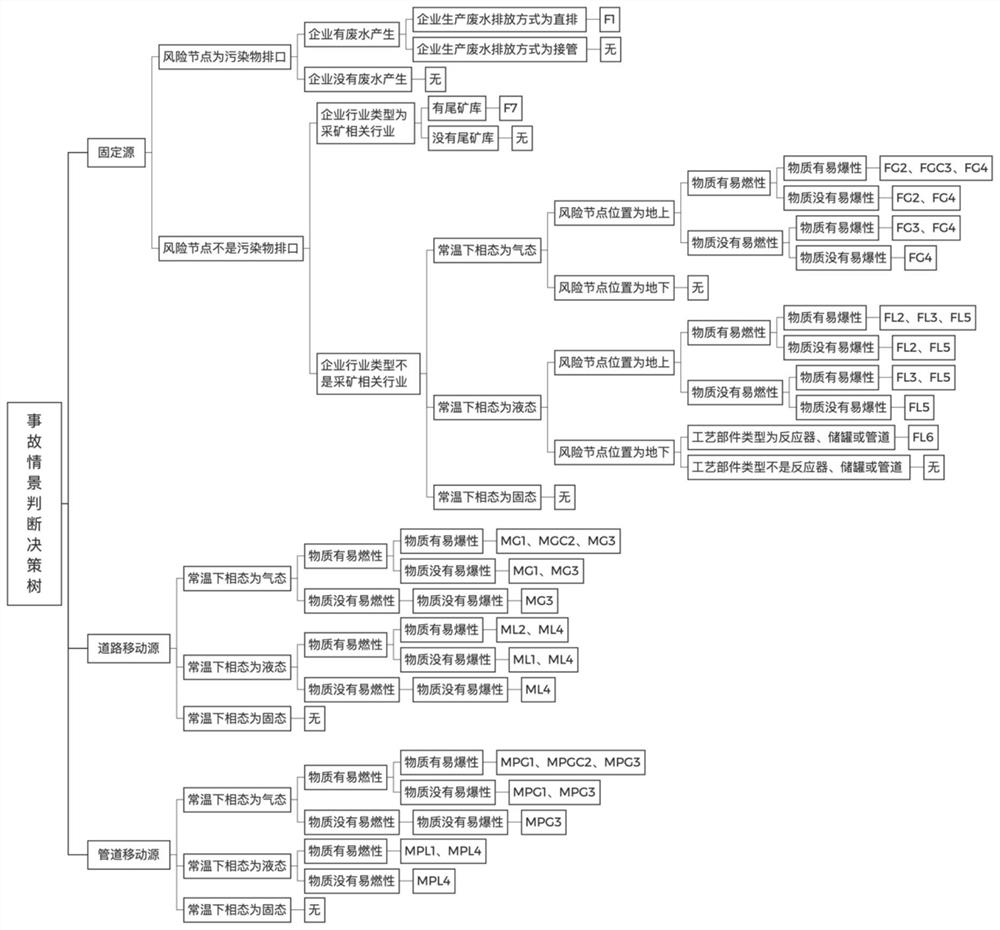
Patents
Literature
36results about How to "Improve risk assessment efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Power consumer screening method and system based on multi-dimensional risk evaluate index
InactiveCN106557882AReduce riskConvenient and intuitive monitoringResourcesScreening methodRisk rating
The invention discloses a power consumer screening method and system based on multi-dimensional risk evaluate indexes; the method comprises the following steps: obtaining power consumer information; screening to obtain a power consumption credit type risk evaluate index and a law credit type risk evaluate index, thus obtaining the basic credit type risk evaluate index; obtaining real scores of various risk evaluate indexes of each power consumer; using a hierarchy analysis method to respectively solve the weight of the basic credit type risk evaluate index and the power consumption credit type risk evaluate index in a two-two comparison mode according to the real score values of the basic credit type risk evaluate index and the power consumption credit type risk evaluate index of the power consumer; obtaining a power consumer integral risk rating score value; presetting risk grades of the power consumer and power consumer integral risk rating score value sections corresponding to each risk grade; finally determining the power consumer risk grade according to the power consumer integral risk rating score value.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
Traffic accident risk estimation method and system
InactiveCN106897826AImproving the Efficiency of Traffic Accident Risk AssessmentImprove risk assessment efficiencyCharacter and pattern recognitionMachine learningSpectral clustering algorithmEstimation methods
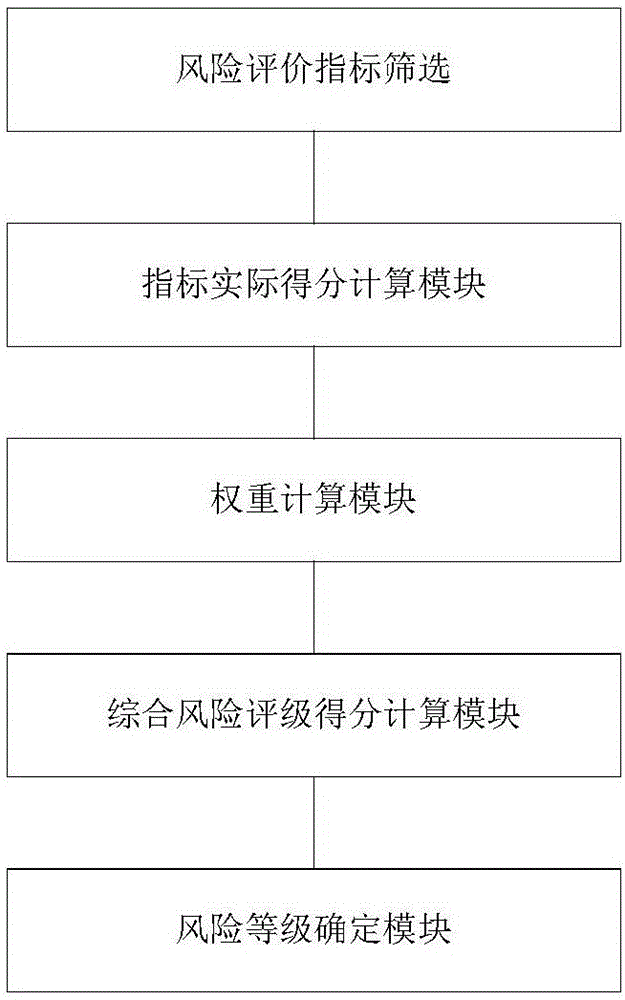
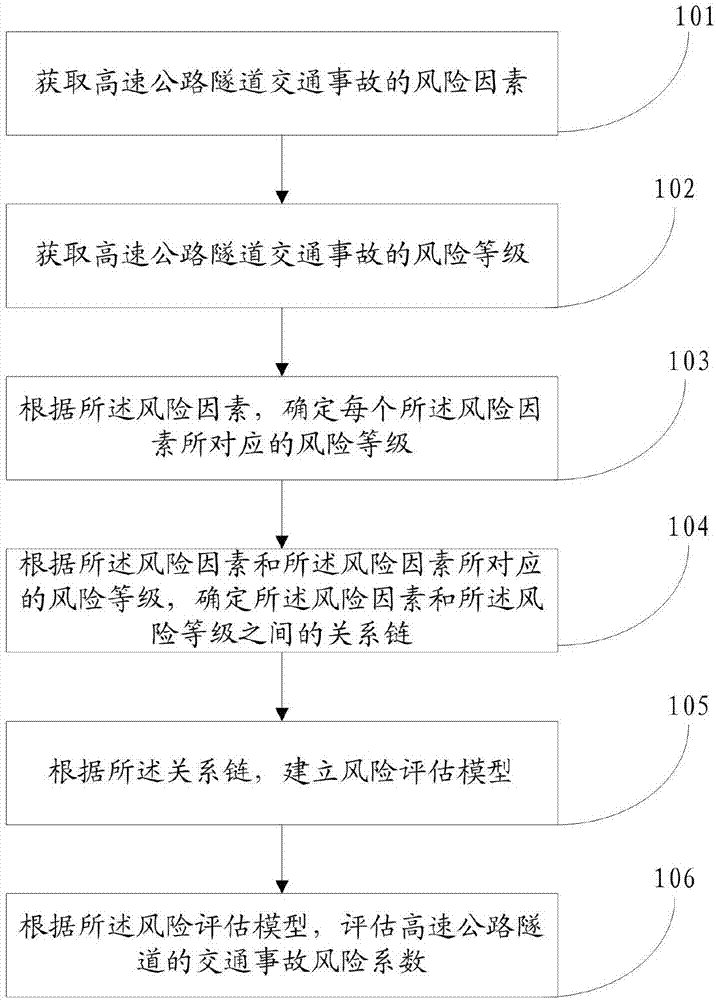
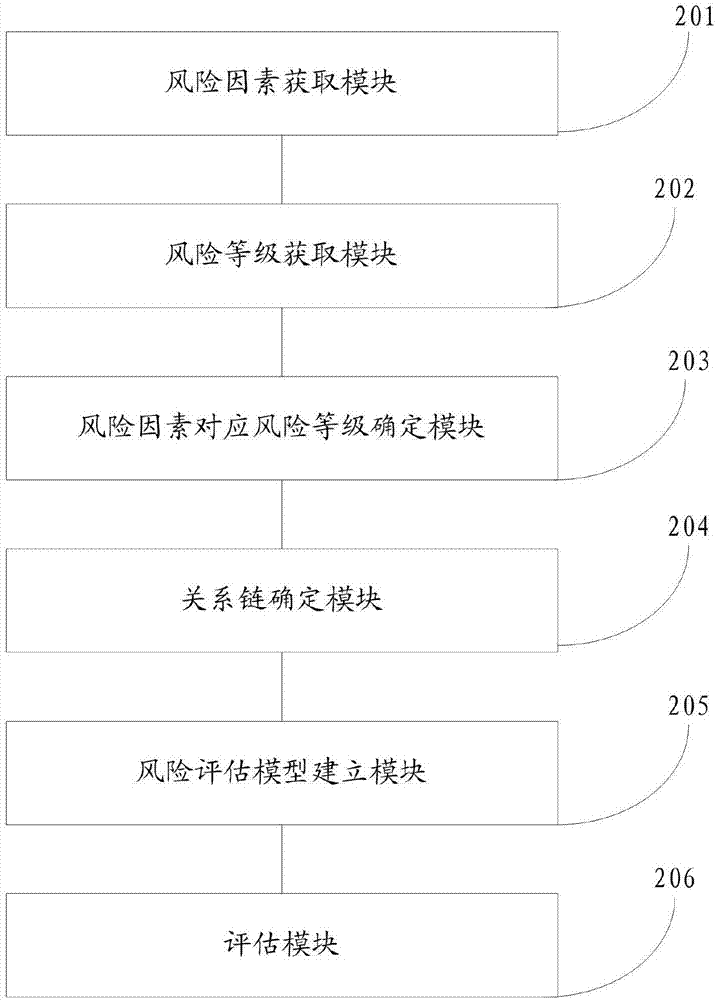
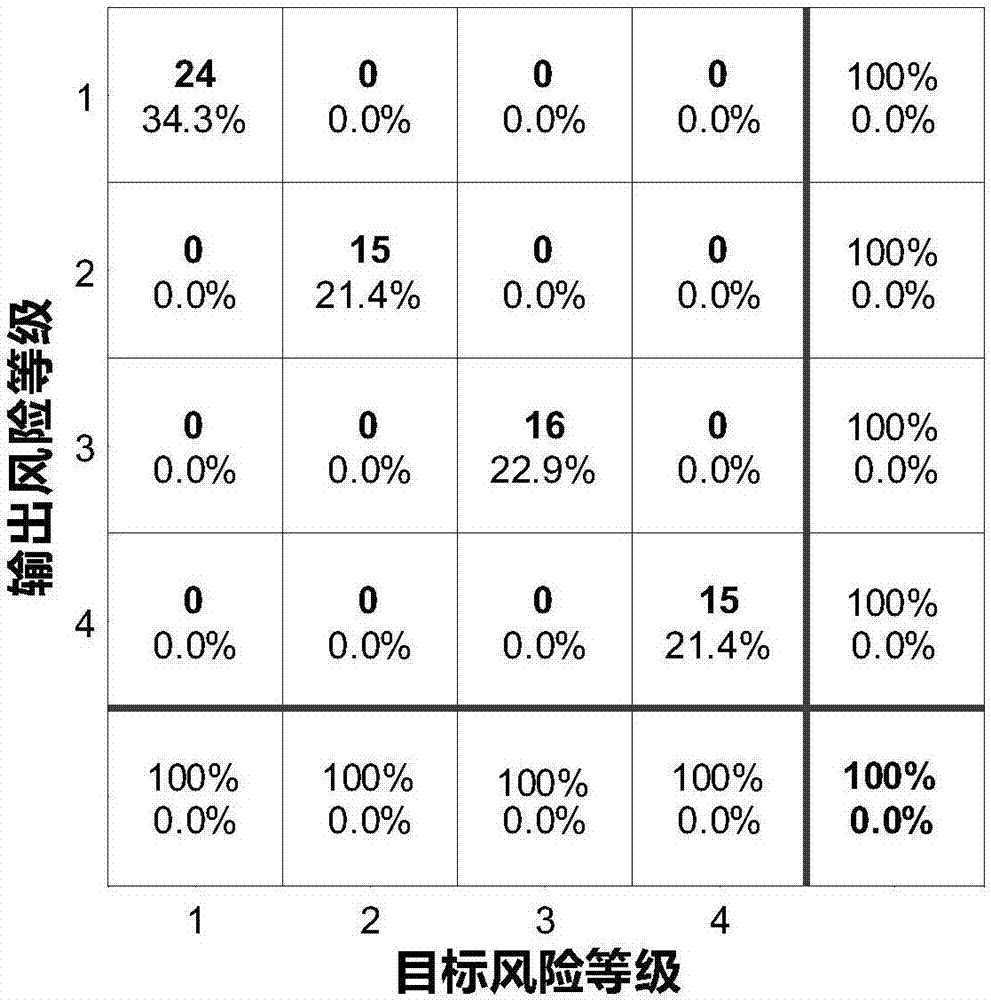
The invention discloses a traffic accident risk estimation method and system. According to the method and the system, a corresponding relation chain between a risk factor and a risk class is calculated and determined by acquiring an expressway tunnel traffic accident risk factor and an expressway tunnel traffic accident risk class and employing a spectral clustering algorithm; a risk estimation model is constructed according to the relation chain and an extreme learning algorithm; and the final risk class corresponding to the risk factor can be obtained by inputting arbitrary risk factor data to the risk estimation model. Therefore, with the adoption of the method or the system provided by the invention, the expressway tunnel traffic accident risk estimation efficiency is effectively improved, so that the expressway tunnel traffic accident risk estimation efficiency process is more high-efficiency and convenient, and the safety evaluation of expressway tunnel operation period is accurately and effectively achieved.
Owner:JILIN UNIV +1
Risk assessment method and device and storage medium thereof
PendingCN110197315AThe assessment results are accurateLow costFinanceResourcesApplication softwareRisk assessment
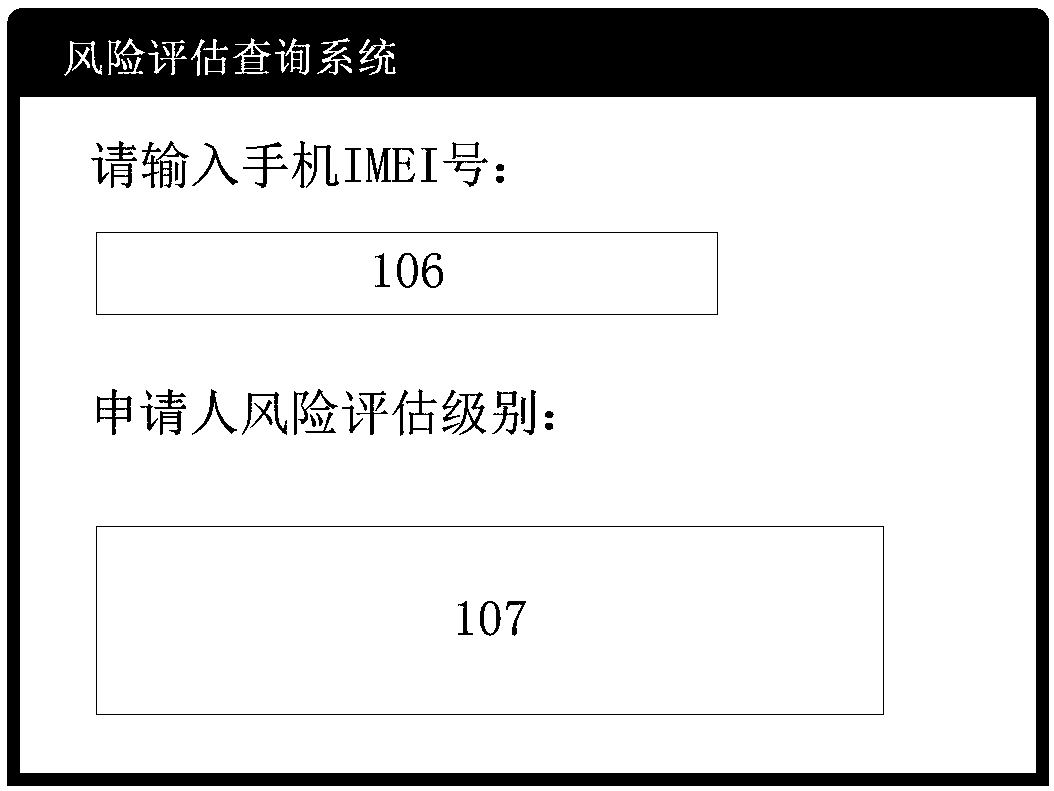
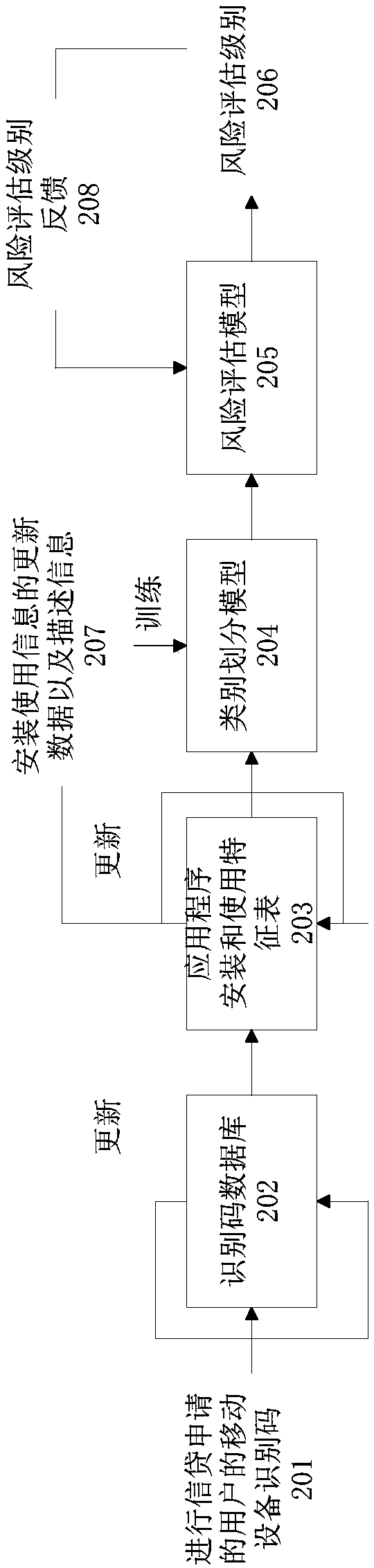
The invention provides a risk assessment method and device, and a storage medium. The method comprises the steps of receiving an identification code of a mobile device from a terminal device; acquiring installation and use information of the application program corresponding to the identification code and generating category information of the application program; and generating a risk assessmentlevel corresponding to the identification code based on the installation and use information of the application program and the category information, and sending the risk assessment level to the terminal device. According to the method disclosed by the invention, category division and portrait drawing are carried out on the application programs of the users who carry out credit application based on the information, and multi-dimensional portrait drawing is carried out based on the financial consumption habits of the users who carry out credit application, so that the accurate evaluation resultof the credit and fraud risks of the users who carry out credit application can be obtained.
Owner:TENCENT TECH (SHENZHEN) CO LTD
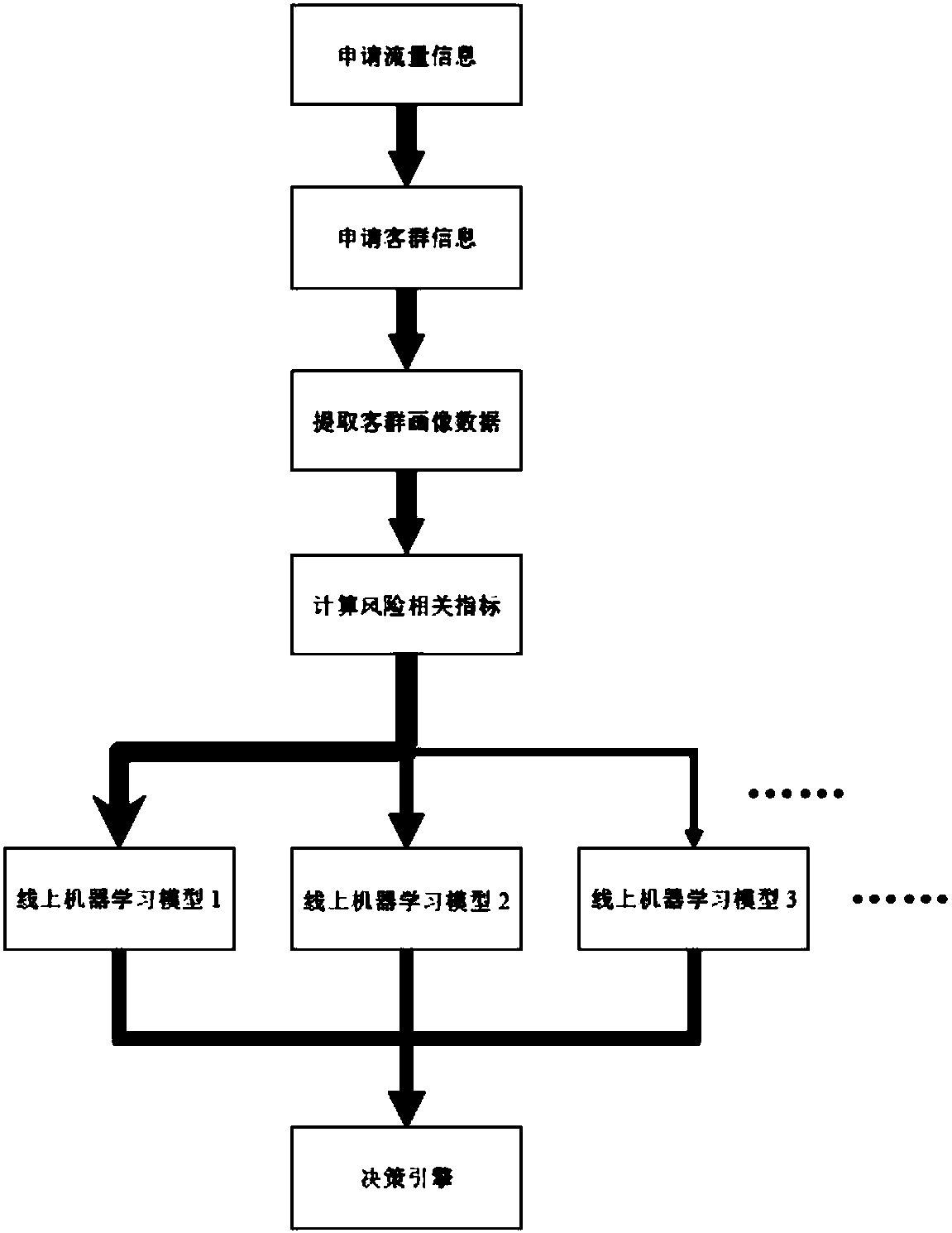
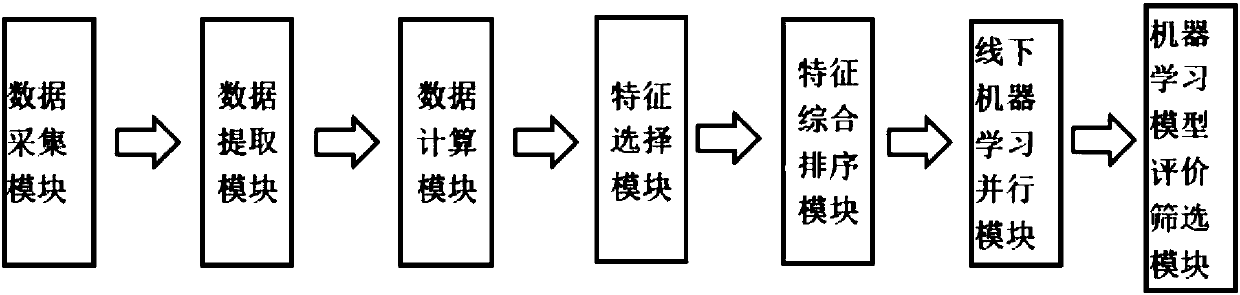
Risk control model application methods and systems based on concurrence of multiple machine learning models
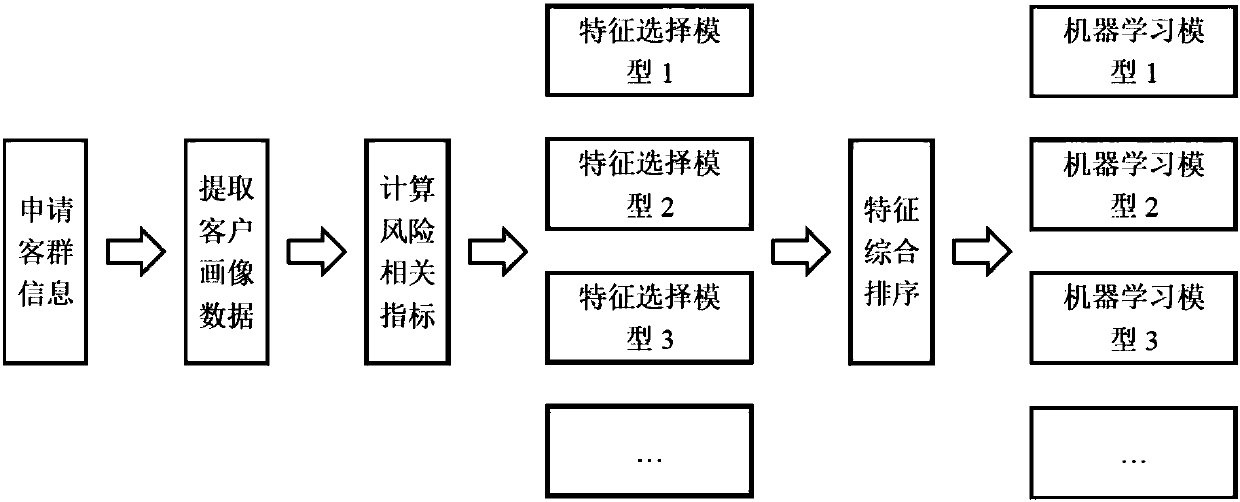
The method discloses a risk control model application methods and systems based on a concurrence of multiple machine learning models. An offline risk control model application method thereof includes:collecting application customer group information; extracting customer portrait data from the above-mentioned information; processing the above-mentioned portrait data, and calculating risk-related indexes; respectively utilizing different feature selection models to process the above-mentioned risk-related indexes to obtain corresponding single-model feature orders; carrying our comprehensive sorting on the obtained corresponding single-model feature orders; and respectively utilizing multiple machine learning models to carry out modeling processing on comprehensively sorted features, evaluating a running effect of each machine learning model, and screening out the plurality of machine learning models with higher ranks. The plurality of machine learning models are put into online runningto process online application flow, and processing results are used as decision bases of whether credit extension is carried out. The flow is allocated in online running according to the rank of eachmachine learning model. By adopting the methods, efficiency of risk evaluation can be improved, and a result is more reliable.
Owner:上海安趣盈科技有限公司
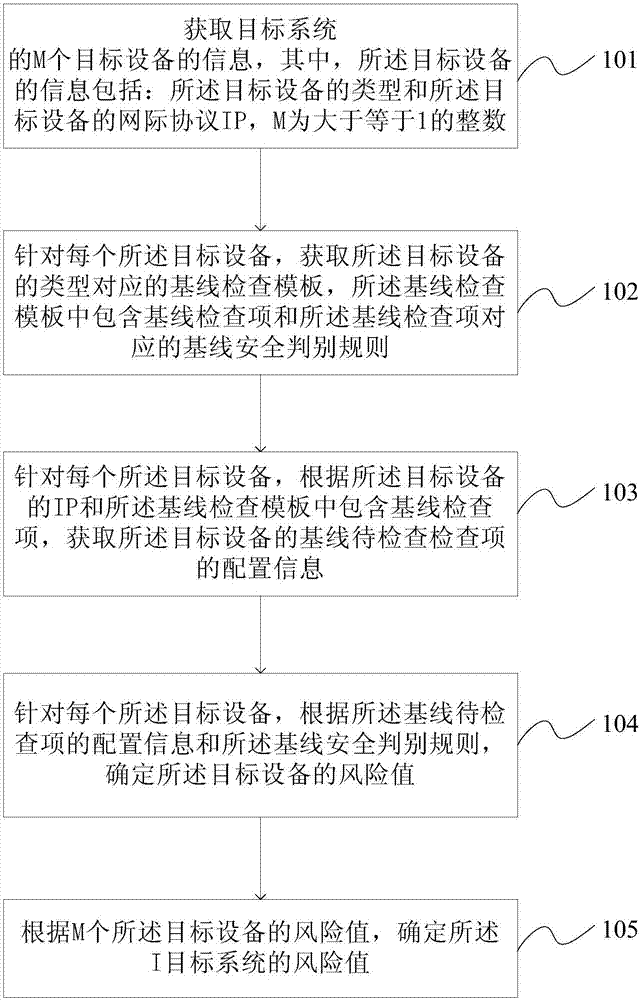
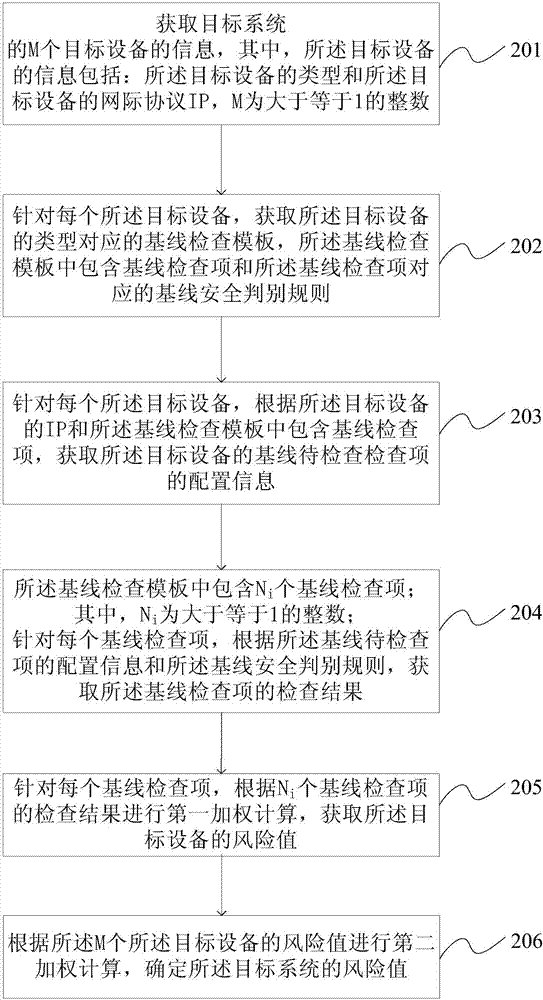
Network safety evaluation method and device based on configuration check
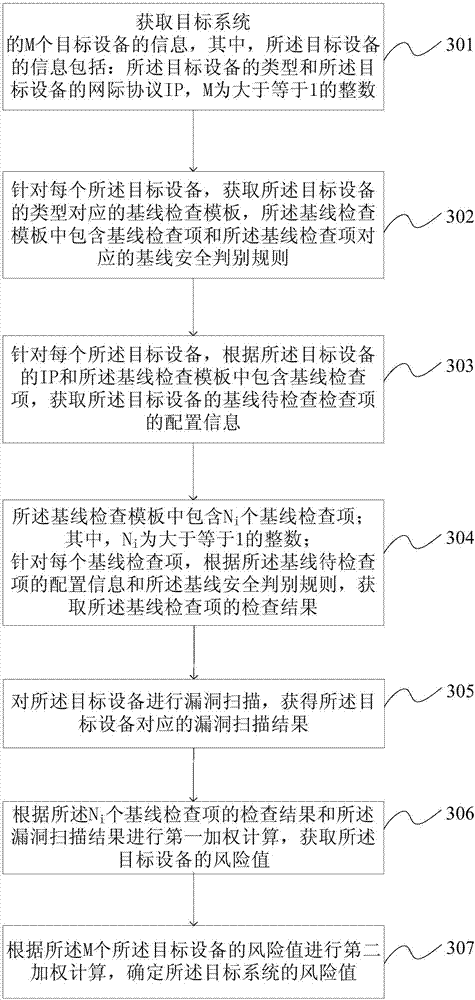
InactiveCN107294979ASolve poor intuitionImprove risk assessment efficiencyData switching networksGoal systemRisk evaluation
The invention provides a network safety evaluation method and device based on configuration check. The network safety evaluation method comprises obtaining information of M target devices of a target system, wherein the information of the target devices comprises types and internet protocols (IP) of the target devices, and M is an integer which is larger than or equal to 1; aiming at each target device, obtaining a baseline check template corresponding to the type of the target device, wherein the baseline check template includes a baseline check item and a baseline safety discrimination rule corresponding to the baseline check item; obtaining configuration information of a baseline item to be checked of the target device in dependence on the IP of the target device and the baseline check item included in the baseline check template; determining the value-at-risk of the target device in dependence on the configuration information of the baseline item to be checked and the baseline safety discrimination rule; and furthermore determining the value-at-risk of the target system. The network safety evaluation method and device based on configuration check can solve the problem that the existing ICS risk evaluation method is poor in visualization.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
Network risk assessment method and device, electronic equipment and storage medium
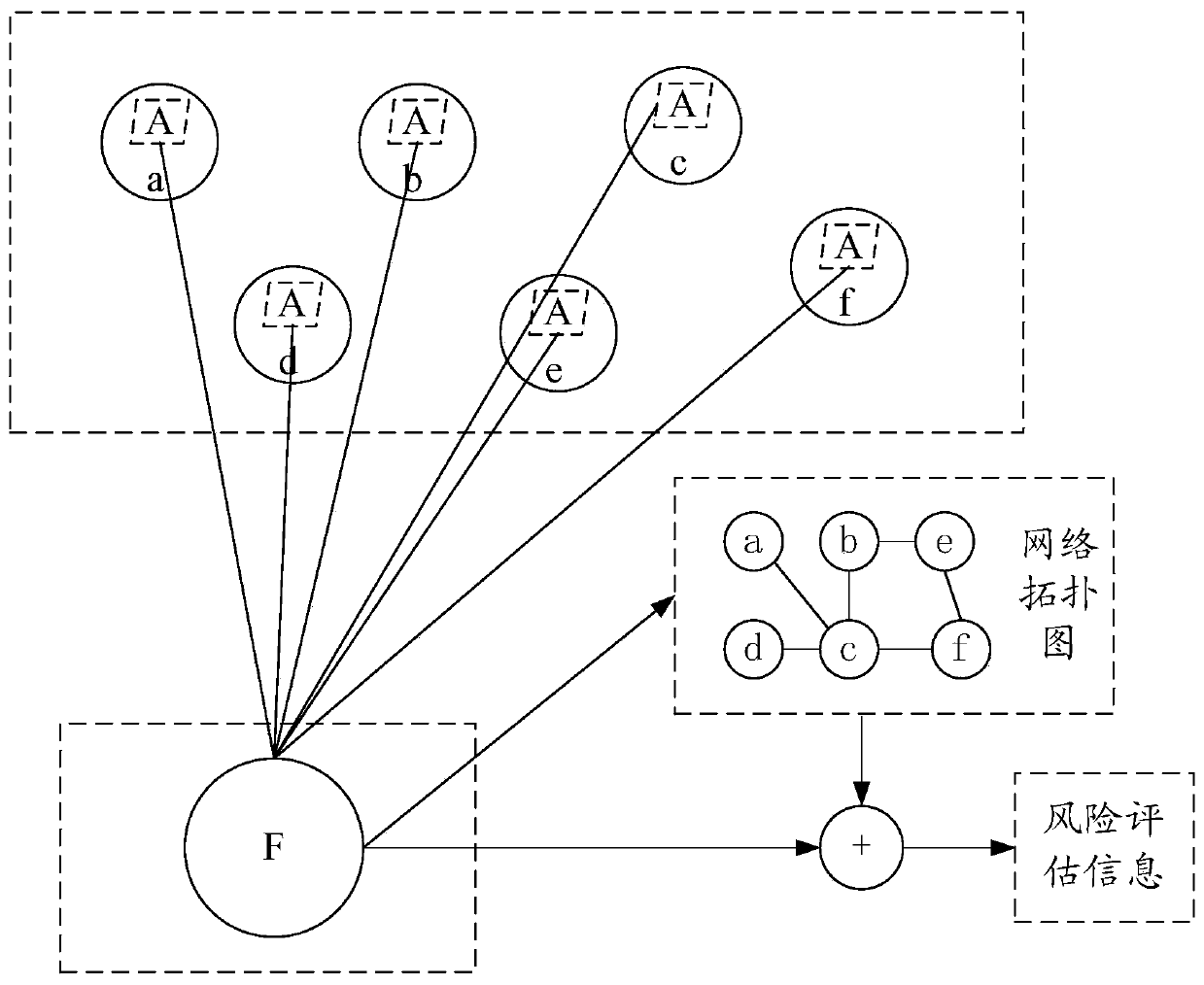
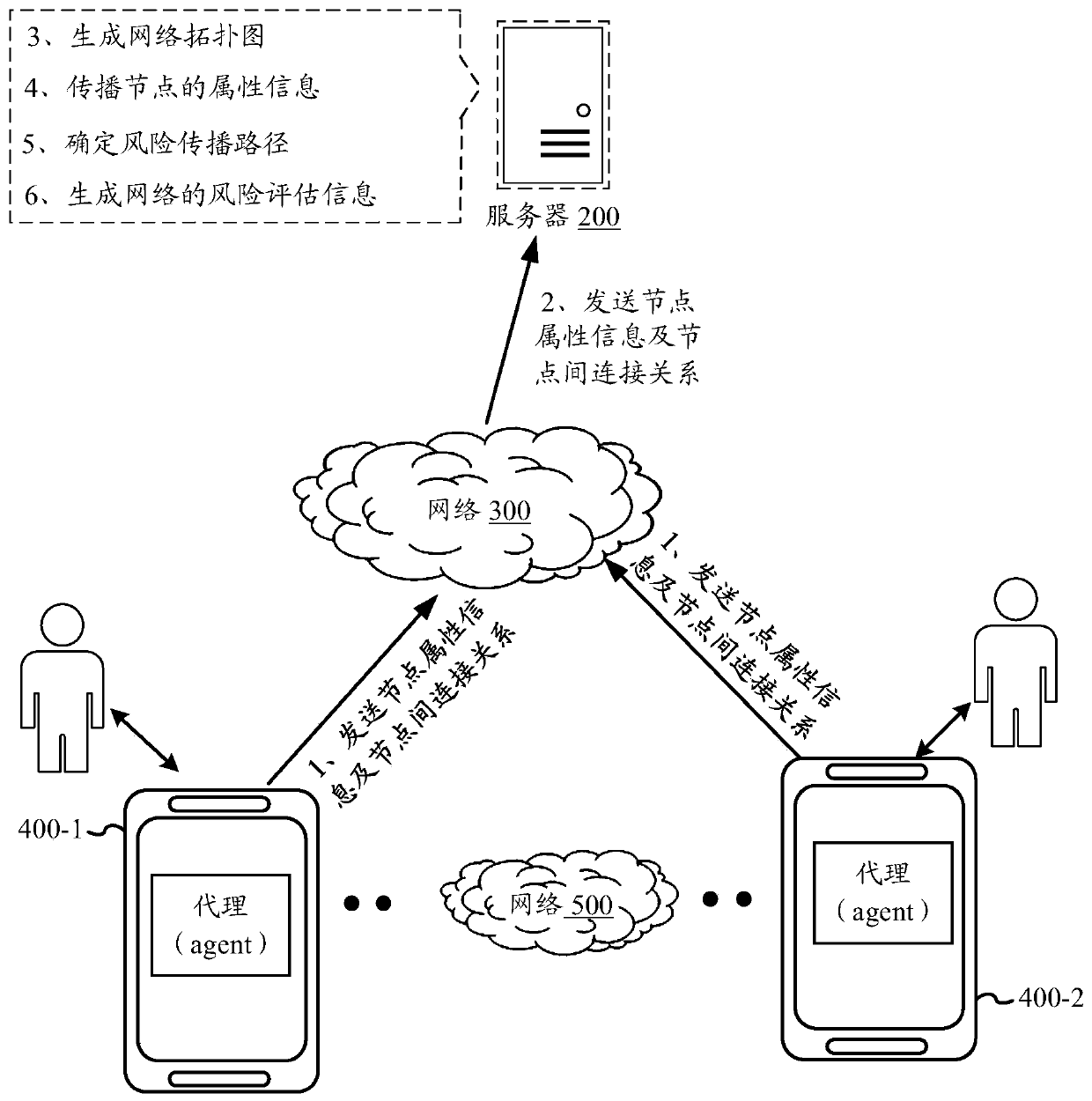
ActiveCN110557393AImprove network securityGet rid of the dependence of manual interventionTransmissionAssessment methodsTopological graph
The invention provides a network risk assessment method and apparatus, an electronic device and a storage medium. The method comprises the steps of receiving attribute information sent by each node inthe same network and a connection relationship among the nodes; generating a corresponding network topological graph according to the attribute information of each node in the network and the connection relationship among the nodes; taking a sensitive node with risk as a starting point of a propagation process in the network topological graph, and propagating attribute information of a forward node to the passed node according to the connection relationship; determining a risk propagation path correspondingly formed when the propagation process converges, and attribute information received byeach node in the risk propagation path; and generating risk assessment information of the network based on the attribute information received by each intermediate node in the risk propagation path. According to the invention, risk assessment of the network can be carried out more accurately, and the network security is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Risk assessment system construction method and device, computer equipment and storage medium
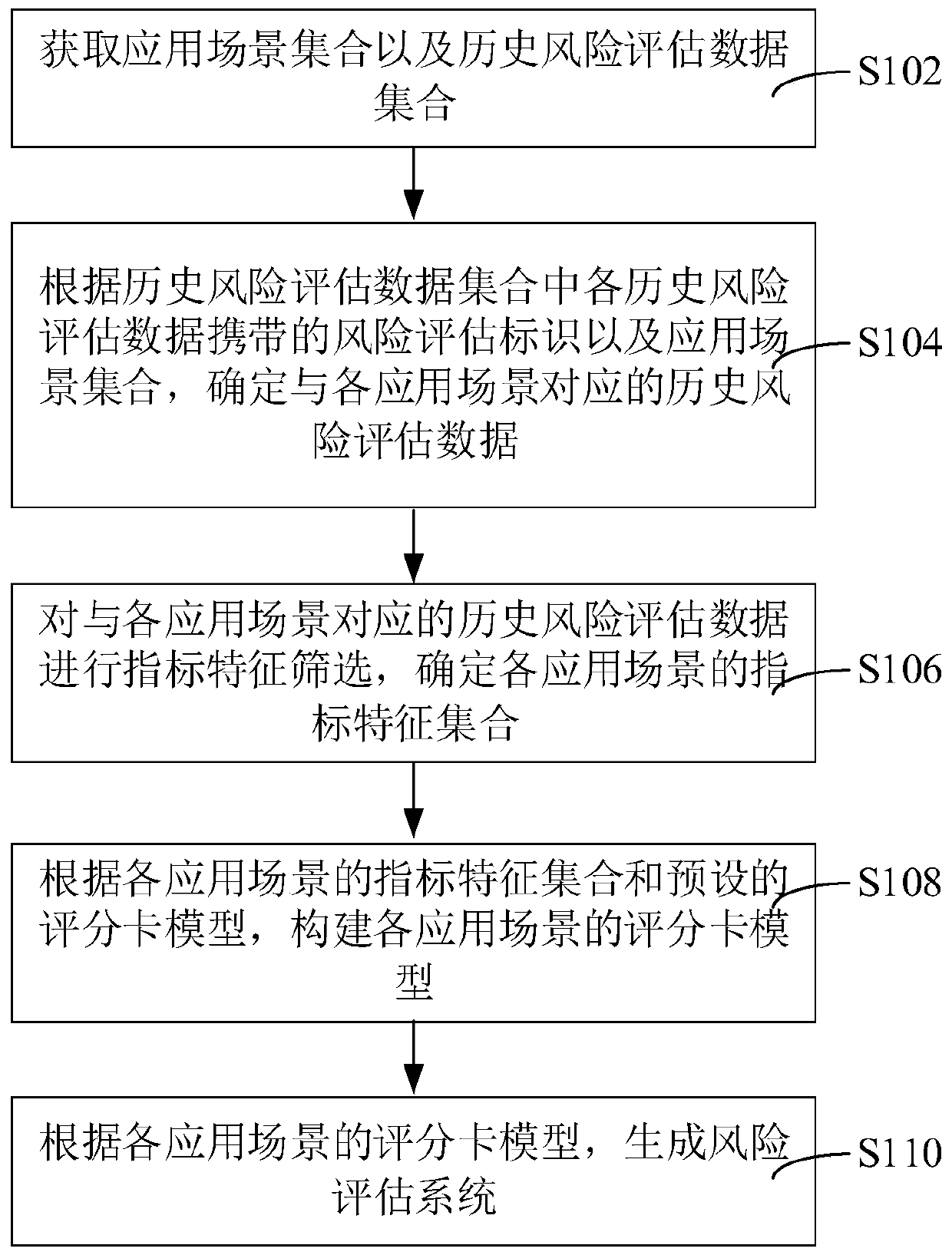
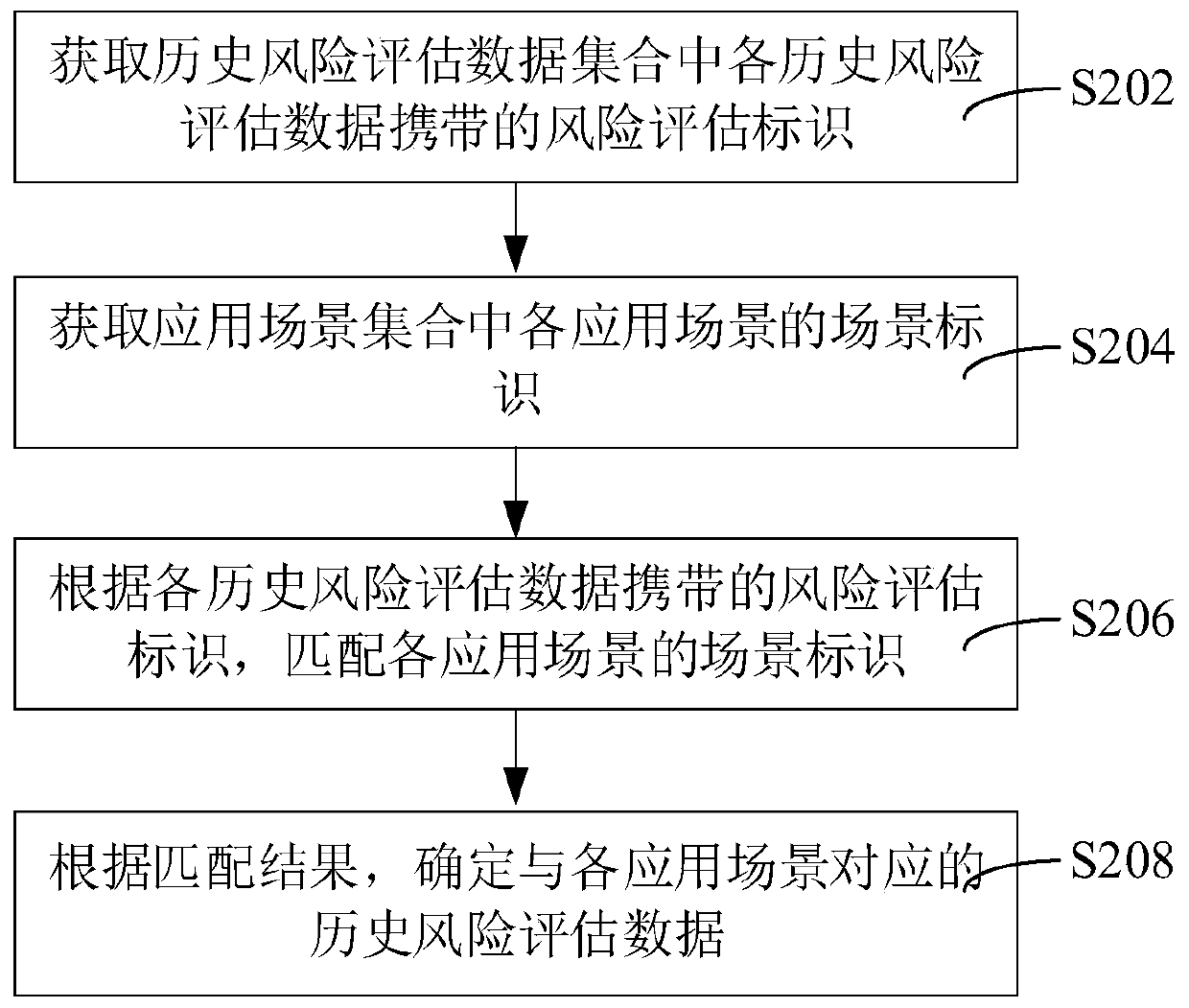
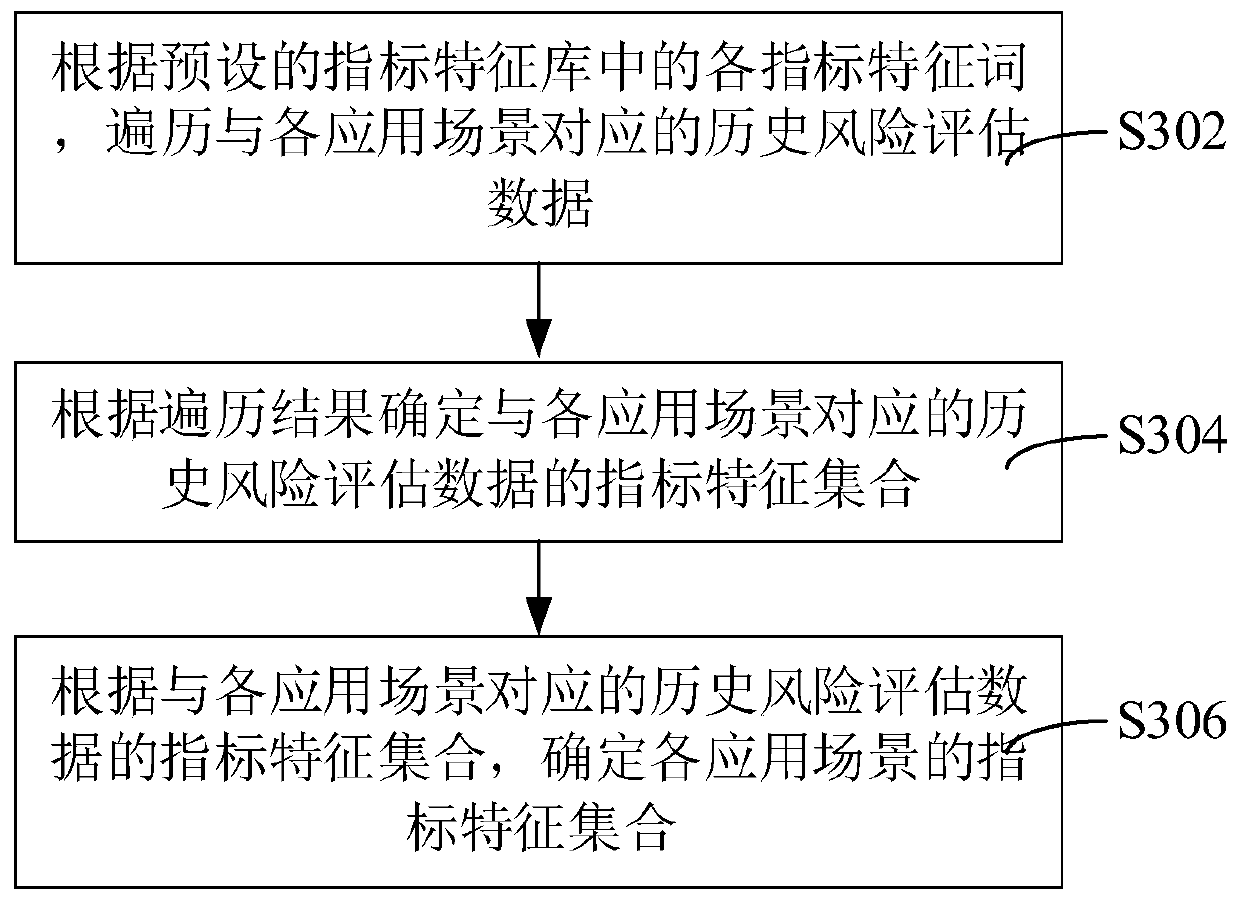
The invention relates to the technical field of data analysis, and provides a risk assessment system construction method and device, computer equipment and a storage medium. The method comprises the following steps of: obtaining an application scene set and a historical risk assessment data set; according to a risk assessment identifier carried by each piece of historical risk assessment data in the historical risk assessment data set and the application scene set, determining historical risk assessment data corresponding to each application scene, and performing index feature screening on thehistorical risk assessment data corresponding to each application scene; determining an index feature set of each application scene, constructing a scoring card model of each application scene according to the index feature set of each application scene and a preset scoring card model, and generating a risk assessment system according to the scoring card model of each application scene. By adopting the method, a risk assessment system which can be compatible with different application scenes to perform risk assessment on the user account can be constructed, and the risk assessment efficiencyis improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
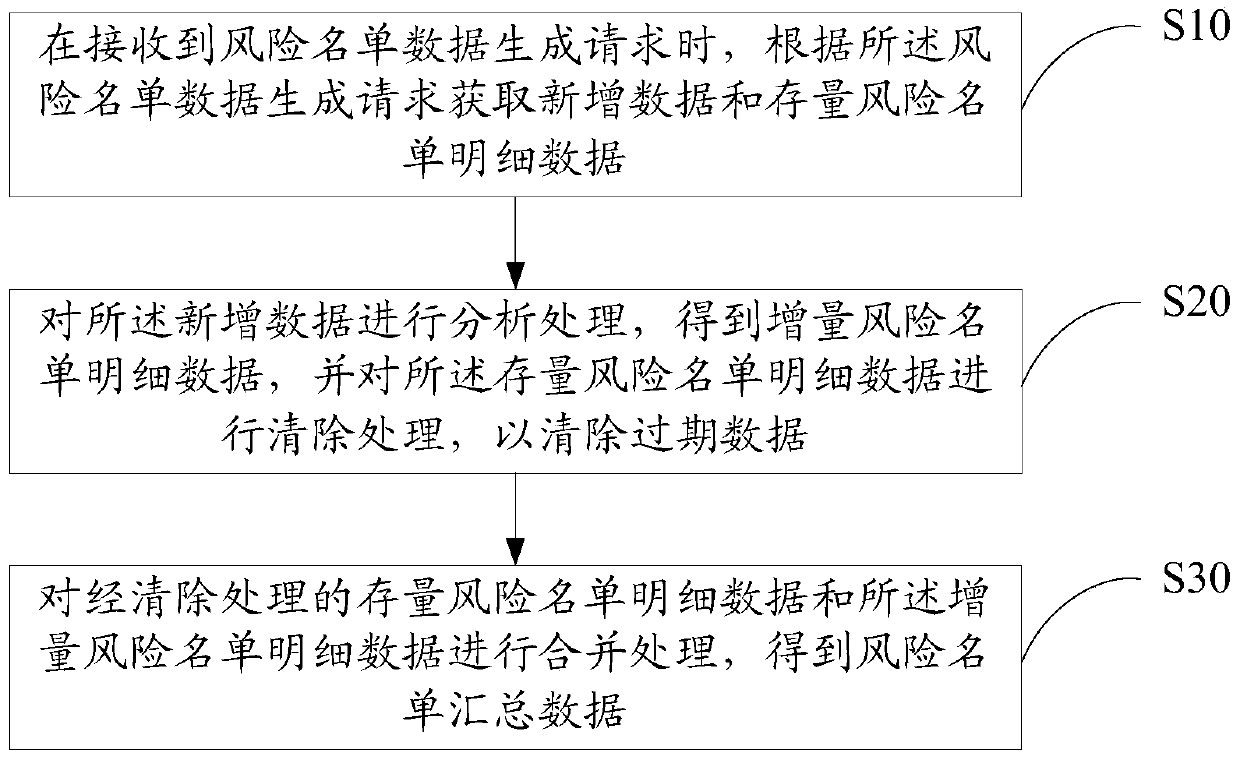
Risk list data generation method, device and equipment and computer storage medium
PendingCN110109905AConvenient queryImprove risk assessment efficiencyDatabase updatingFinanceSummary dataData science
The invention discloses a risk list data generation method. The risk list data generation method comprises: when a risk list data generation request is received, acquiring newly-added data and stock risk list detail data according to the risk list data generation request; analyzing and processing the newly added data to obtain incremental risk list detail data, and clearing the stock risk list detail data to clear out expired data; and performing merging processing on the cleared stock risk list detail data and the incremental risk list detail data to obtain risk list summary data. The invention also discloses a risk list data generation device, equipment and a computer storage medium. The risk list summary data can be intelligently generated, so that financial institutions such as banks can directly inquire credit risk data of enterprises or individuals based on the risk list summary data, and the risk assessment efficiency can be improved. In addition, the invention can also be combined with the block chain technology.
Owner:WEBANK (CHINA)
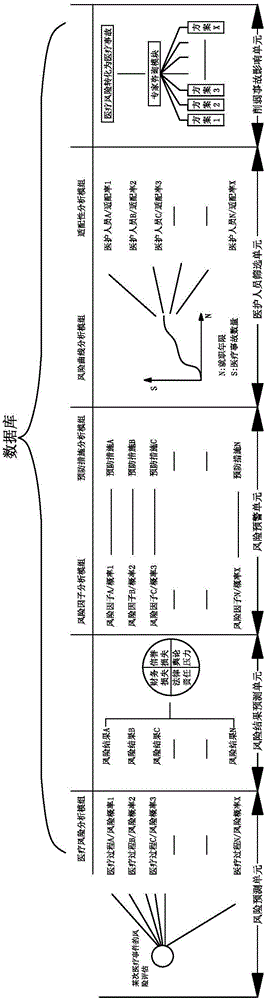
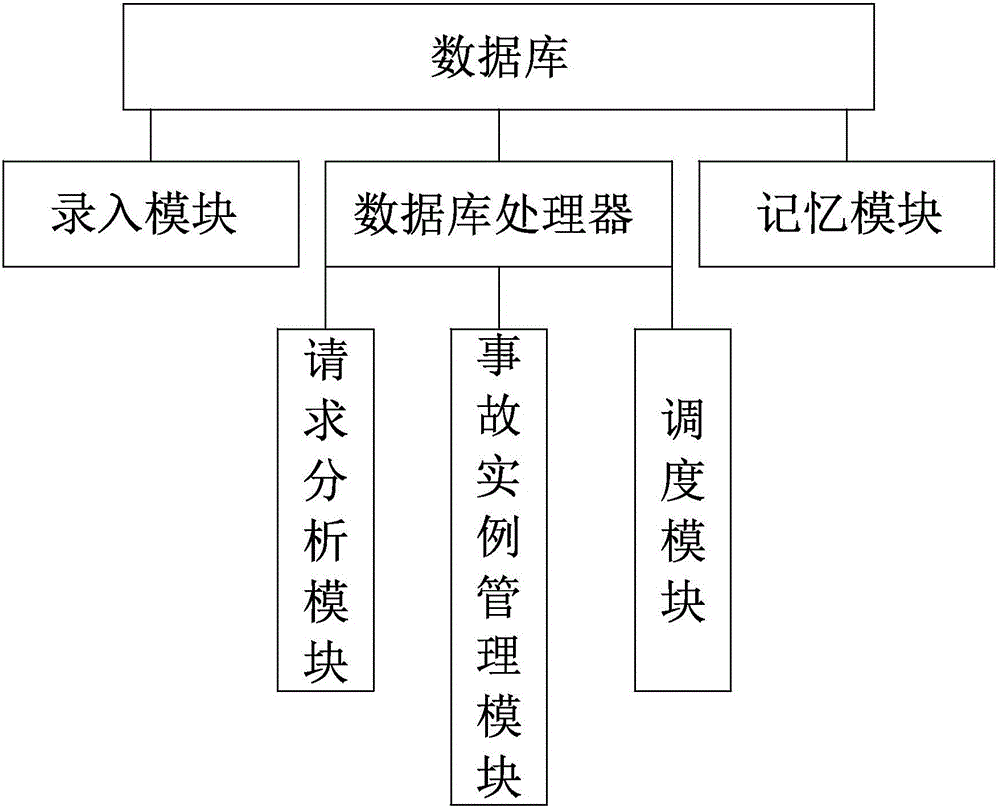
Hospital medical risk assessment system and method
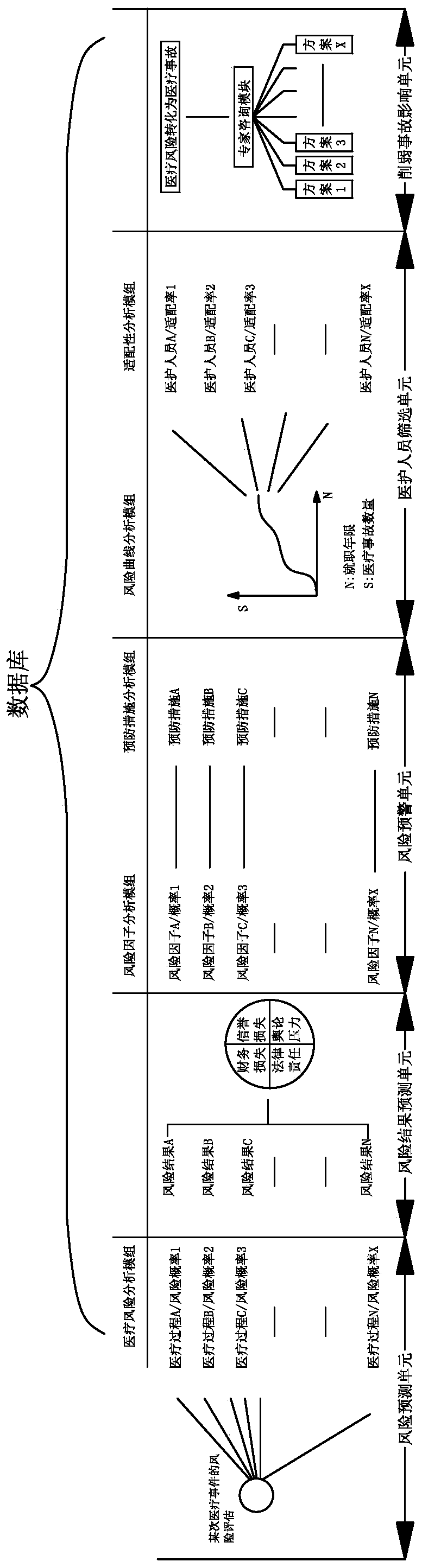
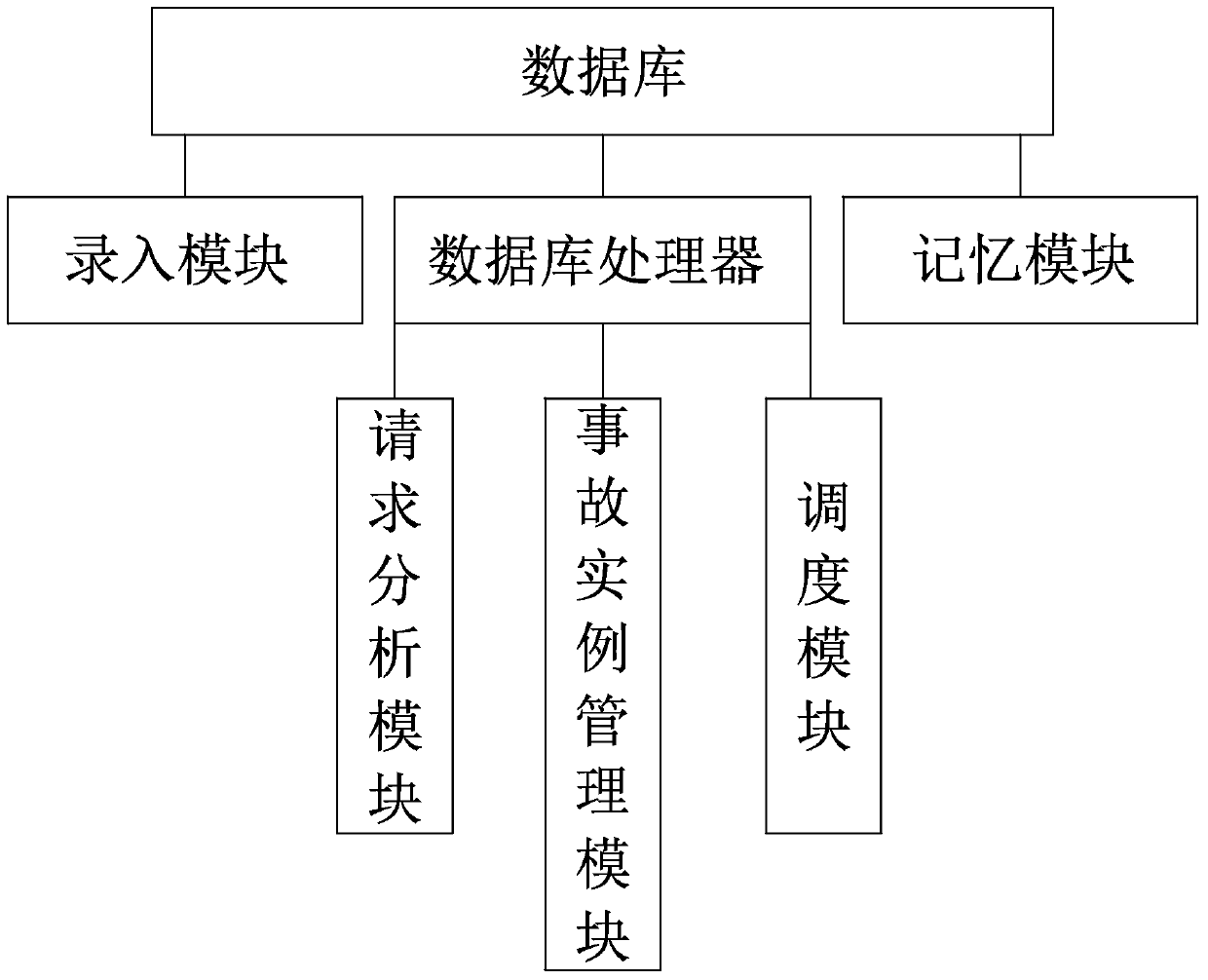
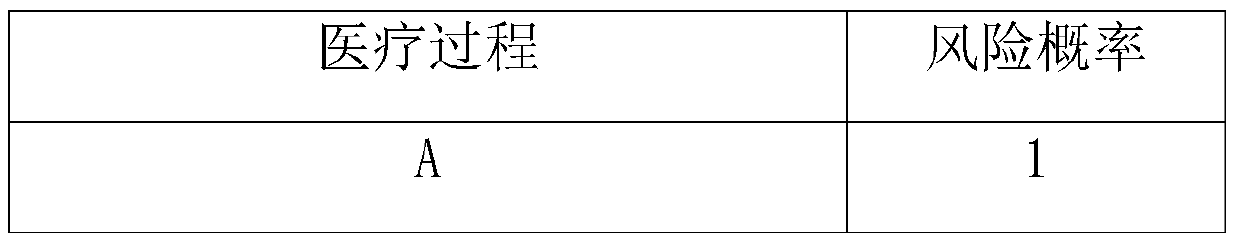
InactiveCN105740992AEasy to operateEvaluation takes less timeForecastingResourcesLong term monitoringEmergency medicine
The invention discloses a hospital medical risk assessment system. The hospital medical risk assessment system comprises a database and an assessment system, the database comprises a database processor, and the assessment system comprises a risk prediction unit, a risk result prediction unit, a risk early-warning unit, a medical care personnel screening unit and an accident influence weakening unit. The risk assessment system having a novel mode is constructed on the basis of the structure, the risk prediction unit, the risk result prediction unit, the risk early-warning unit, the medical care personnel screening unit and the accident influence weakening unit successively analyze a medical practice in the assessment process. Compared with the prior art, the risk assessment system has the advantages of convenient operation, a concise and reasonable operation standard, a concise and reasonable operation flow, short assessment-consumed time, the high response speed and obviously raised risk assessment efficiency. In the test process, long-term monitoring for hospital medical risks is achieved, the medical risks are substantially reduced, and the generation probability of medical accidents is reduced.
Owner:ZHEJIANG UNIV
Risk assessment method, apparatus, computer device and storage medium
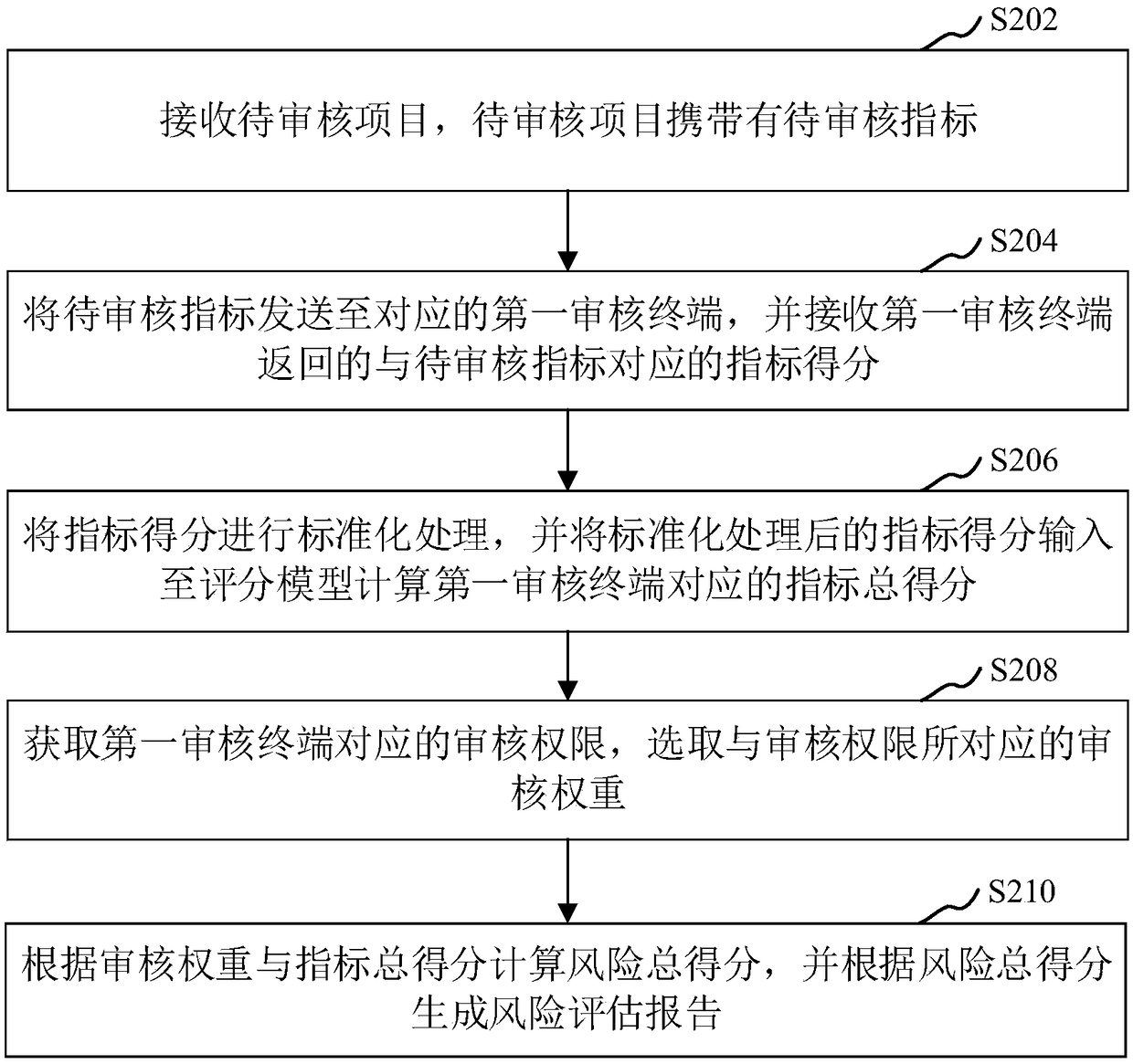
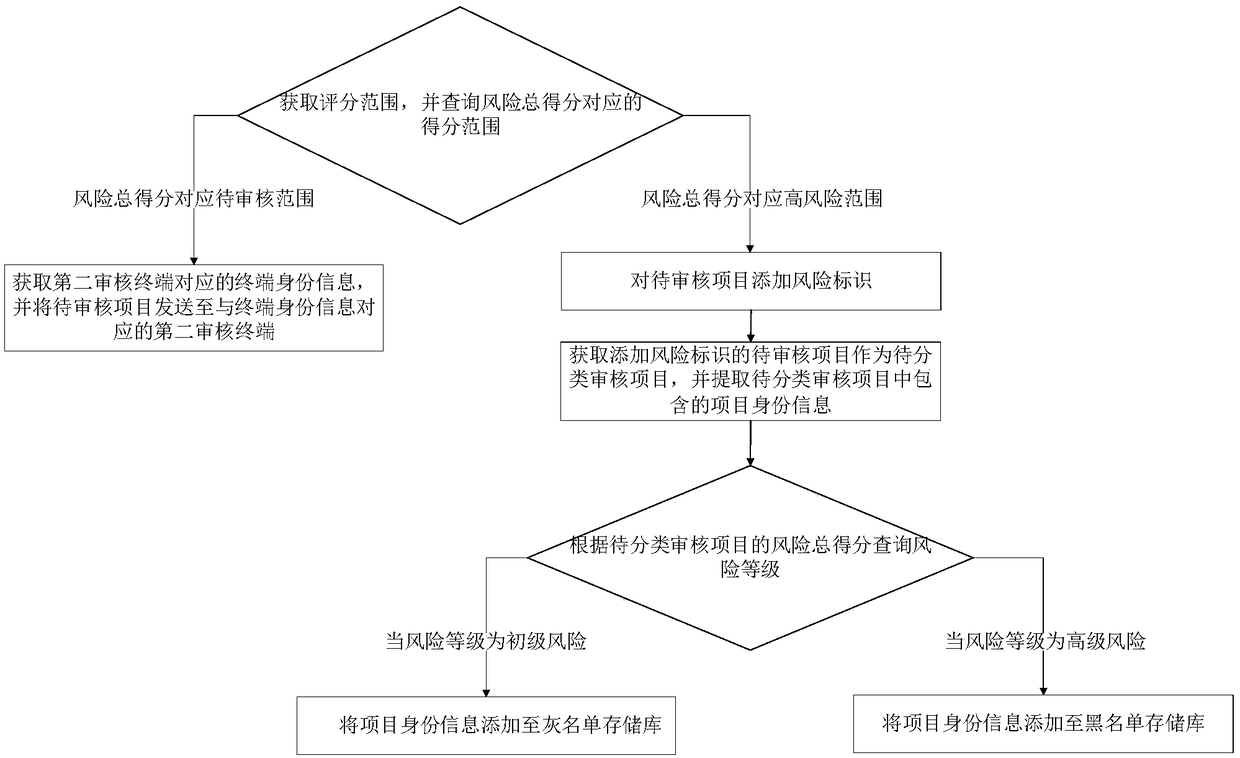
PendingCN109508903ARealize evaluationImprove risk assessment efficiencyBuying/selling/leasing transactionsResourcesTotal riskIndex score
The present application relates to data analysis in the field of big data, in particular to risk management in relational network analysis, i.e., a risk assessment method, apparatus, computer device and storage medium. The method comprises the following steps: receiving items to be audited, wherein the items to be audited carry indicators to be audited; Sending the index to be audited to the corresponding first auditing terminal, and receiving the index score corresponding to the index to be audited returned by the first auditing terminal; The index score is standardized, and the standardizedindex score is inputted to the scoring model to calculate the total index score corresponding to the first audit terminal; Acquiring audit rights corresponding to the first audit terminal, and selecting audit weights corresponding to the audit rights; The total risk score is calculated according to the audit weight and the total index score, and the risk assessment report is generated according tothe total risk score. The method can improve the efficiency of risk assessment.
Owner:PING AN INT FINANCIAL LEASING CO LTD
Data processing method and device, electronic equipment and storage medium
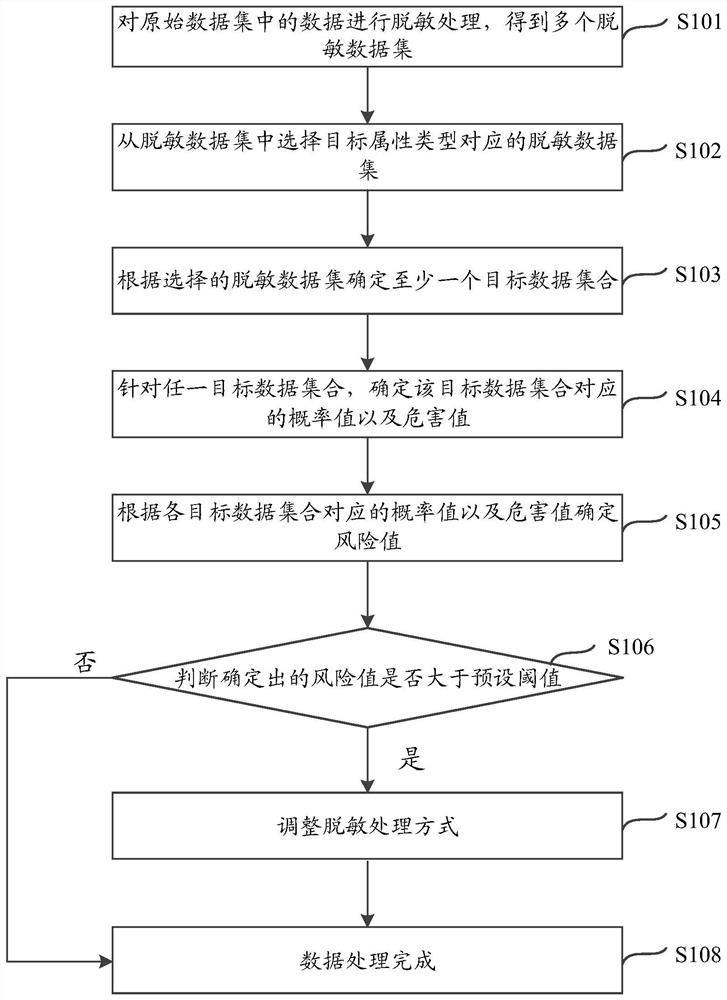
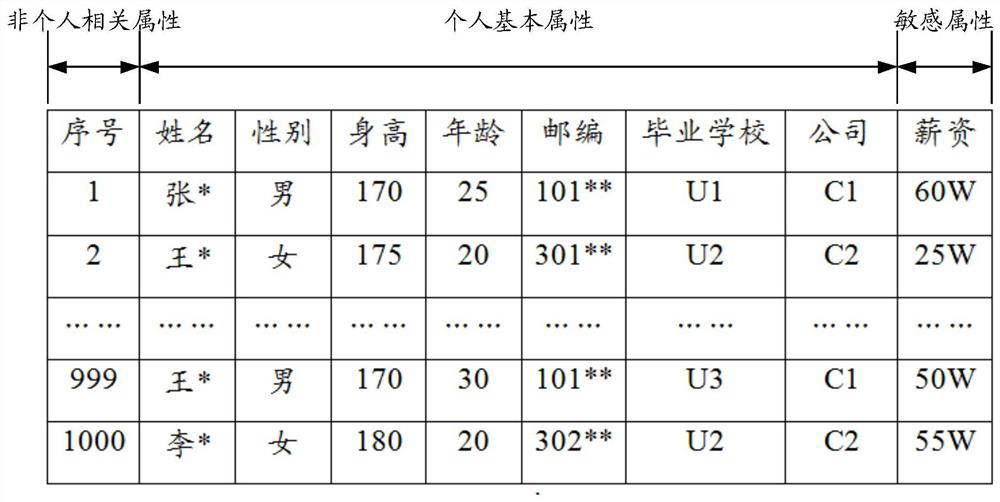
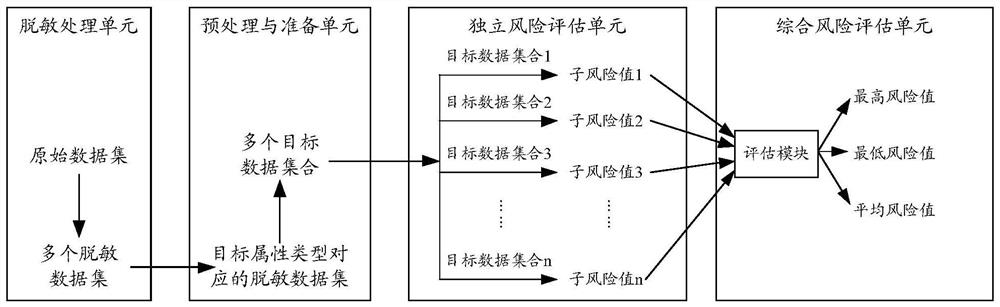
PendingCN111737750AReduce risk of leakageHigh or low risk of leakageDigital data protectionPlatform integrity maintainanceData setOriginal data
The invention discloses a data processing method and device, electronic equipment and a storage medium, which are used for automatically carrying out risk assessment on desensitized data and improvingthe risk assessment efficiency. According to the embodiment of the invention, the method comprises steps of carrying out desensitization processing on data in an original data set to obtain a plurality of desensitized data sets; selecting a desensitized data set corresponding to the target attribute type from the desensitized data set, and determining at least one target data set; and determininga risk value according to the probability value and the hazard value corresponding to each target data set, and if the risk value is greater than a preset threshold, adjusting a desensitization processing mode. According to the embodiment of the invention, risk assessment is carried out from the two aspects of the possibility that the desensitized data is utilized and the harm caused by successfully restoring the business data by utilizing the desensitized data, and the risk value is automatically determined and the data leakage risk is quantitatively determined; and a desensitization processing mode is adjusted according to the determined risk value, so that the data leakage risk is reduced.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
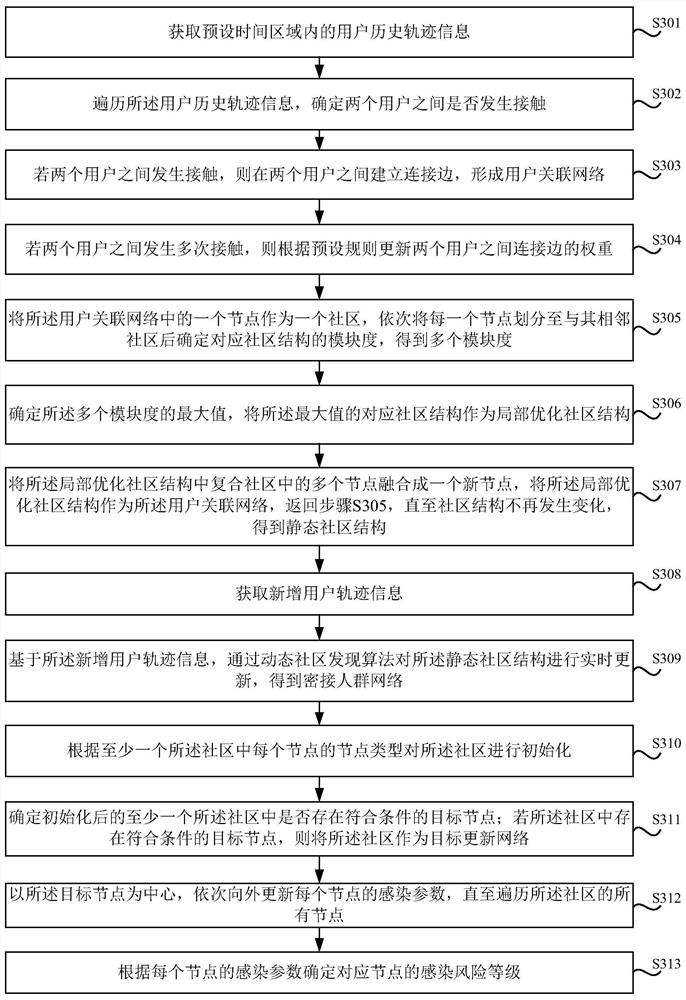
Close contact person infection risk assessment method and device, electronic equipment and storage medium
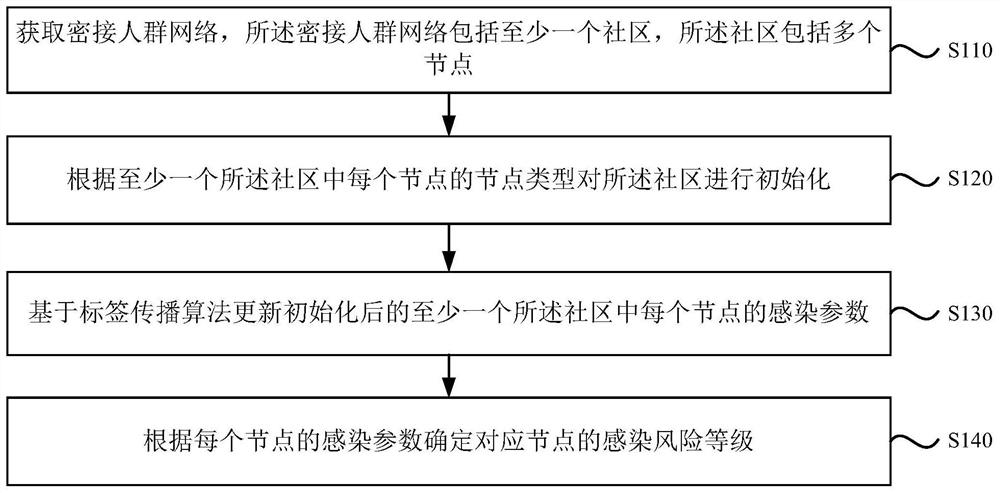
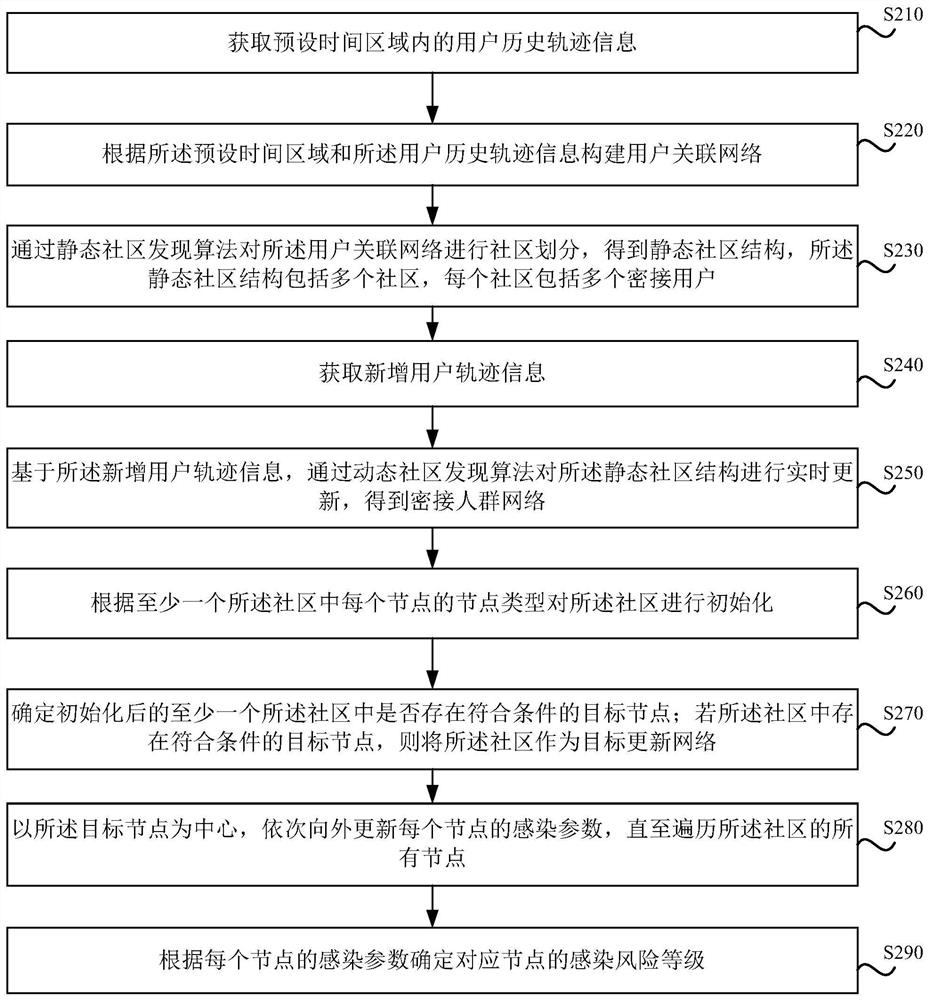
ActiveCN113161006ATake convenienceRapid determination of infection riskEpidemiological alert systemsICT adaptationInfection riskCommunity setting
The embodiment of the invention discloses a close contact person infection risk assessment method and device, electronic equipment and a storage medium, and the method comprises the steps: obtaining a close contact person network which comprises at least one community, wherein the community comprises a plurality of nodes; initializing the community according to the node type of each node in the at least one community; updating infection parameters of each node in the at least one initialized community based on a label propagation algorithm; and determining the infection risk level of the corresponding node according to the infection parameter of each node. According to the embodiment of the invention, the infection risk of the close contact person is rapidly determined, and the risk assessment efficiency is improved; and the infection risk can be quantified so that the infection risk of the close connection personnel can be more intuitively expressed, and the adoption of epidemic situation protection measures is more facilitated.
Owner:SOUTH UNIVERSITY OF SCIENCE AND TECHNOLOGY OF CHINA
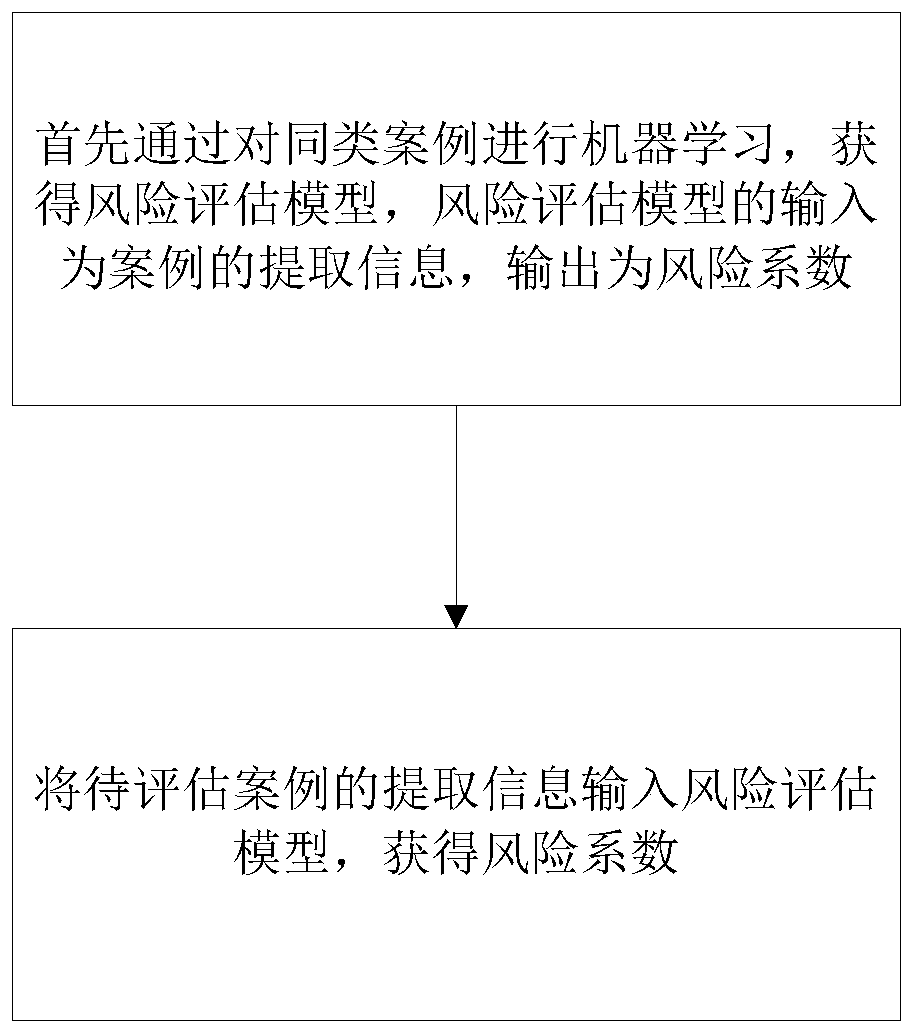
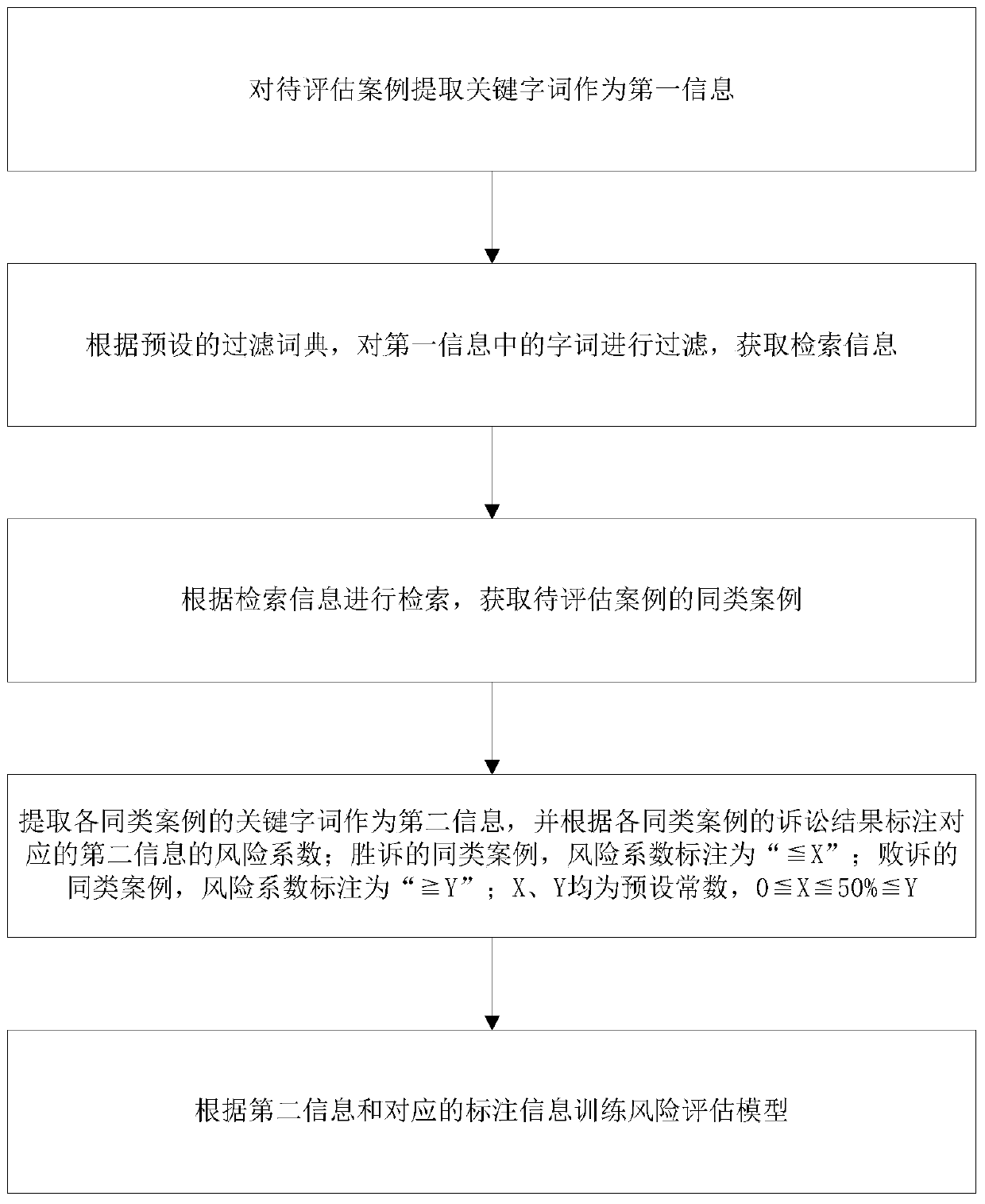
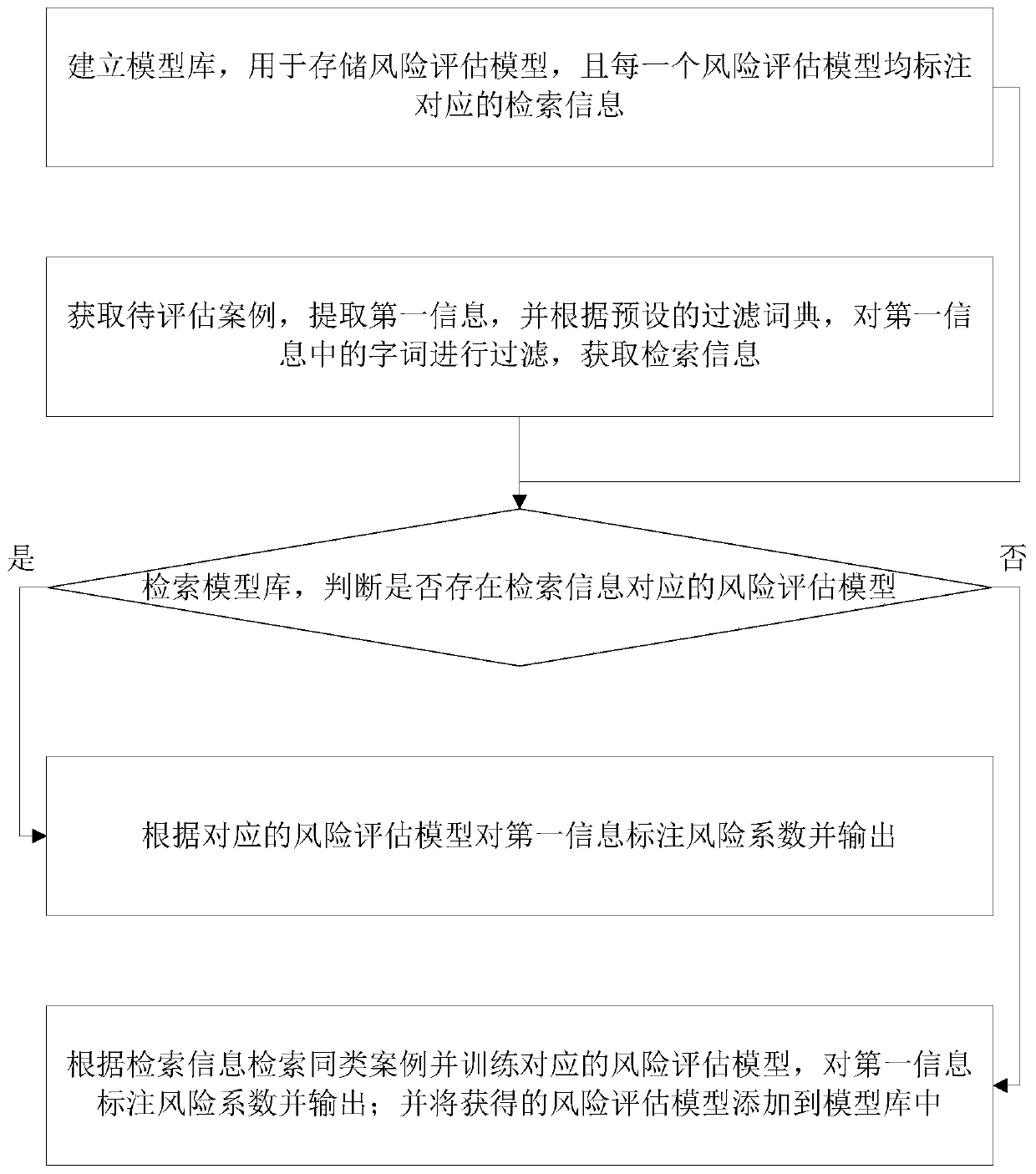
Risk intelligent assessment method
InactiveCN111222765ARealize intelligenceReal-timeDigital data information retrievalMachine learningEngineeringArtificial intelligence
The invention provides an intelligent risk assessment method, which comprises the following steps that: firstly, through carrying out machine learning on similar cases, obtaining a risk assessment model, the input of the risk assessment model being the extraction information of the cases, and the output being a risk coefficient; and inputting the extraction information of the to-be-assessed case into the risk assessment model to obtain a risk coefficient. According to the intelligent risk assessment method provided by the invention, the case extraction information is labeled through the risk assessment model to obtain the risk coefficient, so that the intelligence and real-time performance of risk assessment are realized. And meanwhile, the risk assessment model is obtained by performing machine learning on similar cases of the to-be-assessed case, so that the domain tendency and specificity of the risk assessment model for the to-be-assessed case are ensured, and the accuracy and effectiveness of model assessment are improved.
Owner:合肥长远知识产权管理有限公司
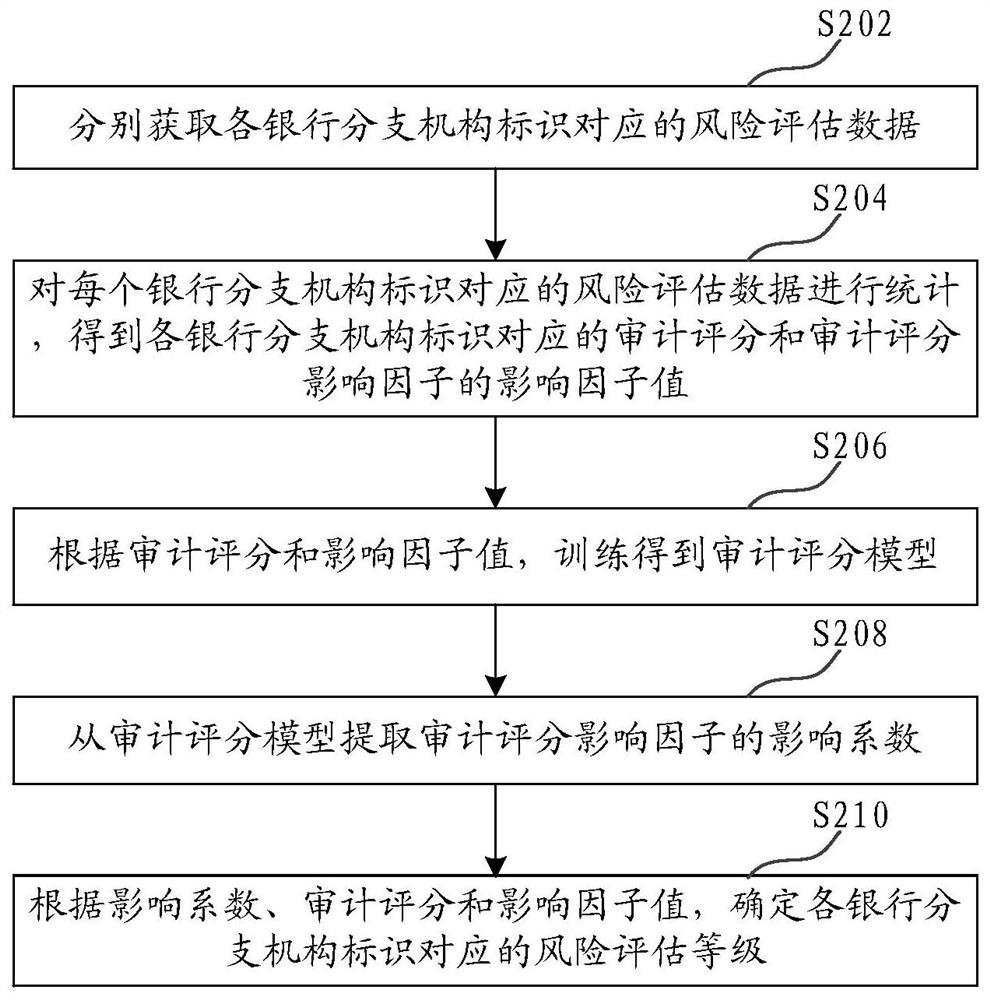
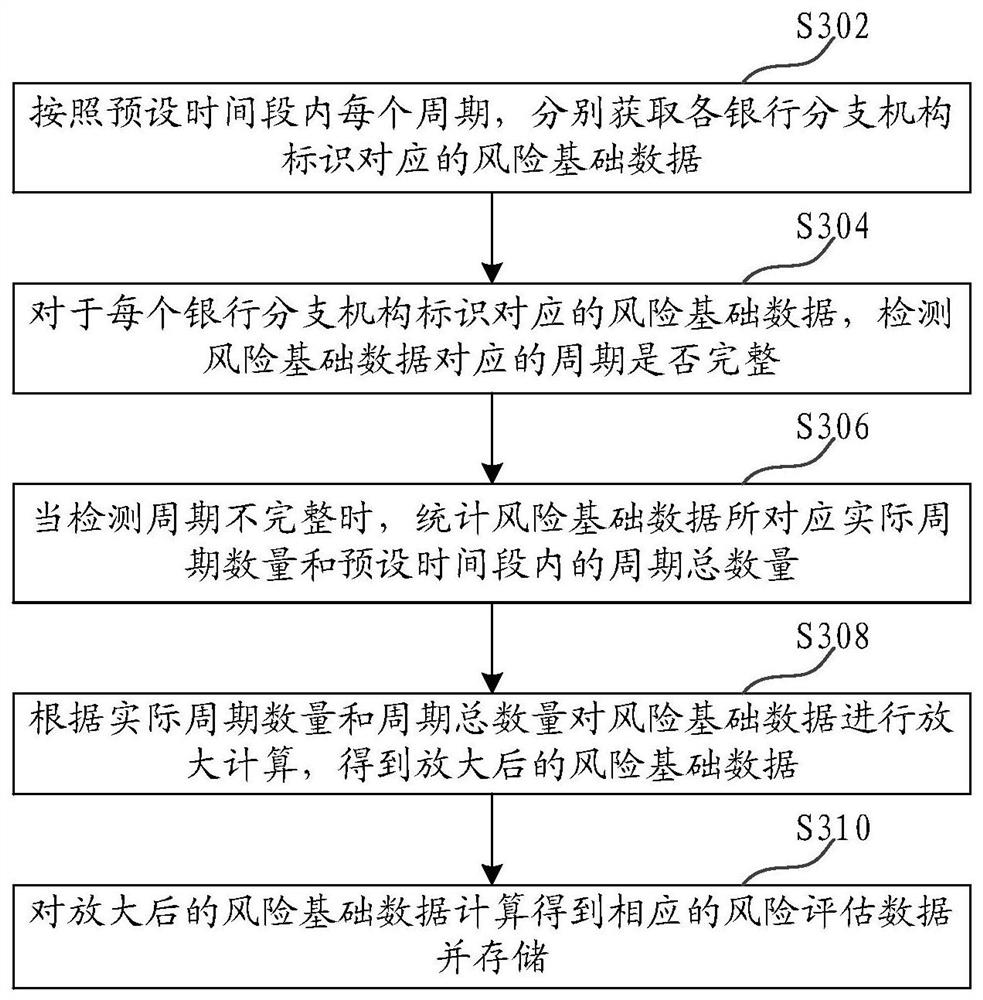
Bank risk data processing method and device, computer equipment and storage medium
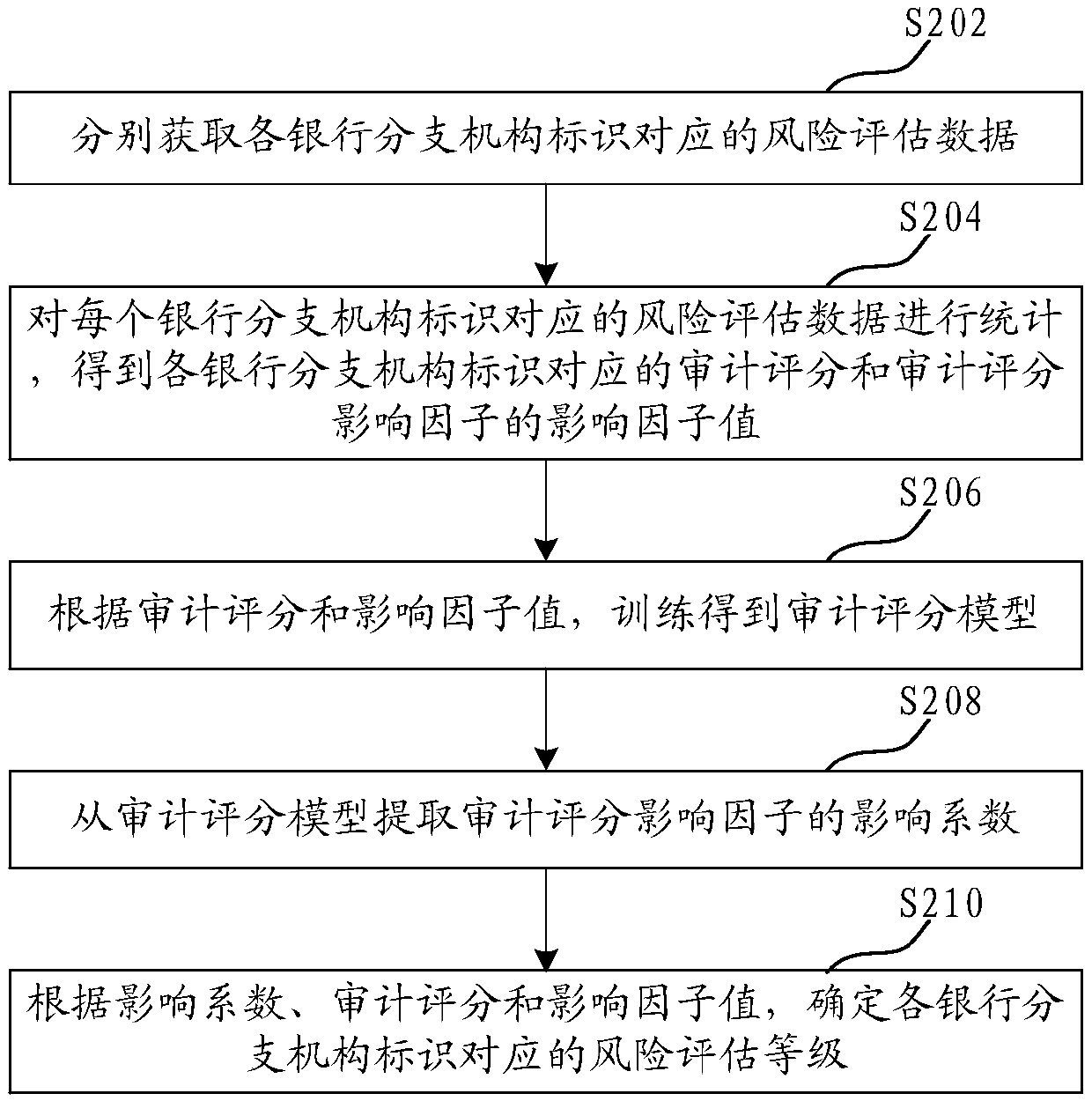
ActiveCN107862599AImprove risk assessment efficiencyImprove accuracyFinanceResourcesComputer scienceRisk assessment
The invention relates to a bank risk data processing method and device, computer equipment and a storage medium. The method comprises the following steps that: independently obtaining risk assessmentdata corresponding to each bank branch mechanism; carrying out statistics on the risk assessment data corresponding to each bank branch mechanism to obtain an auditing score corresponding to the log of each bank branch mechanism and the impact factor value of an auditing score impact factor; according to the auditing score and the impact factor value, training to obtain an auditing score model; from the auditing score model, extracting the impact factor of the auditing score impact factor; and according to the impact coefficient, the auditing score and the impact factor value, determining a risk evaluation level corresponding to the logo of each bank branch mechanism. Through the training of the auditing score model, the impact coefficient of the auditing score impact factor is determined,the accuracy of the determined impact coefficient is improved, and furthermore, bank risk assessment accuracy is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Information processing, method, device and equipment, storage medium and program product
PendingCN113283982ASave on risk assessment costsImprove risk assessment efficiencyFinanceSystems engineeringRisk assessment
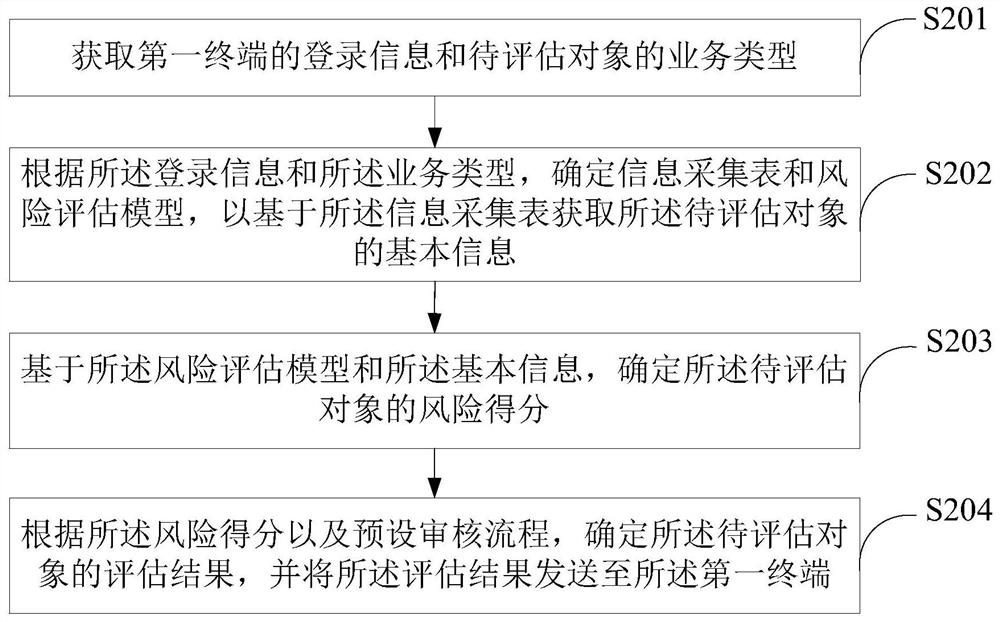
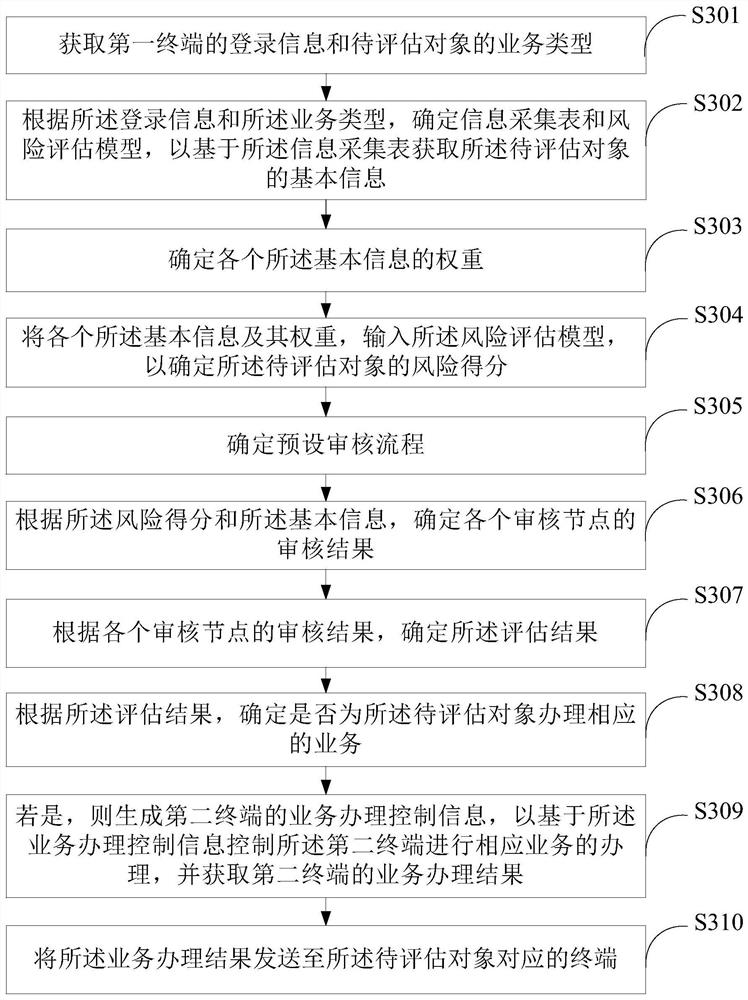
The embodiment of the invention provides an information processing method, device and equipment, a storage medium and a program product. The information processing method comprises the following steps: acquiring login information of a first terminal and a service type of a to-be-evaluated object; determining an information acquisition table and a risk assessment model according to the login information and the service type, so as to obtain basic information of the to-be-assessed object based on the information acquisition table; based on the risk assessment model and the basic information, determining a risk score of the to-be-assessed object; and determining an assessment result of the to-be-assessed object according to the risk score and a preset auditing process, and sending the assessment result to the first terminal, thereby realizing high-customization customer risk assessment. The information processing method, device and equipmentare suitable for customer risk assessment of different regions and different banks, and are high in assessment adaptability and high in efficiency.
Owner:AGRICULTURAL BANK OF CHINA
Method, device and terminal equipment for detecting risk of Alzheimer's disease
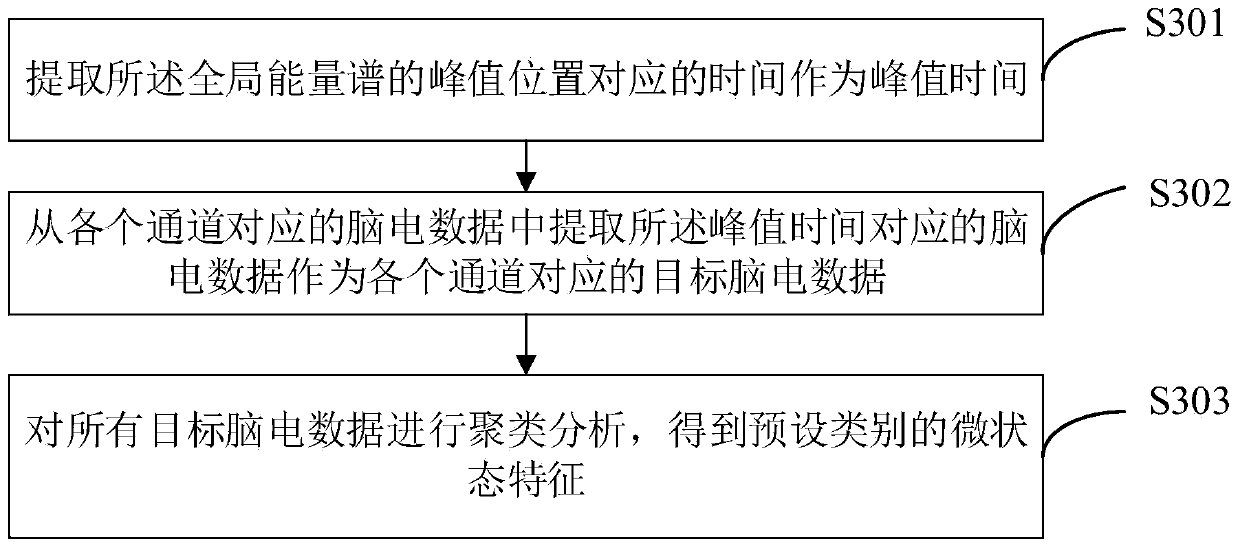
ActiveCN111407231AThe output is accurateImprove risk assessment efficiencyDiagnostic recording/measuringSensorsTopology informationTerminal equipment
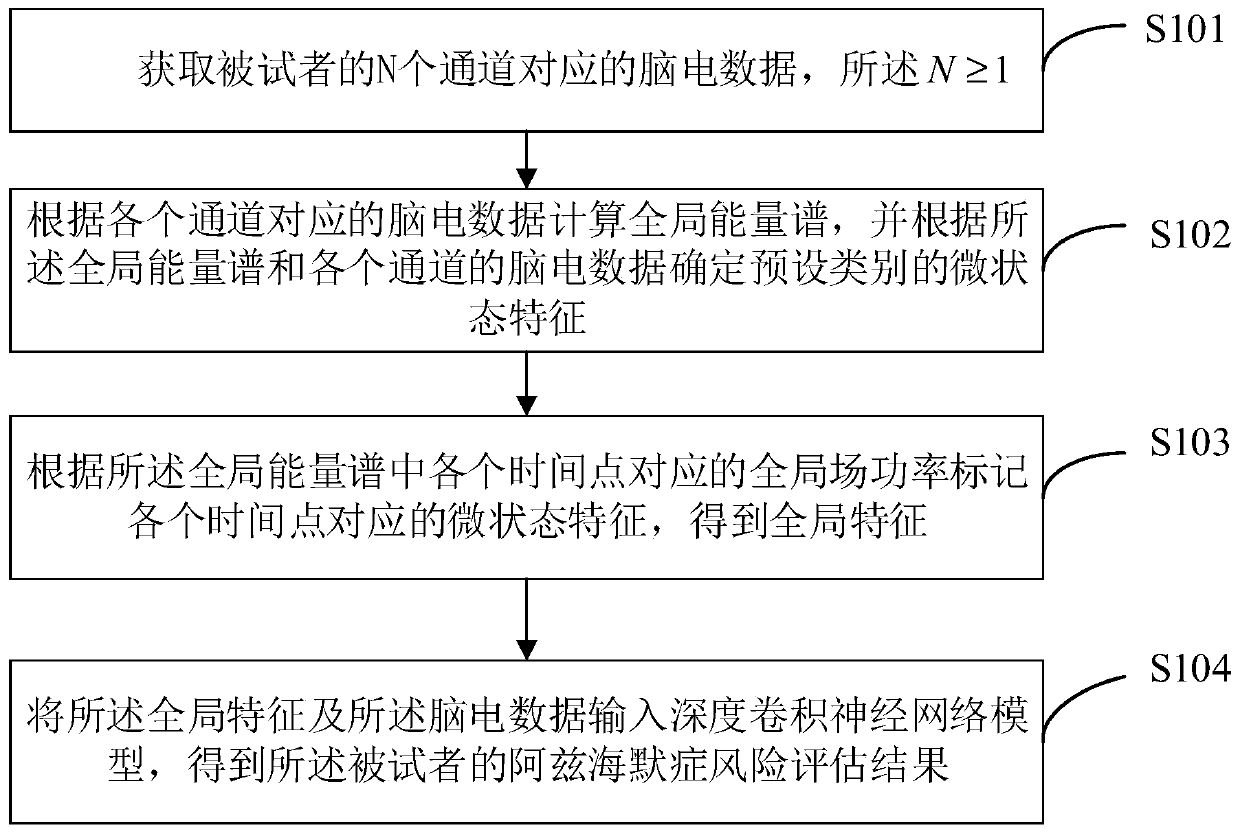
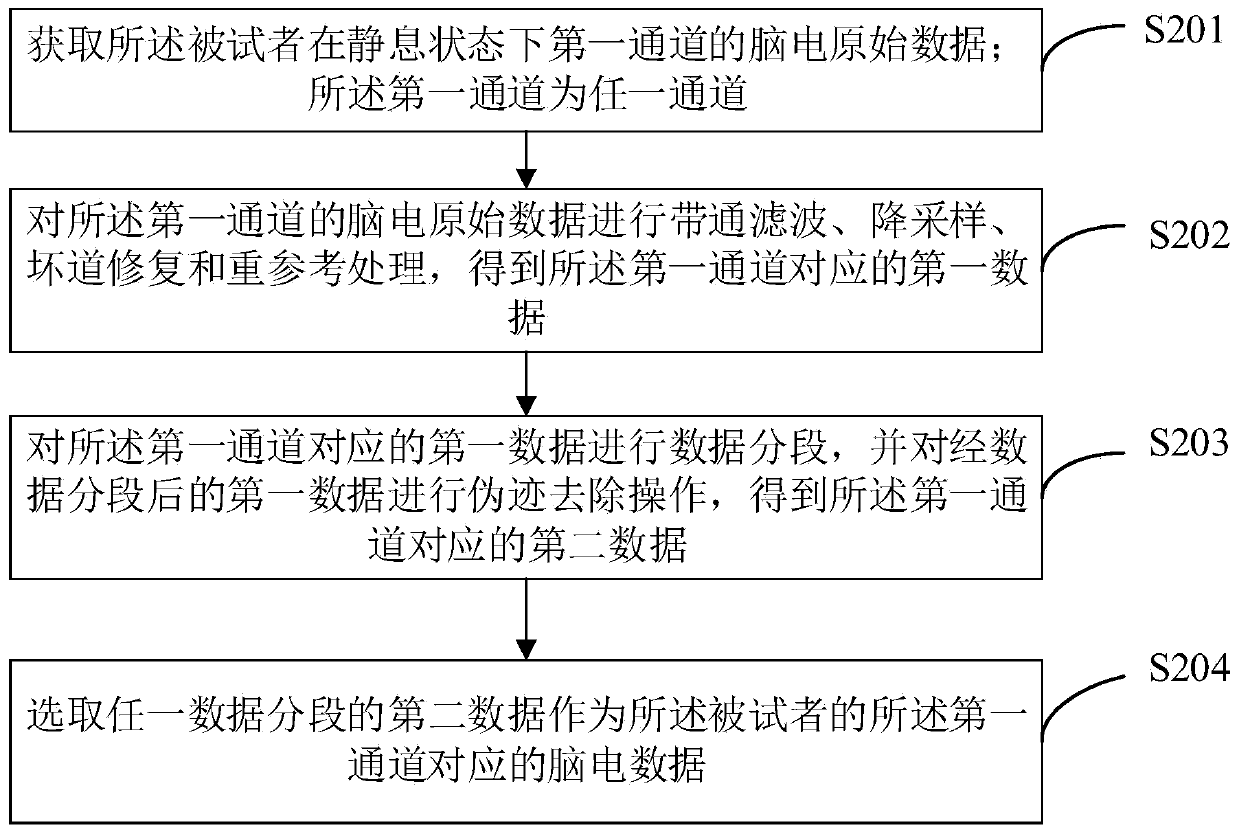
The invention is applicable to the technical field of computers, and provides a method, a device and terminal equipment for detecting risk of Alzheimer's disease (AD). The method includes: acquiring electroencephalogram data corresponding to N channels of a subject; calculating a global energy spectrum according to the electroencephalogram data corresponding to each channel, and determining microstate characteristics of a preset category according to the global energy spectrum and the electroencephalogram data of each channel; marking the micro-state feature corresponding to each time point according to global field power corresponding to each time point in the global energy spectrum to obtain a global feature; and inputting the global characteristics and the electroencephalogram data intoa deep convolution neural network model to obtain an Alzheimer's disease risk evaluation result of the subject. The method, device and terminal equipment comprehensively consider the voltage amplitude change information of the electroencephalogram data and the spatial topology information of the global feature, can make the output result of the deep convolutional neural network model more accurate, can not only improve efficiency of Alzheimer's disease risk assessment, but also improve accuracy of the Alzheimer's disease risk assessment result.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
Regional power grid environment risk assessment method
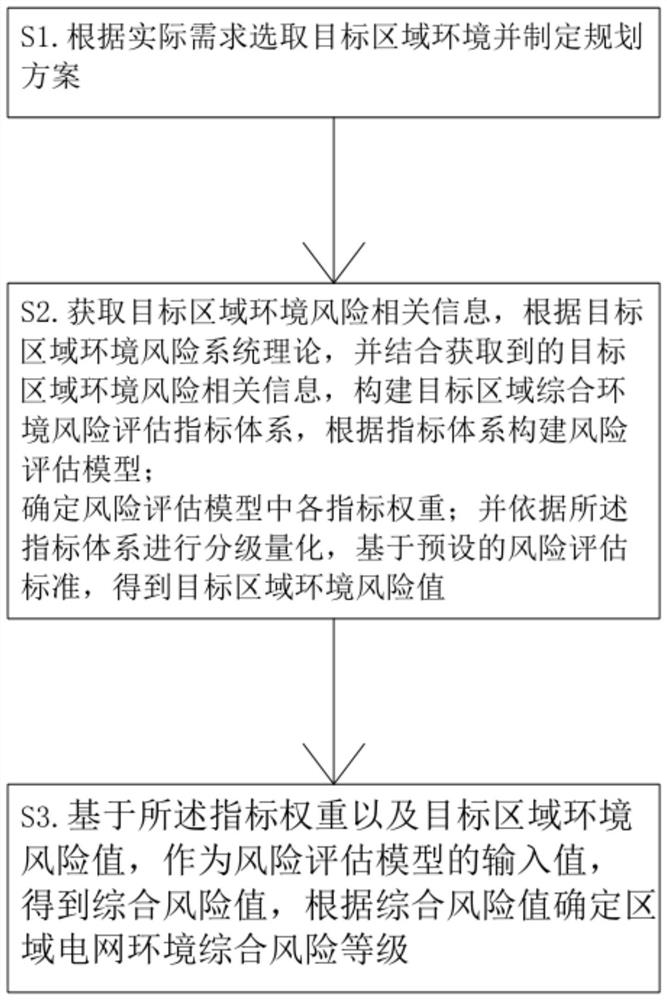
PendingCN114065127AOptimize site selectionOptimize line selectionResourcesSystems intergating technologiesEnvironmental resource managementPower grid
The invention discloses a regional power grid environment risk assessment method, and relates to the technical field of power grid planning, and the method comprises the following steps: selecting a target regional environment according to an actual demand, and making a planning scheme; obtaining environment risk related information of the target area, constructing a comprehensive environment risk assessment index system of the target area, and constructing a risk assessment model according to the index system; determining the weight of each index in the risk assessment model; and carrying out grading quantification according to the indicator system to obtain an environment risk value of the target area. According to the regional power grid environment comprehensive risk assessment method, on the basis of the environment data, the power grid planning environment influence key factors are identified, the corresponding risk levels are assessed, the power grid planning environmental impact evaluation and the power transmission and transformation project are effectively combined, the planned substation site selection and line selection can be optimized, the environmental risk can be fully identified and avoided, and the environmental dispute and emergencies can be prevented and reduced.
Owner:STATE GRID LIAONING ELECTRIC POWER RES INST +2
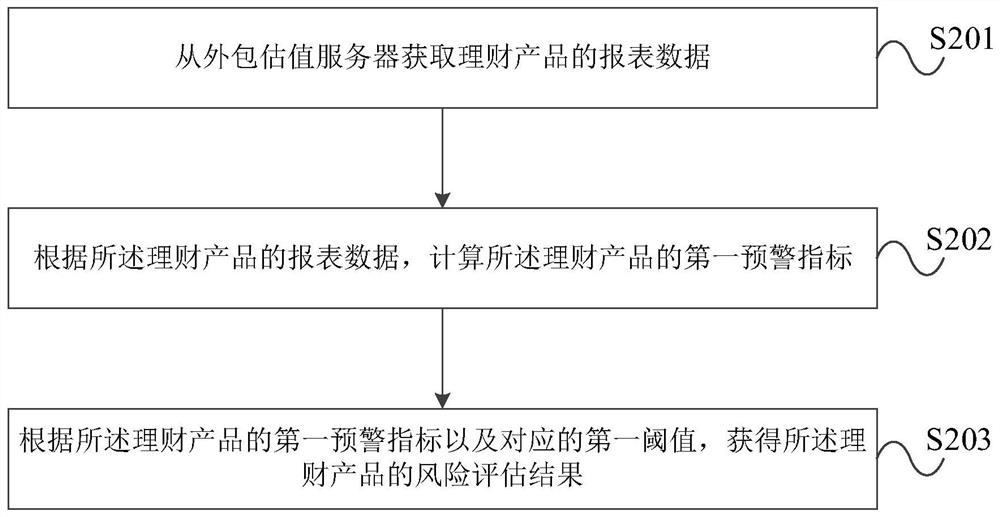
Bank financial product data processing method and device
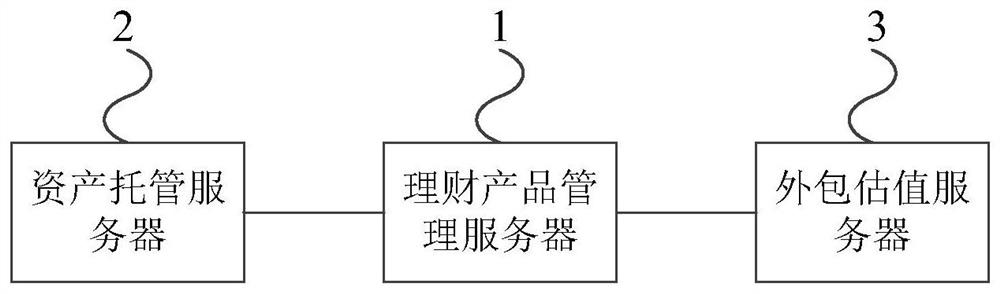
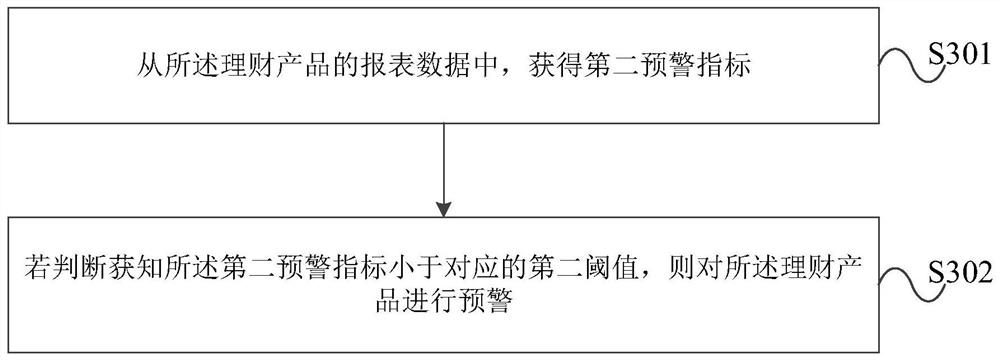
PendingCN111798322AImprove risk assessment efficiencyFinanceOperations researchIndustrial engineering
The invention provides a bank financial product data processing method and a device. The method comprises the steps of obtaining report data of a financial product from an outsourcing valuation server; calculating a first early warning index of the financial product according to the report data of the financial product; and obtaining a risk assessment result of the financial product according to the first early warning index of the financial product and the corresponding first threshold. The device is used for executing the method. According to the bank financial product data processing methodand the device provided by the embodiment of the invention, the risk assessment efficiency of the financial product is improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
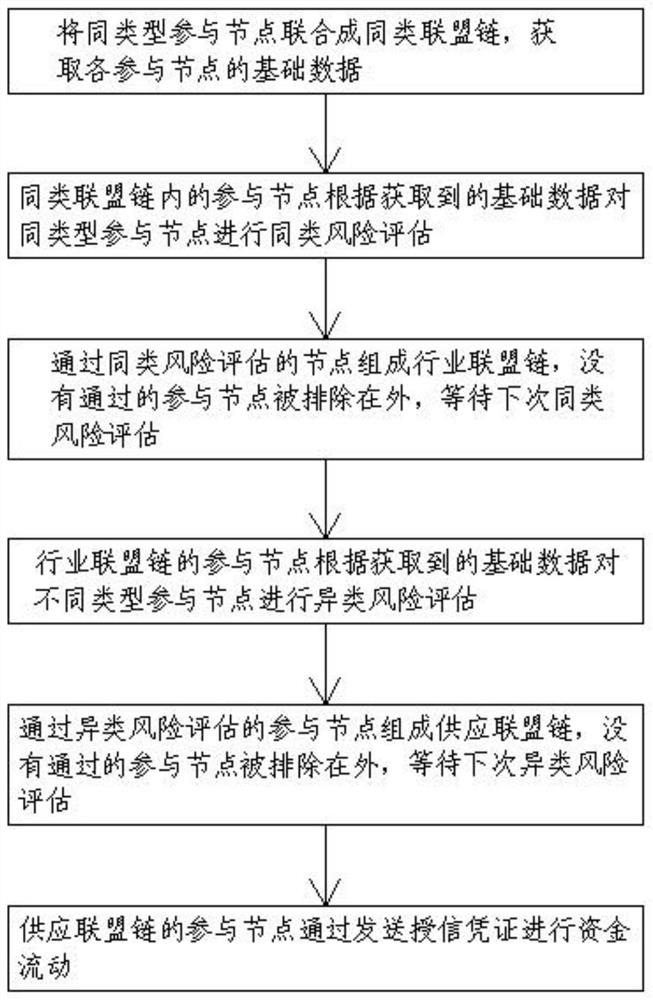
Supply chain financial risk assessment method based on block chain
InactiveCN111861212ASpeed up the processImprove risk assessment efficiencyFinanceResourcesComputer scienceOperations research
The invention relates to supply chain financial risk assessment, specifically relates to a supply chain financial risk assessment method based on a block chain. The participation nodes of the same type are combined into a similar alliance chain; basic data of each participation node is obtained; the participation nodes in the similar alliance chain perform similar risk assessment on the participation nodes of the same type according to the acquired basic data; an industry alliance chain is formed by nodes of the same kind of risk assessment; the participating nodes which do not pass through are excluded to wait for next similar risk assessment, heterogeneous risk assessment is carried out on different types of participation nodes by the participation nodes of the industry alliance chain according to the obtained basic data, a supply alliance chain is formed by the participation nodes passing the heterogeneous risk assessment, the participation nodes which do not pass the supply alliance chain are excluded to wait for next heterogeneous risk assessment; the technical scheme provided by the invention can effectively overcome the defects that in the prior art, the cross-industry riskassessment efficiency is relatively low, and small and medium-sized enterprises are difficult to quickly and effectively obtain financing.
Owner:安徽高山科技有限公司
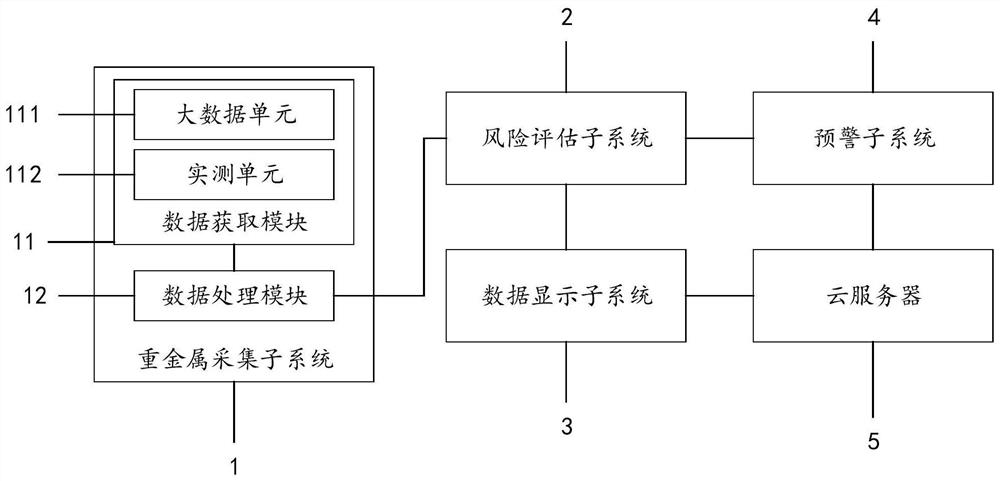
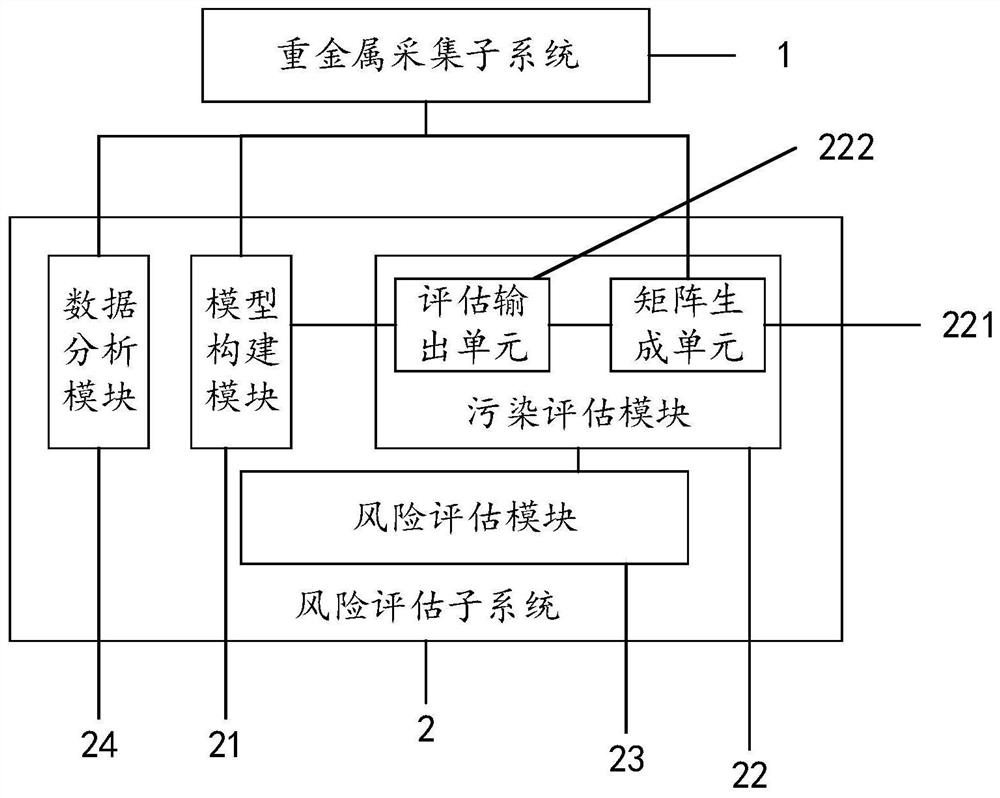
Heavy metal pollution risk assessment system
PendingCN112907096AImprove risk assessment efficiencyResourcesRisk levelEnvironmental resource management
The invention discloses a heavy metal pollution risk assessment system, which comprises the following steps: firstly, acquiring historical pollution data of a research target under a set duration and a plurality of corresponding pollution data at a current acquisition moment through a heavy metal acquisition subsystem, and acquiring corresponding input data and output data; then, constructing a pollution risk assessment model based on the historical pollution data, constructing a plurality of matrixes with weights according to the plurality of pollution data, and obtaining a plurality of corresponding assessment levels with weights through the pollution risk assessment model; calculating a corresponding risk level in combination with the input data and the output data, displaying and storing the corresponding data, and performing corresponding early warning according to the risk level, so that the system can be suitable for heavy metal risk assessment under multiple research targets, and can improve the risk assessment efficiency in combination with historical data and the corresponding input and output data .
Owner:江苏维诗环境科技有限公司
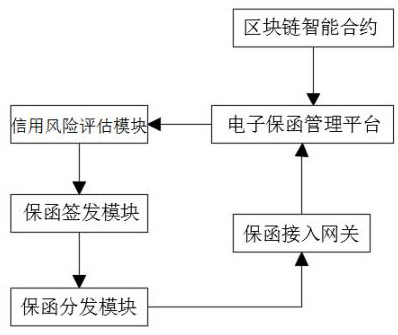
Electronic warrant full-process management and risk management and control system based on block chain
ActiveCN114155093AReduce processingShorten approval timeFinanceProtocol authorisationAccess networkControl system
The invention, which relates to the technical field of the electronic warranty, discloses a blockchain-based electronic warranty full-process management and risk management and control system comprising a blockchain smart contract, an electronic warranty management platform and a credit risk assessment module. A user sends an insurance request to the electronic warranty management platform through the block chain smart contract, and the electronic warranty management platform calls a credit risk assessment module to verify a corresponding user identity after receiving the insurance request, and judges whether the insurance request is within a credit risk security level; then, the request passing the credit risk assessment is returned to the warranty issuing module, and the warranty issuing module is used for analyzing the received insurance request and checking and replying the insurance request in sequence according to the risk coefficient; and the warranty distribution module is used for encrypting the electronic warranty through the warranty access gateway and then distributing the encrypted electronic warranty to a storage address specified by the electronic warranty management platform through a specified transmission mode, so that the electronic warranty is effectively prevented from being tampered, and the data security is improved.
Owner:一方函互联网有限公司
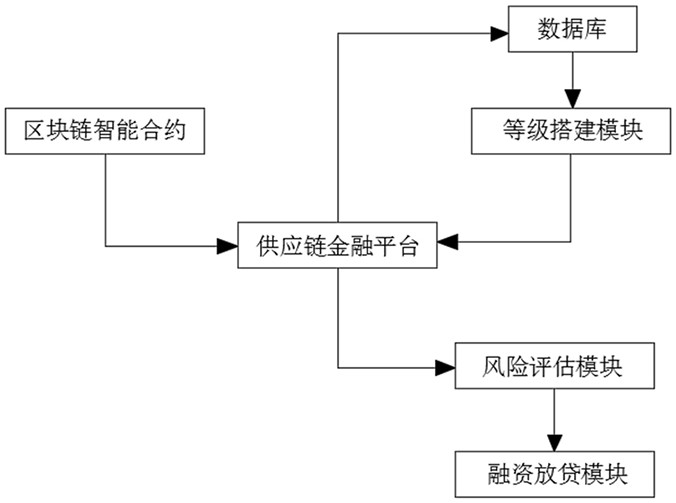
Engineering field supply chain financial risk assessment system based on block chain
InactiveCN114066616AReduce processingShorten approval timeFinanceOffice automationOperations researchIndustrial engineering
The invention discloses an engineering field supply chain financial risk assessment system based on a block chain, relates to the technical field of financial risk assessment, and solves the problem that the financing loan reply time is too long due to the fact that information is dispersed and not integrated and loan risks are difficult to control. The system comprises a supply chain financial platform, a risk assessment module and a financing and lending module. The user sends a financing request to the supply chain financial platform through the block chain smart contract, and the supply chain financial platform verifies the identity of the corresponding user after receiving the financing request and judges whether the financing request is legal; if the financing request is legal, the risk assessment module is used for performing risk coefficient assessment according to the content of the financing request in combination with a customer level model to obtain a processing sequence table of the financing request; and the financing and lending module is used for auditing and replying the financing request according to the sequence position fed back by the risk assessment module, so that the lending risk is effectively controlled, the replying time of the financing request is shortened, the working efficiency is improved, and the asset circulation rate is maximized.
Owner:湖南和信安华区块链科技有限公司
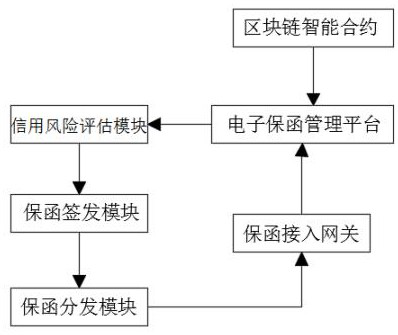
The whole process management and risk control system of electronic letter of guarantee based on blockchain
ActiveCN114155093BReduce processingShorten approval timeFinanceProtocol authorisationAccess networkControl system
The invention discloses a block chain-based electronic letter of guarantee full-process management and risk control system, which relates to the technical field of electronic letters of guarantee, including block chain smart contracts, electronic letter of guarantee management platforms and credit risk assessment modules; The electronic letter of guarantee management platform sends an insurance application request. After receiving the insurance application request, the electronic letter of guarantee management platform calls the credit risk assessment module to verify the identity of the corresponding user, and judges whether the insurance application request is within the credit risk safety level; then returns the request that passes the credit risk assessment. To the letter of guarantee issuance module, the letter of guarantee issuance module is used to analyze the insurance application received, and to review and approve the insurance application request in turn according to the risk factor; the letter of guarantee distribution module is used to encrypt the electronic letter of guarantee through the letter of guarantee access gateway and pass the specified The transmission method is distributed to the storage address specified by the electronic letter of guarantee management platform, which can effectively prevent the electronic letter of guarantee from being tampered with and improve data security.
Owner:一方函互联网有限公司
Bank risk data processing method, device, computer equipment and storage medium
ActiveCN107862599BImprove risk assessment efficiencyImprove accuracyFinanceResourcesBranch officeData mining
Disclosed is a bank risk data processing method, comprising: respectively acquiring risk assessment data corresponding to each bank branch mechanism identifier; creating statistics on the risk assessment data corresponding to each bank branch mechanism identifier so as to obtain an audit score and an influence factor value of an audit score influence factor corresponding to each bank branch mechanism identifier; according to the audit score and the influence factor value, training to obtain an audit score model; extracting an influence coefficient of the audit score influence factor from the audit score model; and according to the influence coefficient, the audit score and the influence factor value, determining a risk assessment level corresponding to each bank branch mechanism identifier.
Owner:PING AN TECH (SHENZHEN) CO LTD
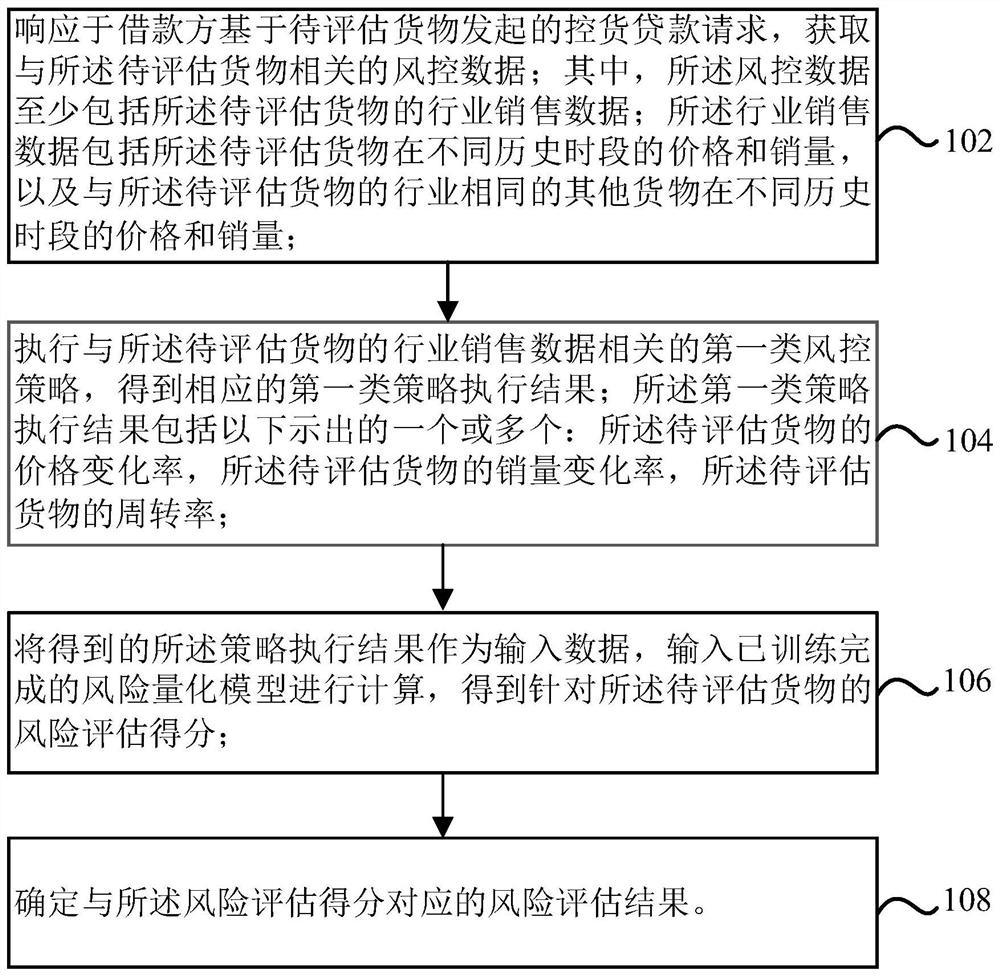
Risk assessment method and device for controlling cargo loan
PendingCN114298818AImprove risk assessment efficiencyAccurate assessmentFinanceRisk ControlRisk quantification
The invention provides a risk assessment method and device for controlling cargo loan, and the method comprises the steps: obtaining risk control data related to a to-be-assessed cargo in response to a cargo control loan request initiated by a borrower based on the to-be-assessed cargo; wherein the risk control data at least comprises industry sales data of the to-be-evaluated goods; the industry sales data comprises prices and sales volumes of the to-be-evaluated goods in different historical periods, and prices and sales volumes of other goods having the same industry as the to-be-evaluated goods in different historical periods; executing a first-class risk control strategy related to the industry sales data of the to-be-evaluated goods to obtain a corresponding first-class strategy execution result; taking the obtained strategy execution result as input data, inputting the input data into a trained risk quantification model for calculation, and obtaining a risk assessment score for the to-be-assessed cargo; and determining a risk assessment result corresponding to the risk assessment score.
Owner:普洛斯科技(重庆)有限公司
A hospital medical risk assessment system and method
InactiveCN105740992BEasy to operateEvaluation takes less timeHealthcare managementForecastingEmergency medicineLong term monitoring
Owner:ZHEJIANG UNIV
Risk assessment model training, risk assessment method and device
ActiveCN111401914BLow costReduce overheadCharacter and pattern recognitionProtocol authorisationTotal riskFeature coding
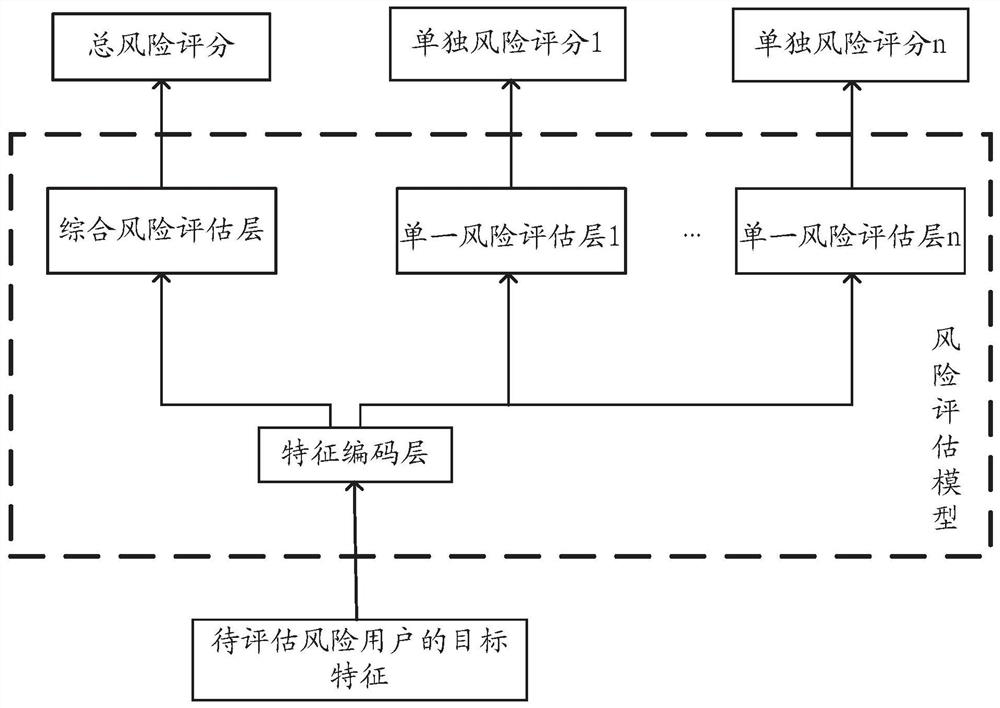
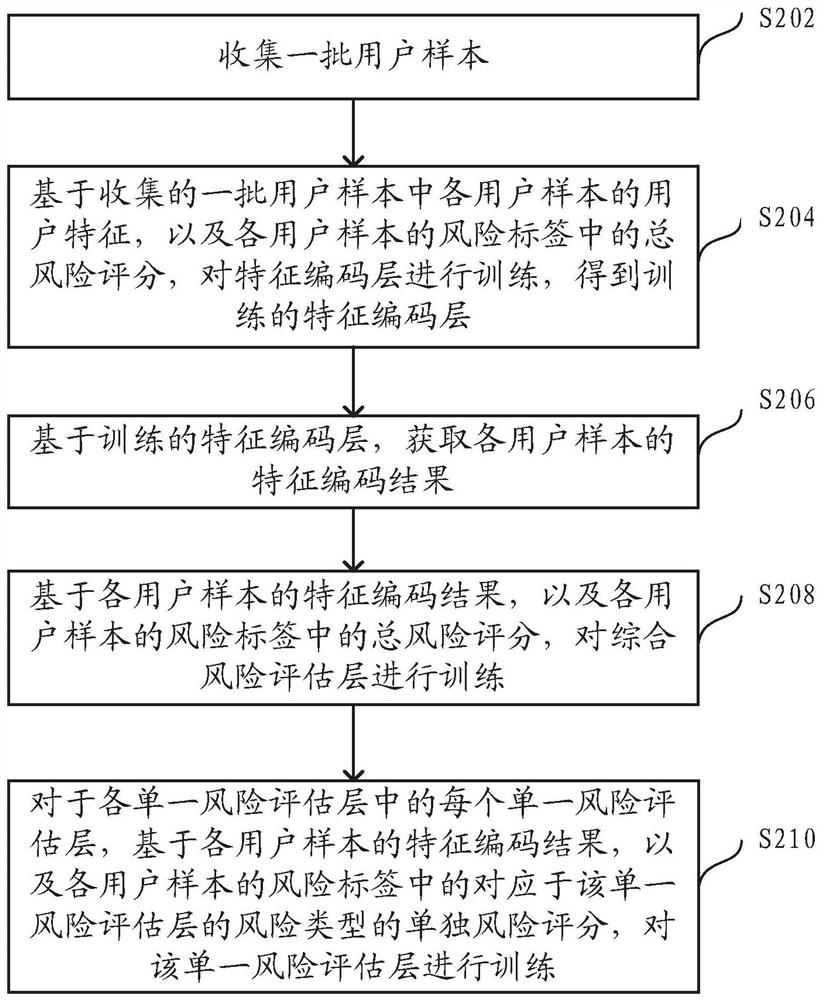
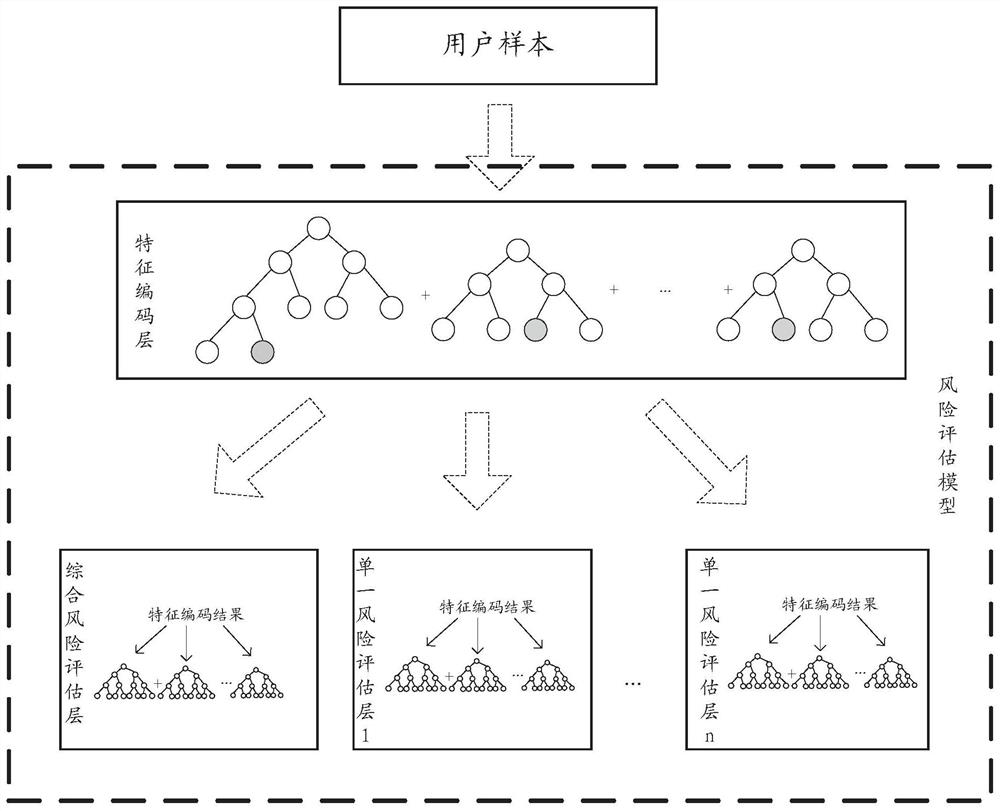
The embodiments of this specification provide a training of a risk assessment model, a risk assessment method, and an apparatus. In the training method, a batch of user samples are collected, and each user sample includes user characteristics and a risk label, and the risk label is used to indicate the user , as well as multiple individual risk scores for each predetermined risk type. Based on the user characteristics of each user sample and the total risk score in the risk label, the feature coding layer is trained to obtain a trained feature coding layer, and based on the trained feature coding layer, the feature coding result of each user sample is obtained. Based on the feature encoding results of each user sample and the total risk score in the risk label, the comprehensive risk assessment layer is trained. For each single risk assessment layer in each single risk assessment layer, the single risk assessment layer is trained based on the feature coding result of each user sample and the individual risk score of the corresponding risk type in the risk label.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Method and device for risk assessment of access behavior
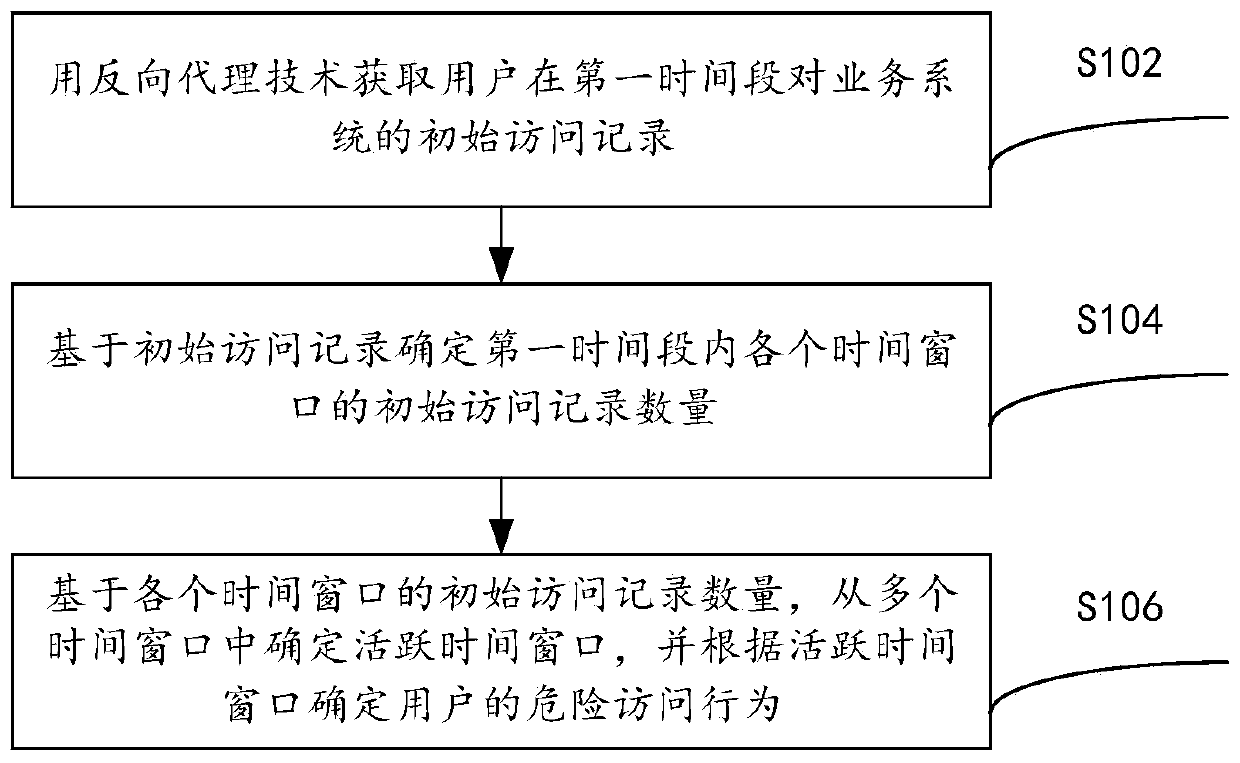
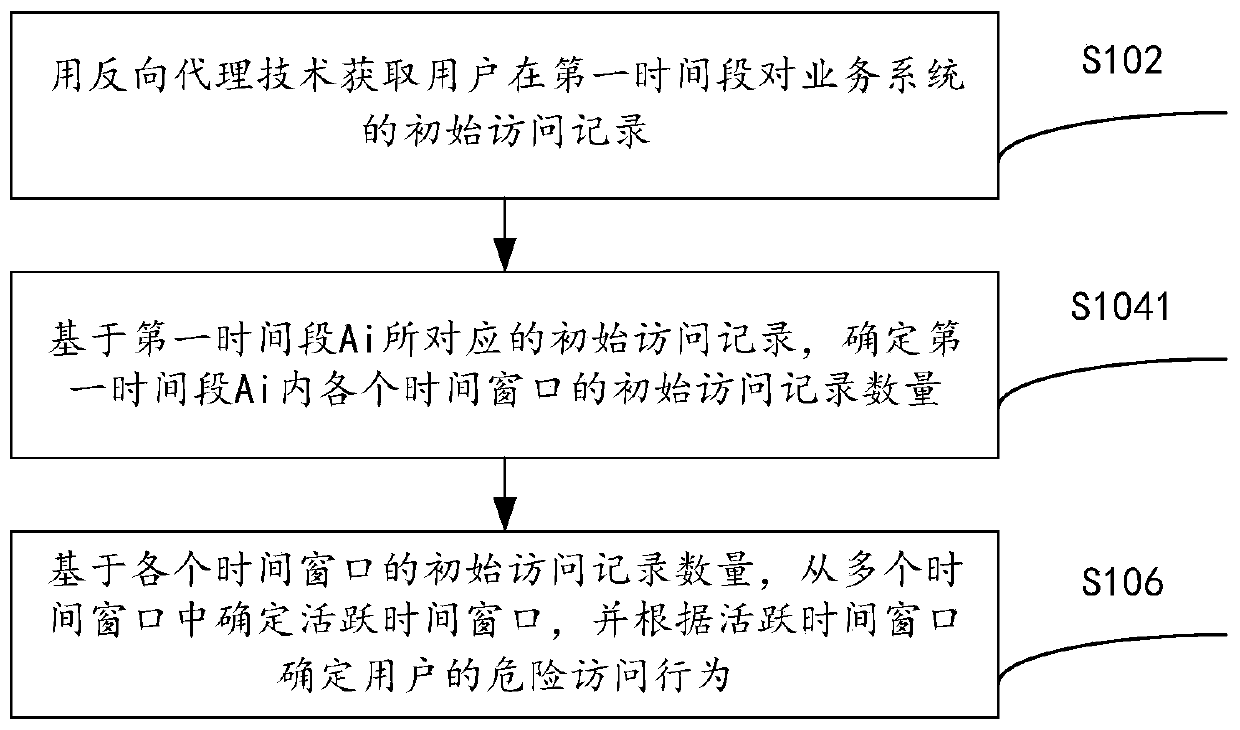
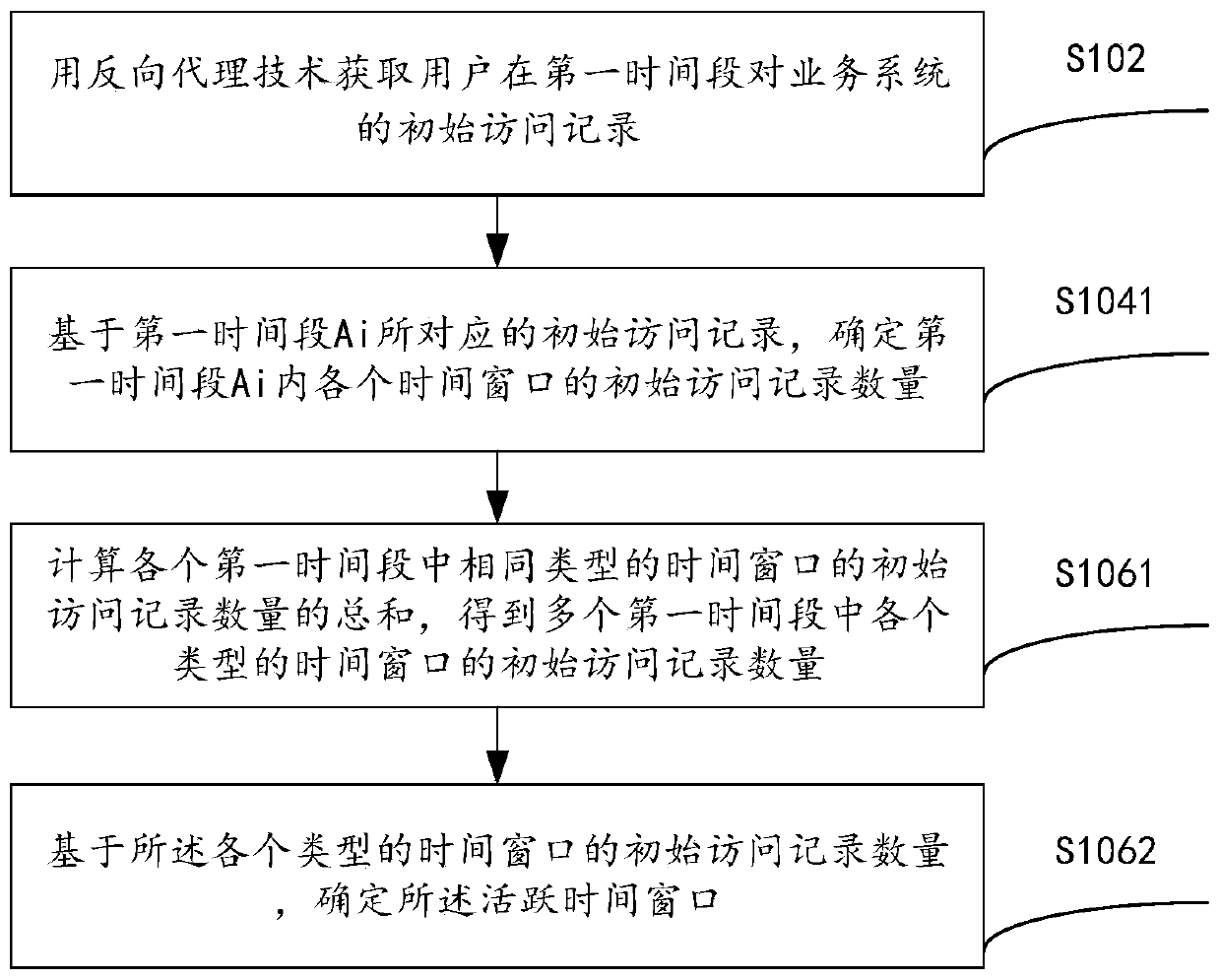
ActiveCN109543404BImprove risk assessment efficiencyImprove the efficiency of access risk assessmentPlatform integrity maintainanceActive timeReverse proxy
The present invention provides a risk assessment method and apparatus for access behavior, and relates to a technical field of information security, comprising: acquiring an initial access record of auser to a service system in a first time period by using a reverse proxy technology, wherein the first time period comprises a plurality of time windows, and the initial access record comprises an access time of the user to the service system; Determining an initial number of access records for each time window in the first time period based on the initial access records; Based on the initial number of access records for each time window, determining the active time windows from multiple time windows, and determining dangerous access behaviors of users according to the active time windows, which solves the problem that in the existing risk assessment methods of access behaviors, the steps of acquiring access time are tedious, and the risk assessment efficiency of access behaviors is low.
Owner:BEIJING TRUSFORT TECH CO LTD
Automated enterprise environmental risk assessment method and device
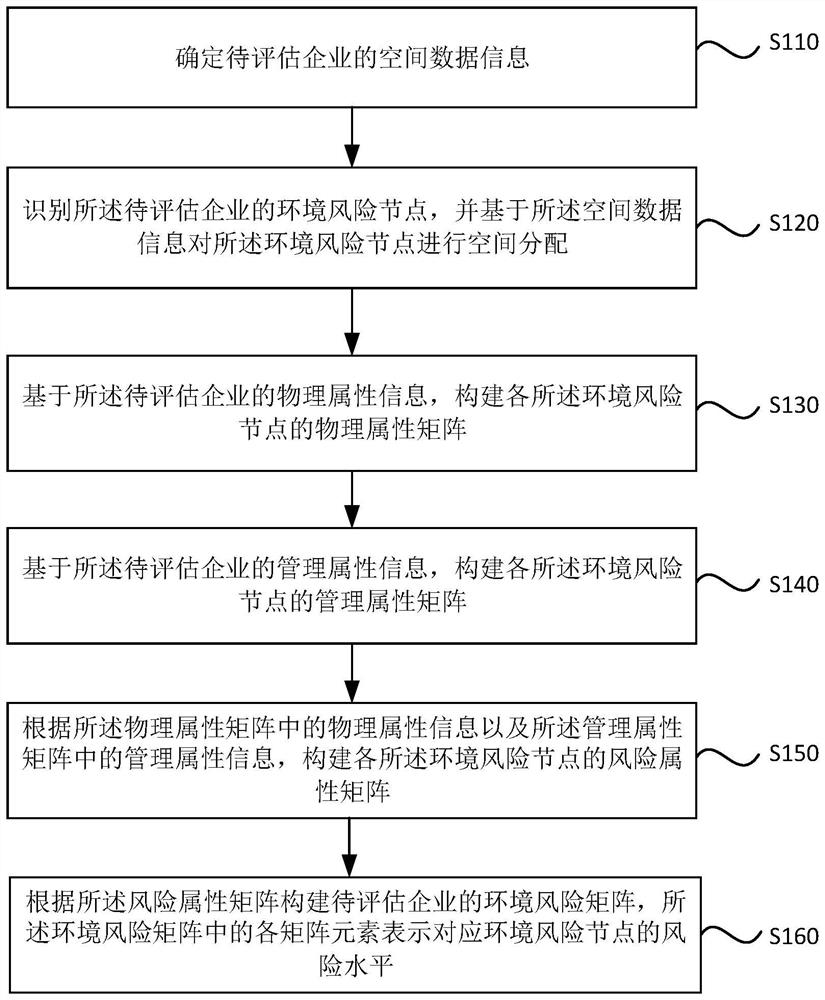
ActiveCN114154817BShorten the timeReduce labor costsResourcesRisk levelEnvironmental resource management
The invention discloses an automatic enterprise environmental risk assessment method and device. The method includes: determining the spatial data information of the enterprise to be assessed; identifying the environmental risk nodes of the enterprise to be assessed, and performing spatial allocation to the environmental risk nodes based on the spatial data information; constructing each of the environmental risk nodes The physical attribute matrix, management attribute matrix, and risk attribute matrix of the node; the environmental risk matrix of the enterprise to be evaluated is constructed according to the risk attribute matrix, and each matrix element in the environmental risk matrix represents the risk level of the corresponding environmental risk node. The technical solution of this embodiment comprehensively adopts various databases, and by constructing a multi-dimensional environmental risk attribute matrix, can realize automatic enterprise environmental risk node identification, environmental risk assessment and early warning, which provides an efficient and convenient environment for enterprise environmental risk accident prevention and control. and low-cost tools.
Owner:NANJING UNIV
Risk assessment method, device and system
PendingCN113762671AImprove code reuseReduce development and maintenance costsFinanceSoftware designService systemSystem risk
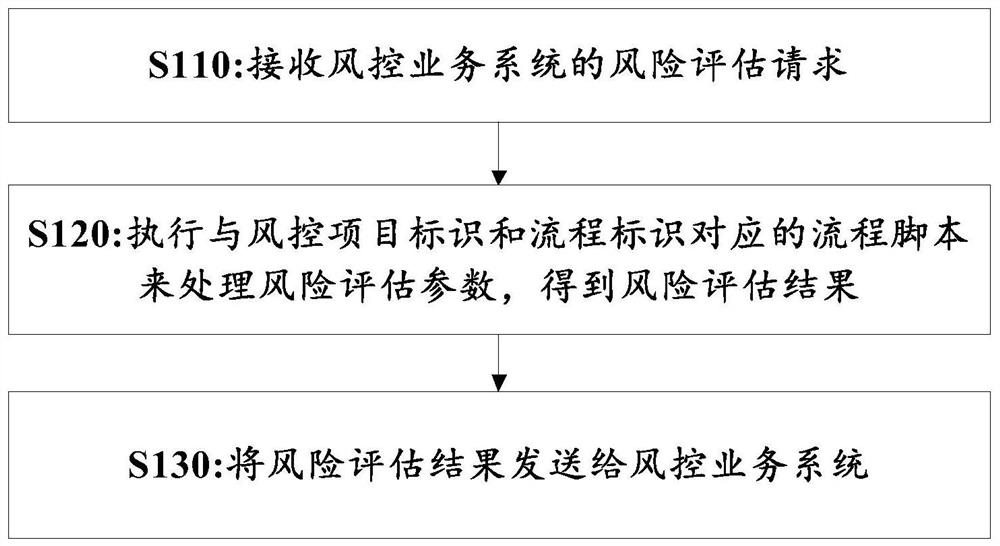
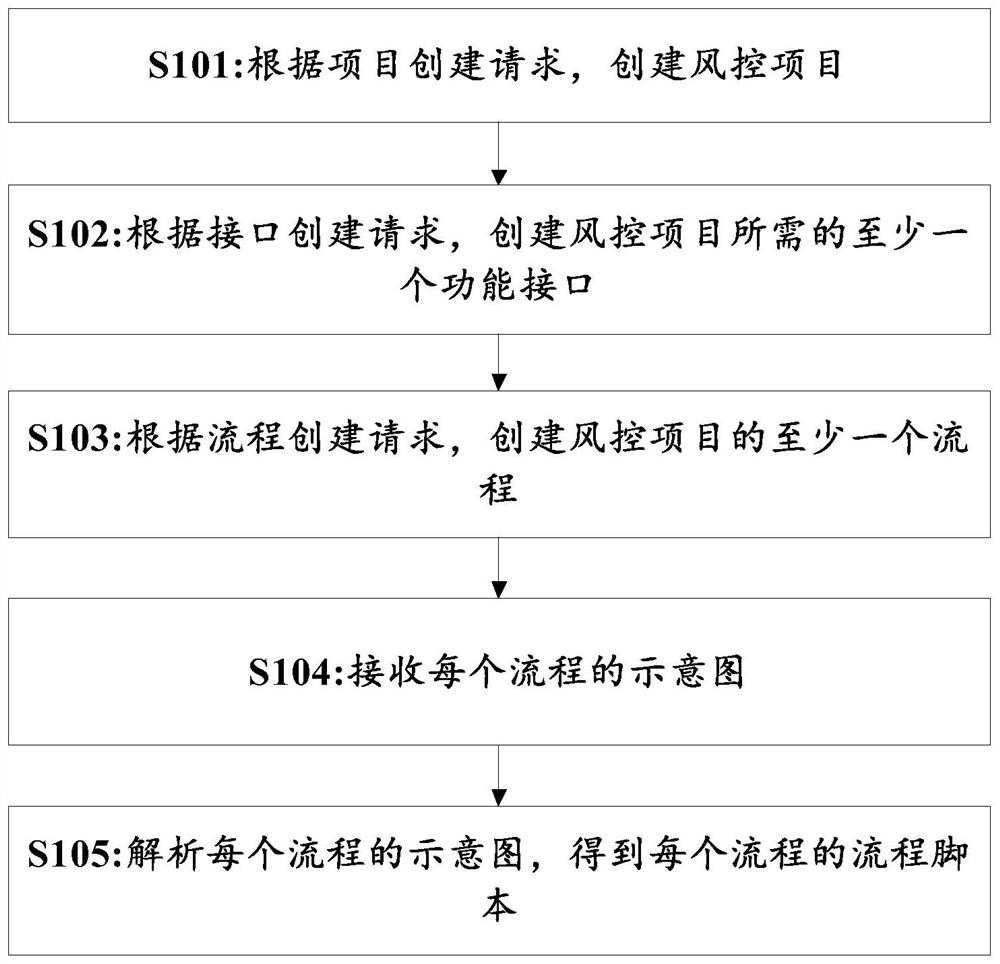
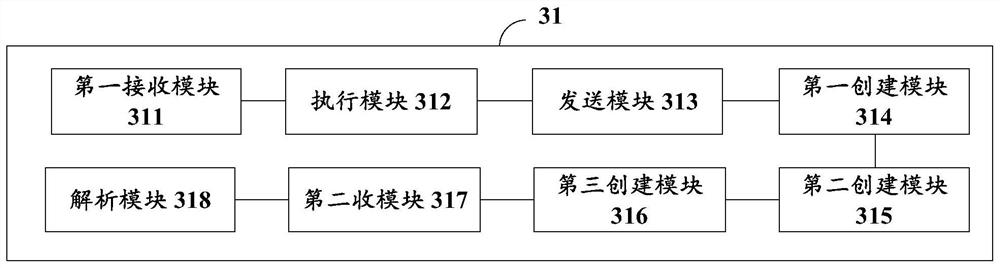
The invention relates to a risk assessment method, device and system. The risk assessment method comprises the following steps of receiving a risk assessment request of a risk control business system, wherein the risk assessment request comprises a risk control project identifier, a process identifier and a risk assessment parameter; executing a process script corresponding to the risk control item identifier and the process identifier to process the risk assessment parameter to obtain a risk assessment result; sending the risk assessment result to a risk control service system; risk control items being created according to the item creation request, and the risk control items being in one-to-one correspondence with risk control item identifiers; creating at least one functional interface required by the risk control project according to the interface creation request; according to the process creation request, creating at least one process of the risk control project, each process corresponding to one process identifier; a schematic diagram of each process being received, the schematic diagram of each process comprising a plurality of process nodes, and part of the process nodes being associated with the function interfaces; and analyzing the schematic diagram of each process to obtain a process script of each process.
Owner:BEIJING TONGBANGZHUOYI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com