Web interface design method for preventing request message from being tampered, attacked and replayed
A technology for requesting message and interface design, applied in user identity/authority verification, digital transmission system, electrical components, etc., can solve problems such as exposure and no secrets, and achieve the effect of reducing API power
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
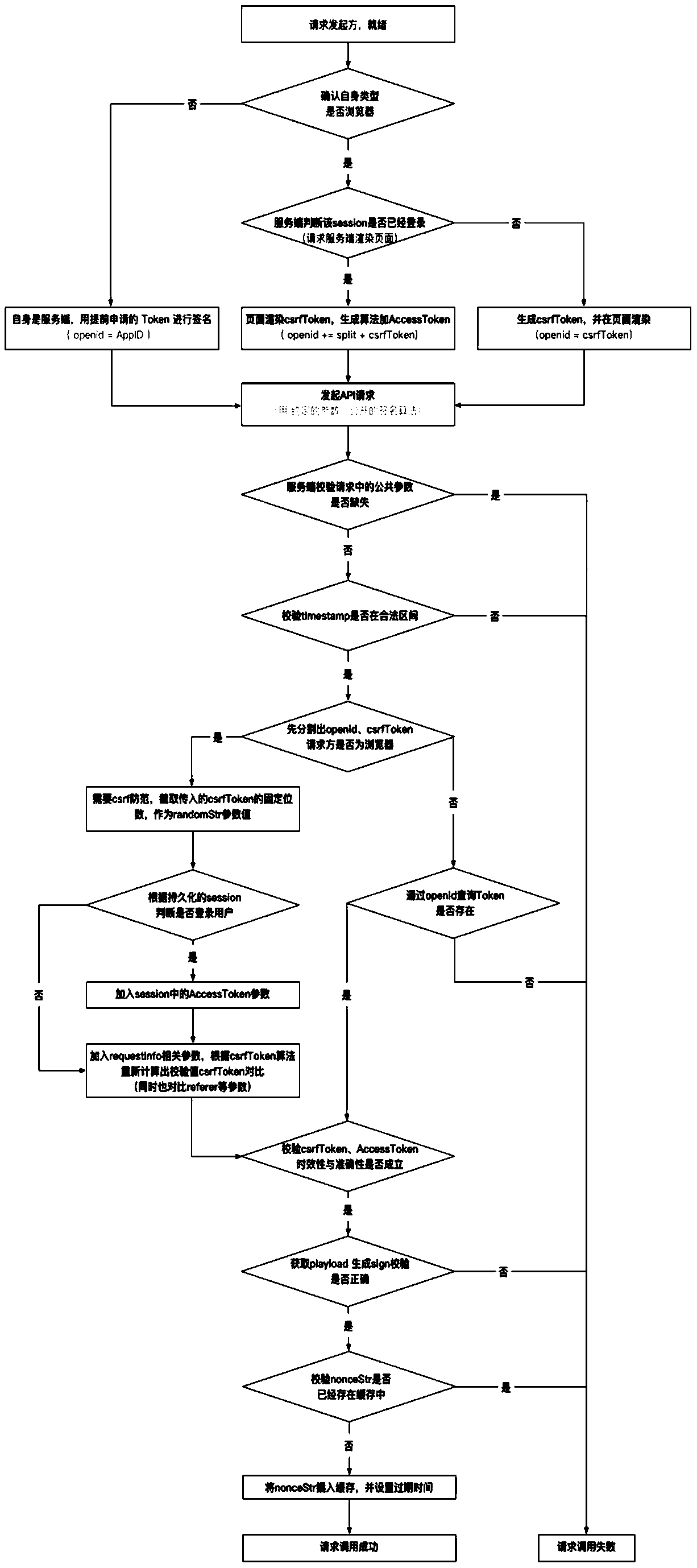
[0042] Such as figure 1 In the described embodiment, a kind of web interface design method that prevents the request message from being tampered with and attacked to replay, specifically comprises the following steps:
[0043](1) The server combines specific information to construct a Token, and if the caller is also a server, it will be issued in advance; if it is a browser client, it will return csrfToken;
[0044] If the caller is also a server, it will be issued in advance: Token=uuidNamespace(AppID). The Token is time-sensitive and associated with the AppID of the caller. The caller applies for it on the receiver server in advance, and needs to apply again after it expires.
[0045] If it is a browser client, csrfToken is returned, and relevant specific parameters are agreed first:
[0046] requestInfo=remoteIP+URLpath+UserAgentRandomSt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com