Network flow anomaly detection method based on intuitionistic fuzzy time series graph mining
A technology of time series and network traffic, applied in data mining, visual data mining, structured data retrieval, etc., can solve problems such as inaccurate prediction results, failure to consider the relationship between vertices in the graph, and insufficient consideration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
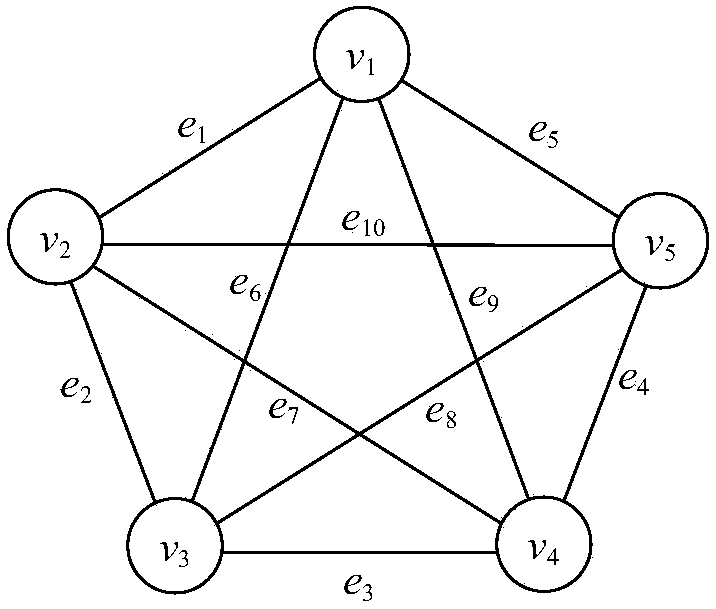
[0071] The present invention uses Intuitionistic Fuzzy Time Series (IFTS) prediction to solve the typical fuzzy time series problem of traffic anomaly detection, and comprehensively utilizes information entropy theory and graph mining technology to propose a network traffic anomaly detection based on IFTS graph mining method. This method introduces frequent subgraph mining technology to mine frequent subgraphs at each moment, establishes abnormal vectors to represent the abnormal situation of network traffic at this moment, and obtains its dynamic threshold by fitting and analyzing the distance between abnormal vectors, so as to carry out Judgment of network anomalies.
[0072] The present invention first uses information entropy to quantify the five-dimensional attributes of network traffic data, respectively establishes a heuristic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com