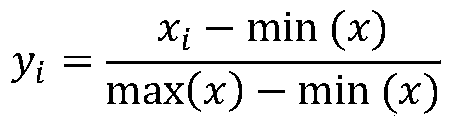Node risk assessment fusing ICT supply chain network topology and product business information
A technology of network topology and business information, which is applied in the field of node risk assessment, can solve problems such as incomplete assessment methods, and achieve the effect of perfect evaluation index system and high evaluation accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
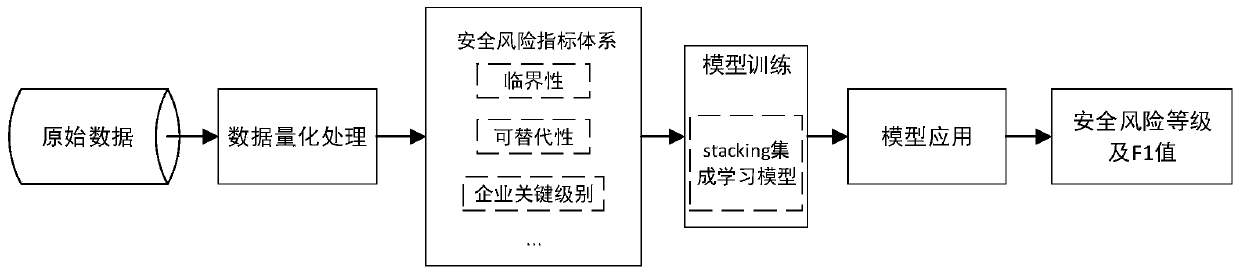
[0021] In order to better illustrate the purpose and advantages of the present invention, the implementation of the method of the present invention will be further described in detail below in conjunction with examples.
[0022] The experimental data comes from the National Enterprise Credit Information Publicity System and the websites of various bidding platforms, including 2043 pieces of enterprise data. Split the training set and test set at a ratio of 2:1.
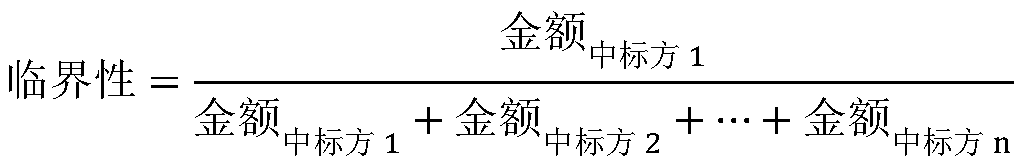
[0023] The following is a detailed introduction to the quantitative processing method of the 11-dimensional index.
[0024] 1. Enterprise type: The enterprise type is a single state-owned or listed company, and the quantitative assignment is 0.5; the enterprise type includes two types of state-owned and listed companies, and the quantitative assignment is 1;
[0025] 2. Registered capital: Normalize the registered capital of all companies, and the processing formula is:
[0026]
[0027] 3. Establishment date: Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com