Privacy protection set intersection solving method based on DH encryption and Hash table
A technology of privacy protection and encryption, applied in the field of intersection of privacy protection sets based on DH encryption and Hash table, to achieve the effect of improving intersection efficiency and reducing server costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
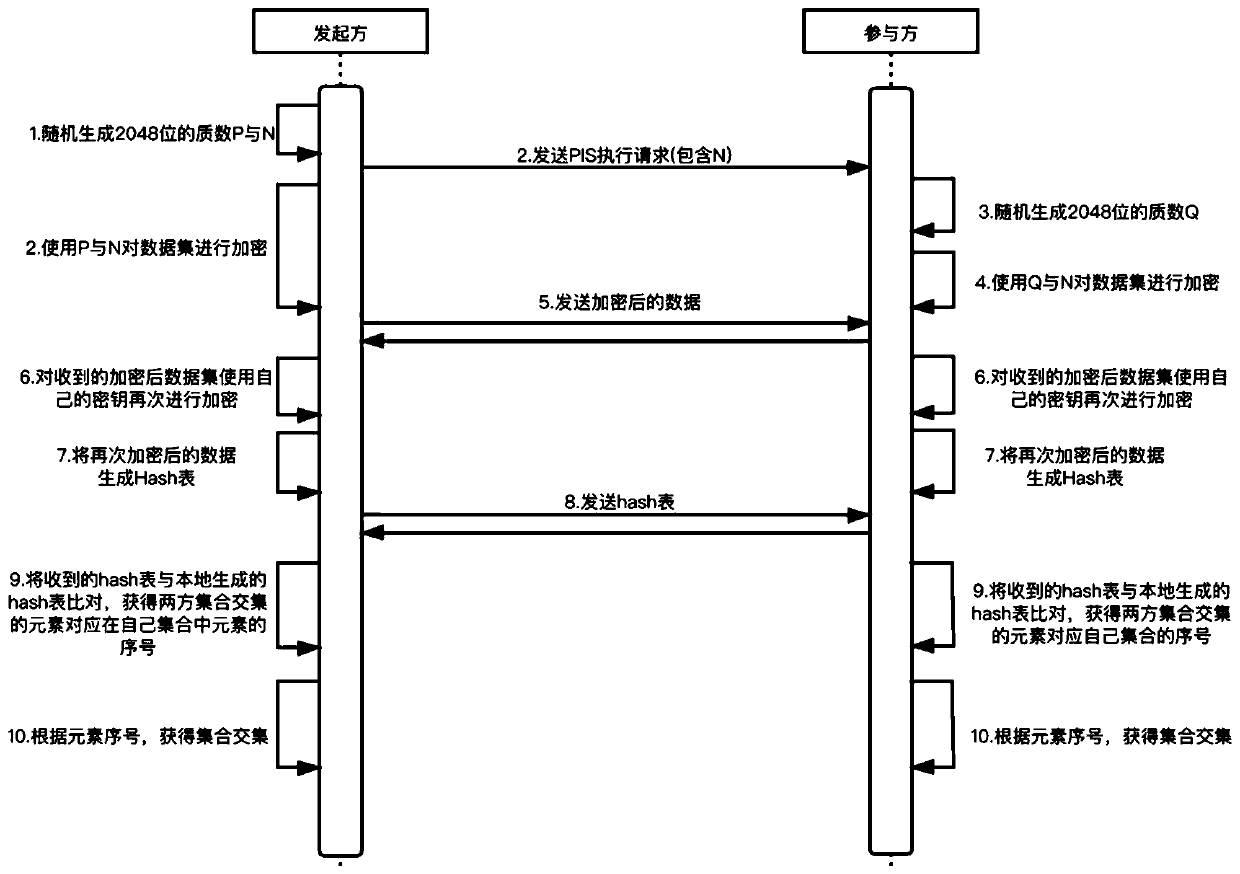
[0032] A method for finding the intersection of privacy-preserving sets based on DH encryption and Hash tables, the execution process is as follows figure 1 , which is used to initiate this intersection set request and the participants participating in this intersection set request, including the following steps:
[0033] (1) The initiator randomly generates a 2048-bit (decimal) prime number n as the encrypted modulus, and sends a PSI execution request for the privacy protection set intersection containing the prime number n to the participant; at the same time, a 2048-bit prime number p is randomly generated as the encrypted key Key, according to the one-way encryption method for the initiator data set M 1 The elements in are encrypted sequentially to obtain the data K encrypted by the initiator for the first time p ,Specifically:
[0034]
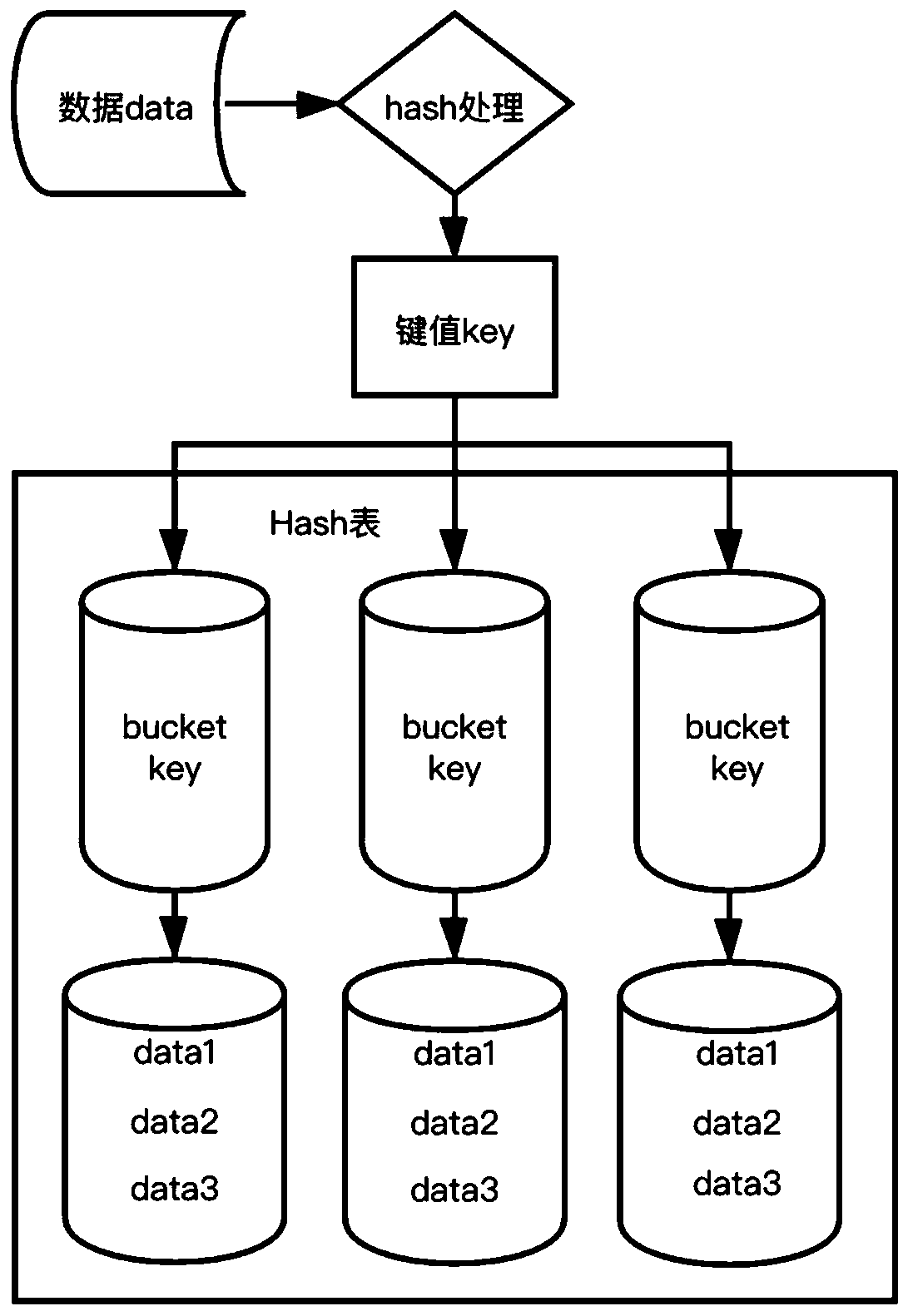
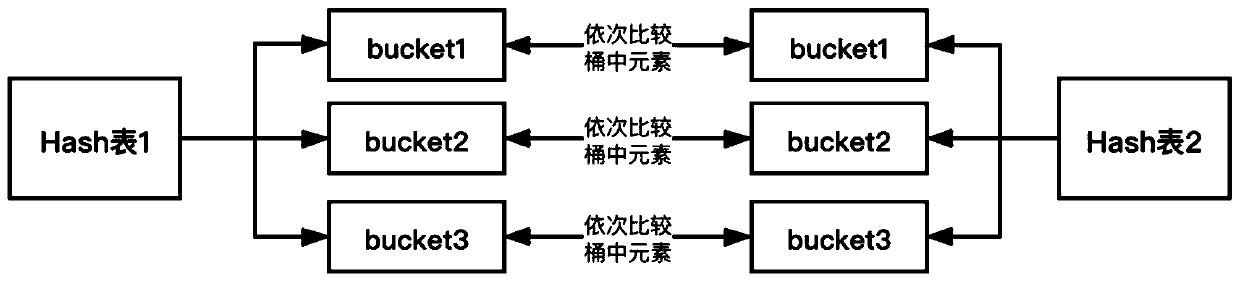
[0035] Among them, mod n Indicates the remainder of division by n, ie K p for The remainder of dividing by n; after the encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com