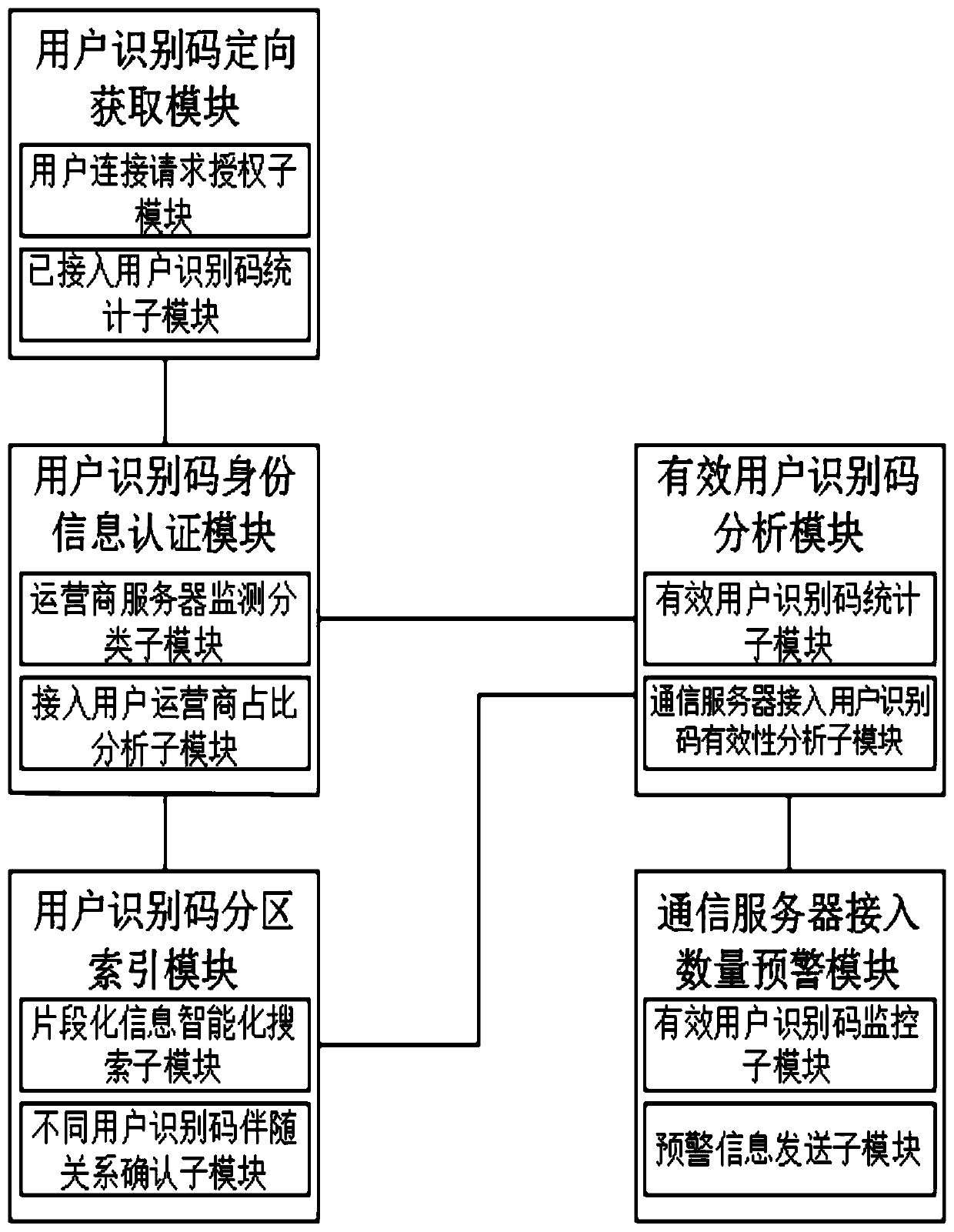
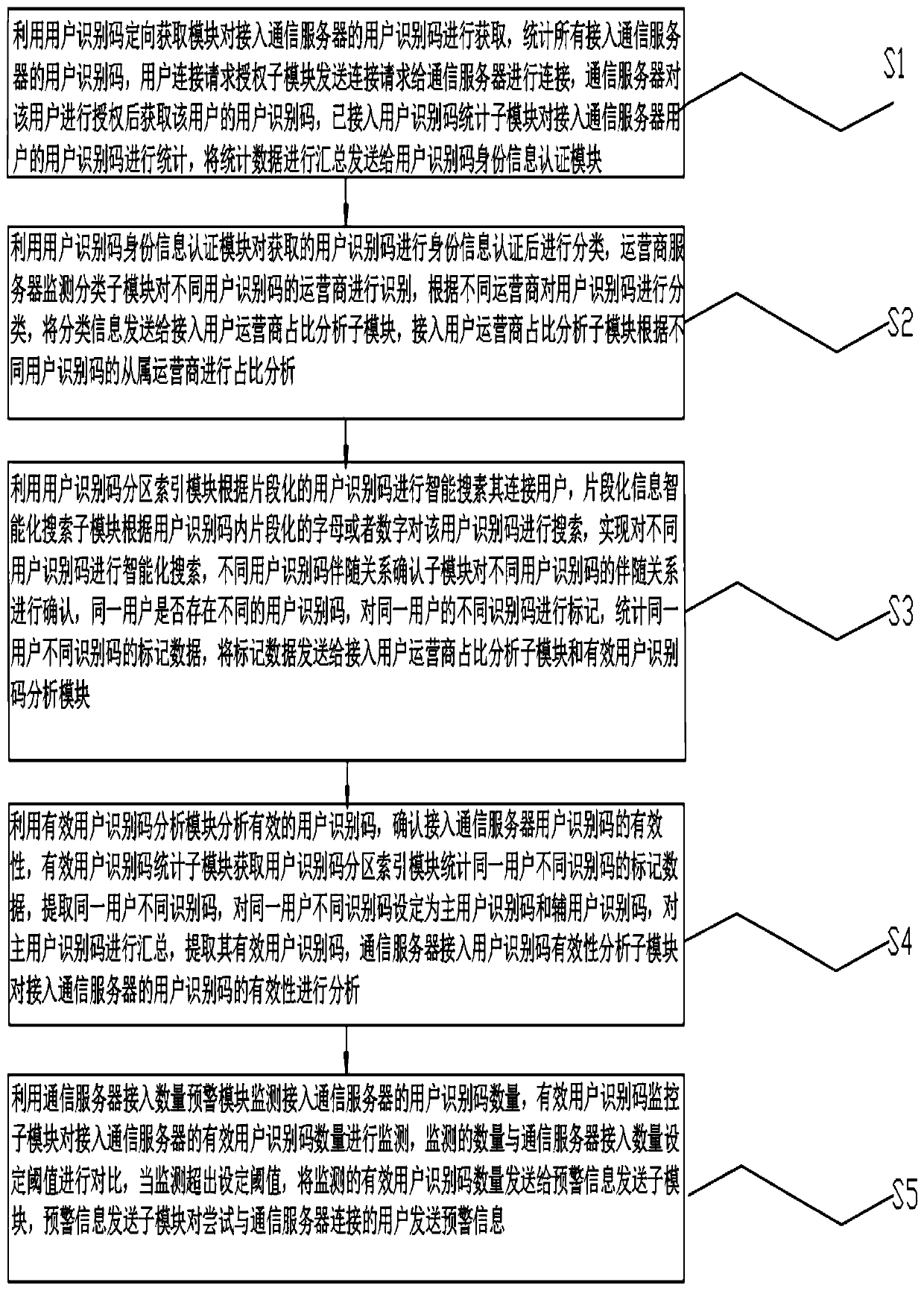
Communication service system and method for monitoring different user identification codes
A technology of user identification code and user identification, applied in the field of user identification code
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
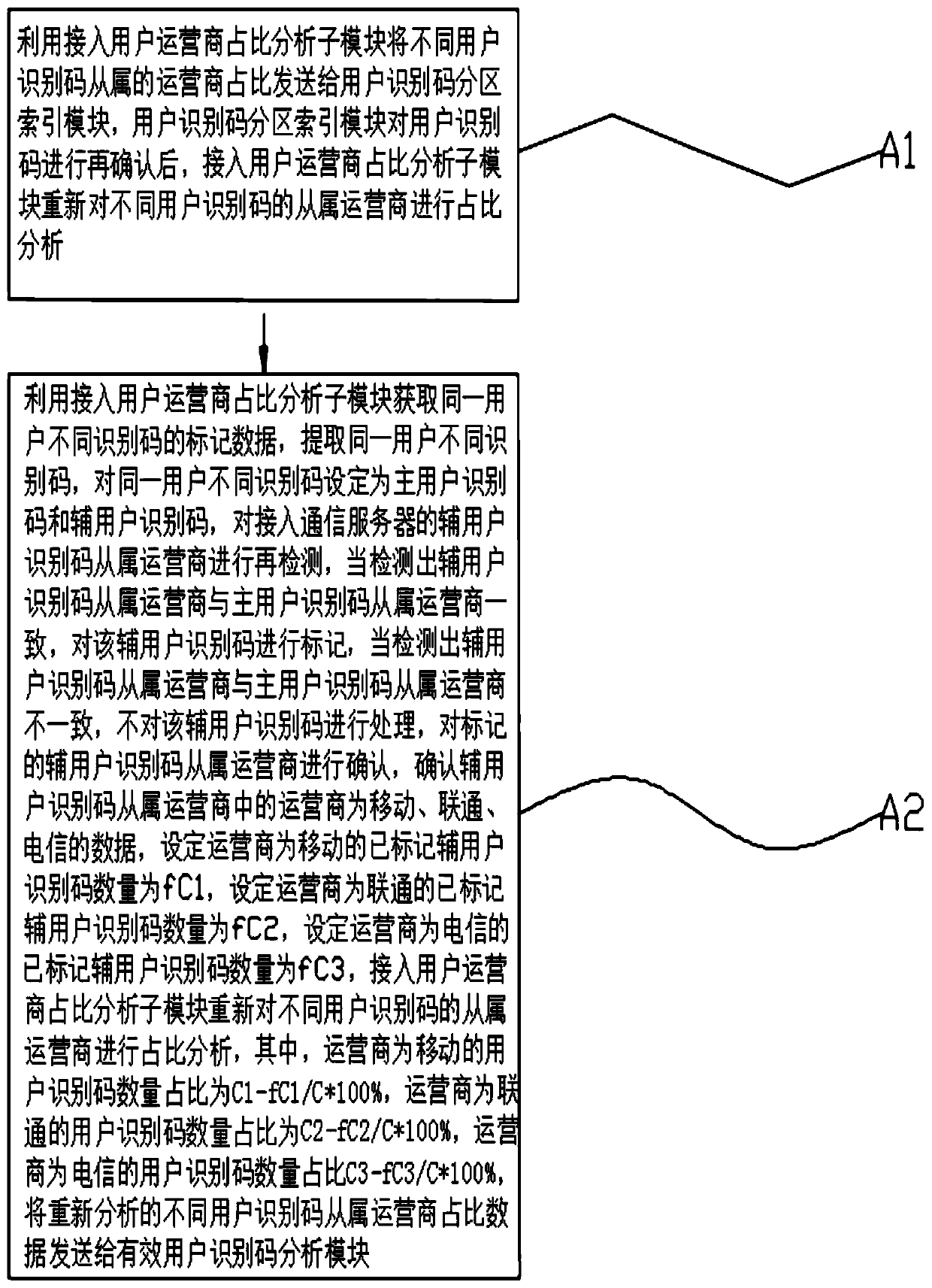
[0056] Embodiment 1: limited condition, set the number of user identification codes accessing the communication server to be 169, monitor that the number of user identification codes whose operator is China Mobile is 44, the operator is that the number of user identification codes of China Unicom is 47, and the operator is The number of subscriber identification codes of China Telecom is 78, the number of marked secondary subscriber identification codes of which the operator is China Mobile is 21, the number of marked secondary subscriber identification codes of which the operator is China Unicom is 23, and the operator is set of China Telecom The number of marked secondary user identification codes is 41, and the access user operator proportion analysis sub-module analyzes the proportion of subordinate operators with different user identification codes again. Among them, the proportion of the number of user identification codes whose operator is China Mobile is The proporti...
Embodiment 2
[0057] Embodiment 2: limited condition, set the number of user identification codes accessing the communication server to be 825, monitor that the number of user identification codes whose operator is China Mobile is 241, the operator is that the number of user identification codes of China Unicom is 197, and the operator is The number of subscriber identification codes of China Telecom is 387, the number of marked secondary subscriber identification codes of which the operator is China Mobile is 17, the number of marked secondary subscriber identification codes of which the operator is China Unicom is 21, and the operator is set of China Telecom The number of marked secondary user identification codes is 77, and the access user operator proportion analysis sub-module analyzes the proportion of subordinate operators with different user identification codes again. Among them, the proportion of the number of user identification codes whose operator is China Mobile is The proport...
Embodiment 3
[0058] Embodiment 3: Limiting conditions, setting and extracting the user identification code R for accessing the communication server 1 , R 2 , R 3 ,...,R n-1 , R n , extract the main user ID R0 in the above user ID 1 , R0 2 , R0 3 ,...,R0 n-1 , R0 n , wherein, the number of secondary user identification codes in the above-mentioned user identification codes is 2, 3, 1, 3, 4, and the validity of the above-mentioned user identification codes is set as Set the validity of the user identification code of the access communication server to D, according to the formula:
[0059]
[0060] It is calculated that the effectiveness of the user identification codes currently accessing the communication server is 30.7%, and the valid user identification codes are sent to the early warning module of the number of access to the communication server for monitoring.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com