A method and system for implementing software-defined boundaries based on SDN
A technology of software definition and implementation method, applied in the direction of transmission system, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
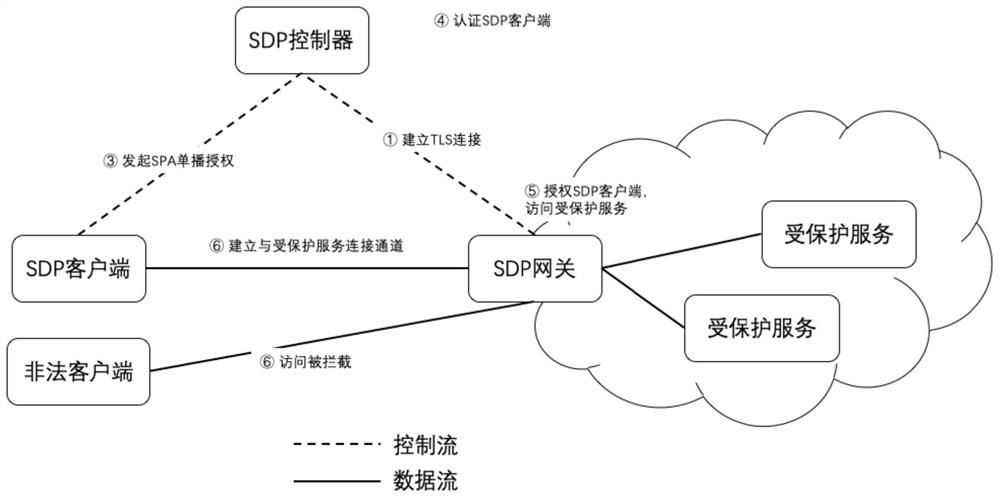
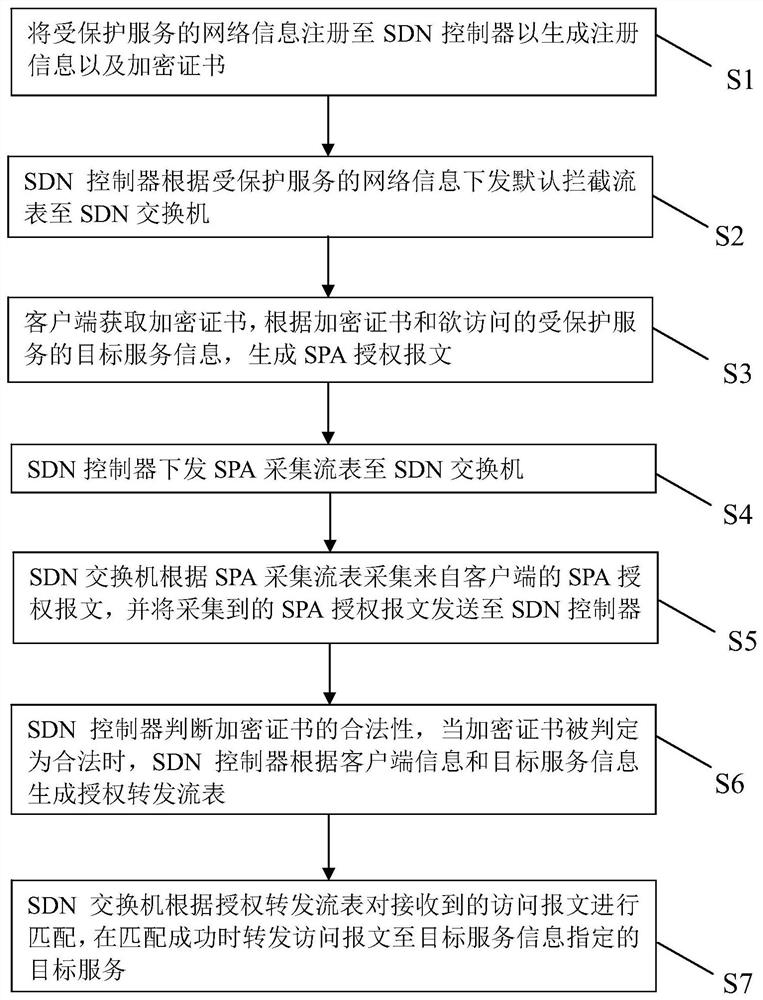
[0037] Such as figure 2 with Figure 4 As shown, this embodiment discloses a method for implementing an SDN-based software-defined boundary, the steps of which include:
[0038] S1. Register the network information of the protected service to the SDN controller to generate registration information and an encryption certificate.
[0039] Specifically, the registration information includes credentials for decrypting the encryption certificate. Therefore, the SDN controller can subsequently verify the legitimacy of the received encryption certificate according to the credentials in the registration information.
[0040] S2. The SDN controller sends a default intercept flow table to the SDN switch according to the network information of the protected service.
[0041]Specifically, the default interception flow table is set to discard the access packets whose destination address is the protected service. In this embodiment, the purpose of this setting is that when the protecte...
Embodiment 2
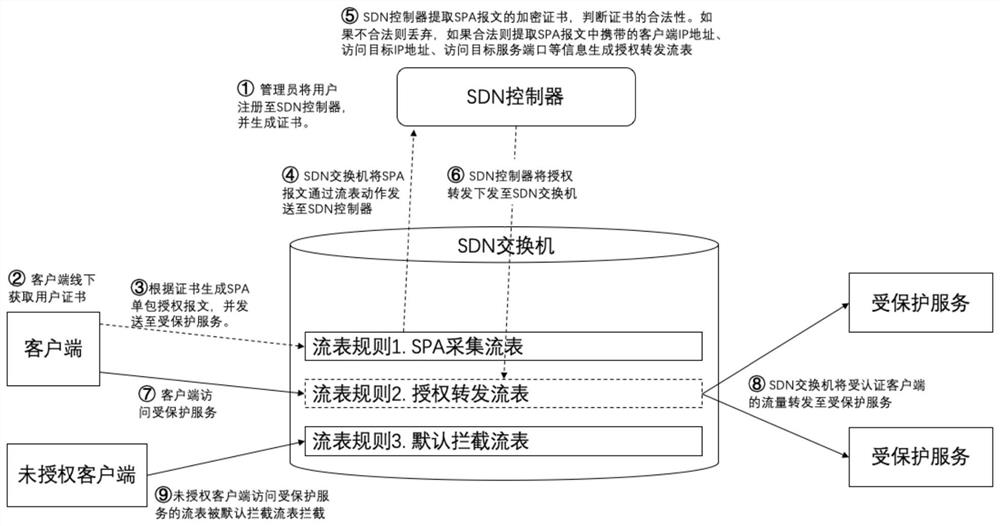
[0054] Such as image 3 with Figure 4 As shown, this embodiment corresponds to the method for realizing the SDN-based software-defined boundary disclosed in Embodiment 1, and discloses a specific application solution of the method.
[0055] Specifically, this application scheme includes the following steps:
[0056] ①The administrator registers the user to the SDN controller and generates a certificate.
[0057] ②The client obtains the user certificate offline to ensure that the SDN controller does not need to expose the external network and prevent the SDN controller from being attacked by hackers.
[0058] ③The client generates a SPA single-package authorization message based on the certificate, and sends it to the protected service. The SPA message is a UDP protocol message, and the target IP of the message is the IP address of the protected service. The data content of the message includes: user name, time stamp, encryption type, encryption mode, signature data, encryp...
Embodiment 3
[0066] This embodiment discloses a software-defined boundary implementation system based on SDN, its structure can refer to image 3 , the system includes an SDN controller and an SDN switch, wherein the SDN controller controls multiple virtual machines in the service group through the SDN switch. Specifically, the SDN controller and the SDN switch in this embodiment are used to execute such as implementing The SDN-based software-defined boundary implementation method described in Example 1 is used to realize the software-defined boundary. Specifically, the technical effect of the technical solution in this embodiment is similar to that in Embodiment 1, and will not be repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com