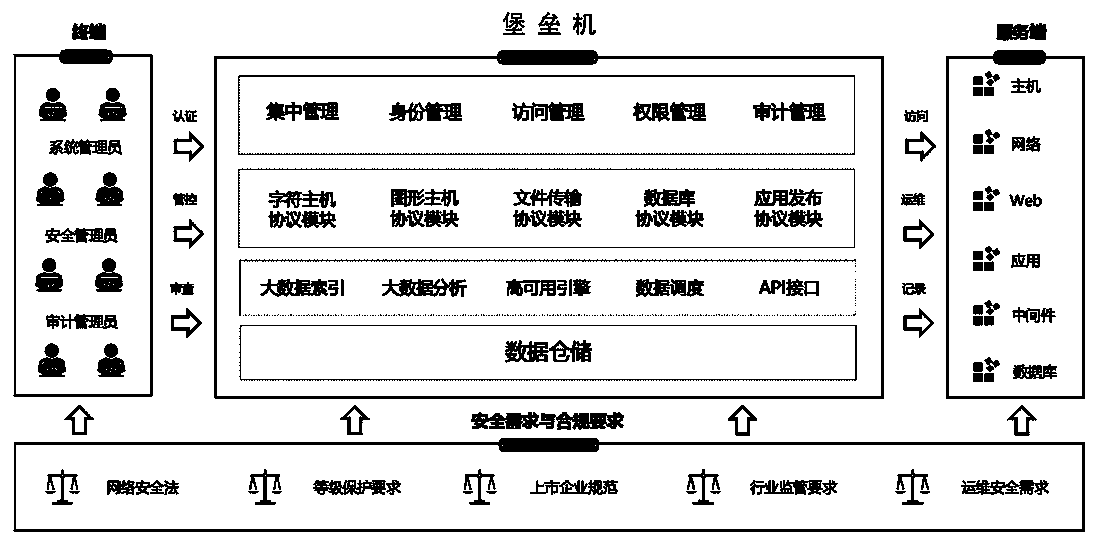
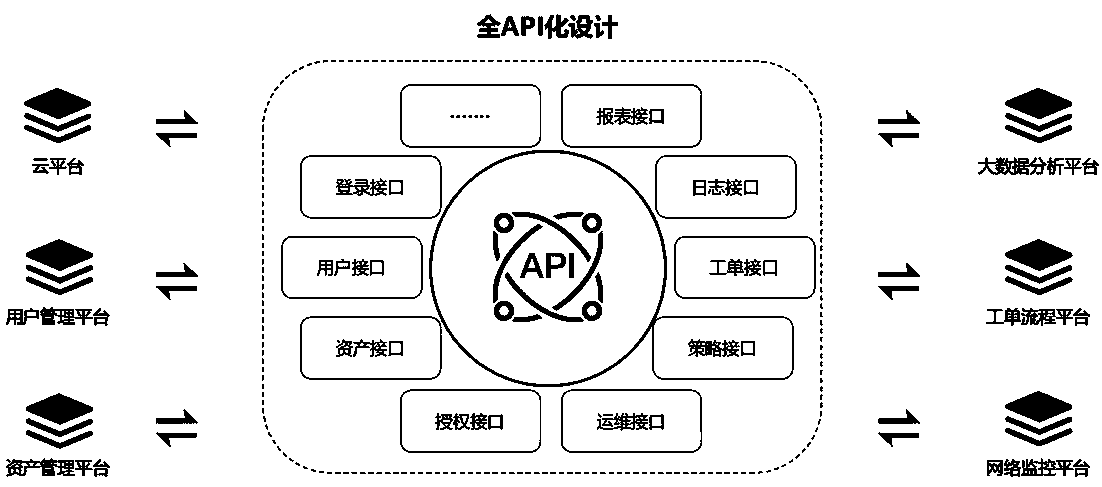
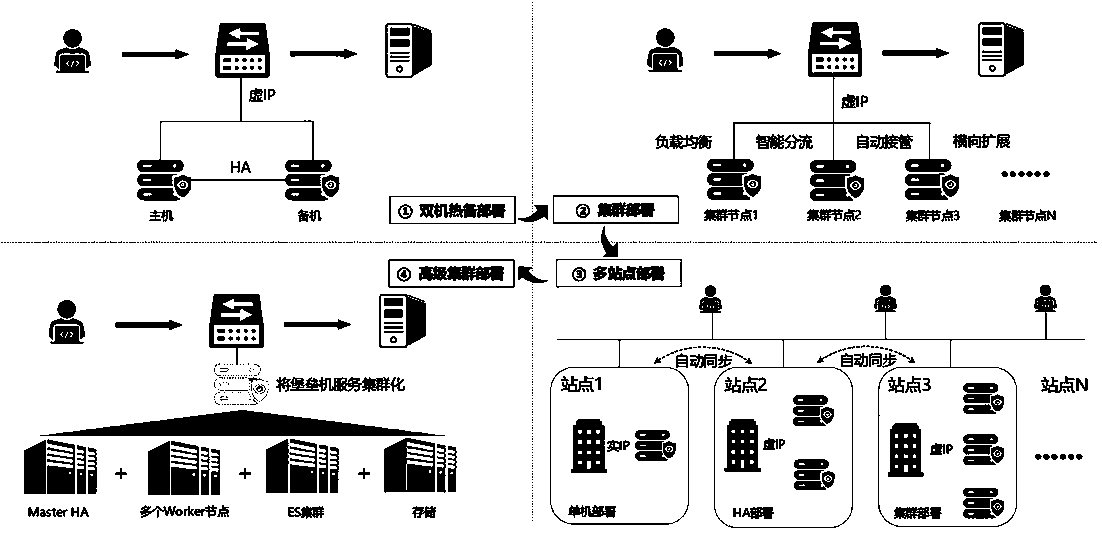
Bastion host
A bastion machine and account technology, applied in the field of information security, can solve the problems of not paying attention to IT security, difficulty in sorting out asset ledgers, diverse and scattered asset risks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] abnormal behavior
[0034] The abnormal behavior mentioned in the present invention refers to the operation behavior that does not match the content of the white list, including but not limited to abnormal behavior caused by hacker attacks, abnormal behavior caused by misoperation of internal operation and maintenance personnel, etc.
[0035] gateway
[0036] Everyone knows that to walk from one room to another, one must pass through a door. Likewise, gateways send messages from one network to another. Information must also pass through a "pass", which is the gateway. As the name implies, a gateway is a "gateway" that connects a network to another network, that is, a network gate. The gateway mentioned in the present invention refers to the door to enter the data center.
[0037] workflow engine
[0038] The so-called workflow engine refers to workflow as a part of the application system, and it provides core solutions such as determining information transmis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com