A fault location method, device, electronic equipment and storage medium
A fault location and fault propagation technology, applied in the computer field, can solve problems such as high frequency of system iterations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0062] Embodiment 1 This embodiment provides a fault location method
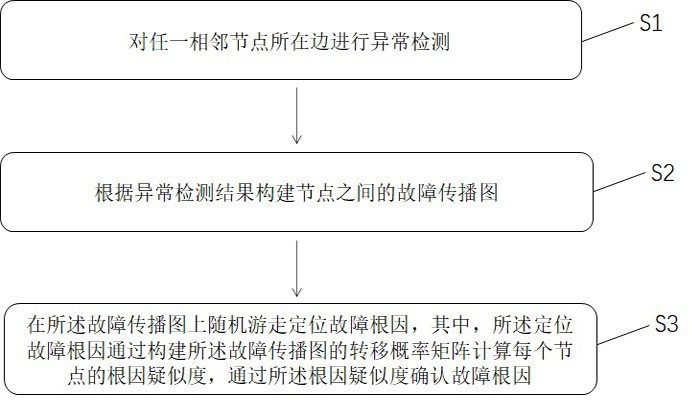
[0063] Such as figure 1 As shown, the method provided in this embodiment includes:
[0064] S1 performs anomaly detection on the KPI between nodes;
[0065] S2 builds a fault propagation graph between nodes according to the abnormality detection results;
[0066] S3 randomly walks on the fault propagation graph to locate the root cause of the fault, wherein the root cause of the fault is calculated by constructing the transition probability matrix of the fault propagation graph to calculate the root cause suspicion of each node, and by the root cause suspicion Identify the root cause of the failure.
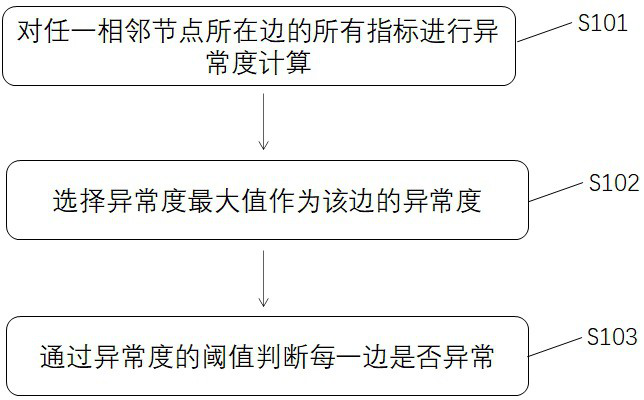
[0067] Such as figure 2 As shown, anomaly detection in S1 includes the following steps:
[0068] S101 Calculate the abnormality of all indicators on the edge where any adjacent node is located;
[0069] S102 selects the maximum value of the abnormality degree as the abnormality degree of the edge;
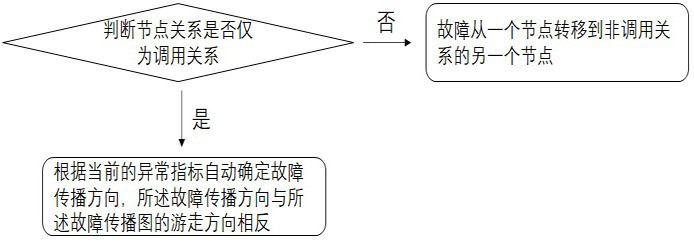
[0...
Embodiment 2
[0096] Embodiment 2 This embodiment provides another fault location method
[0097] 1. Anomaly detection
[0098] Such as Figure 6 As shown, it is a schematic diagram of the 3-sigma algorithm, where A, B, C, D, and E are several service nodes, and the arrows indicate the call relationship between nodes. It is necessary to perform anomaly detection on each edge on the graph, and each edge contains Several indicators, such as total transaction volume, success rate, response rate, average response time, etc., perform anomaly detection on each indicator.
[0099] In this embodiment, the commonly used 3-sigma algorithm is used for anomaly detection. The specific method is that for each index of each edge, we calculate its abnormal degree, and then select the maximum value of the abnormal degree of all indicators as the abnormal degree of an edge. Finally, we determine whether each edge is abnormal through the threshold of abnormality. The 3-sigma algorithm is as follows:
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com