A mimetic defense device, mimetic defense method and mimetic defense architecture
A heterogeneous, virtual machine technology, applied in computer security devices, instruments, computing, etc., can solve problems such as increasing the difficulty and cost of body mimicry transformation, and reducing the efficiency of executive body mimicry transformation, to ensure security and prevent mimicry. Escape, credibility-enhancing effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
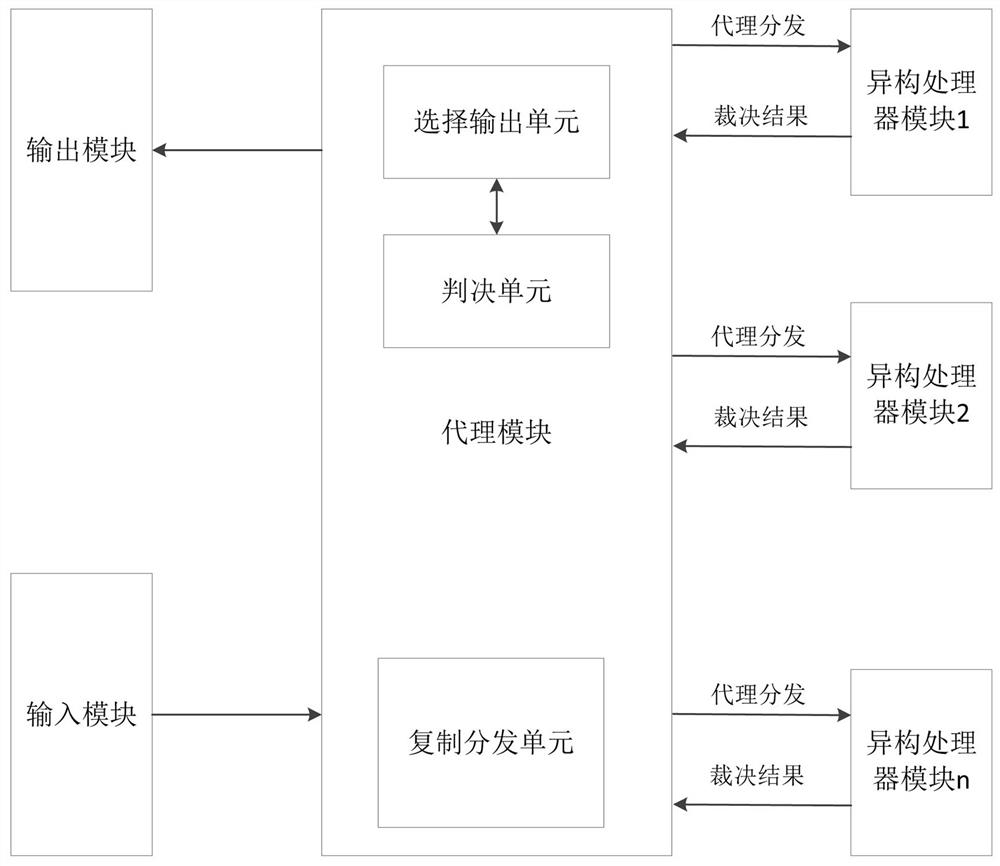
[0038] like figure 1 As shown, the first aspect of the present invention provides a mimetic defense device, comprising an input module, an output module, an agent module and a plurality of heterogeneous processor modules, the agent module includes a copy distribution unit, a judgment unit and a selection output unit; preferably , the selection output unit and the judgment unit are respectively software function modules generated inside the proxy module using software programming;
[0039] The input module supports the reception and transmission of external data;
[0040] The copying and distributing unit is respectively connected with the input module and a plurality of heterogeneous processor modules, receives external data sent by the input module, and copies and distributes it to the plurality of heterogeneous processor modules;
[0041] Each heterogeneous processor module includes an input agent, a plurality of heterogeneous virtual machines, and an arbiter. The input age...
Embodiment 2
[0054] This embodiment provides a mimetic defense method, comprising the following steps:
[0055] The input module receives external data, and replicates and distributes the external data to multiple heterogeneous processor modules through the replication and distribution unit of the agent module;
[0056] The input agent of each heterogeneous processor module replicates and distributes external data to multiple heterogeneous virtual machines, and multiple heterogeneous virtual machines process the external data and output the processing results to the arbiter; The processing result of the machine is used for adjudication, and the adjudication result is output to the selection output unit;
[0057] The judgment unit obtains the judgment results output by the multiple heterogeneous processor modules from the selection output unit, judges the multiple judgment results, and returns the judgment results to the selection output unit;
[0058] The selection output unit selects a j...
Embodiment 3
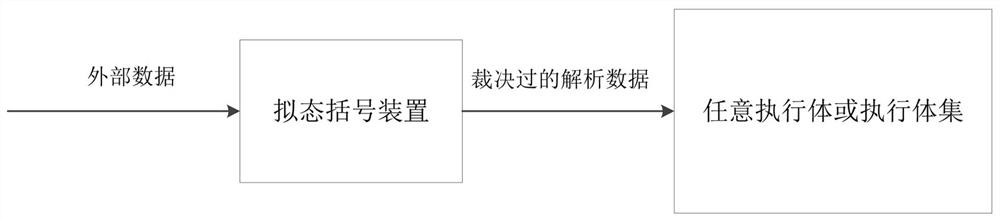
[0066] This embodiment provides a mimetic defense architecture, such as figure 2 As shown in the figure, it includes the aforementioned mimetic defense device and an executor, and the mimetic defense device is connected to the executor for receiving external data, analysing and adjudicating the external data, and outputting the adjudication result to the executor; the execution The body responds to the ruling.
[0067] It should be noted that the mimetic defense architecture can be applied in front of servers, routers or other devices according to specific mimetic defense requirements.
[0068] By adding a mimetic defense device with independent functions at the front end of the executive body, the data received by the executive body at this time is the data that has been judged by the mimetic defense device, and its security can be effectively guaranteed, that is, it can effectively ensure that the executive body does not It will be attacked by this external data; on the pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com