Power transmission line external damage prevention identification method and terminal
A transmission line and identification method technology, applied in the field of image recognition, can solve problems such as limited improvement, and achieve the effect of fast recognition speed and high recognition accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
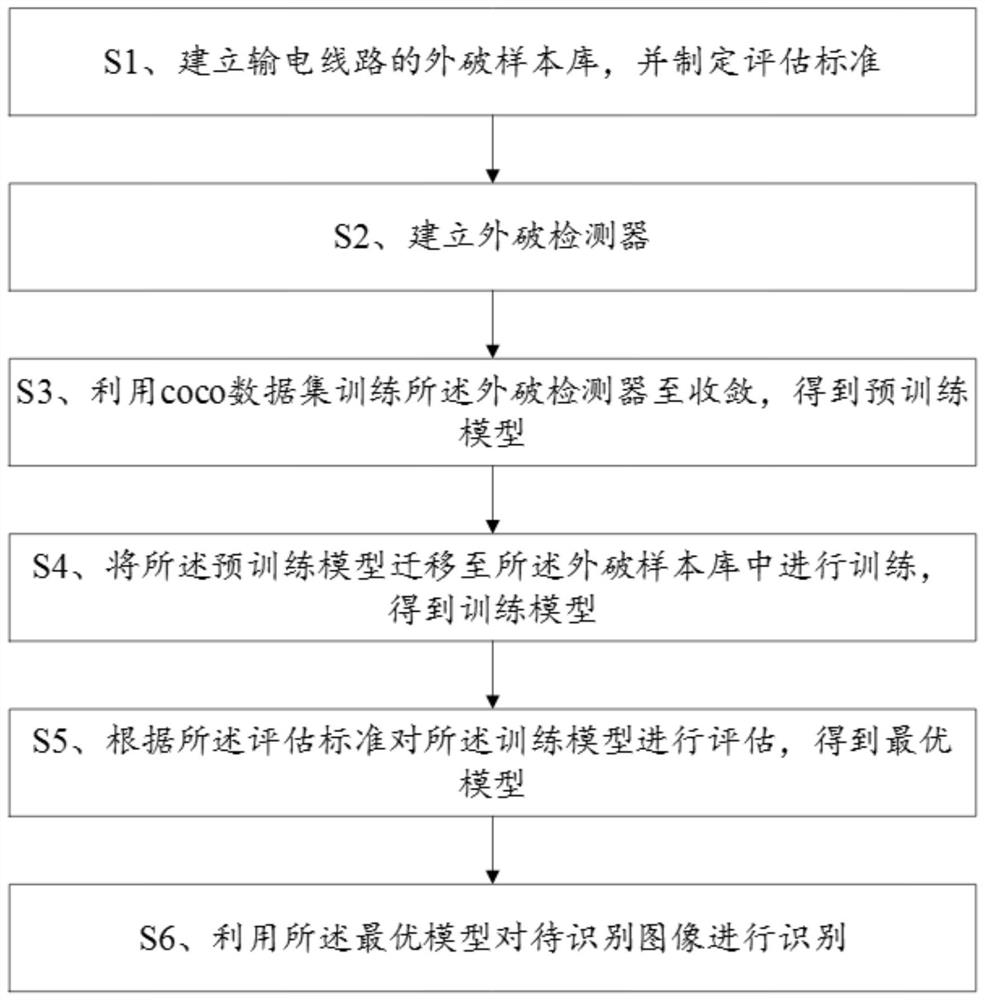
[0080] Please refer to figure 1 and figure 2 , Embodiment 1 of the present invention is a transmission line anti-breakage identification method, comprising the following steps:
[0081] S1. Establish a sample library of external failures of transmission lines, and formulate evaluation standards.
[0082] In this embodiment, the breach sample library includes pictures of different breach categories, for example, pictures of breach targets such as cranes, tower cranes, bulldozers, pump trucks, excavators, and forklifts. The evaluation standard is the mAP value of Pascal VOC challenge.
[0083] S2. Establishing a breach detector.
[0084] In this embodiment, step S2 is specifically:
[0085] S21. Obtain an overall feature map.
[0086] Utilize the DLA34 network as the backbone of the deep neural network to extract features to obtain a deep feature map (that is, the overall feature map), the overall feature map includes several regions to be detected with targets to be detec...
Embodiment 2
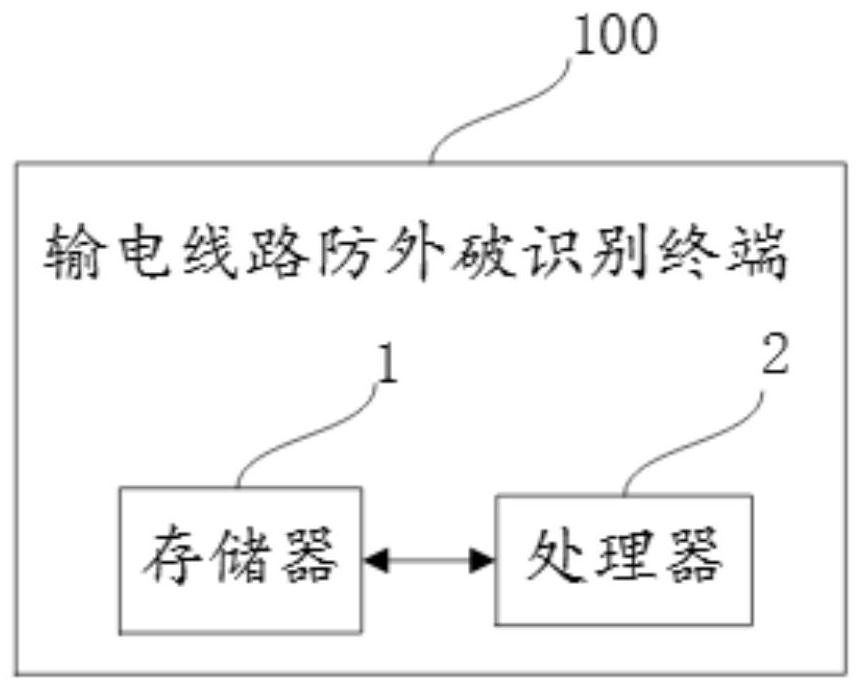
[0117] Please refer to image 3 , the second embodiment of the present invention is:
[0118] A transmission line anti-breakage identification terminal 100, corresponding to the method in Embodiment 1, including a memory 1, a processor 2, and a computer program stored in the memory 1 and operable on the processor 2, the processing Implement the following steps when the device 2 executes the computer program:
[0119] Establish a sample library of external failures of transmission lines and formulate evaluation standards;
[0120] Build a breakout detector;
[0121] Utilize the coco data set to train the described outer breakage detector to converge, obtain the pre-training model;
[0122] Migrating the pre-trained model to the breach sample library for training to obtain a training model;
[0123] Evaluating the training model according to the evaluation criteria to obtain an optimal model;
[0124] The image to be recognized is recognized by using the optimal model.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com