UICC application setting information management method, system and terminal
An information management and terminal technology, applied in the field of communication, can solve the problem of unable to control the behavior of UICC application settings, and achieve the effect of reducing the possibility of damage and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
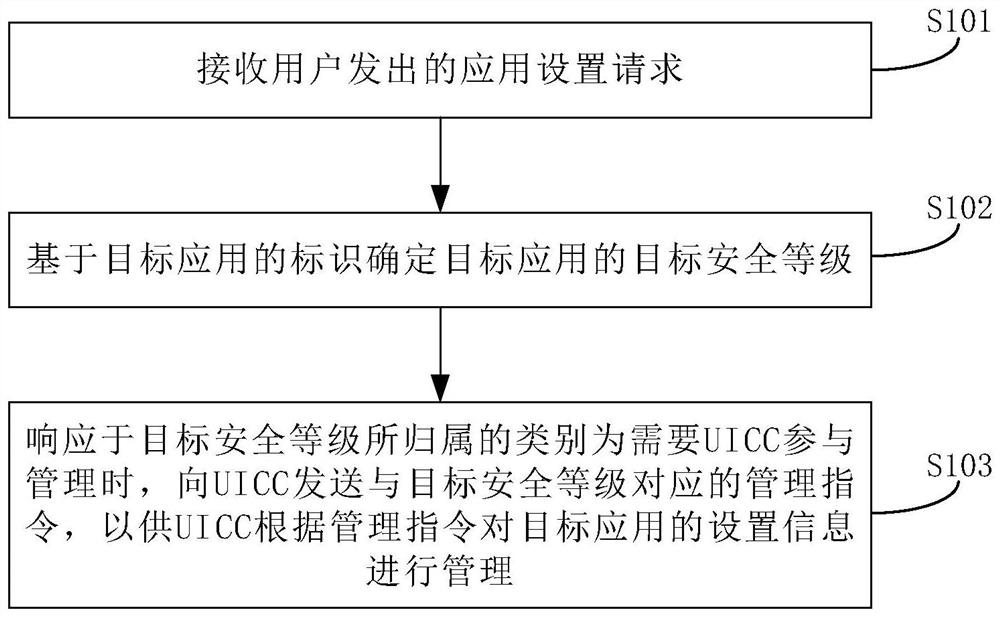
[0037] figure 2 It is a flow chart of a UICC application setting information management method provided in Embodiment 1 of the present invention, the method is based on figure 1 The implementation of terminal 1 in the implementation, through the method provided by this implementation, the UICC can participate in the management and control of the user's setting behavior of each UICC application, thereby improving the security of the necessary UICC application, and then protecting the user's rights and interests.
[0038] Such as figure 2 As shown, the method includes:
[0039] Step S101, receiving an application setting request sent by a user, where the application setting request includes an identifier of a target application.
[0040] Step S102. Determine the target security level of the target application based on the identifier of the target application.
[0041] Step S103 , when the category to which the target security level belongs requires UICC participation in man...
Embodiment 2
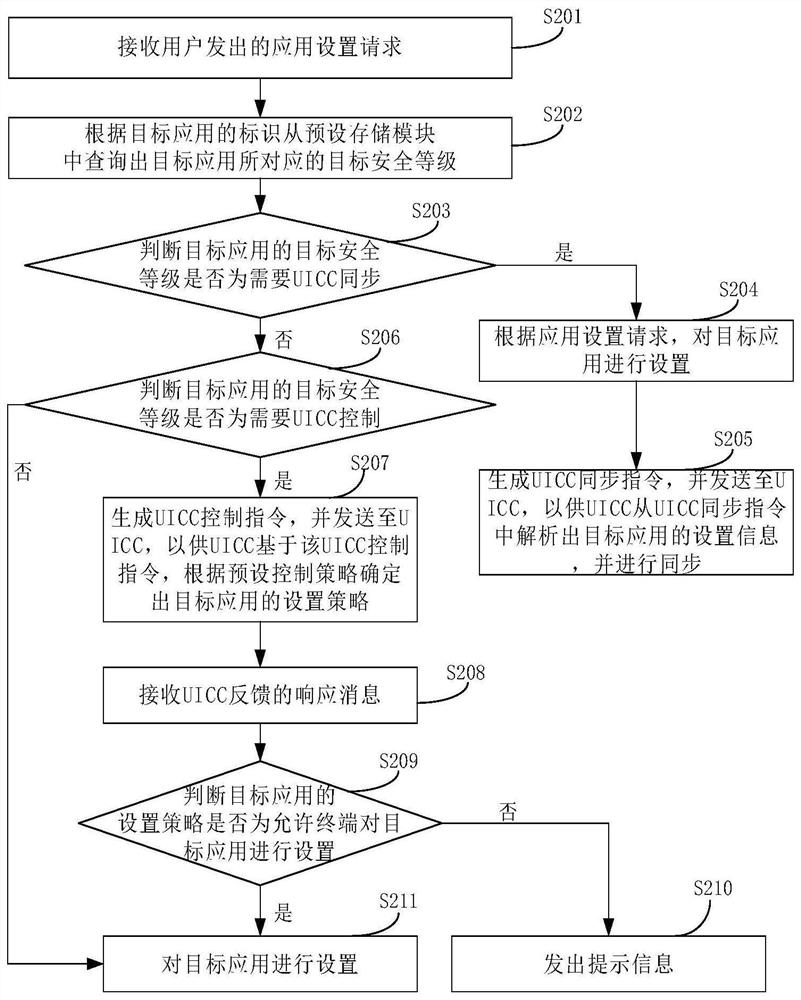
[0044] image 3 A flow chart of a UICC application setting information management method provided in Embodiment 2 of the present invention, as shown in image 3 As shown, the method includes:
[0045] Step S201, receiving an application setting request sent by a user, where the application setting request includes an identifier of a target application.
[0046]When the user needs to set the application on the UICC, the setting operation is performed on the terminal application of the terminal to send an application setting request to the terminal. The application setting request includes the identification of the target application, and the target application refers to the application that the user wants to set , preferably, in this embodiment, the setting performed by the user refers to the default setting of the application on the UICC, that is, setting a certain application as the default calling application for executing a certain service, so as to reduce the daily operat...
Embodiment 3
[0078] Figure 4 A schematic structural diagram of a terminal provided by the present invention, the terminal is used to implement the UICC application setting information management method provided by the present invention, such as Figure 4 As shown, the terminal includes: a receiving module 11 , a determining module 12 and an instruction generating module 13 .
[0079] Wherein, the receiving module 11 is used to receive the application setting request sent by the user, and the application setting request includes the identification of the target application; the determining module 12 is used to determine the target security level of the target application based on the identification of the target application; the instruction generating module 13 is used to respond When the category to which the target security level belongs requires UICC to participate in management, a management instruction corresponding to the target security level is generated, and the management instruc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com