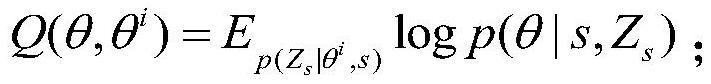Machine learning training data poisoning attack defense method
A technology of training data and machine learning, which is applied in the field of information security and can solve problems such as restrictions on attack methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
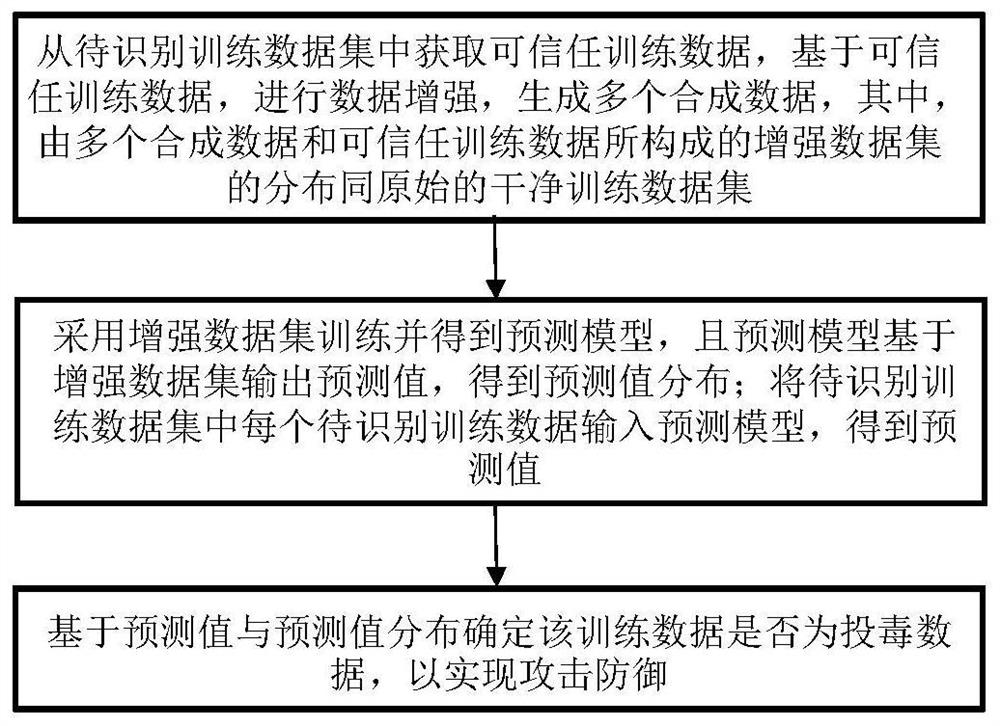
[0036] A defense method against poisoning attacks on machine learning training data, comprising:
[0037]Obtain the predicted value distribution of the clean training data set corresponding to the training data set to be identified; input each training data to be identified into the trained prediction model to obtain the predicted value; determine whether the training data is cast based on the predicted value and the predicted value distribution Toxic data to achieve attack defense;
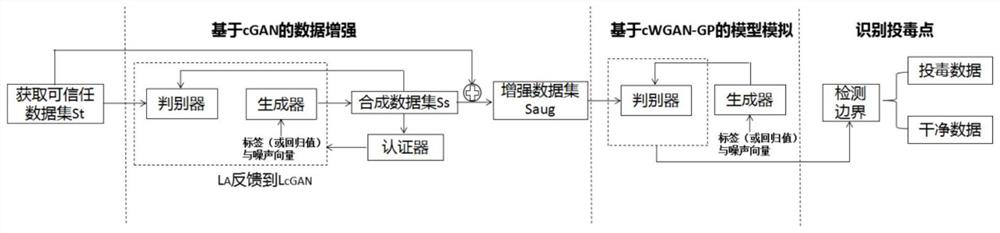
[0038] Among them, the prediction model is obtained by the following training methods: data augmentation based on the same type of trusted training data as the training data to be identified to generate multiple synthetic data; using an enhanced data set composed of multiple synthetic data and trusted training data Train and obtain the prediction model; the distribution of the enhanced data set is the same as that of the clean training data set, and the prediction model is based on the distributi...
Embodiment 2
[0082] A computer-readable storage medium, the computer-readable storage medium includes a stored computer program, wherein, when the computer program is run by a processor, the device where the storage medium is located is controlled to perform the above-mentioned machine learning training A defense method against data poisoning attacks. The relevant technical solutions are the same as those in Embodiment 1, and will not be repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com