Method and system for visualizing attack and defense strategies
A strategy and network attack technology, applied in the field of network security, which can solve the problems of difficulty in updating and defining attack types and ineffective deployment of defense strategies.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, so as to define the protection scope of the present invention more clearly.
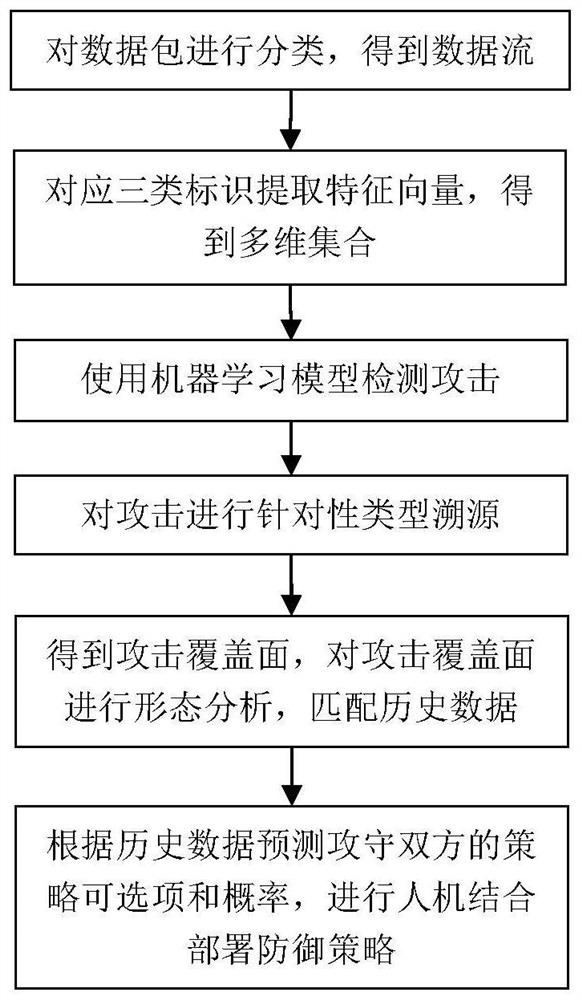
[0032] figure 1 A general flow chart of the attack defense strategy visualization method provided by this application, the method includes:
[0033] Obtain the data packets in the data stream, classify the data packets based on the transmission protocol, port, and application feature code, and put the classified data packets into a designated buffer queue;
[0034] Configure corresponding policy graphical interface systems for different types of data packets, use WYSIWYG policy management, select operations on the interface system, and continuously merge and organize the different types of data packets according to user identification information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com