Vulnerability attack detection system and method based on mimicry defense mechanism, and medium
An attack detection and defense mechanism technology, applied in transmission systems, computer security devices, instruments, etc., can solve problems such as difficult to know vulnerability attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054]The present invention is based on the mimetic DHR architecture, aiming at SQL injection, XSS (Cross-Site Script) cross-site scripting attack, CSRF (Cross-Site Request Forgery ) Cross-site request forgery and other attack behaviors have active detection capabilities, using tools such as NESSUS, awvs, OpenVAS, NetSparker, OWASP ZAP, Burpsuit, and MapReduce to build an active vulnerability attack detection system.
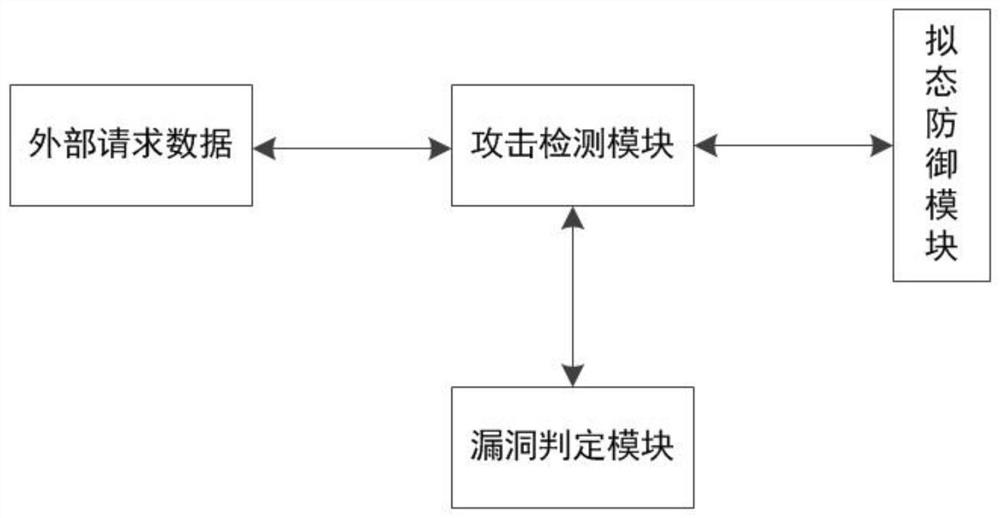
[0055] see figure 1 According to a vulnerability attack detection system based on a mimic defense mechanism provided by the present invention, it includes an attack detection module, a mimic defense module, and a vulnerability determination module;
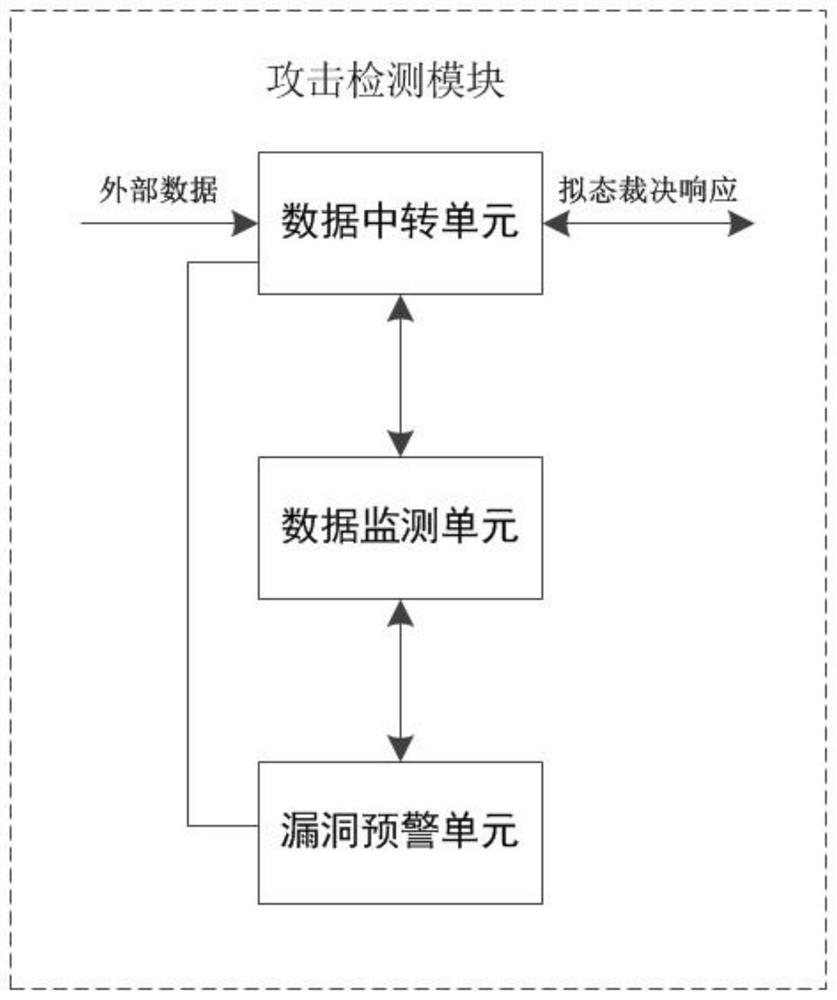
[0056] The attack detection module is used to receive the data sent by the external device, temporarily store and transfer the external data, forward the data to the mimic defense module, and judge whether it is attacked according to the signal returned by the mimic defense module. The judgment module sends a signa...
Embodiment 2
[0069] The vulnerability attack detection system based on the mimic defense mechanism provided by the present invention includes:
[0070] Attack detection module: Receive the data sent by the external device, temporarily store and transfer the external data, forward the received external data to the mimic defense module, and judge whether it is attacked according to the signal returned by the mimic defense module. The vulnerability determination module sends a signal;
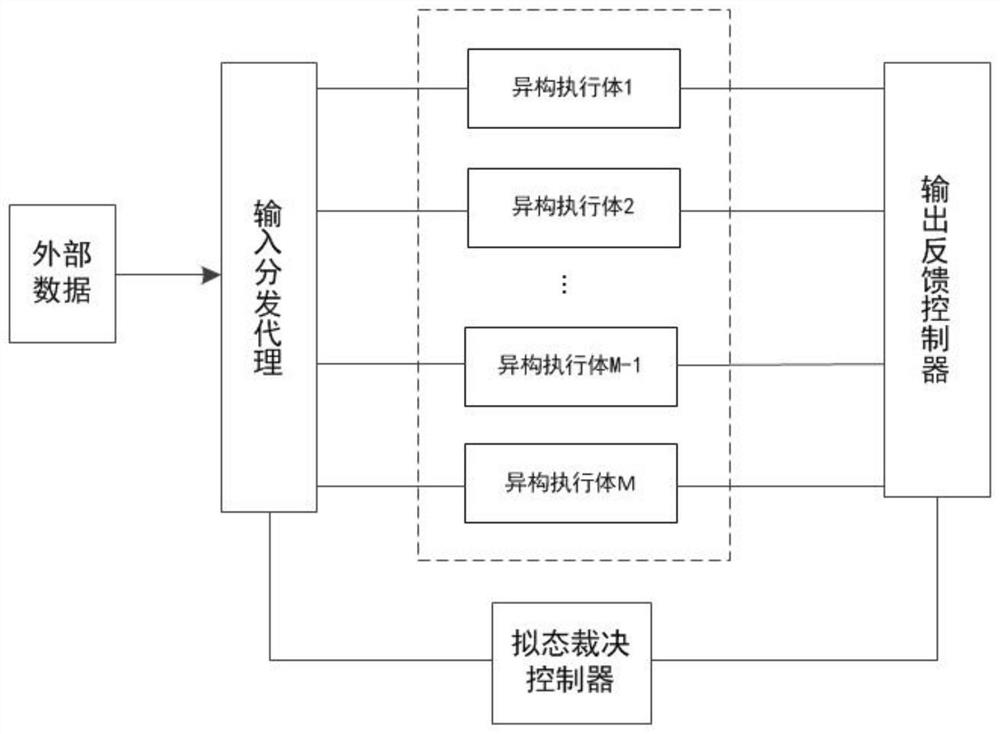
[0071] Mimic defense module: According to the mimic defense mechanism, it performs input agent distribution, redundant heterogeneous judgment and external response output for the received external data, and returns the judgment result to the attack detection module;
[0072] Vulnerability determination module: extract information from detected attack behaviors, obtain attack source characteristic information, trace attack source, establish vulnerability detection information database, match attack source chara...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com