Attack Detection Method for Device Defects in Discrete Quantum Key Distribution
A quantum key distribution, discrete quantum technology, applied in the field of attack detection for device defects, can solve problems such as difficult theoretical verification, increased system vulnerabilities, and insecurity of DVQKD systems, achieving high reliability and good accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
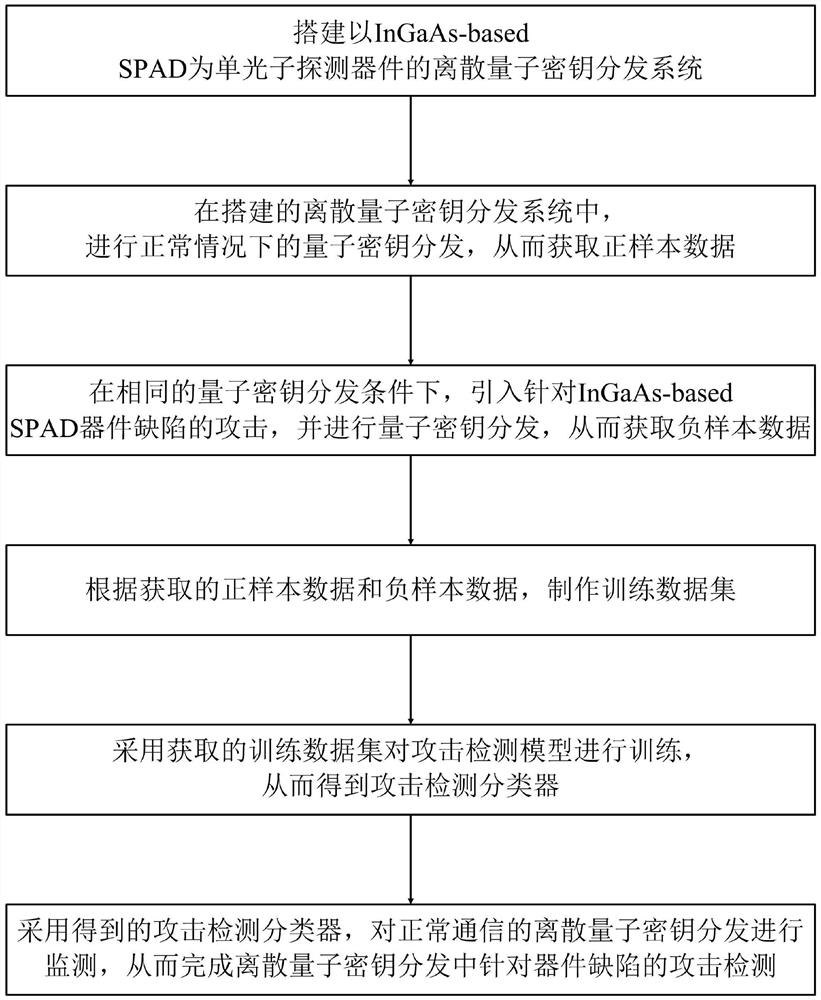
[0044] like figure 1 Shown is a schematic diagram of the method flow of the method of the present invention: the attack detection method for device defects in the discrete quantum key distribution provided by the present invention includes the following steps:
[0045] S1. Build a discrete quantum key distribution system using InGaAs-based SPAD as a single photon detection device;
[0046] S2. In the discrete quantum key distribution system built in step S1, perform quantum key distribution under normal circumstances to obtain positive sample data; specifically, the following rules are used to obtain positive sample data:
[0047] The discrete quantum key distribution system adopts the BB84 protocol, the encoding method is polarization encoding, the optical fiber is used as the transmission channel, and the working wavelength is 1550nm;
[0048] In the communication process, a gate mode duty cycle T is used as the measurement unit; every time t elapses, the number n of photon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com