Encryption and decryption method and system for quantum secret communication
A quantum security communication, encryption and decryption technology, which is applied in the field of quantum security communication, can solve problems such as high computing pressure, high communication pressure, and leakage, and achieve the effects of reducing computing pressure, ensuring security, and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] This embodiment proposes an encryption and decryption method for quantum secure communication, which is implemented in image 3 In the shown encryption and decryption system for quantum secure communication, the number of relay nodes in this system is n.
[0044] The whole method includes the following steps:
[0045] (1) Establish a quantum channel between the starting node and the target node.
[0046] (2) Divide the n relay nodes between the starting node and the target node into odd nodes and even nodes. Adjacent relay nodes are regarded as even nodes, and so on until all relay nodes are divided; image 3 As shown, among the n relay nodes, the relay node directly connected to the target node is numbered B1, and then numbered sequentially in the direction of the starting node, and the next relay node connected to the relay node B1 is numbered B2, The number of the next relay node connected to the relay node B2 is B3..., and the number of the relay node directly co...
Embodiment 2
[0054] The flow of this embodiment is as follows Figure 4 As shown, in the entire communication link, the starting node is A, the target node is E, and there are three relay nodes, namely B, C, and D.
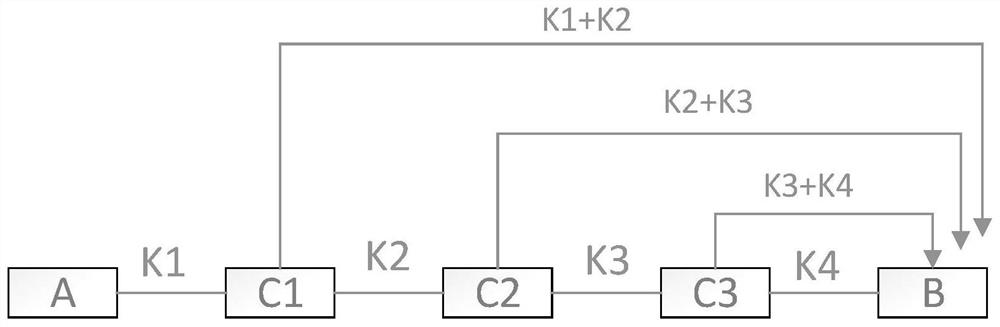
[0055] When A initiates a communication requirement, first establish a quantum communication link between A and E, and then negotiate a quantum key between adjacent nodes through quantum secure communication, and share the quantum key between node A and node B K1, the shared quantum key between B and C is K2, the shared quantum key between C and D is K3, and the shared quantum key between D and E is K4. When the quantum communication link is established, the intermediate nodes are identified as odd and even nodes. The specific rules are as follows: starting from the target node, the relay nodes directly adjacent to it are odd nodes, and then encode the relay nodes in sequence according to the odd and even numbers , such as attached Figure 4 D in D is an odd node, C is an ev...
Embodiment 3
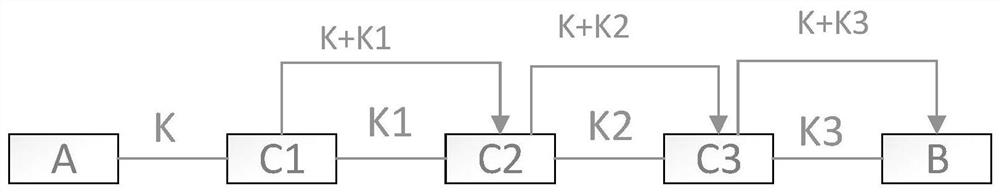
[0057] The flow of this embodiment is as follows Figure 5 As shown, in the entire communication link, the starting node is A, the destination node is D, and there are two relay nodes, namely B and C. According to the above identification of the parity of the relay node, C is an odd node, B is an even node, the starting node A’s own quantum key is K1, and the received quantum key of the odd node is the K2 XOR K3 of the C node, Therefore, the encryption key of the starting node is K1⊕(K2⊕K3); the quantum key of the target node D itself is K3, and the received quantum key of the even node is K1 XOR K2 of node B, so the target node’s The decryption key is K3⊕(K1⊕K2).
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com