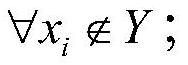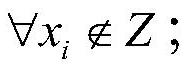Method and system for quickly generating an unmanned aerial vehicle cooperative relay network under a flow demand
A technology of traffic demand and cooperative relay, applied in the field of unmanned aerial vehicles
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
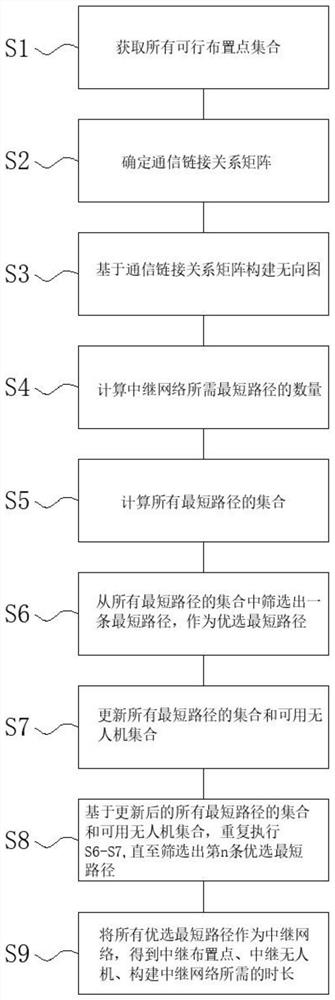
[0061] like figure 1 As shown, the present invention provides a method for quickly generating a UAV cooperative relay network under traffic demand, the method is executed by a computer, and the method includes:
[0062] A method for quickly generating a UAV cooperative relay network under traffic demand, the method comprising:
[0063] S1. Discretize the battlefield area based on the maximum communication distance constraint of the UAV, and obtain all feasible layout point sets X={x based on terrain obstacle constraints and enemy air defense threat constraints 1 ,...,x i ,x j ,…x k}; where x i 、x j Indicates two adjacent feasible arrangement points, and k indicates the number of feasible arrangement points;
[0064] S2. Obtain the communication link relationship matrix C based on the source node s, the target node t, the maximum communication distance constraint of the UAV and the feasible arrangement point set X;
[0065] S3. Construct an undirected graph G=(V, E, W) b...
Embodiment 2
[0119] A system for rapidly generating a coordinated relay network for unmanned aerial vehicles under traffic demand, the system includes a computer, and the computer includes:
[0120] at least one storage unit;
[0121] at least one processing unit;
[0122] Wherein, at least one instruction is stored in the at least one storage unit, and the at least one instruction is loaded and executed by the at least one processing unit to realize the following steps:
[0123] S1. Discretize the battlefield area based on the maximum communication distance constraint of the UAV, and obtain a set of all feasible deployment points based on terrain obstacle constraints and enemy air defense threat constraints X={x 1 ,…,x i ,x j ,…x k}; where x i , x j represents two adjacent feasible layout points, and k represents the number of feasible layout points;
[0124] S2. Obtain the communication link relationship matrix C based on the source node s, the target node t, the maximum communica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com