VPN flow identification method based on SSL encryption
An identification method and traffic technology, which is applied in the field of VPN traffic identification based on SSL encryption, can solve the problem of high rate of missed identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
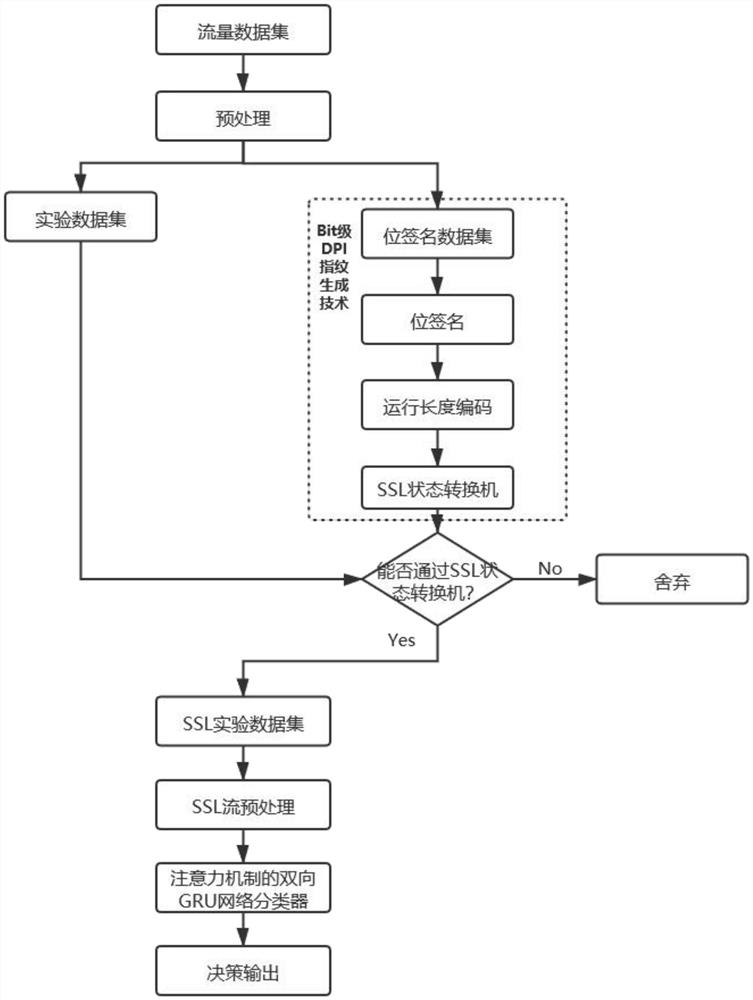
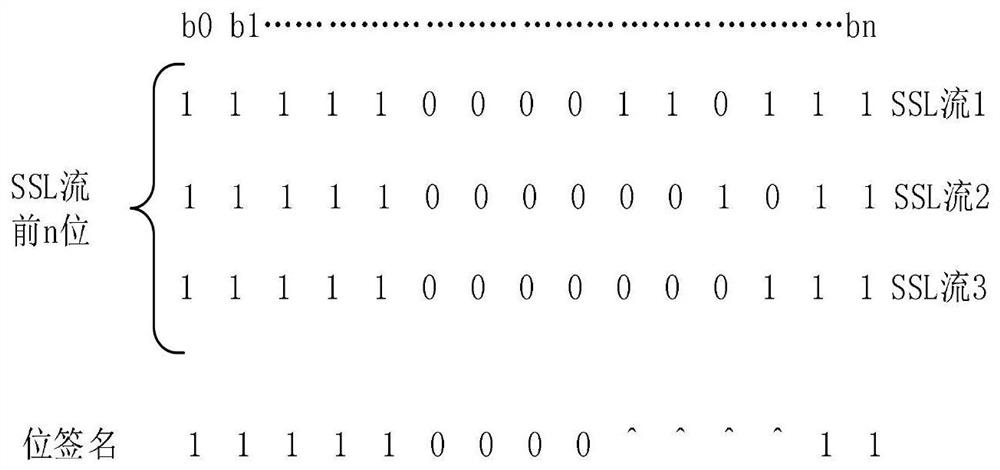
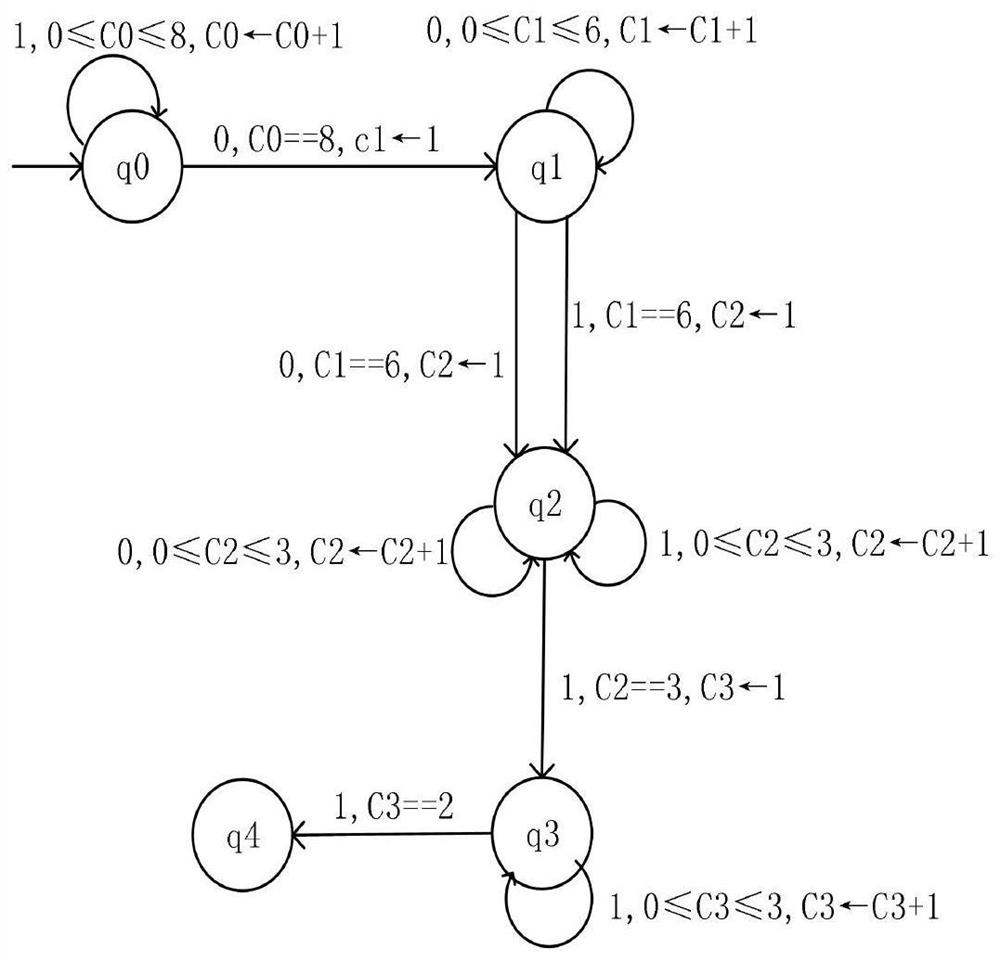
[0058] Embodiment: A method for identifying VPN traffic based on SSL encryption. Aiming at the problem of high missing recognition rate in traditional SSL encrypted traffic fingerprint identification methods, Bit-level DPI fingerprint generation technology is used to identify SSL traffic. After the data is preprocessed, a bit signature is generated through specific rules, and then the bit signature is encoded with run length. The encoded bit signature is used to generate an SSL state transition machine, which is used to identify SSL traffic. On the basis of identified SSL traffic, the two-way GRU network traffic identification model based on attention mechanism is used to identify SSL VPN traffic.
[0059] like figure 1 As shown, the process of identifying encrypted traffic under category imbalance includes at least: acquiring data sets, data preprocessing, bit-level DPI fingerprint generation, identifying SSL traffic, SSL flow set data preprocessing, identifying SSL VPN encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com